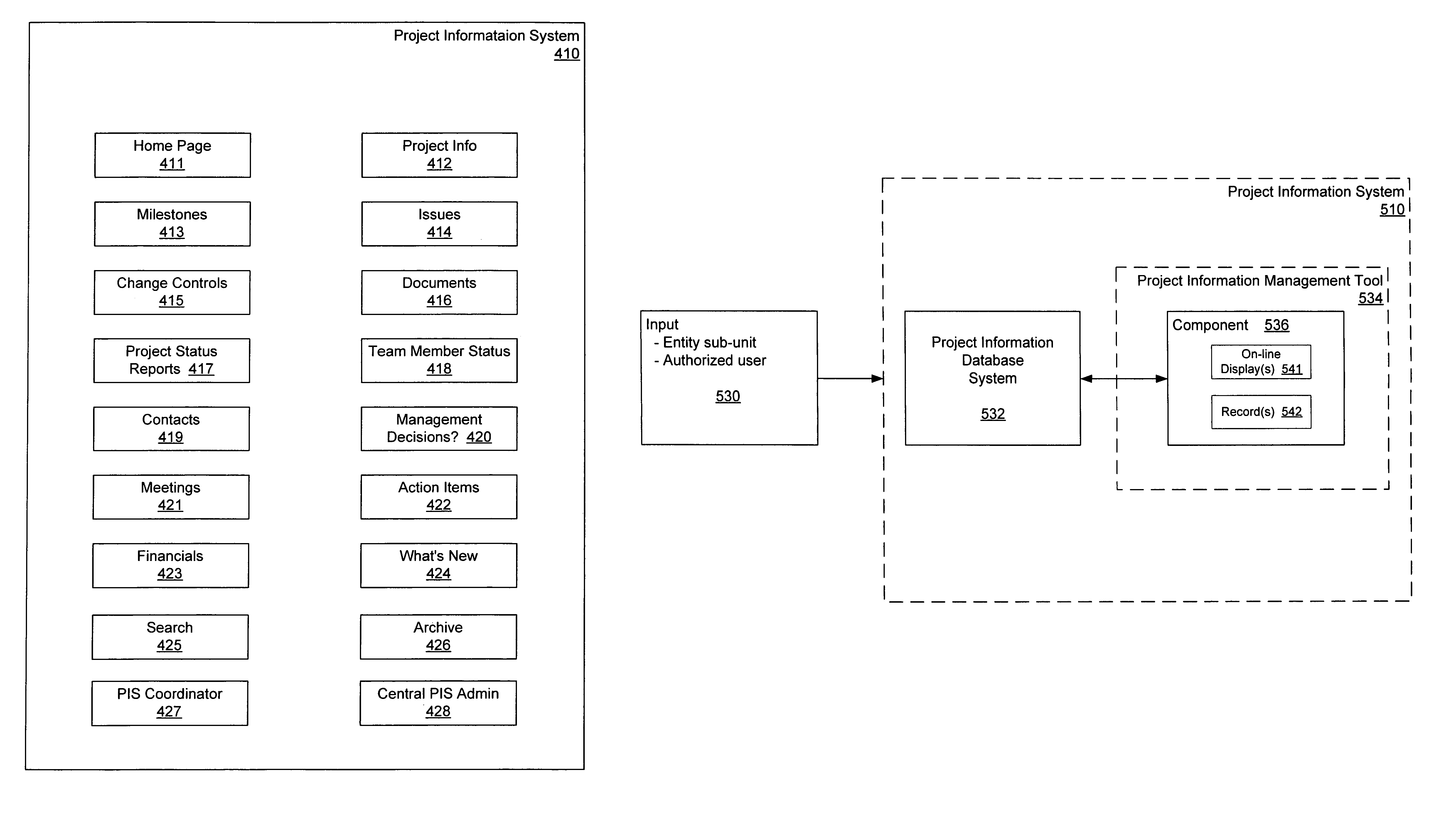
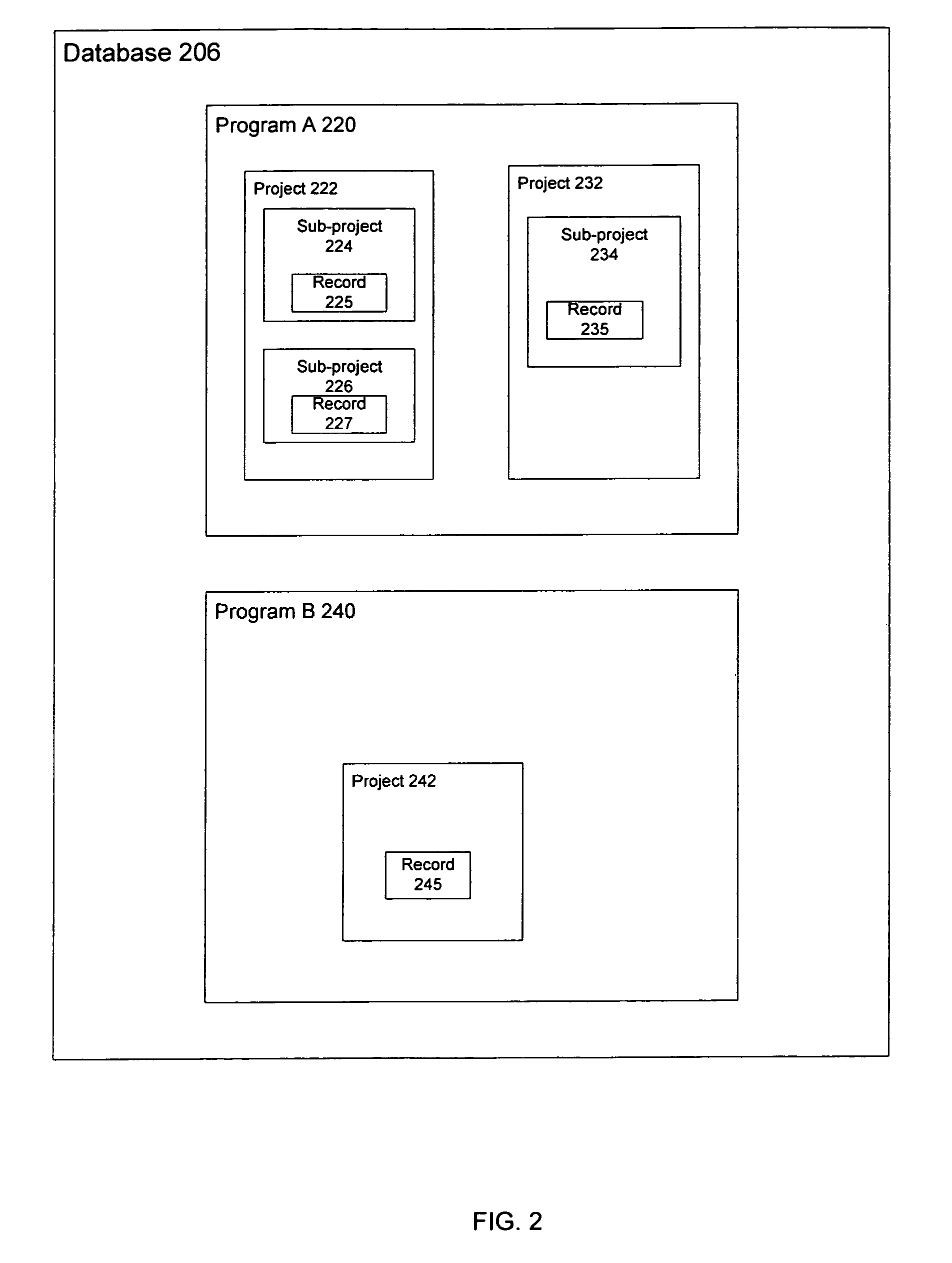
