Method for realizing information safety through conversation and mobile terminal thereof
An information security and mobile terminal technology, applied in the field of methods and mobile terminals, can solve the problems of easy uninstallation and complicated operation, and achieve the effect of simplifying operation, avoiding complicated operation and improving user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
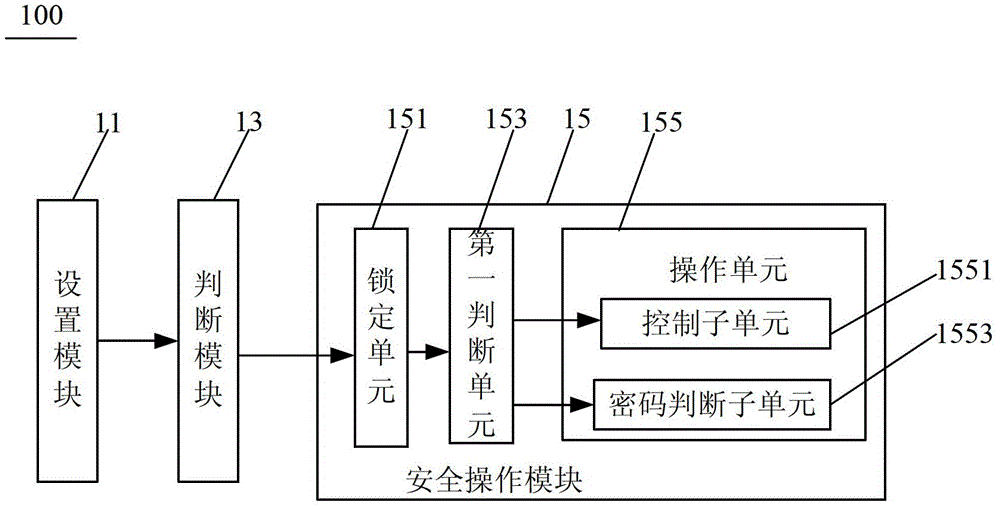
Image
Examples
Embodiment Construction
[0036] Embodiments of the present invention will now be described with reference to the drawings, in which like reference numerals represent like elements.
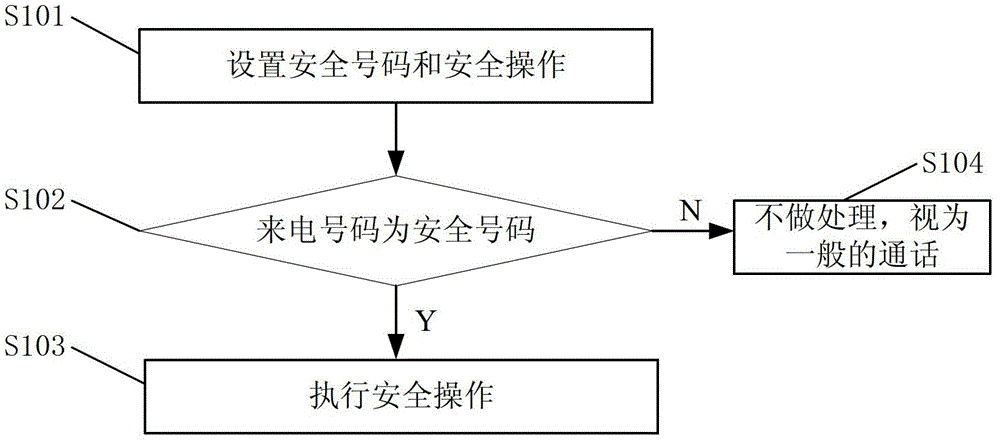
[0037] Please refer to figure 1 , describes the working process of an embodiment of the method for realizing information security by using a call in the present invention. like figure 1 shown, including the following steps:
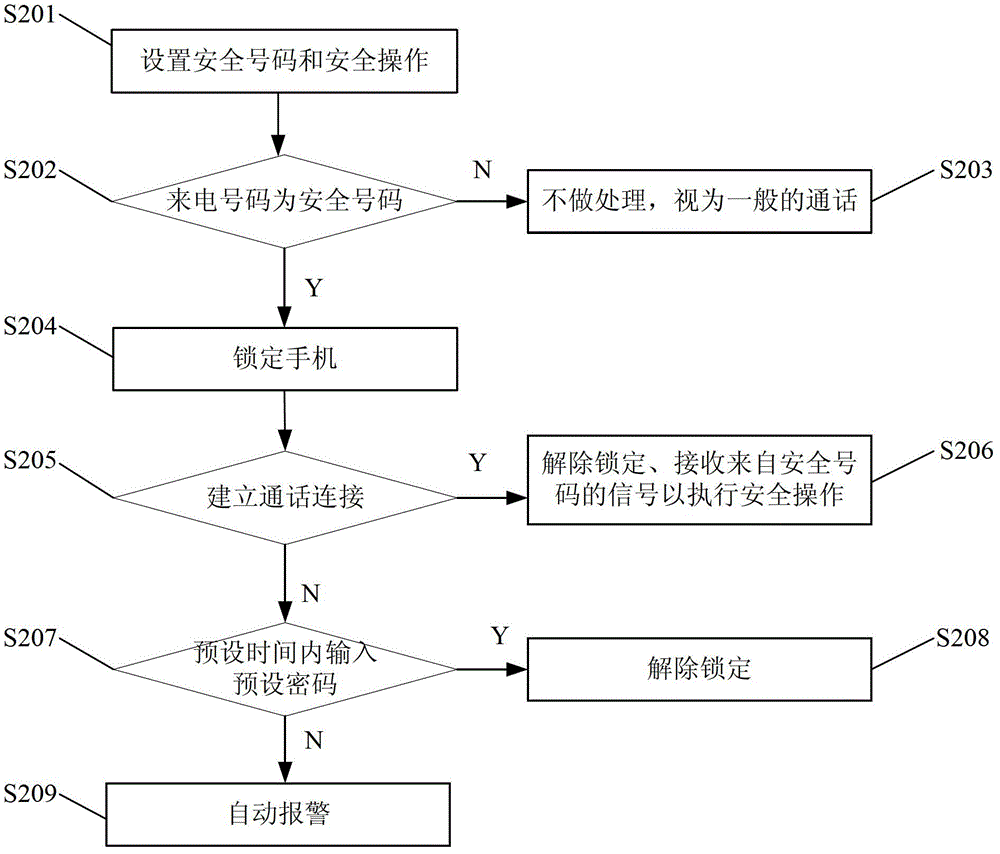
[0038] Step S101, setting a security number and a security operation; wherein the security number is a mobile number or a fixed-line number, and the security operation is to lock the mobile phone, delete information, automatically alarm or any combination of the three, and the specific implementation process of deleting information is: call the reset of the system Clear the interface to restore the data to factory settings, so that when the mobile phone is lost or stolen, the user's private information in the mobile phone can be deleted to ensure information security. The specific process of automa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com