Android malicious software detection method based on method call graph
A malicious code detection and malicious technology, applied in the field of mobile Internet, can solve the problem that new unknown malware has no ability to detect and kill, and achieve the effect of improving identification and killing capabilities, security scanning and protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
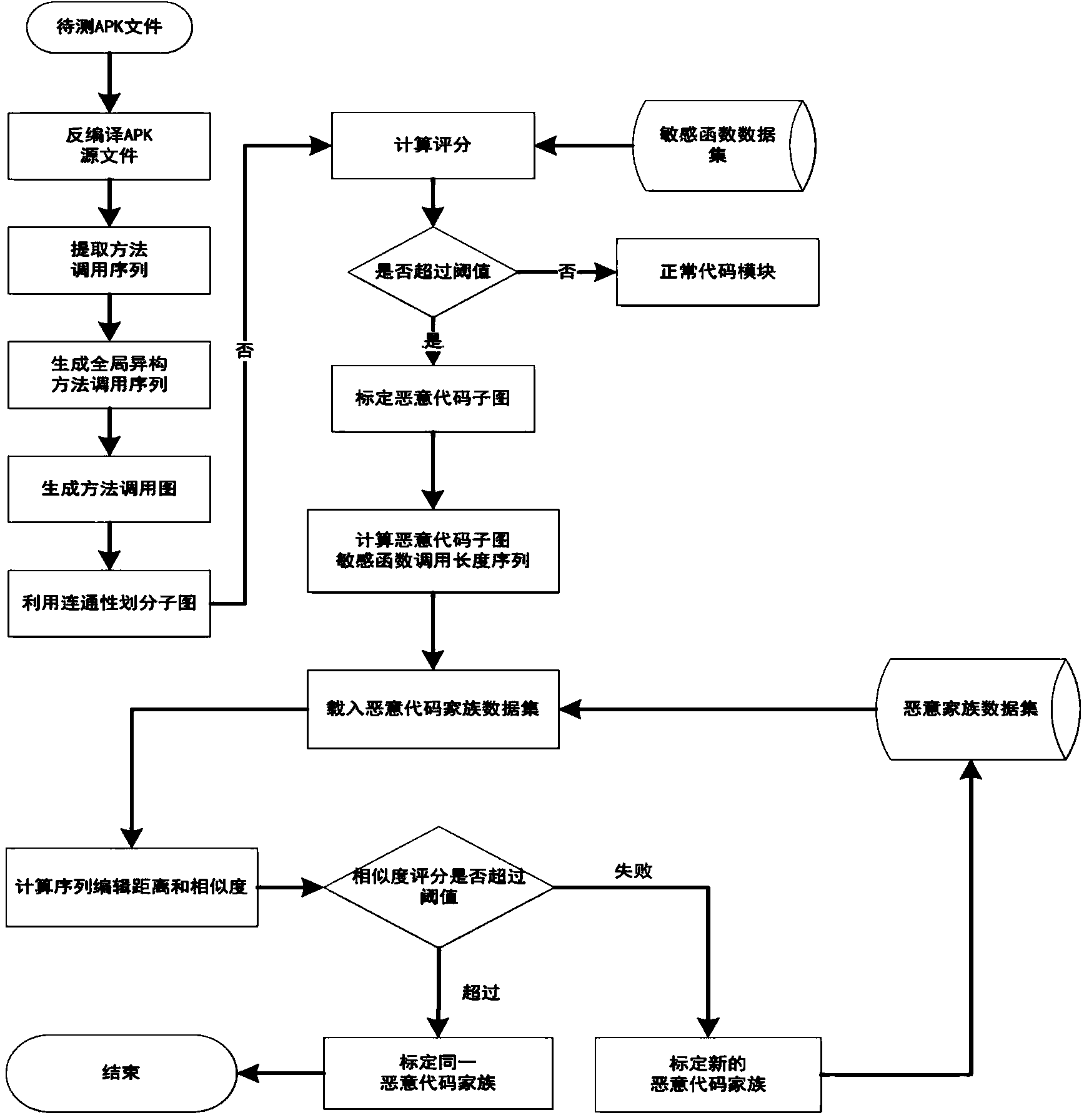
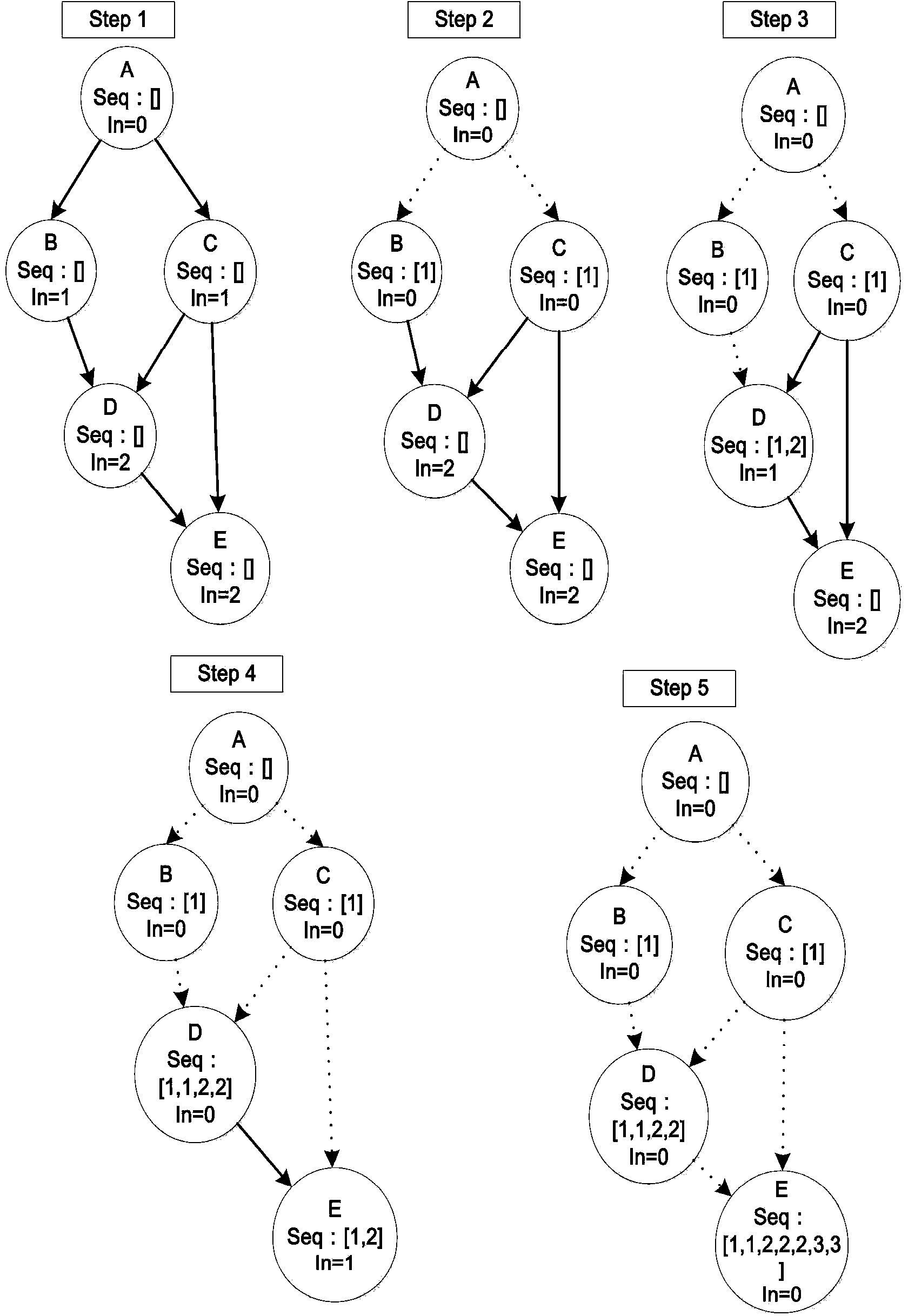
[0023] Such as figure 1 As shown, the present invention constructs Apk software heterogeneous method call graph, calibrates sensitive functions, and then implements location and family classification of Android malicious codes in a graph correlation manner. In a specific embodiment, the detection method specifically includes the following steps:
[0024] The first step is to collect malicious samples of Android software, conduct manual analysis, and extract sensitive functions.
[0025] The sensitive functions include seven categories: network, short message, phone, file operation, device operation, code execution, and geographic location. In one embodiment, the sensitive functions have a total of 31 sensitive api function interfaces, as shown in Table 1.
[0026] Table 1 Sensitive functions and examples of sensitive receivers
[0027] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com