Attack detection method, device, equipment and storage medium
A detection method and equipment technology, applied in the field of network security, can solve problems such as network attack detection errors, poor network attack detection accuracy, and surge in data traffic, and achieve the effect of reducing the false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
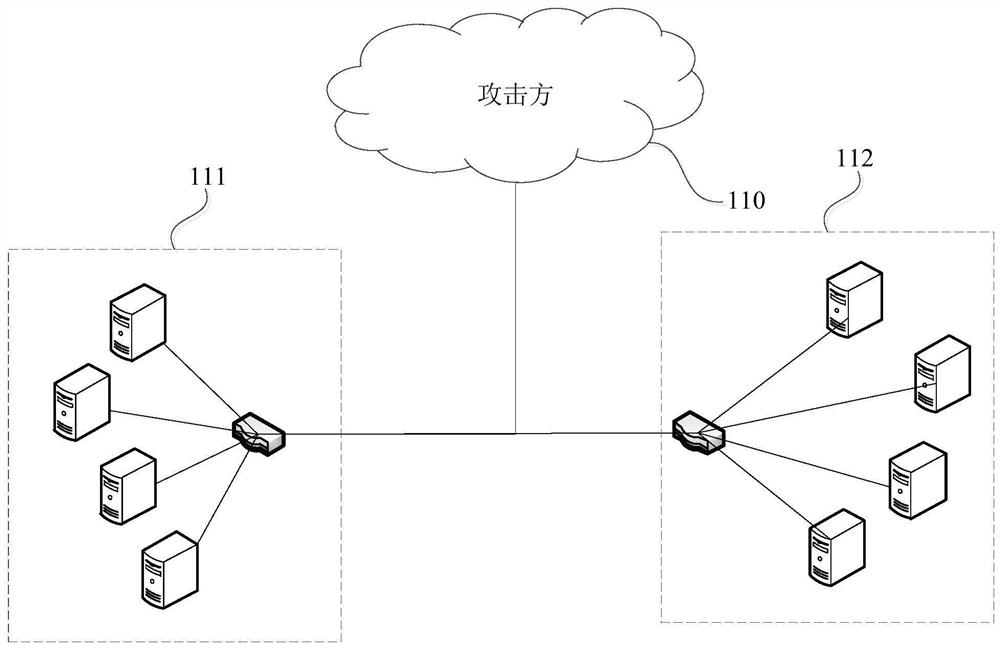
[0030] image 3 It is a scene architecture diagram of an attack detection method provided by the embodiment of the present invention. This embodiment is applicable to the detection of a distributed denial-of-service attack across Internet data centers. detection means, which can be implemented in hardware and / or software. see image 3 , the method of the embodiment of the present invention includes:
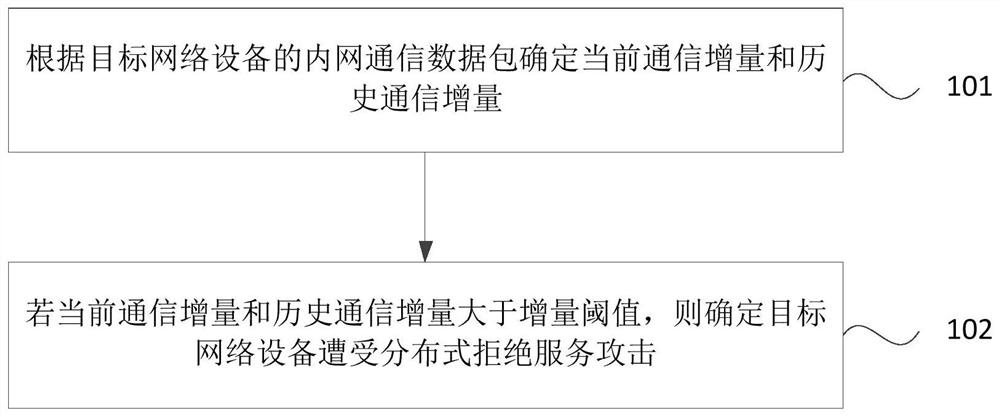
[0031] Step 101. Determine the current communication increment and historical communication increment according to the intranet communication data packets of the target network device.
