Terminal locking and unlocking method and terminal locking and unlocking system
A locking system and terminal technology, applied in electrical components, wireless communication, network data management, etc., can solve problems such as economic loss of cost users, complex security software, personal information leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
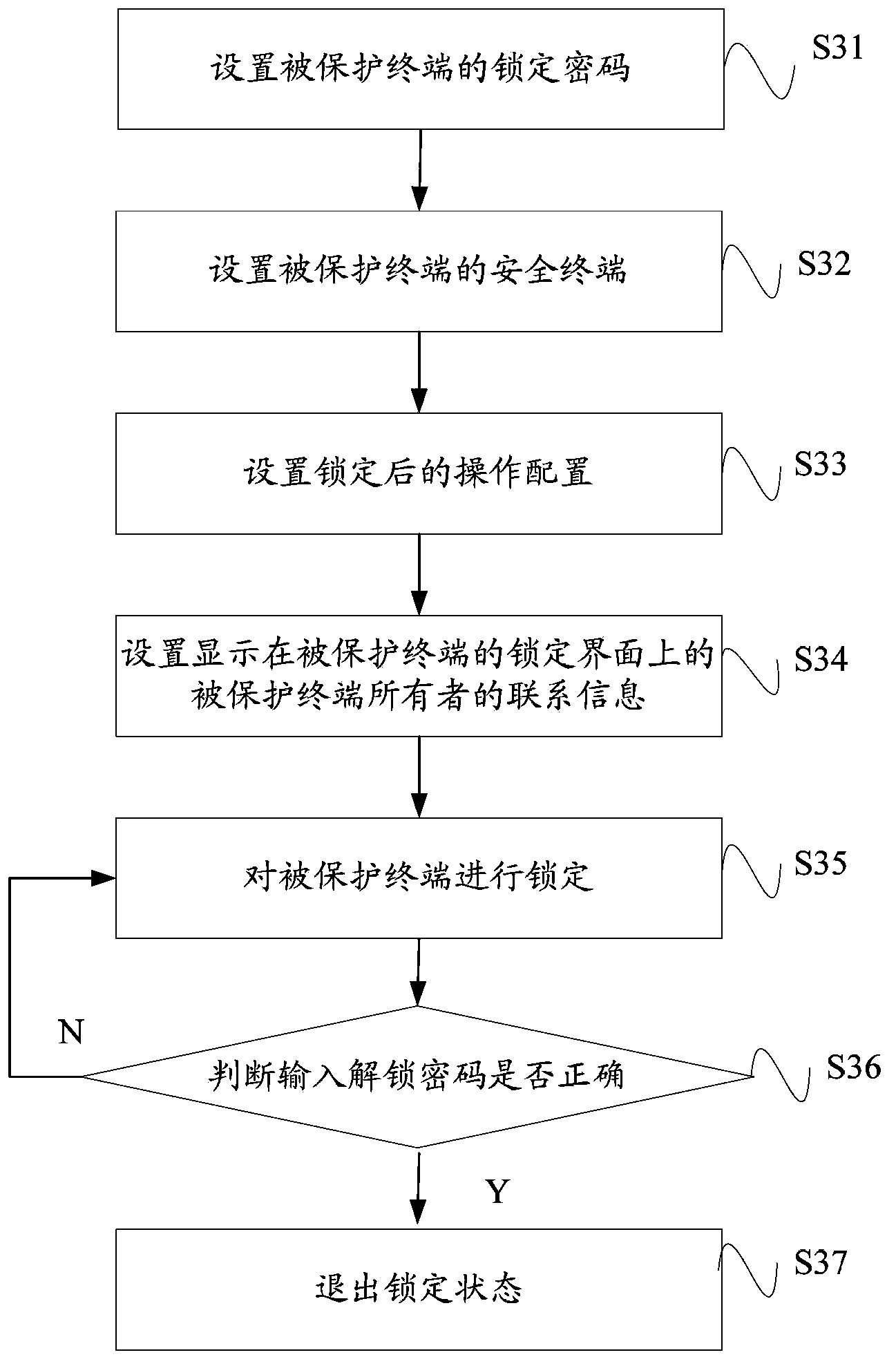
[0105] The present invention provides a terminal locking method. The locking in this embodiment and subsequent embodiments refers to locking the protected terminal such as a mobile phone, that is, the user is not allowed to enter any operation interface of the protected terminal, and only the locked terminal is displayed. Prompt information, this embodiment specifically includes the following steps:
[0106] When the preset locking condition is met, the protected terminal is locked, so that when the locking condition is satisfied, the protected terminal is locked to protect the personal information therein.
