Method of access control, module and user device
A user equipment and access control technology, applied in access restriction, security device, network traffic/resource management, etc., can solve the problem that access control scheme cannot be applied
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
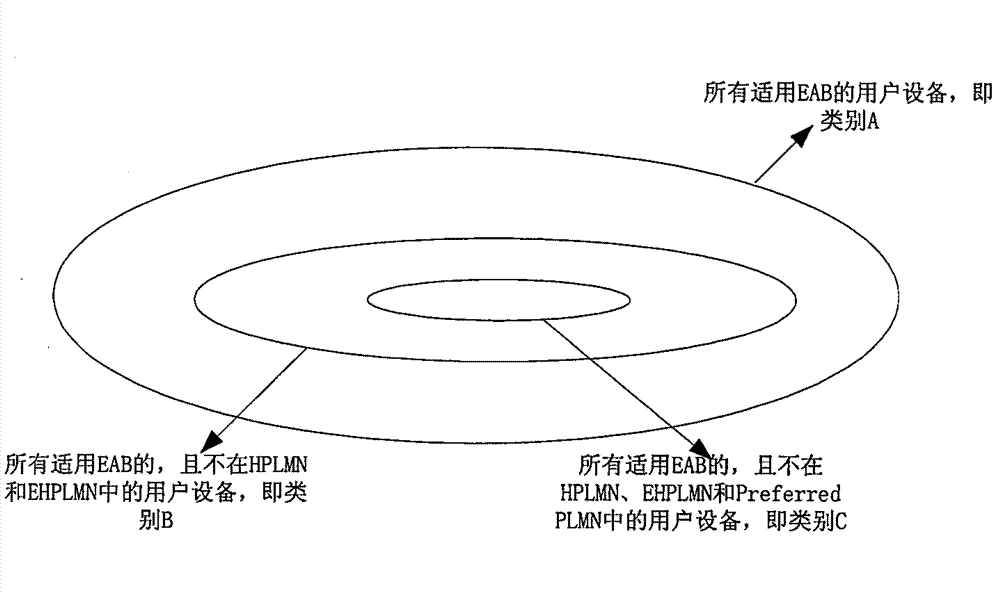
[0052] In the LTE system, the UE is in an idle state. A valid EAB is configured in the USIM card of the UE, which may be that the EAB configuration is set to True. In addition, the USIM card of the UE indicates that the access class (Access Class) of the UE is 8 and 11.
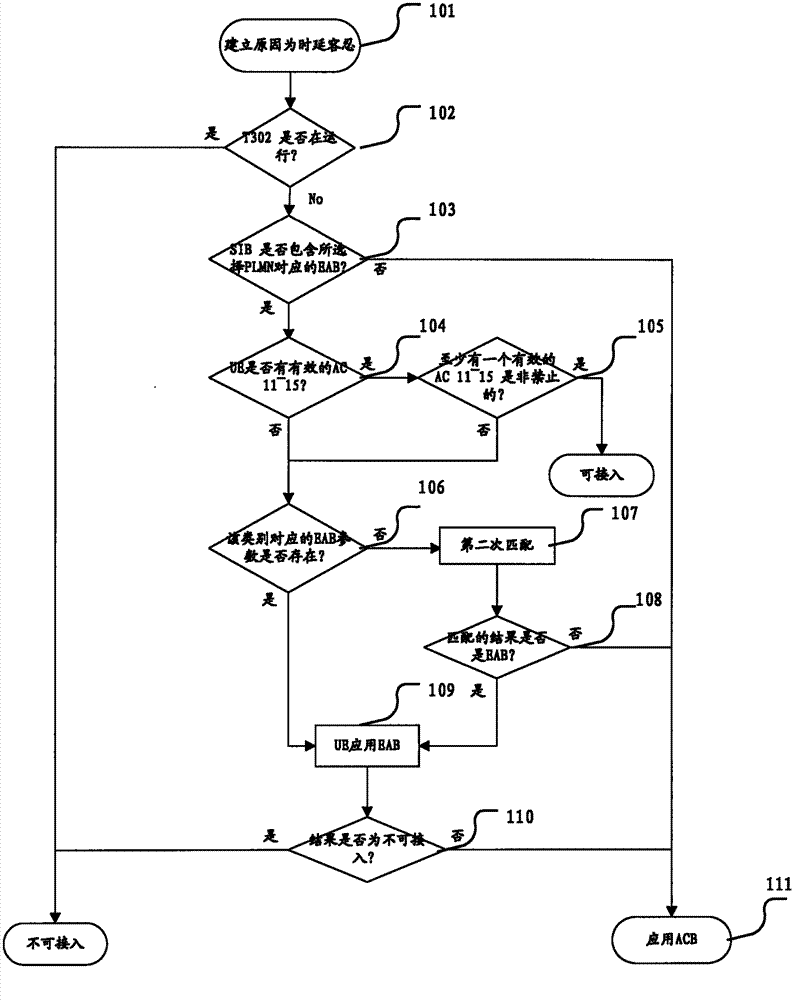
[0053] When the UE needs to initiate a delay tolerant (Delay Tolerant) service or a low priority (LowPriority) service, the non-access stratum NAS (non-Access Stratus, NAS for short) layer of the UE sends the establishment reason ( Establishment Cause) is the cause of delay tolerance or low priority. The AS layer of the UE implements the access decision process as follows: figure 1 Shown:
[0054] Step 101: the AS of the UE receives a service request from its upper layer (NAS), and the reason for establishing the service is delay tolerance.
