Method and device for P2P (peer-to-peer) flow inspection
A P2P traffic and quantity technology, applied in the field of network security, can solve the problems of high recognition error rate, many detection indicators, long detection time, etc., achieve high detection accuracy, improve recognition accuracy, and improve recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0049] In the first embodiment of the present invention, a method for detecting P2P traffic, such as figure 1 shown, including the following specific steps:
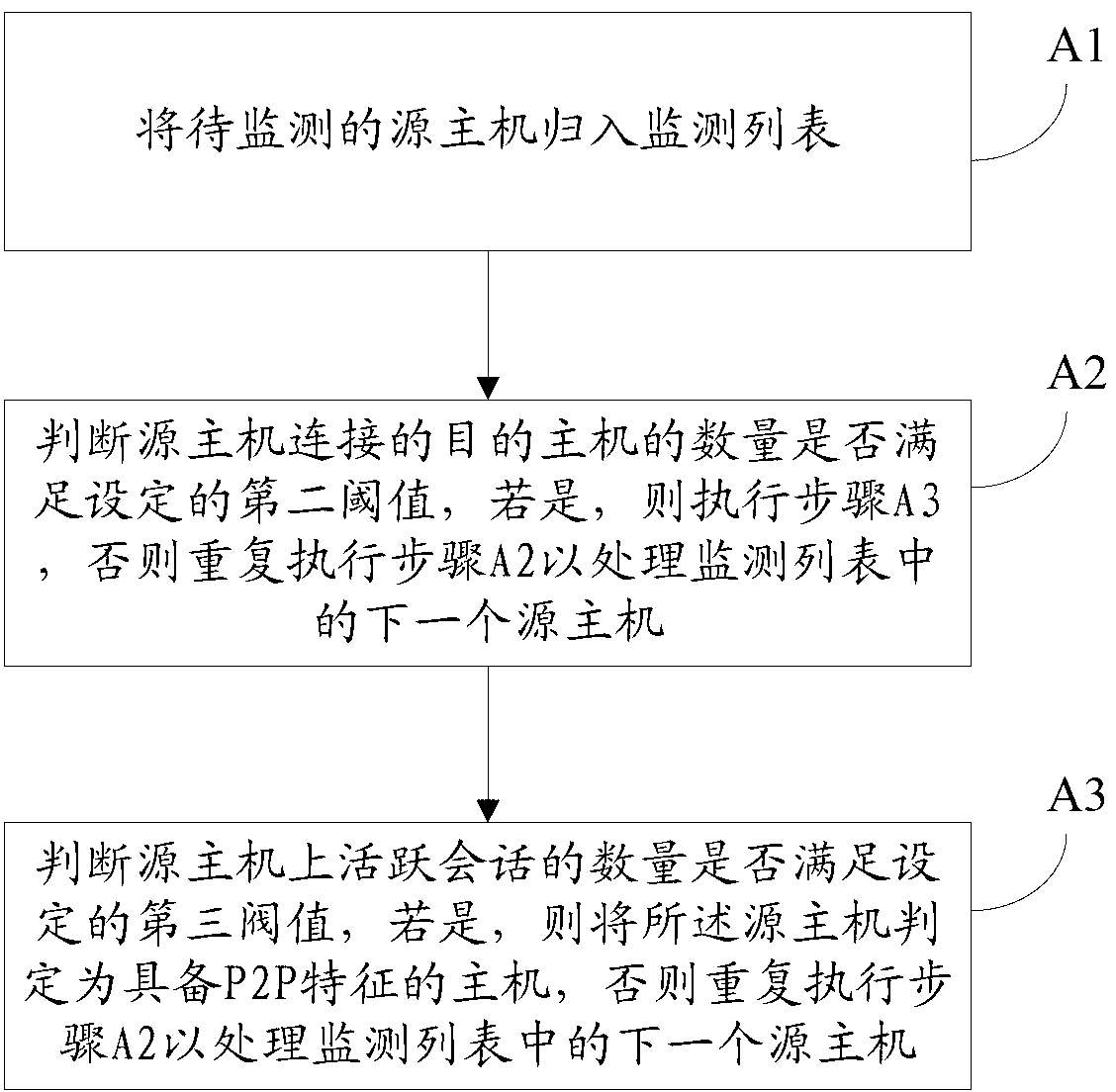
[0050] In step S101, the source host is monitored to obtain the number of destination hosts connected to the source host and the number of active sessions on the source host. When the source host accesses the destination host, it initiates a connection request to the destination host, and the destination host is a host that provides download resources.