[0107] Preferably, the locking condition is that the protected terminal does not have a SIM card installed; or the locking condition is that the replaced SIM card on the protected terminal is inconsistent with the initial SIM card; or the locking condition is that the protected terminal The protected terminal does not have an SD card installed; or the locking condition is...
Embodiment 2
[0120] The present invention provides a method for unlocking a terminal. Unlocking in this embodiment and subsequent embodiments refers to releasing the locked state of a protected terminal such as a mobile phone and entering a normal operation mode. This embodiment specifically includes the following steps:
[0121] The protected terminal is unlocked when the preset unlocking condition is met, so that when the unlocking condition is met, the user with unlocking authority can unlock the protected terminal.
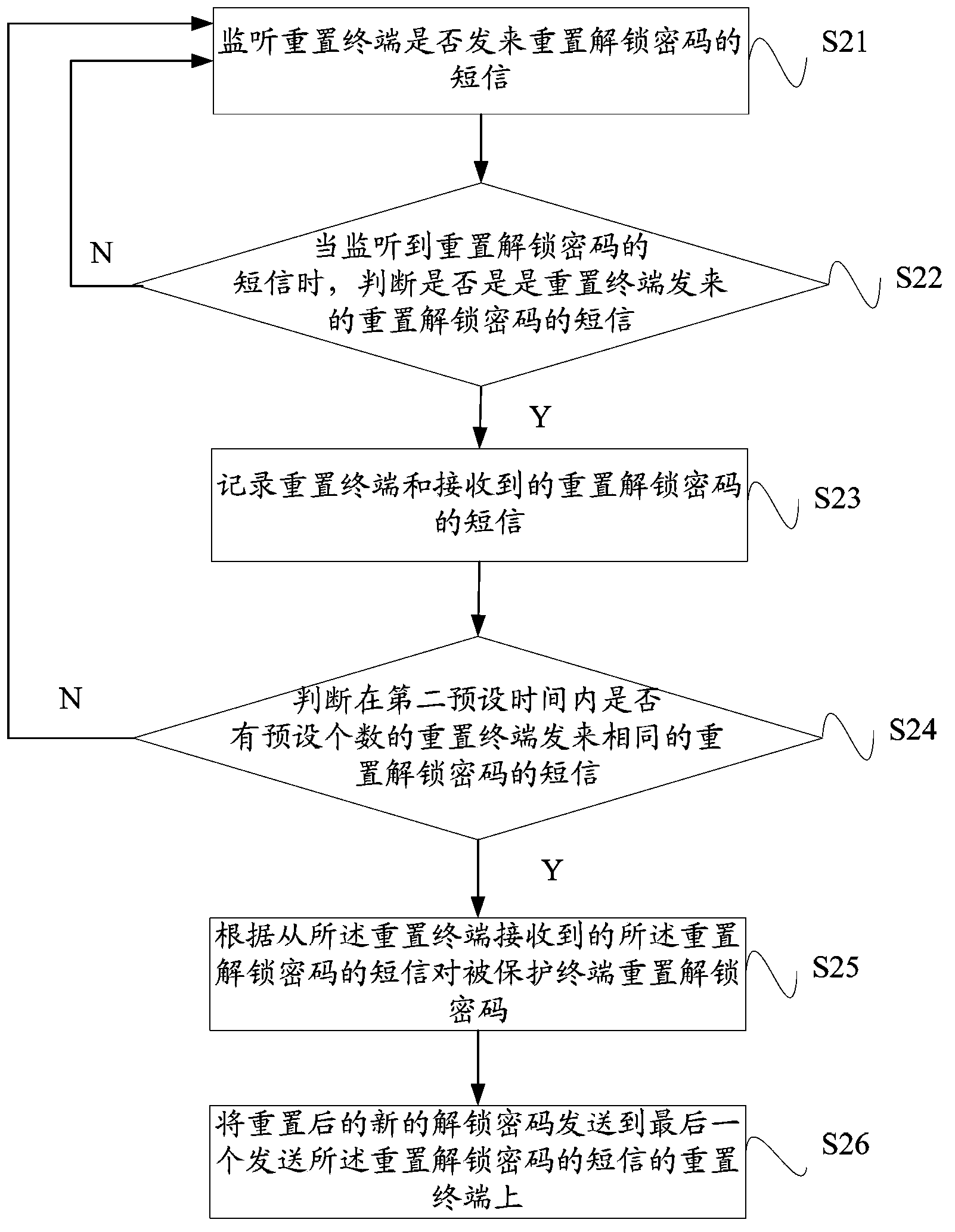
[0122]Preferably, the unlocking condition is that the SIM card of the protected terminal is restored to the initial SIM card, or the unlocking condition is that the SD card of the protected terminal is restored to the initial SD card, or the unlocking condition is In order to receive a preset unlocking instruction from the security terminal, or the unlocking condition is to receive a preset unlocking password input by the user, the step of unlocking the protected terminal w...
