Information leakage preventing technology based on safety desktop for network environment
A technology of secure desktop and network environment, which is applied in the field of information leakage prevention based on secure desktop, can solve the problems of unable to prevent data leakage and employees themselves, and achieve the effect of providing convenience, convenient and flexible deployment, and preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
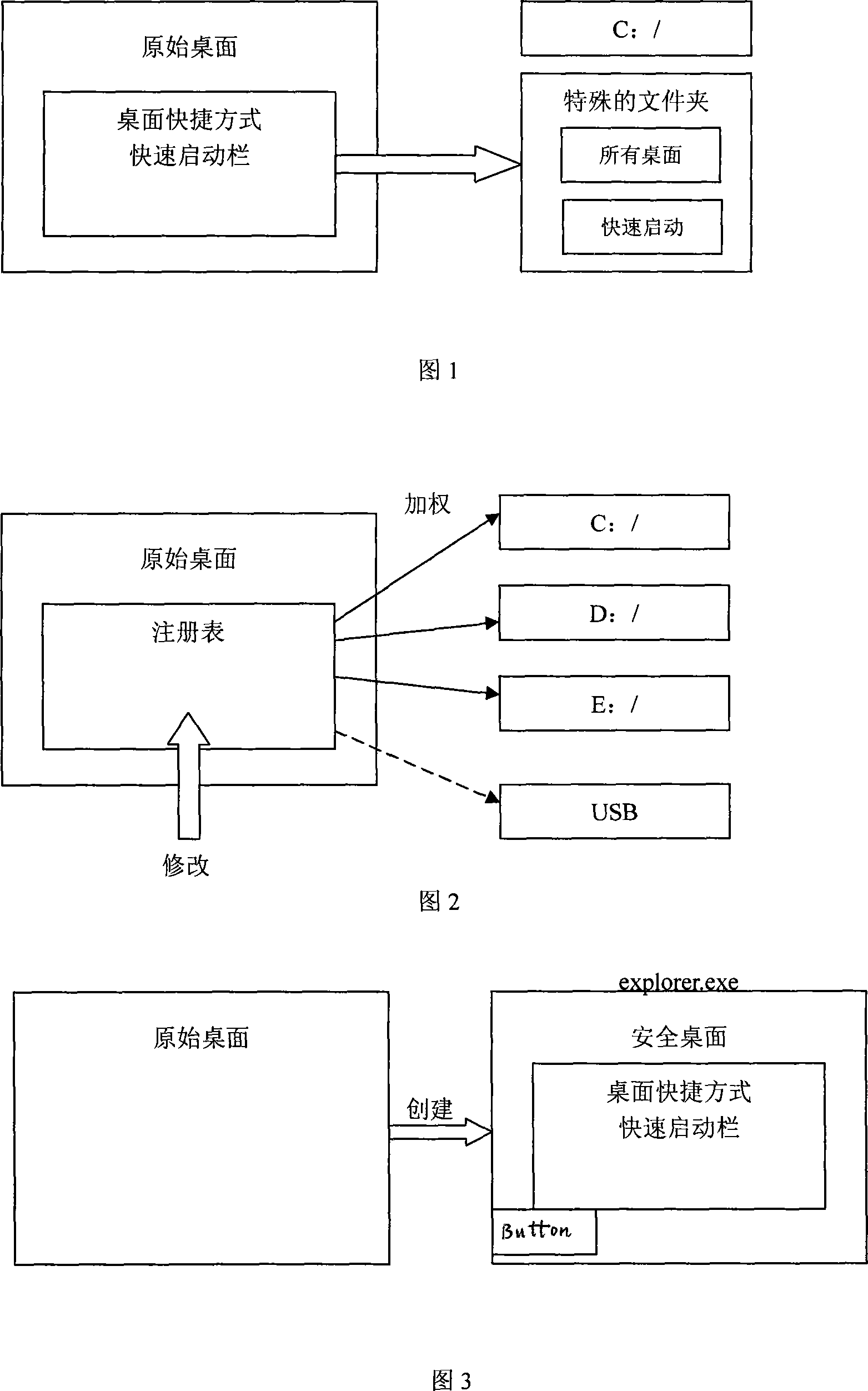
[0062] 1 Structural diagram of the security desktop-based network environment information leakage prevention technology scheme:
[0063] The terminal can be inside the enterprise or outside the enterprise network. Because the SSL VPN networking mode is adopted between the secure desktop and the content control gateway, it can break through the limitation of the network boundary and ensure security.
