Communication method, system and equipment based on security gateway
A technology of a security gateway and a communication method, applied in the field of communication methods, systems and equipment based on a security gateway, can solve the problems of high business pressure on the system gateway and core network, and achieve the effect of reducing business pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
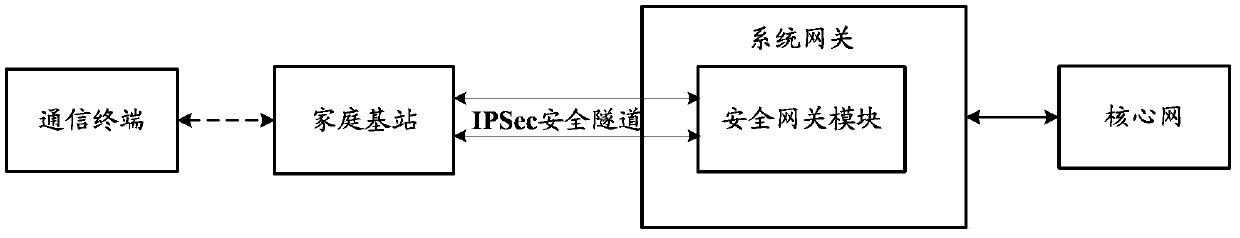
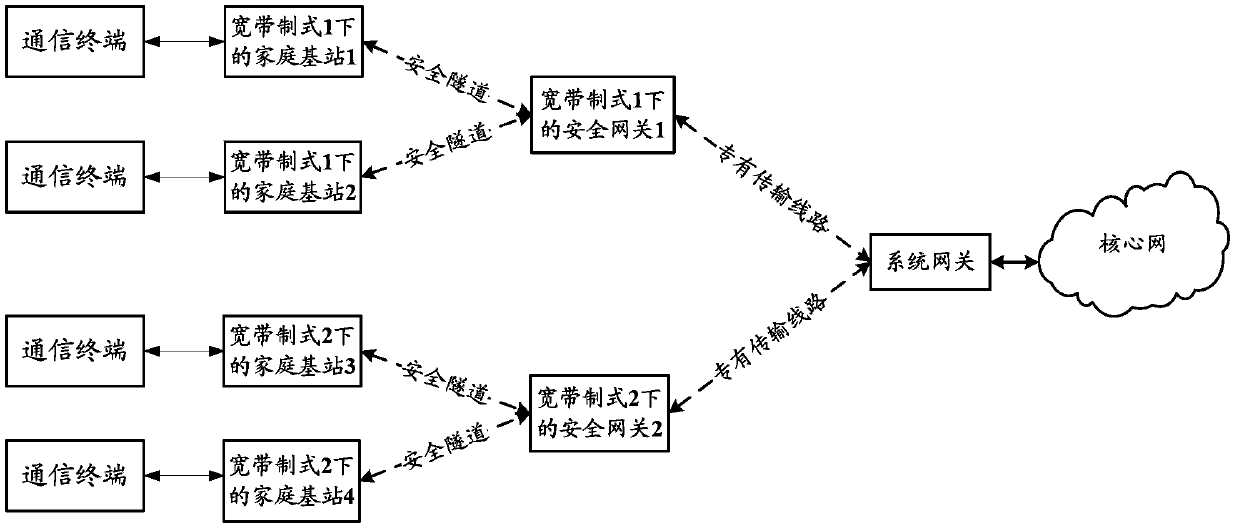
[0033] Such as image 3 As shown, it is a schematic diagram of the architecture of the communication system based on the security gateway in Embodiment 1 of the present invention. image 3 In the system architecture shown, the communication terminal accesses the home base station through the air interface; a secure tunnel is established between the home base station and the security gateway, and the security tunnel can be used for communication; the security gateway is independent of the system gateway, and the security gateway uses a proprietary transmission The line is connected to the system gateway; the system gateway is connected to the core network through the switch.
[0034] The system architecture is described in detail below:
[0035] Take femtocell 1 and femtocell 2 in broadband standard 1 connecting to security gateway 1 in broadband standard 1, femtocell 3 and femtocell 4 in broadband standard 2 to access security gateway 2 in broadband standard 2 as an example. ...
Embodiment 2
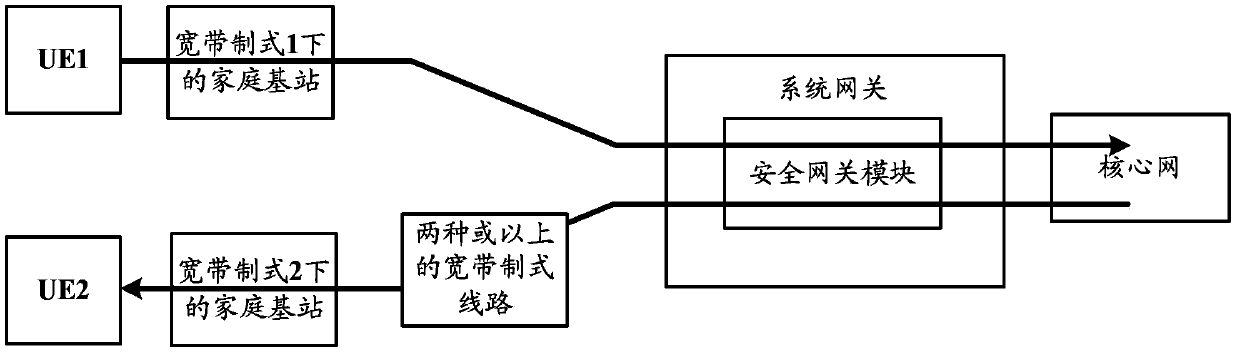
[0046] Assuming that the broadband standard of the security gateway in the second embodiment and the third embodiment is the same as the broadband standard of each home base station that has established a security tunnel with the security gateway, it is avoided that when the home base station accesses a security gateway of a different broadband standard, the The communication data packets transmitted by the home base station need to pass through multiple devices to reach the security gateways of different broadband standards, aggravating the problems of communication data packet delay and packet loss.
[0047] Such as Figure 4 As shown, it is a schematic diagram of the steps of the communication method based on the security gateway in Embodiment 2 of the present invention, and the method mainly includes the following steps:
[0048] Step 101: the security gateway receives the communication data packet sent by the source communication terminal through the accessed source home ...
Embodiment 3
[0058] Such as Figure 5 As shown, it is a schematic diagram of the steps of the communication method based on the security gateway in the third embodiment of the present invention, and the method mainly includes the following steps:
[0059] Step 201: The security gateway receives the communication link information sent by the core network.
[0060] The communication link information is generated by the core network when a communication link is established between the source communication terminal and the target communication terminal, and the communication link information includes the source communication terminal identifier, the source home base station identifier, the target communication terminal identifier, and Target Femtocell ID.
[0061] Take the voice call service between the source communication terminal (called UE1) and the target communication terminal (called UE2) as an example, assuming that UE1 is the calling terminal, accessing the source home base station, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com