Method and device for protecting codes of embedded software by hardware encryption module
A hardware encryption and software code technology, applied in the protection of internal/peripheral computer components, digital data protection, etc., can solve problems such as hidden technical security risks and cumbersome preparation work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
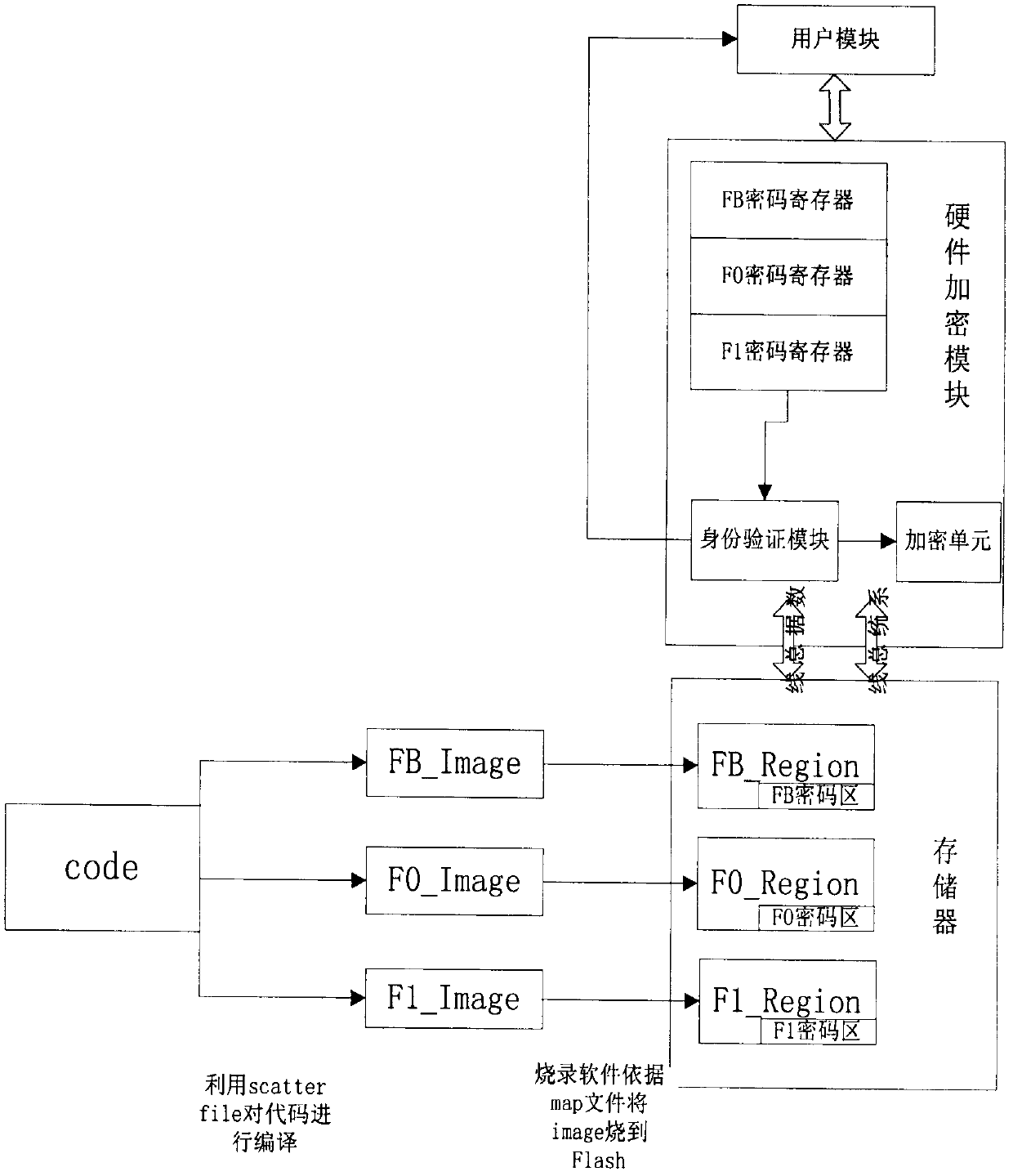
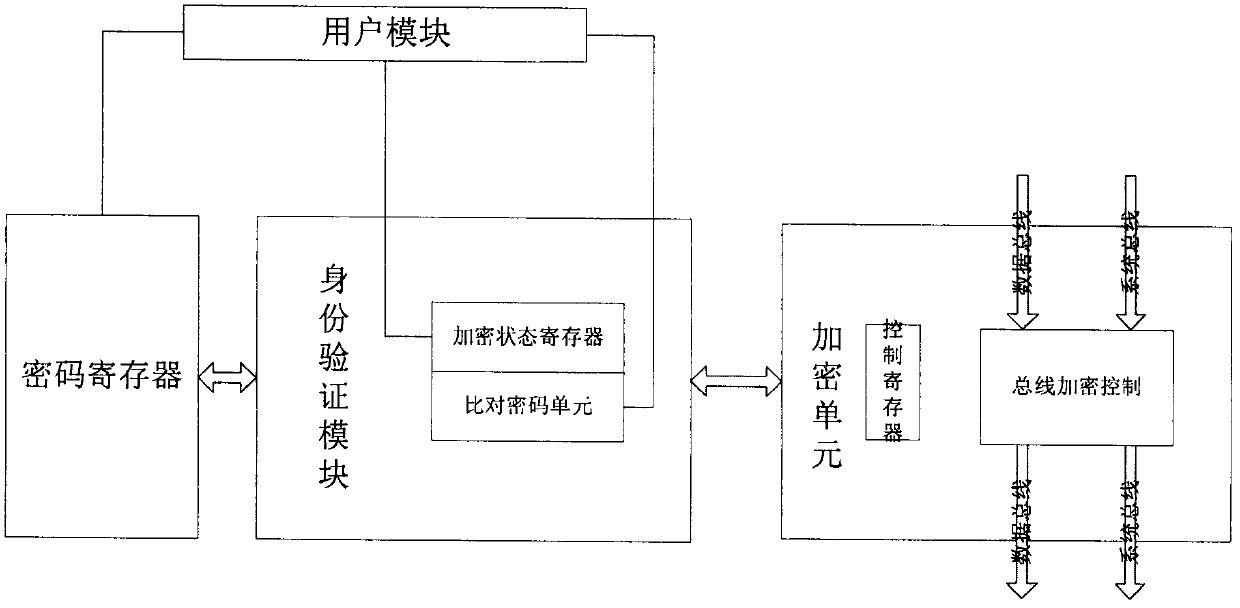
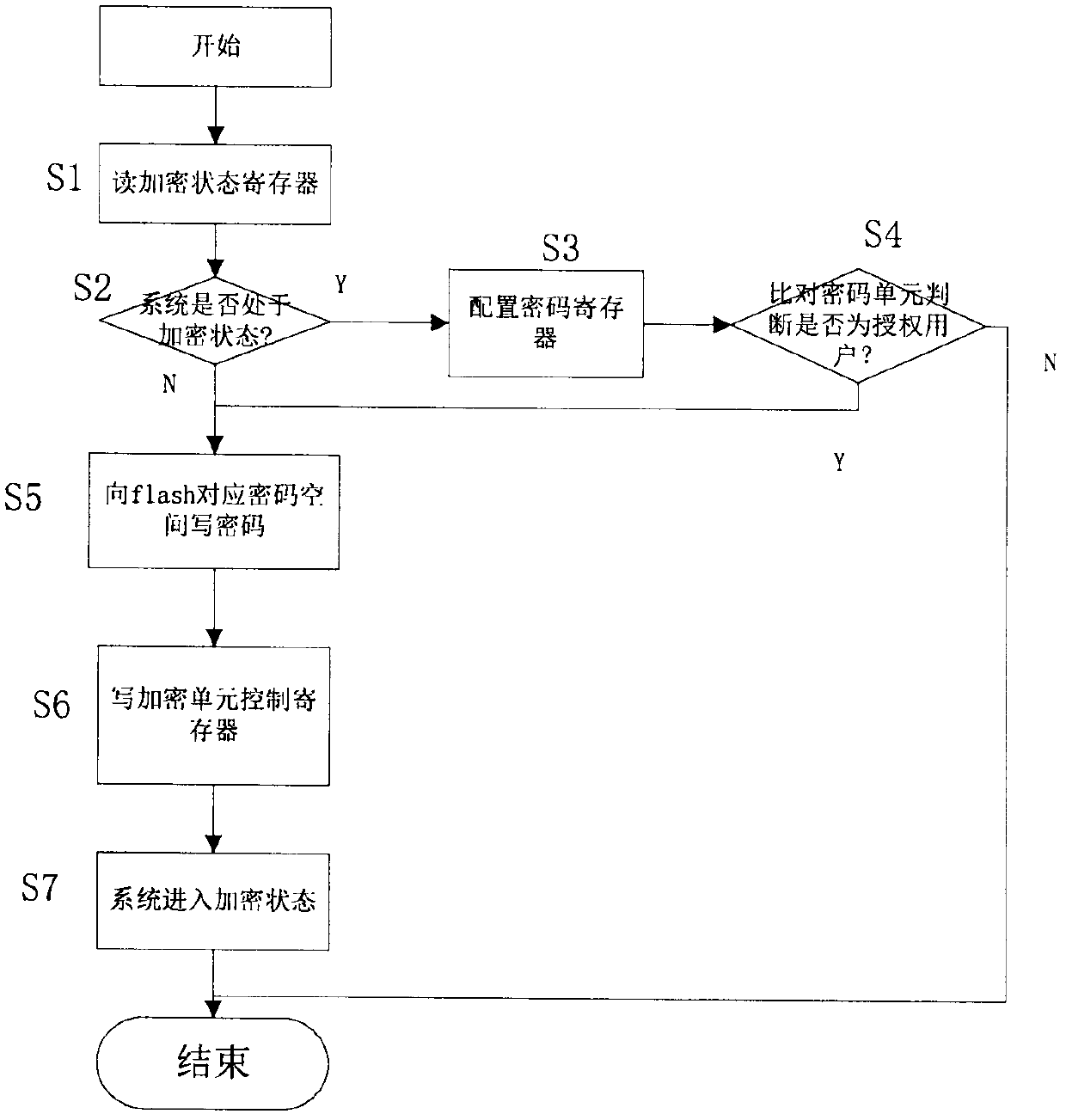
[0025] The invention utilizes the user module to control the hardware encryption module to perform encryption operation on the memory, so as to realize the code protection. The user module may be software, or a processor or other types of hardware modules that execute specific steps. The main idea of the present invention is to generate multi-segment images corresponding to different areas after compiling and linking the codes, and then burn them into the corresponding areas, and realize the separation of the storage area and the user through the user module to control the hardware encryption module, thereby to the effect of code protection.
[0026] Such as figure 1 As shown, the invention divides the memory into three regions, namely FB_Region, F0_Region and F1_Region. FB_Region mainly stores some key data and code information of the hardware driver layer; F0_Region is the first-level customer encryption area; F1_Region is the second-level customer encryption area, as sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com