[0032] Wherein, the target network device may be a gateway device of the Internet data center, and may be used to receive data packets sent through the network. The data packets may include data packets sent from the external network and service data packets sent from the internal network. The data packets can be forwarded to the server in the internal network.
[0033] Among them, the intran...
Embodiment 2
[0040] Figure 4It is a flow chart of an attack detection method provided by Embodiment 2 of the present invention. The embodiment of the present invention can be applied to devices in Internet data centers, and can detect network attacks on devices in Internet data centers. The embodiments of the present invention are described above On the basis of the embodiment of the invention, see Figure 4 , the method of the embodiment of the present invention includes:
[0041] Step 201, obtain the network data packet of the target network device through a bypass, and the network data packet whose destination address and source address are internal addresses is an intranet communication data packet.
[0042] Wherein, the network data packet can be the data packet obtained by the target network device, the network data packet can be used for data transmission and synchronization between Internet data centers, and the network data packet can include Transmission Control Protocol (TCP, ...
Embodiment 3
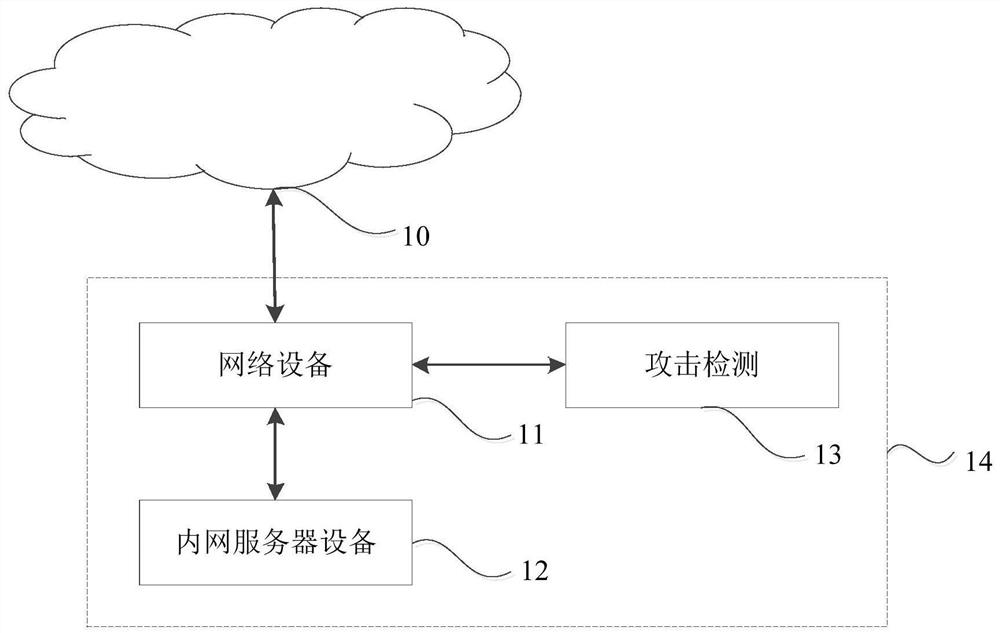
[0082] Figure 7 It is a schematic structural diagram of an attack detection device provided in Embodiment 3 of the present invention. The attack detection device provided in the embodiment of the present invention can execute the attack detection method provided in any embodiment of the present invention, and has corresponding functions for executing the method Modules and benefits. see Figure 7 , the device in this embodiment of the present invention includes: an increment determination module 301 and an attack determination module 302 .
[0083] Wherein, the increment determination module 301 is configured to determine the current communication increment and the historical communication increment according to the intranet communication data packets of the target network device.
[0084] The attack determination module 302 is configured to determine that the target network device suffers from a distributed denial of service attack if the current communication increment an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com