[0051] Specifically, the acquisition process of the number of destination hosts connected to the source host is as follows:
[0052] Determine the number of destination hosts connected to the source host by counting the IP addresses of the destination hosts accessed by the source host;
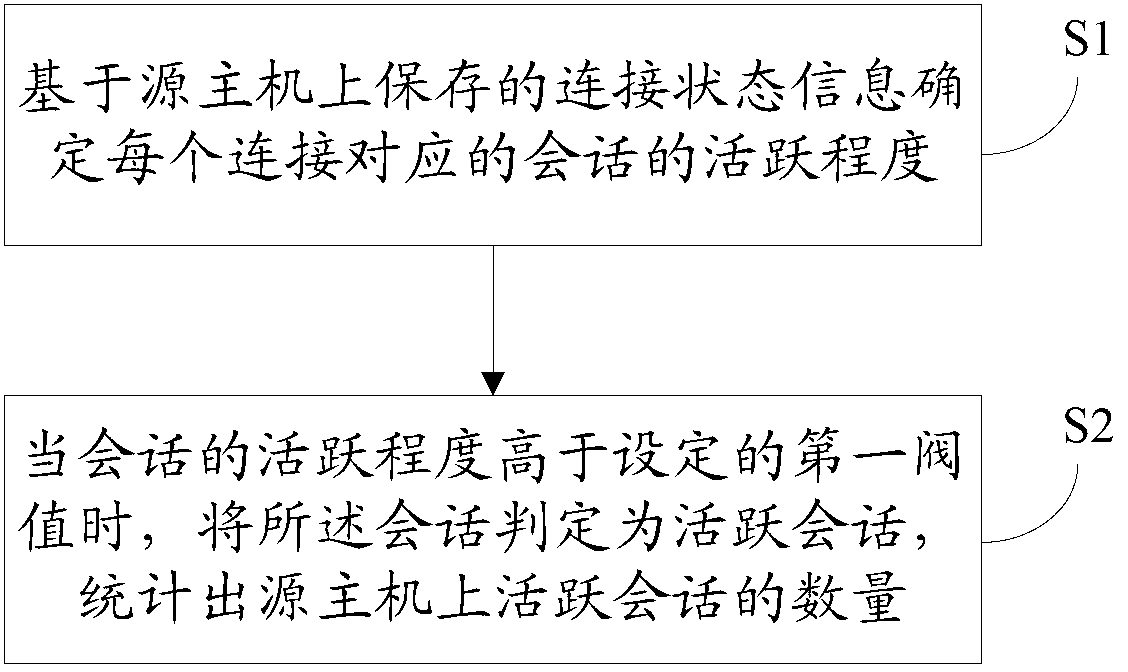
[0053] Such as figure 2 As shown, the acquisition process of the number of active sessions on the source host is as follows:
[0054] S1. Determine the activity level of the session...
no. 2 example
[0065] In the second embodiment of the present invention, a device for detecting P2P traffic, such as Figure 4 shown, including the following components:
[0066] The monitoring module 100 is used to monitor the source host to obtain the number of destination hosts connected to the source host and the number of active sessions on the source host; when the source host accesses the destination host, it initiates a connection request to the destination host, and the destination host provides download resources the host.
[0067] The judging module 200 is configured to judge whether the source host has P2P features according to the number of destination hosts connected to the source host and the number of active sessions on the source host.
[0068] Specifically, when acquiring the number of destination hosts connected to the source host, the monitoring module 100 is specifically used to:
[0069] Determine the number of destination hosts connected to the source host by countin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com