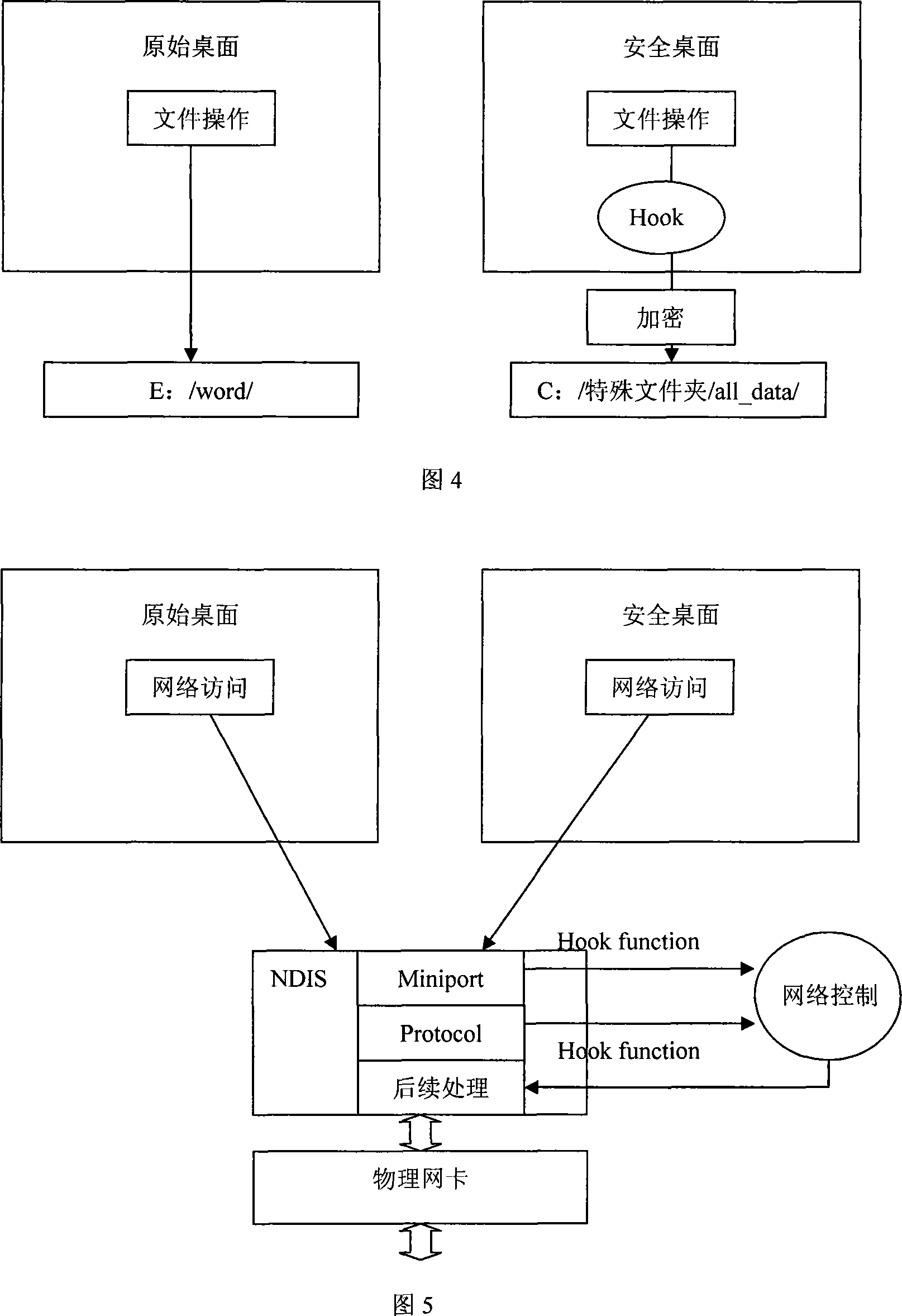
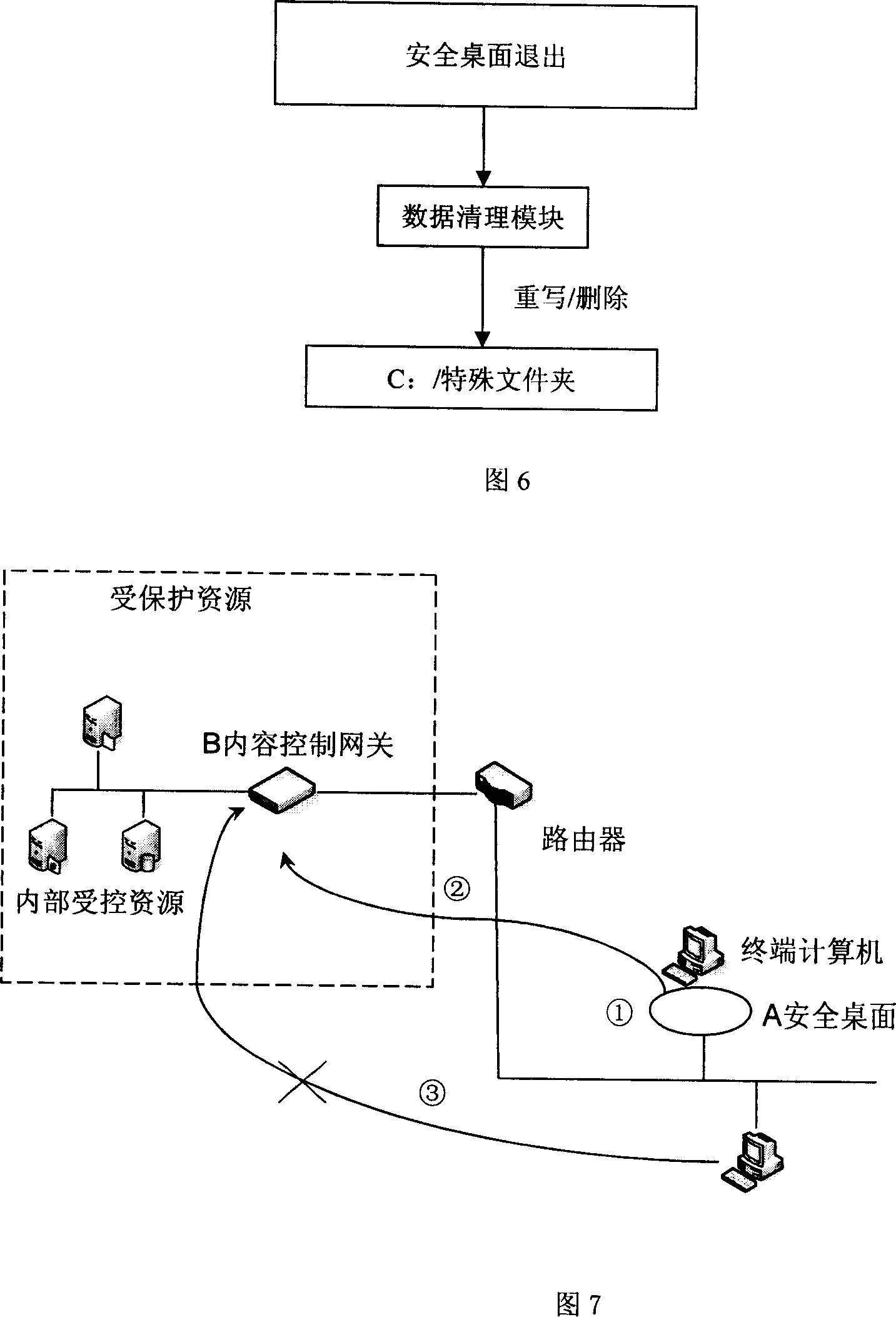
[0064] 2 Flowchart of the security desktop-based network environment information leakage prevention technology solution:
[0065] The specific process diagram of this scheme is shown in Figure 11, which mainly includes:
[0066] Step ①: When the terminal computer tries to access the intranet server, it must first log in to the content control gateway.
[0067] The content control gateway checks whether the computer is enabled with a secure desktop, and this handshake negotiation mechanism is carried out periodically. Moreover, it is performed in an encrypted channel, effectivel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com