Method and device for encrypting and decrypting java source code
An encryption device and source code technology, applied in the network field, can solve the problem that Java language is easy to be decompiled, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
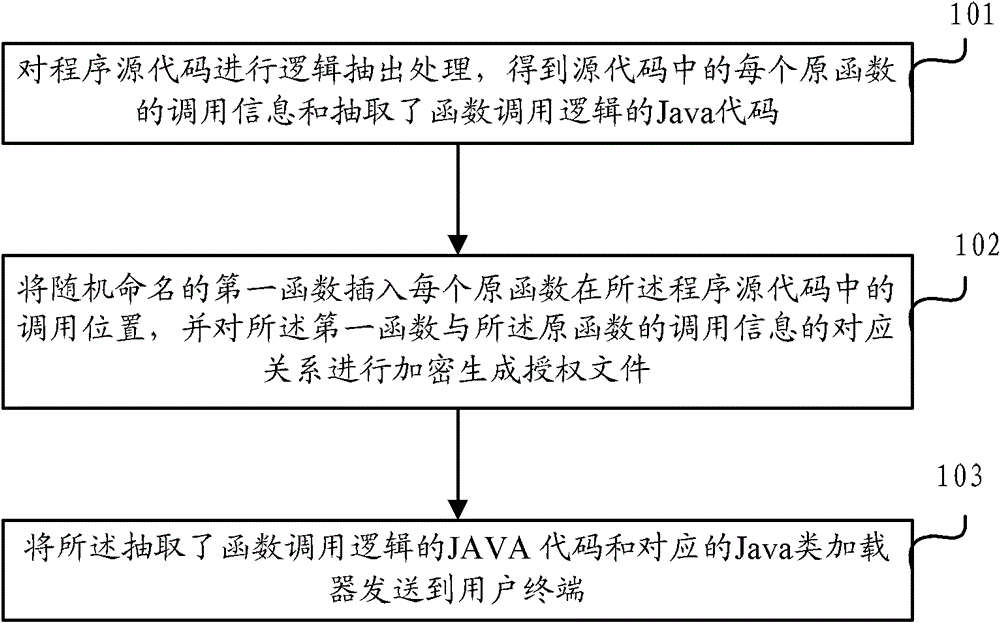
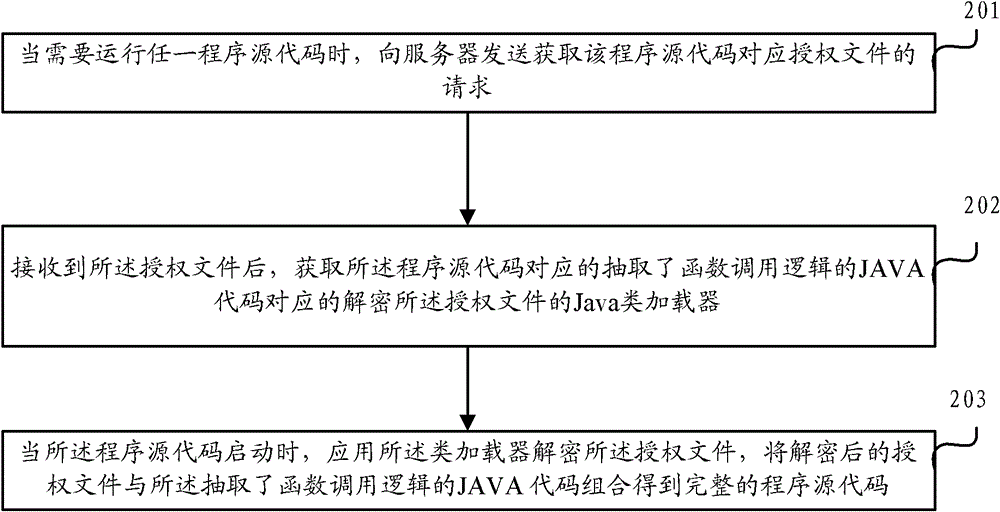
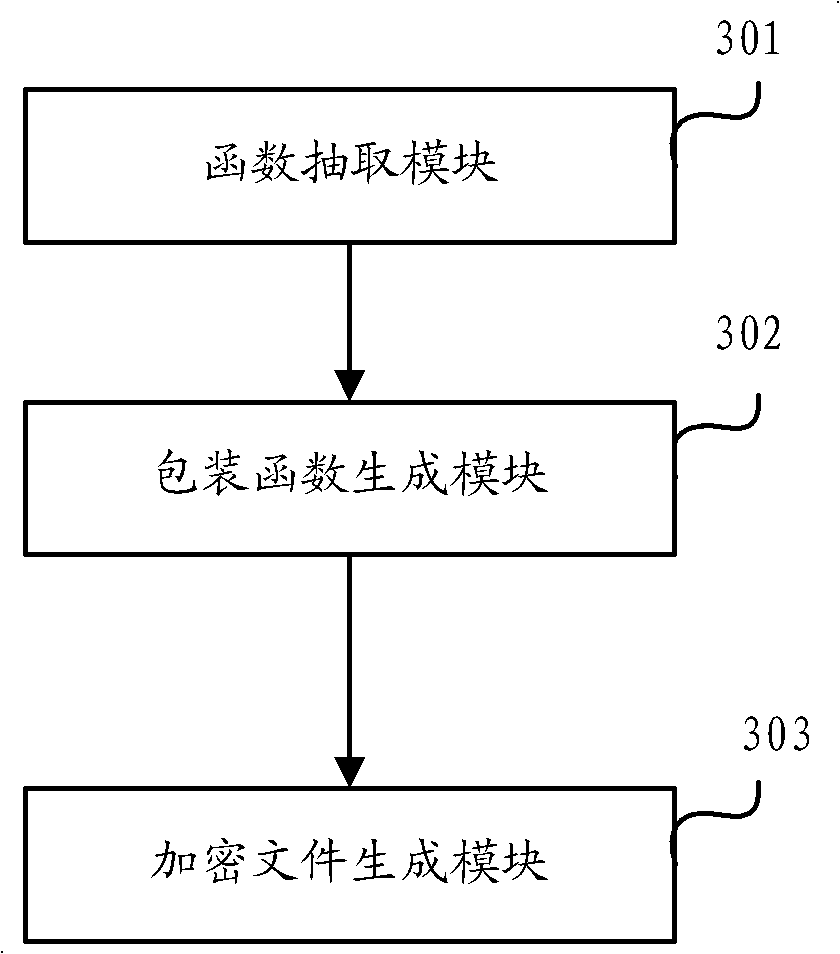
[0035] The embodiment of the present application provides a method for encrypting Java source code, the method comprising: performing logic extraction on the program source code to obtain the function call logic in the source code and the Java code that has extracted the function call logic; Insert a randomly named first function at the original calling position of the logic, and encrypt the corresponding relationship between the first function and the function calling logic to generate an authorization file; extract the Java code with the function calling logic and the corresponding The Java class loader sends it to the user terminal, so that the user terminal obtains the authorization file by sending a request, then uses the Java class loader to decrypt the authorization file, and combines the decrypted function call logic with the extracted function call Logical Java code generates source code files.
[0036] Such as figure 1 As shown, the embodiment of the present applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com