Embedded terminal software anti-copy and anti-plagiarism method
An embedded terminal and anti-copy technology, which is applied in electrical components, user identity/authority verification, transmission systems, etc., can solve the problems of terminal failure and high cost, and achieve command function and performance-price ratio advantages, low cost, High safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
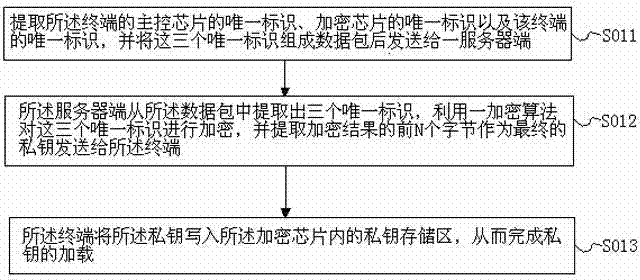
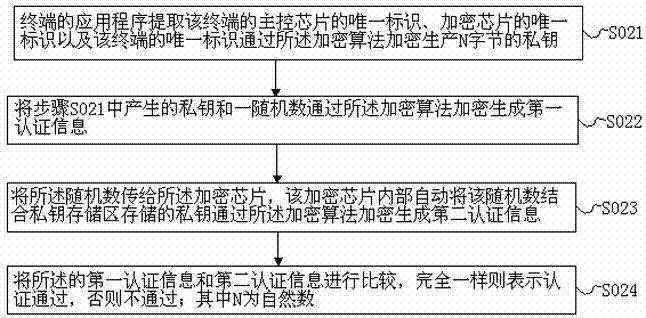
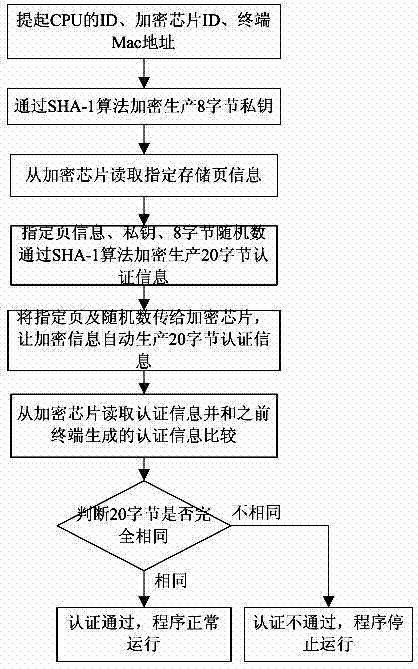
[0029] Such as figure 1 with figure 2 As shown, this embodiment provides a method for preventing copying and plagiarism of embedded terminal software, which is characterized in that it includes generation and loading of private keys, and terminal identity authentication;
[0030] The generation and loading of the private key includes the following steps:
[0031] Step S011: Extract the unique identifier of the main control chip of the terminal, the unique identifier of the encryption chip and the unique identifier of the terminal, and send these three unique identifiers into a data packet and send it to a server;
[0032] Step S012: The server extracts three unique identifiers from the data packet, encrypts the three unique identifiers using an encryption algorithm, and extracts the first N bytes of the encrypted result as the final private key and s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com