Universal serial bus (USB) device and method for recognition of host operating system
A host operating system and device identification technology, applied in the field of information security, can solve the problem that USB devices cannot identify the host operating system, and achieve the effect of optimizing USB devices and their applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
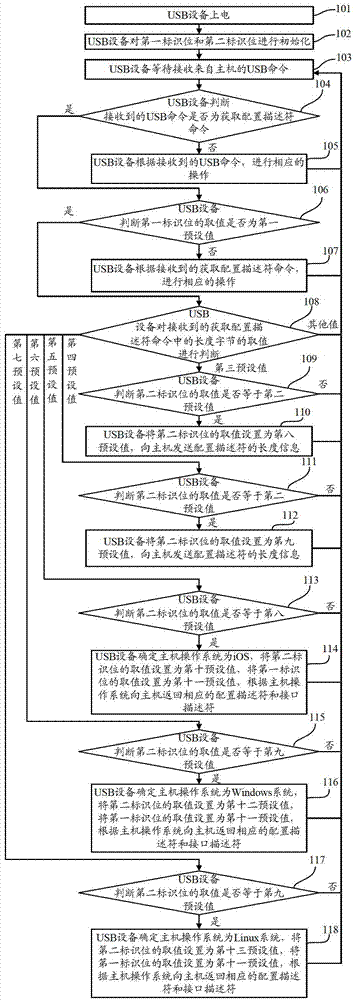
[0063] Such as figure 1 As shown, it is a flowchart of a method for identifying a host operating system by a USB device in Embodiment 1 of the present invention, including the following steps:
[0064] Step 101, the USB device is powered on.
[0065] Specifically, the USB device is connected to the host through the USB bus, and obtains the operating voltage from the host Vcc (power supply voltage or operating voltage). Among them, the USB device is specifically a security device (such as a USB Key), a card reader, a storage device (such as a U disk), or a keyboard, a mouse and other computer peripherals;
[0066] Step 102, the USB device initializes the first identification bit and the second identification bit.
[0067] Specifically, the USB device may set the value of the first identification bit as a first preset value, and set the value of the second identification bit as a second preset value. Wherein, the first identification bit is used to identify whether the USB de...
Embodiment 2
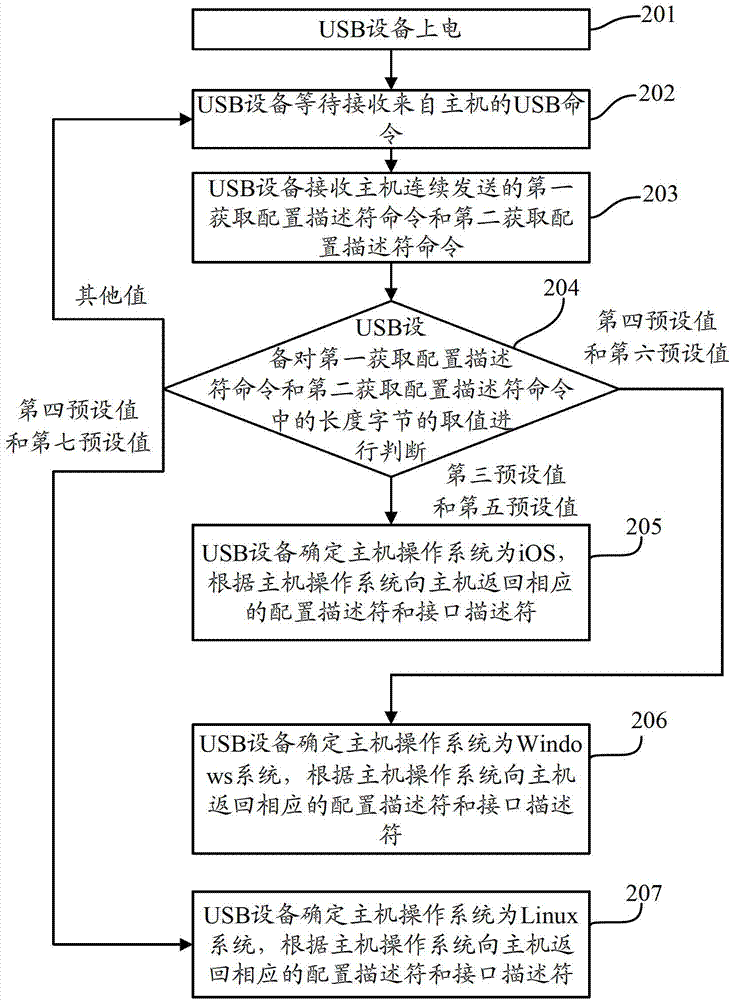
[0109] Such as figure 2 As shown, it is a flowchart of a method for identifying a host operating system by a USB device in Embodiment 2 of the present invention, including the following steps:
[0110] In step 201, the USB device is powered on.
[0111] Step 202, the USB device waits to receive a USB command from the host.
[0112] In step 203, the USB device receives the first acquire-configuration-descriptor command and the second acquire-configuration-descriptor command continuously sent by the host.
[0113] Wherein, the first acquire-configuration-descriptor command and the second acquire-configuration-descriptor command are USB commands sent by the host to the USB device during the enumeration phase of the USB device. The host requests to obtain the configuration descriptor of the USB device by sending the first obtain configuration descriptor command and the second obtain configuration descriptor command to the USB device. The first Get Configuration Descriptor comm...
Embodiment 3
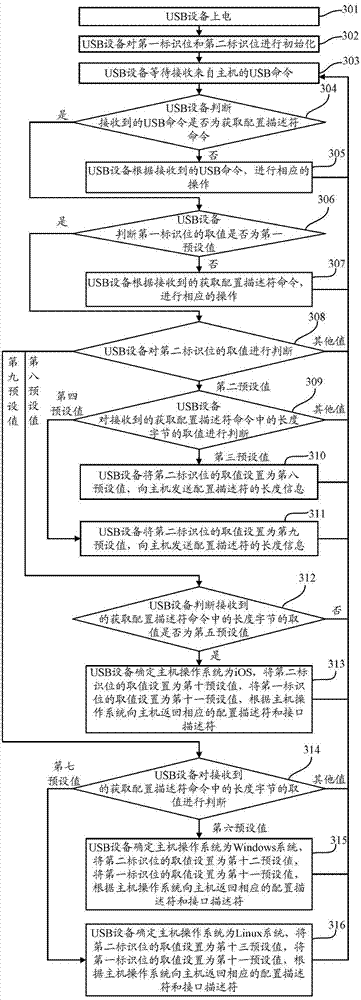
[0130] Such as image 3 As shown, it is a flowchart of a method for identifying a host operating system by a USB device in Embodiment 3 of the present invention, including the following steps:
[0131] In step 301, the USB device is powered on.
[0132] Specifically, the USB device is connected to the host through the USB bus, and obtains the operating voltage from the host Vcc (power supply voltage or operating voltage). Among them, the USB device is specifically a security device (such as a USB Key), a card reader, a storage device (such as a U disk), or a keyboard, a mouse and other computer peripherals;
[0133] Step 302, the USB device initializes the first identification bit and the second identification bit.
[0134] Specifically, the USB device may set the value of the first identification bit as a first preset value, and set the value of the second identification bit as a second preset value. Wherein, the first identification bit is used to identify whether the USB...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com