IGMP Snooping realizing method of ONU based on VLAN
An implementation method and core technology, applied in multiplexing system selection devices, digital transmission systems, electrical components, etc., can solve the problems of IGMPSnooping function failure and failure to take into account
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
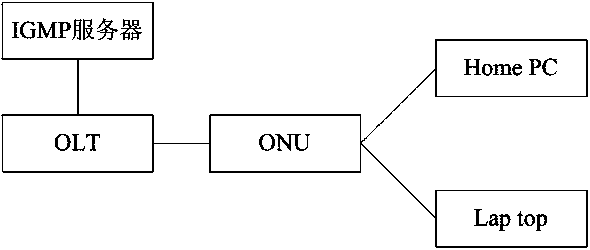
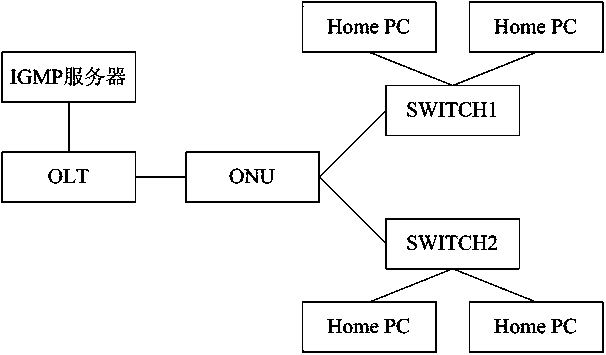
[0021] Embodiment 1, this embodiment provides a kind of similar as figure 2 The implementation method of IGMP Snooping of VLAN in the home network of the shown fiber-to-the-home topology. The method of the present invention will be described in detail below.
[0022] In this embodiment, another hook function igmp_snooping_handler needs to be hung in the hook function br_handle_frame_finish of the hook point NF_BR_PRE_ROUTING in the kernel netfilter. In addition, an igmp_snooping kernel module needs to be implemented. When the igmp_snooping kernel module is initialized, the actual processing function br_handle_igmp_snooping(struct sk_buff *skb) of igmp_snooping is assigned to igmp_snooping_handler.
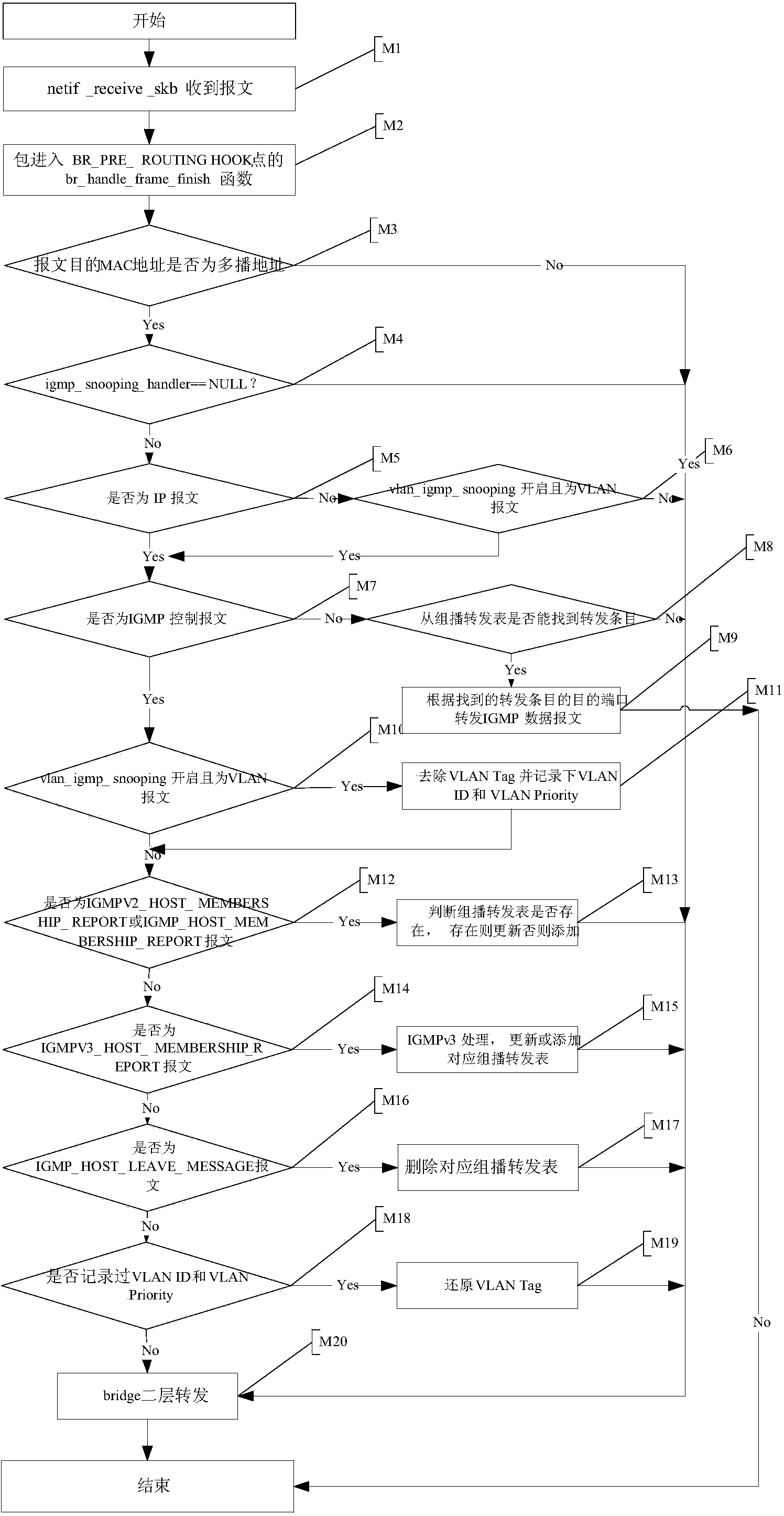
[0023] like image 3 As shown in the figure, it is a flowchart of the implementation of IGMP Snooping with VLAN, including the following steps:
[0024] Steps M1 to M8 in this embodiment are to judge that the received message is an IGMP control message, and only the IGMP contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com