Rights management method, system and server
A technology of authority management and server, which is applied in the field of information management, can solve problems such as insecurity, and achieve the effect of ensuring security, convenient use, and meeting the requirements of privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
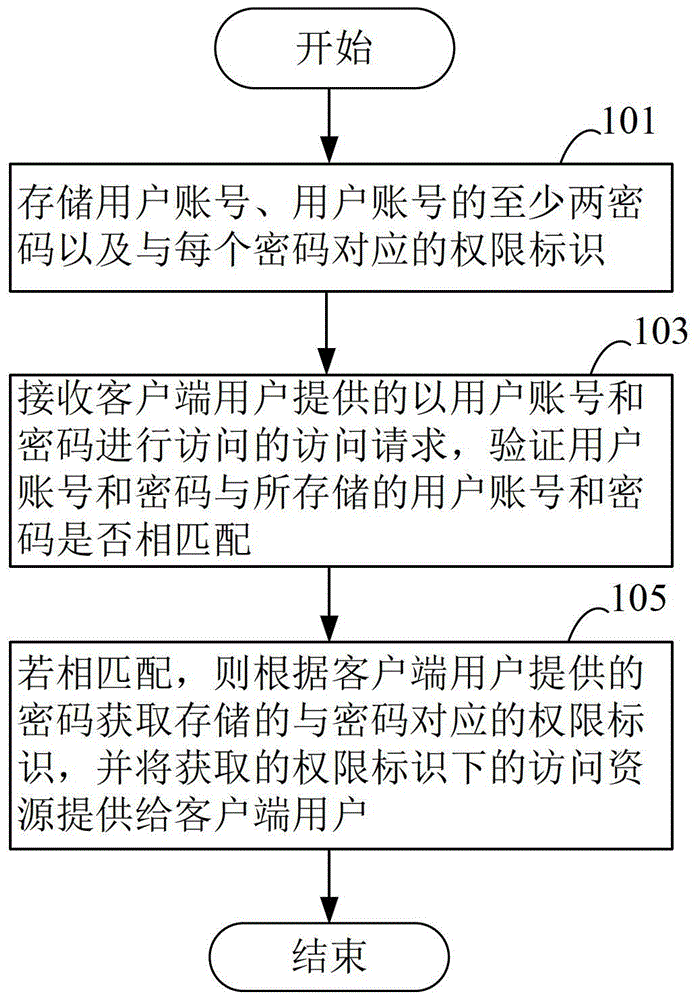
[0020] Please refer to figure 1 , which shows a method flowchart of a rights management method provided by an embodiment of the present invention. The rights management method may include the following steps 101-105:
[0021] Step 101, storing a user account, at least two passwords of the user account, and an authority identifier corresponding to each password.
[0022] The user account may be a unique account number assigned by the server to multiple users of the client, and may include letters, numbers and other information. The user account may be a chat application account or any other type of account, which will not be listed here.
[0023] The permission identifier is used to identify multiple users of the same account to distinguish different users. Each password can be configured with a corresponding permission identifier, which can include information composed of letters, numbers and other arbitrary characters.
[0024] Step 103, receiving an access request provide...
