Attack Detection Method Based on Spanning Tree Protocol of Trusted Switches
A technology of spanning tree protocol and attack detection, applied in the field of information security, to reduce the burden of network traffic, reduce workload, and prevent root takeover attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
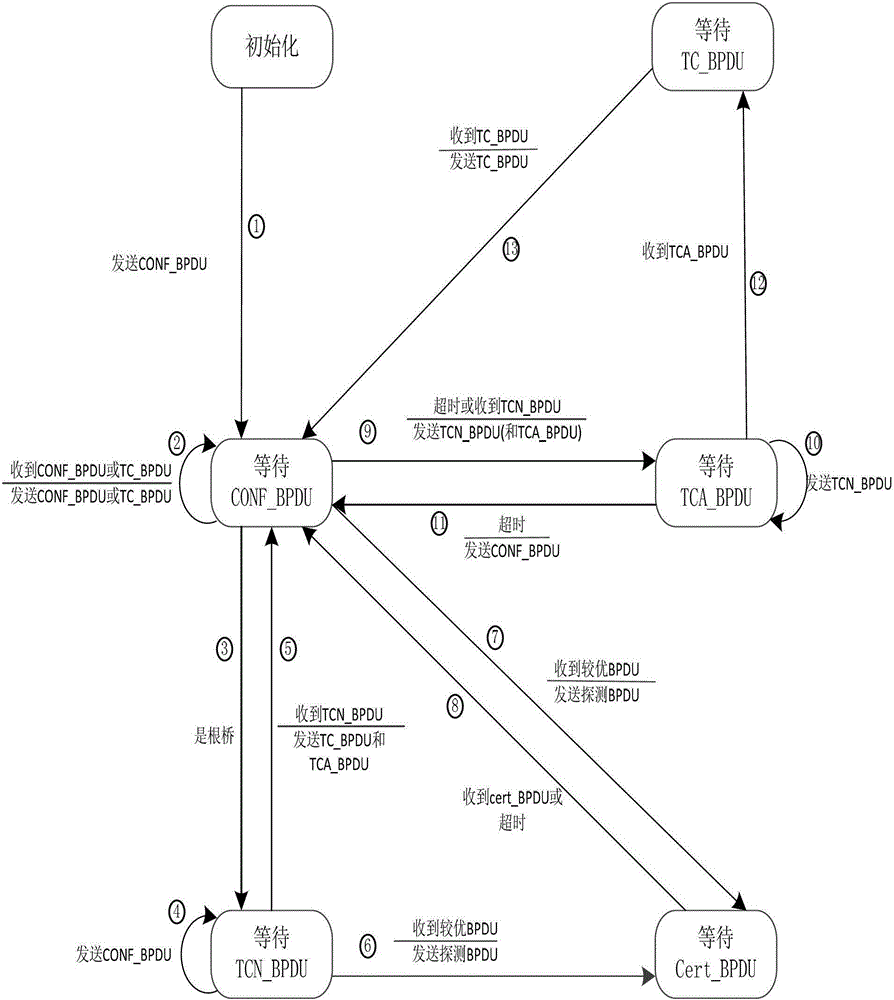
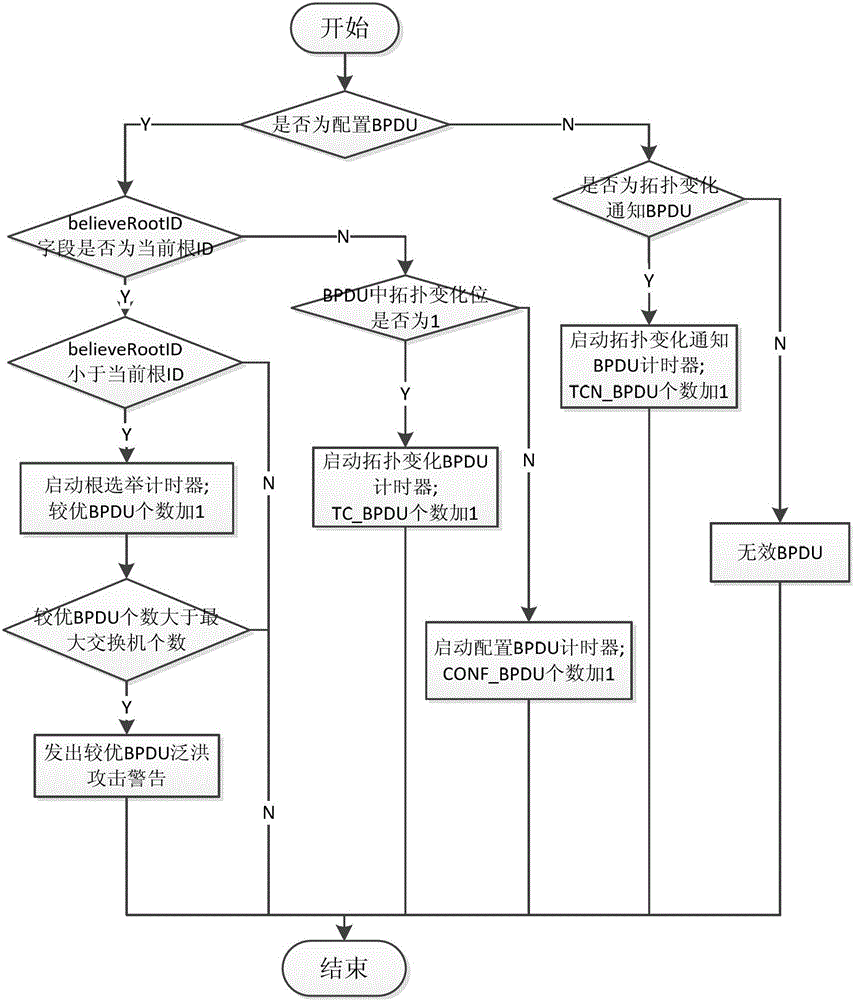
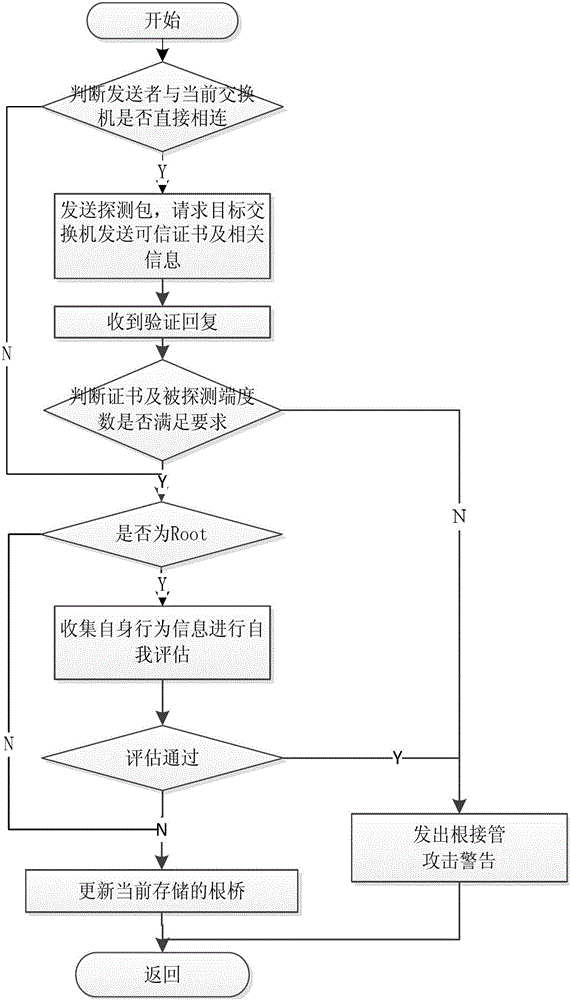
[0032] Attached below figure 1 , 2 , 3 specifically explain the implementation method and steps of the present invention.
[0033] The invention is an attack detection method based on the trusted exchange spanning tree protocol, which is divided into two parts: internal monitoring and external protection. After the switch successfully intervenes in the network, it first starts the state machine, executes the internal monitoring module, and regulates the internal operations of the spanning tree protocol, such as figure 1 . When a BPDU is received, the flood detection of the external protection module of the spanning tree protocol is performed to detect the flood attack behavior from the outside, such as figure 2 . Finally, perform root takeover attack detection, send verification and decide whether to replace the root bridge, such as image 3 .
[0034] First, according to figure 1 The state diagram in the Spanning Tree Protocol monitors the entire running process of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com