[0055] Step 102: The UE judges whether the waiting time timer (T302) is running, if it is running, the UE judges that access to the current cell is prohibited (Consid...
specific Embodiment 2
[0082] In an LTE system, a UE resides in a cell under the jurisdiction of a base station and is in an idle state. A valid EAB is configured in the USIM card of the UE. In addition, the USIM card of the UE indicates that the access class of the UE is 5, that is, the Access Class is 5.
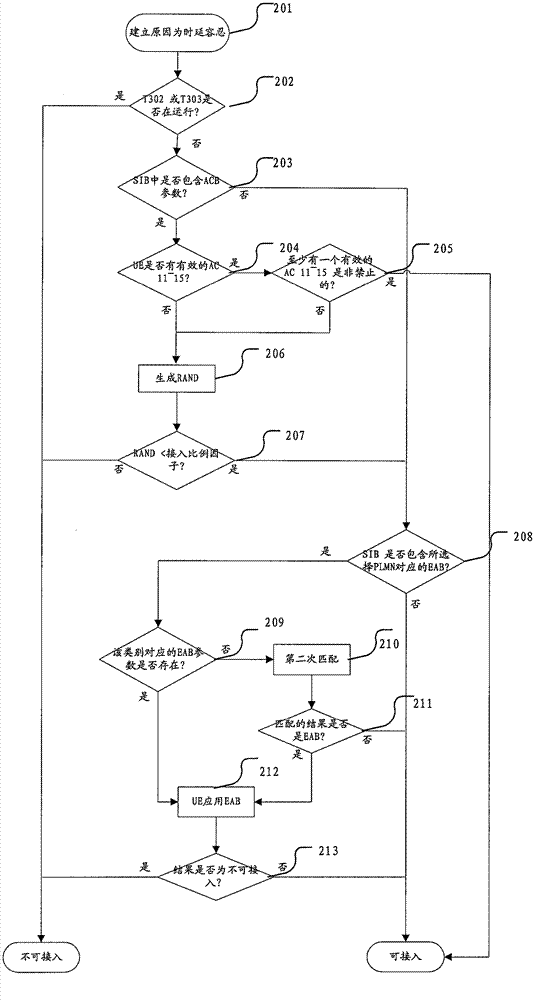
[0083] When the UE needs to initiate a delay tolerant (Delay Tolerant) service, the NAS layer of the UE sends the establishment reason to the AS layer of the UE as a delay tolerant reason. The AS layer of the UE implements the access decision process as follows: image 3 Shown:
[0084] Step 201: the AS of the UE receives a service request from its upper layer (NAS), and the reason for establishing the service is delay tolerance.
[0085] Step 202: The UE judges whether the waiting time timer (T302) or the access restriction timer (T303) set for the data service initiated by the user is running. If it is running, the UE judges that accessing the current cell is prohibited (consider access to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com