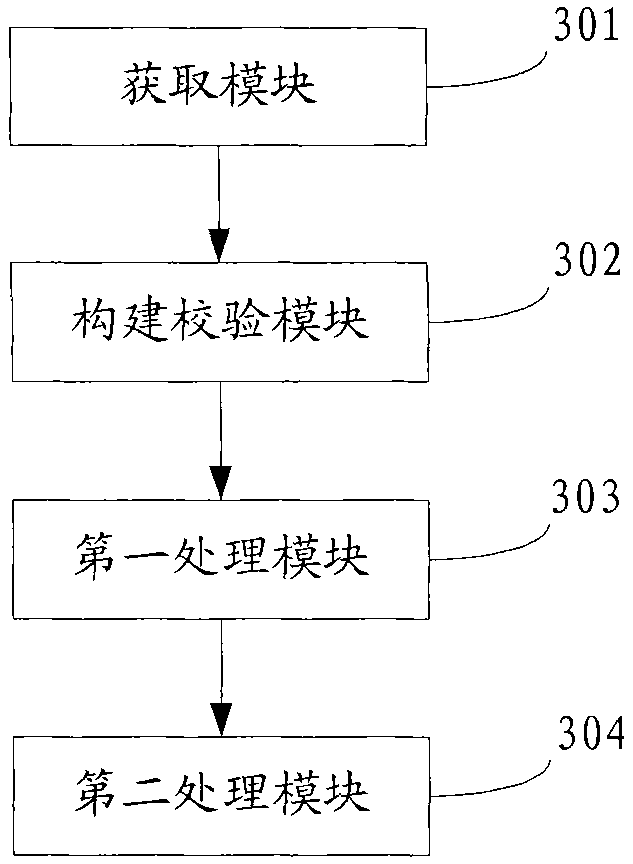
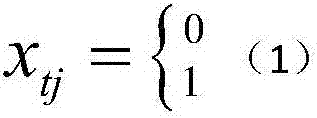