A Method for Identifying Spam Sources Based on Frequency and Called Distribution Rules
A technology of spam text messages and text messages, applied in wireless communication, network data management, security devices, etc., can solve problems such as ineffective identification, and achieve the effect of improving completeness and precision, accurate search and management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below.
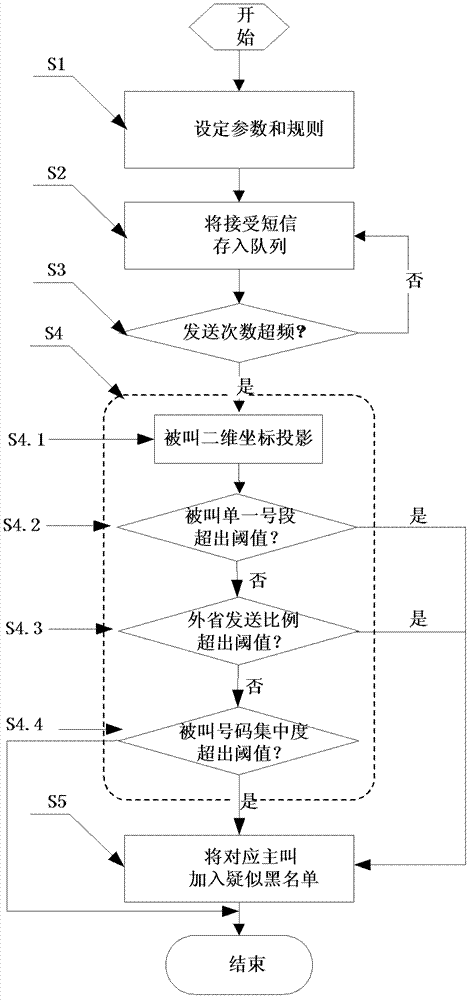
[0035] see figure 1 , the method for identifying spam source based on frequency and called distribution rules of the present invention, specifically comprises the following steps:
[0036] Step S1: Set parameters and rules, that is, set time granularity range, SMS frequency threshold and called number dispersion rules, among which:
[0037] SMS frequency threshold, that is, the maximum threshold of the number of SMS messages sent by the calling source within the set time granularity range; when the number of SMS messages sent by the calling source within the set time granularity range exceeds the SMS frequency threshold, the calling source SMS messages will be monitored;
[0038] Called number dispersal rules, that is, within the set time granularity, monitor the dispersive rule feature of calling source SMS sending called numbers; when the sending behavior of the calling source conforms to the called number dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com