Recommendation system attack detection method based on time series data
A technology of recommendation system and attack detection, which is used in electrical digital data processing, special data processing applications, computing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The detailed issues involved in the technical solution of the present invention are described in detail below. It should be pointed out that the described embodiments are intended to facilitate the understanding of the present invention, but do not limit it in any way.
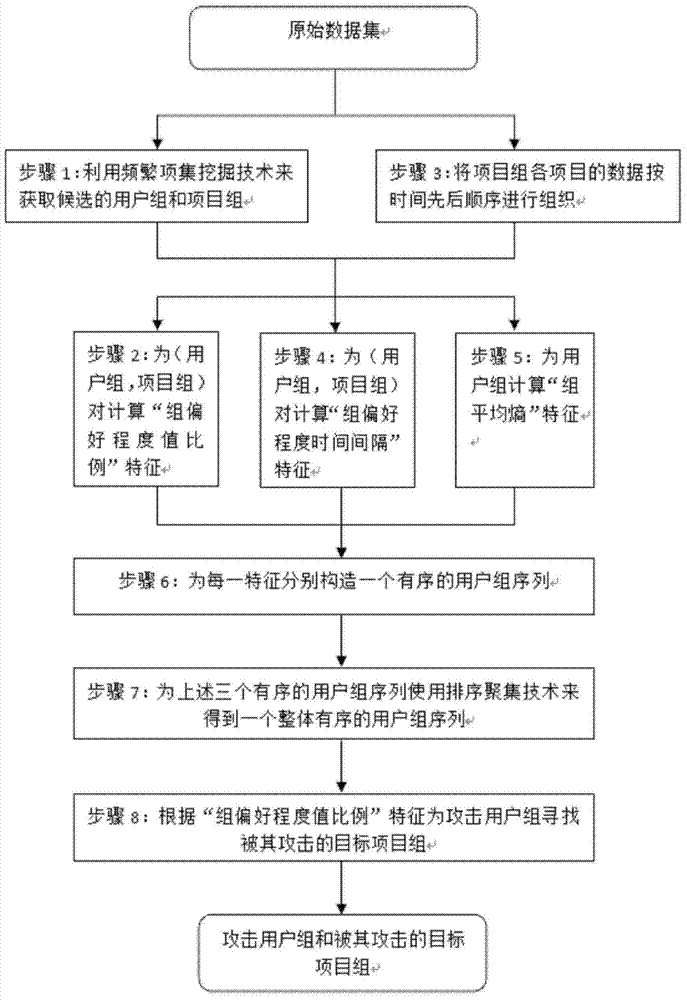
[0019] figure 1 It shows the flowchart of the attack detection method for recommendation system based on time series data proposed by the present invention. Such as figure 1 As shown, the method includes the following steps:
[0020] Step S1 uses the user-item preference data set and frequent itemset mining technology to obtain candidate user groups and candidate item groups;
[0021] Step S2 is based on the user group and item group obtained in the first step, and calculates the "group preference degree value ratio" feature for each pair of user group and item group, which is used to describe the characteristics of the group attack behavior preference degree value;
[0022] Step S3 organizes all th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com