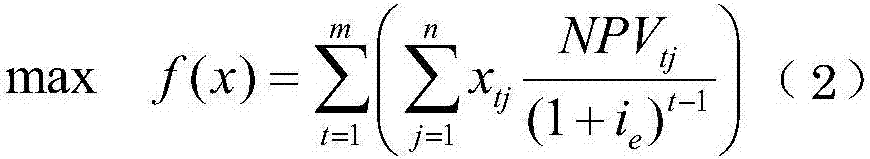Patents
Literature
132 results about "Project group" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
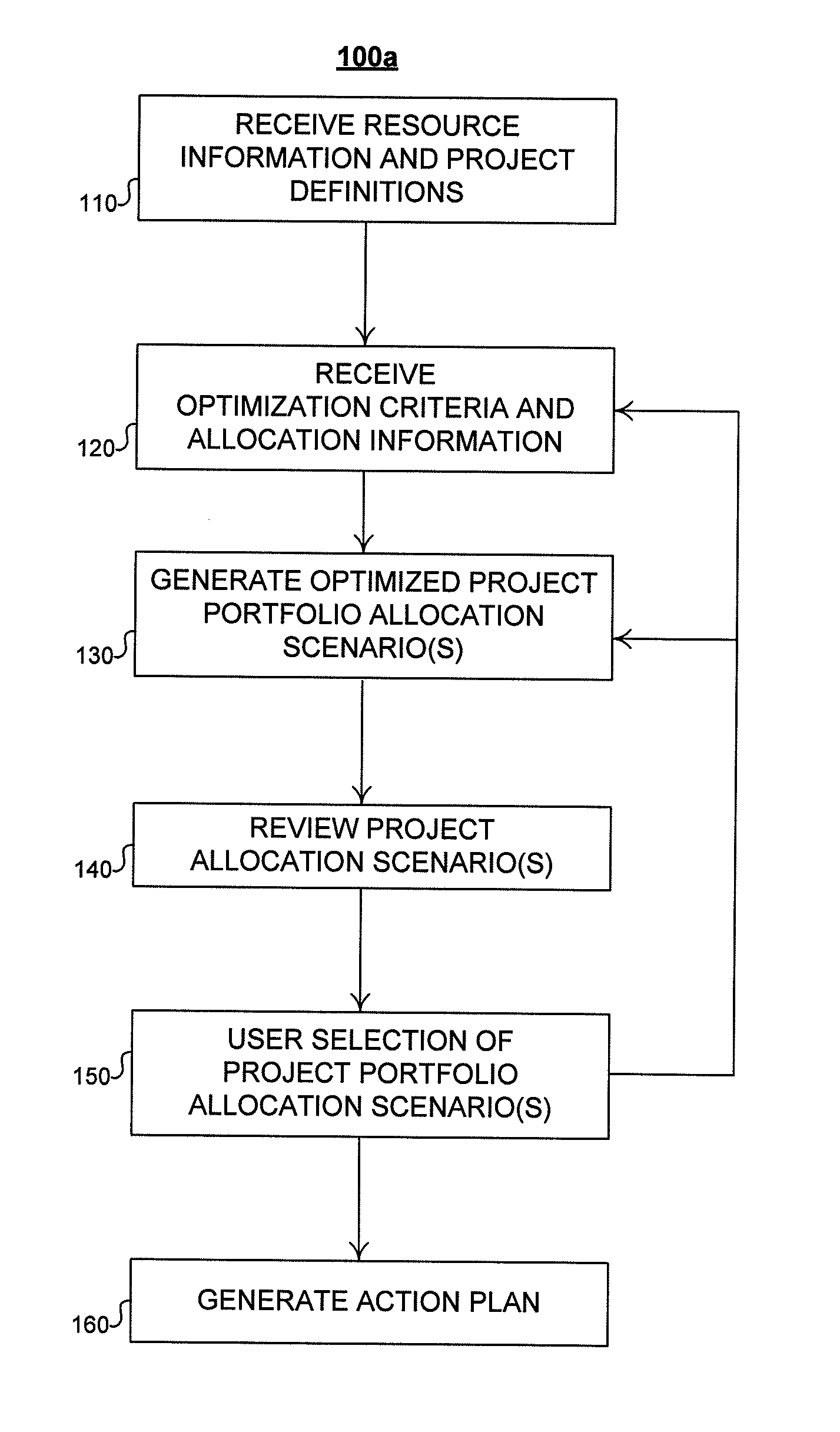
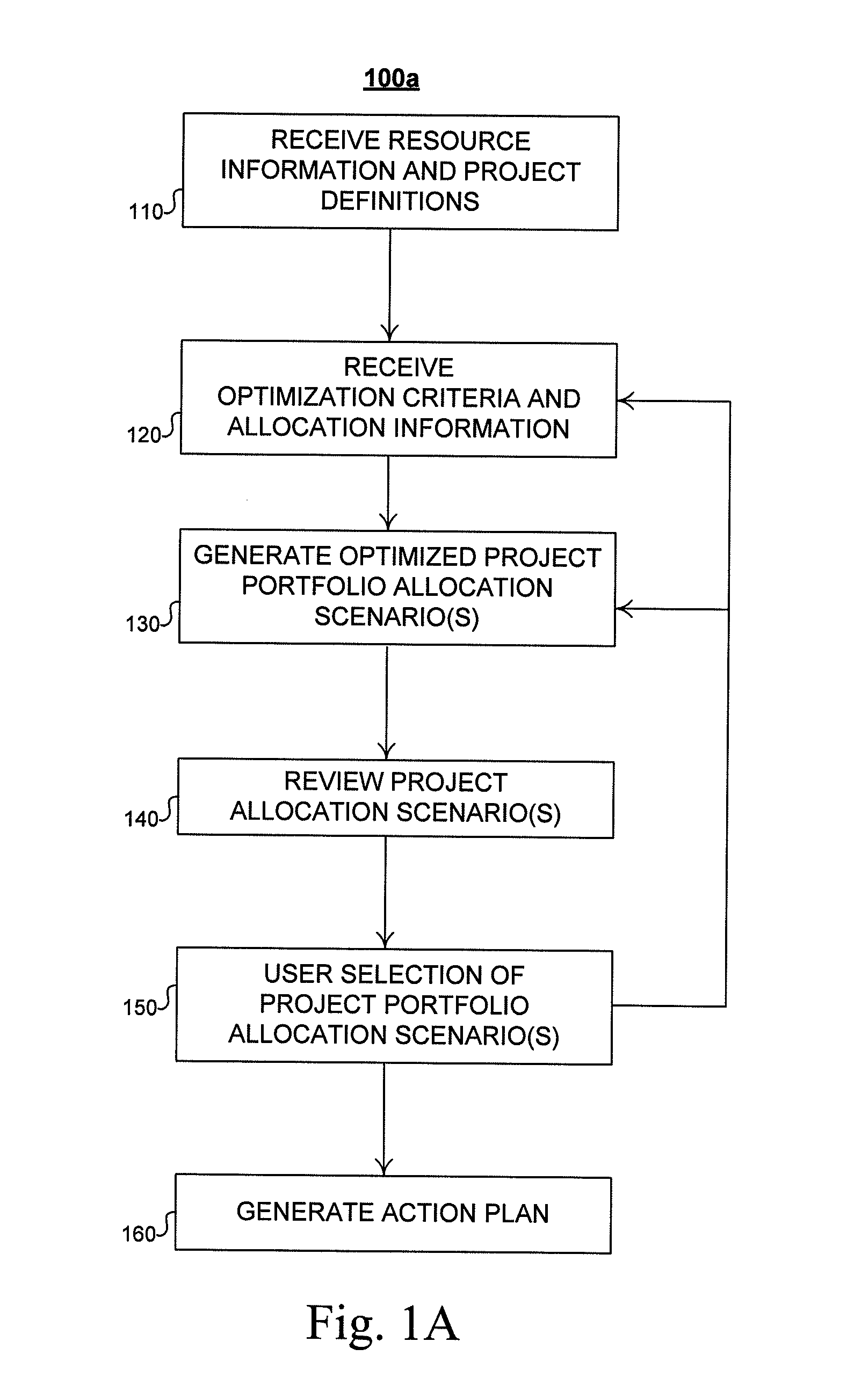