no. 2 example
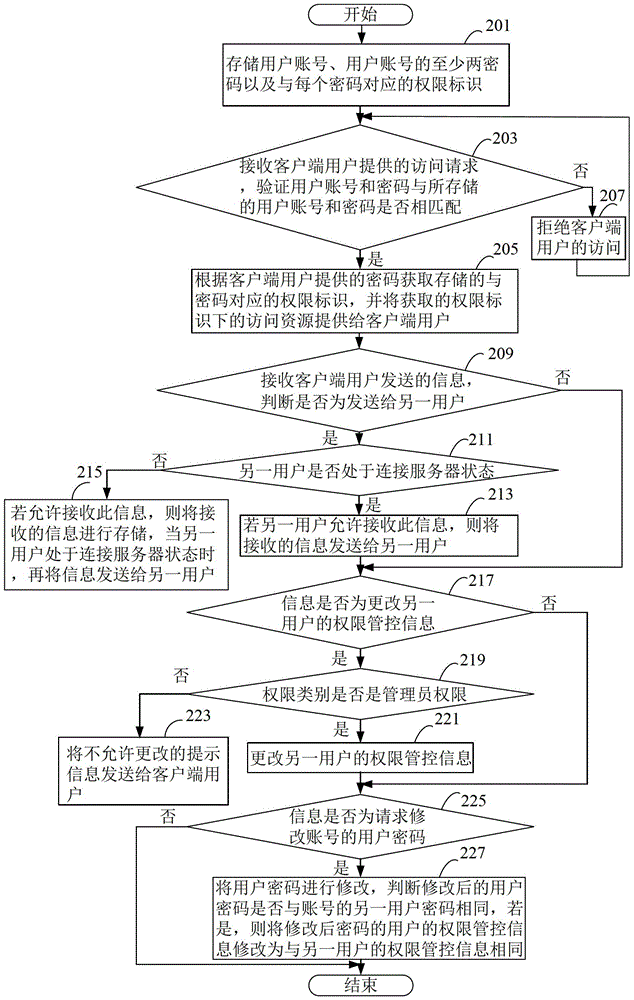
[0028] Please refer to figure 2 , which shows a method flowchart of a rights management method provided by another embodiment of the present invention. figure 2 is in figure 1 improved on the basis of The rights management method may include the following steps 201-227:
[0029] Step 201, storing a user account, at least two passwords of the user account, and an authority identifier corresponding to each password.
[0030] The user account may be a unique account number assigned by the server to multiple users of the client, and may include letters, numbers and other information. The user account may be a chat application account or any other type of account, which will not be listed here.
[0031] The permission identifier is used to identify multiple users of the same account to distinguish different users. Each password can be configured with a corresponding permission identifier, which can include information composed of letters, numbers and other arbitrary character...
no. 3 example
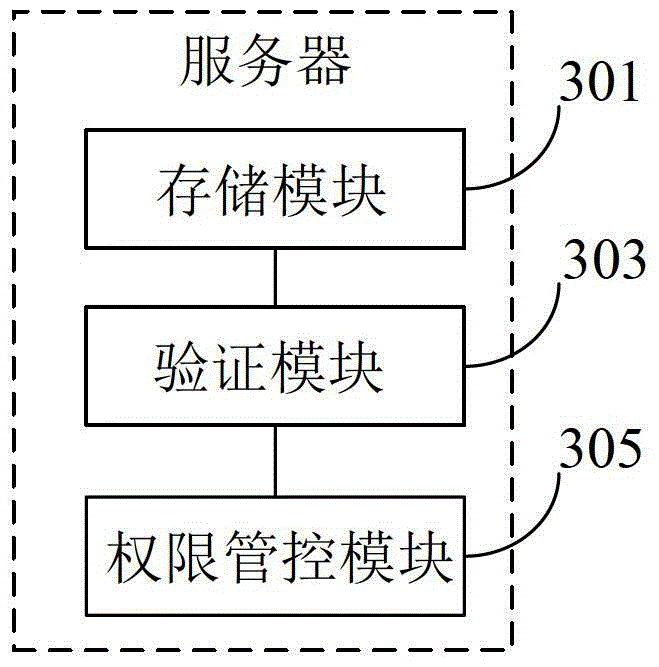
[0081] Please refer to image 3 , which shows a main structural block diagram of a server provided by an embodiment of the present invention. The server includes: a storage module 301, a verification module 303, and a rights control module 305.
[0082] Specifically, the storage module 301 is configured to store a user account, at least two passwords of the user account, and an authorization identifier corresponding to each password.
[0083] The verification module 303 is configured to receive an access request provided by a client user with a user account and password, and verify whether the user account and password match the stored user account and password.
[0084] The authority control module 305 is configured to obtain the stored authority identifier corresponding to the password according to the password provided by the client user if they match, and provide the access resources under the acquired authority identifier to the client user.
[0085] To sum up, the serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com