Encryption parameter transmitting method of wireless communication terminal equipment
An encryption parameter and wireless terminal technology, applied in the field of wireless communication, can solve the problems of occupying encryption parameters, affecting voice restoration, unable to restore voice data, etc., to achieve the effect of improving security performance and high confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
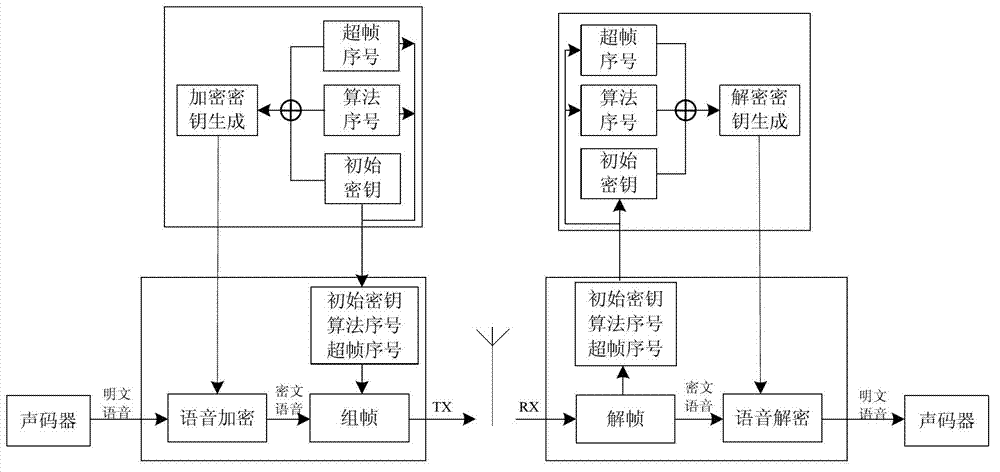
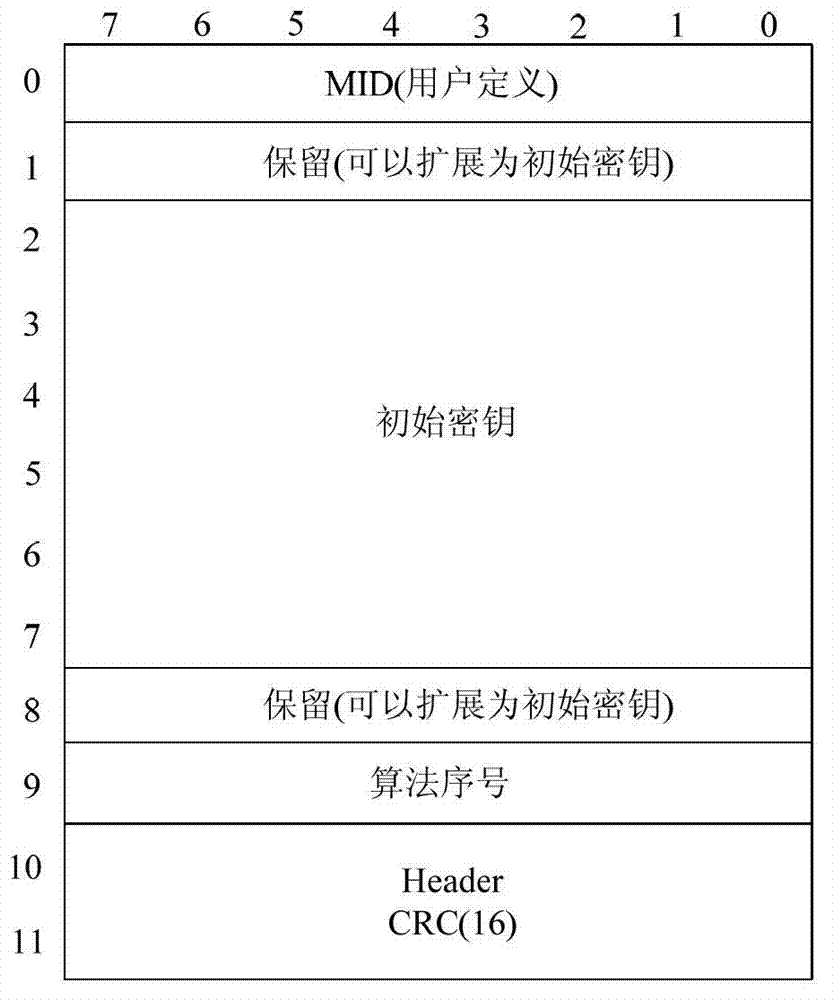
[0034] Compared with a large number of analog point-to-point or trunked intercom communications currently in use, digital communication equipment supports high-security voice and data encryption in addition to high language clarity, high spectrum utilization, and convenient data service functions. Functionality is one of the more prominent and valuable features out there. Utilizes various encryption algorithms recognized as the safest, such as AES, ARC4 and DES, etc., to make the communication process more confidential. However, in the voice encryption process of the communication terminal adopting the DMR standard or other similar double-slot TDMA standards, a part of the effective voice load is required to transmit the encryption and decryption algorithm parameters end-to-end. There are two weaknesses in this processing: 1. Since these encryption parameters occupy a certain amount of effective voice load, a certain amount of voice data needs to be covered, which affects the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com