Embodiment 3
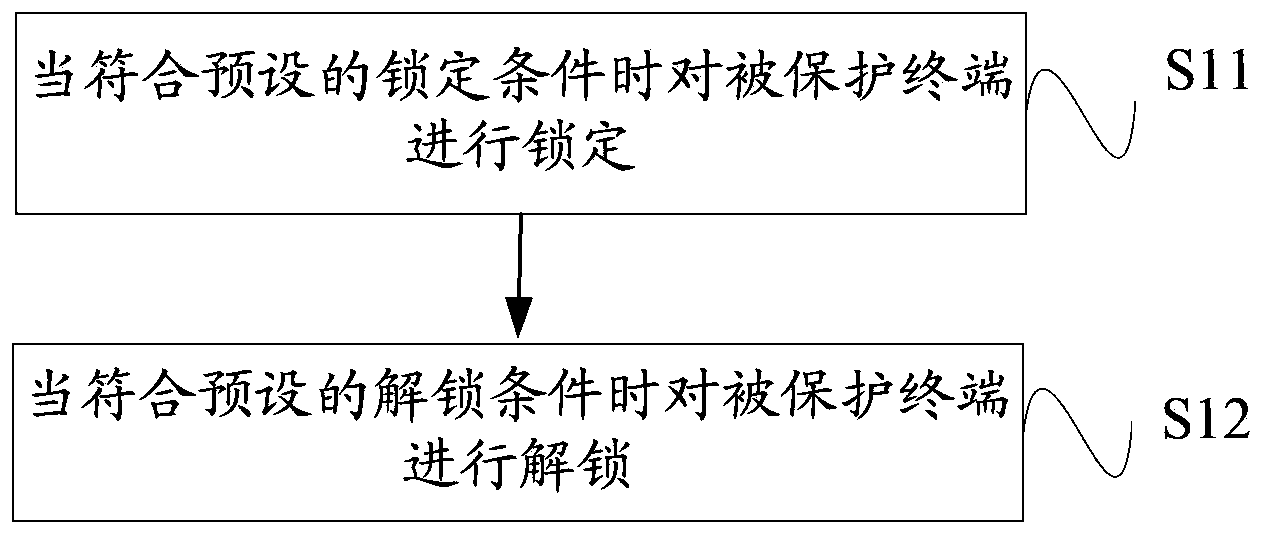
[0128] Such as figure 1 As shown, the present invention provides a terminal locking and unlocking method. The locking in this embodiment and subsequent embodiments refers to locking the protected terminal such as a mobile phone, that is, the user is not allowed to enter any operation interface of the protected terminal, and only the protected terminal is displayed. The prompt message that the protected terminal has been locked; unlocking refers to releasing the locked state of the protected terminal such as a mobile phone and entering the normal operation mode. This embodiment specifically includes the following steps:
[0129] Step S11, lock the protected terminal when the preset locking condition is met, so that when the locking condition is satisfied, lock the protected terminal to protect the personal information therein;
[0130] Step S12, unlocking the protected terminal when the preset unlocking condition is met, so that when the unlocking condition is satisfied, the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com