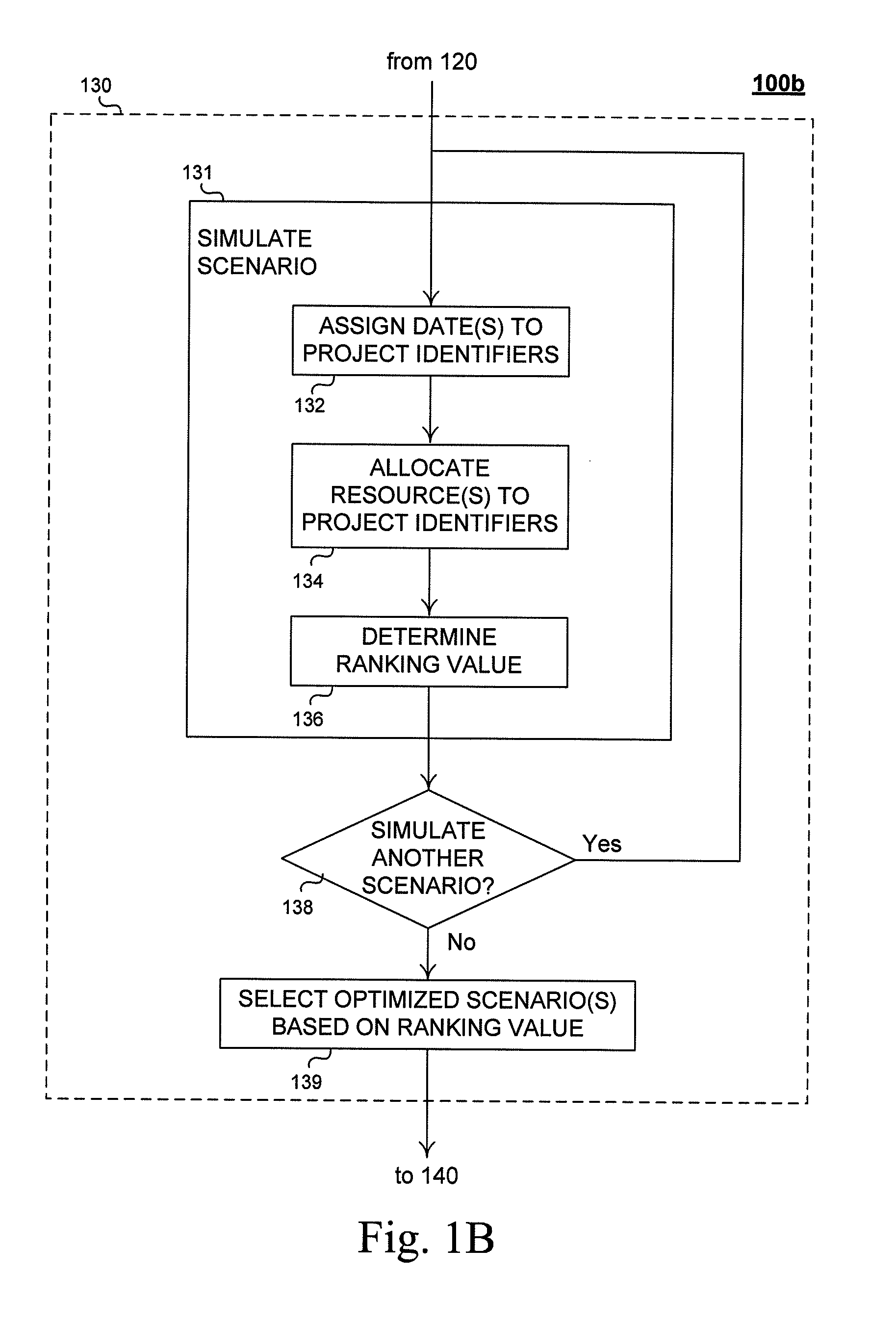
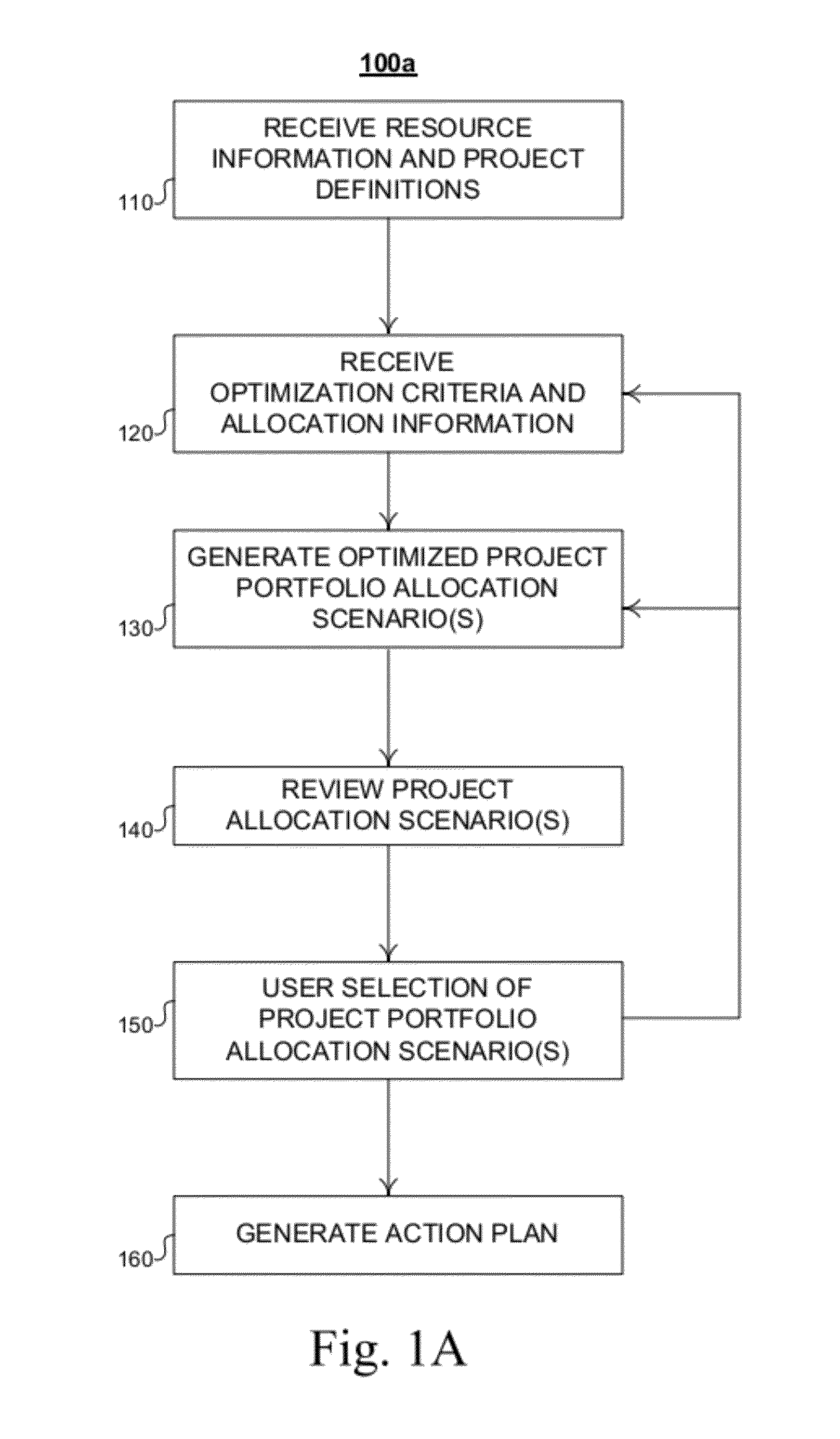
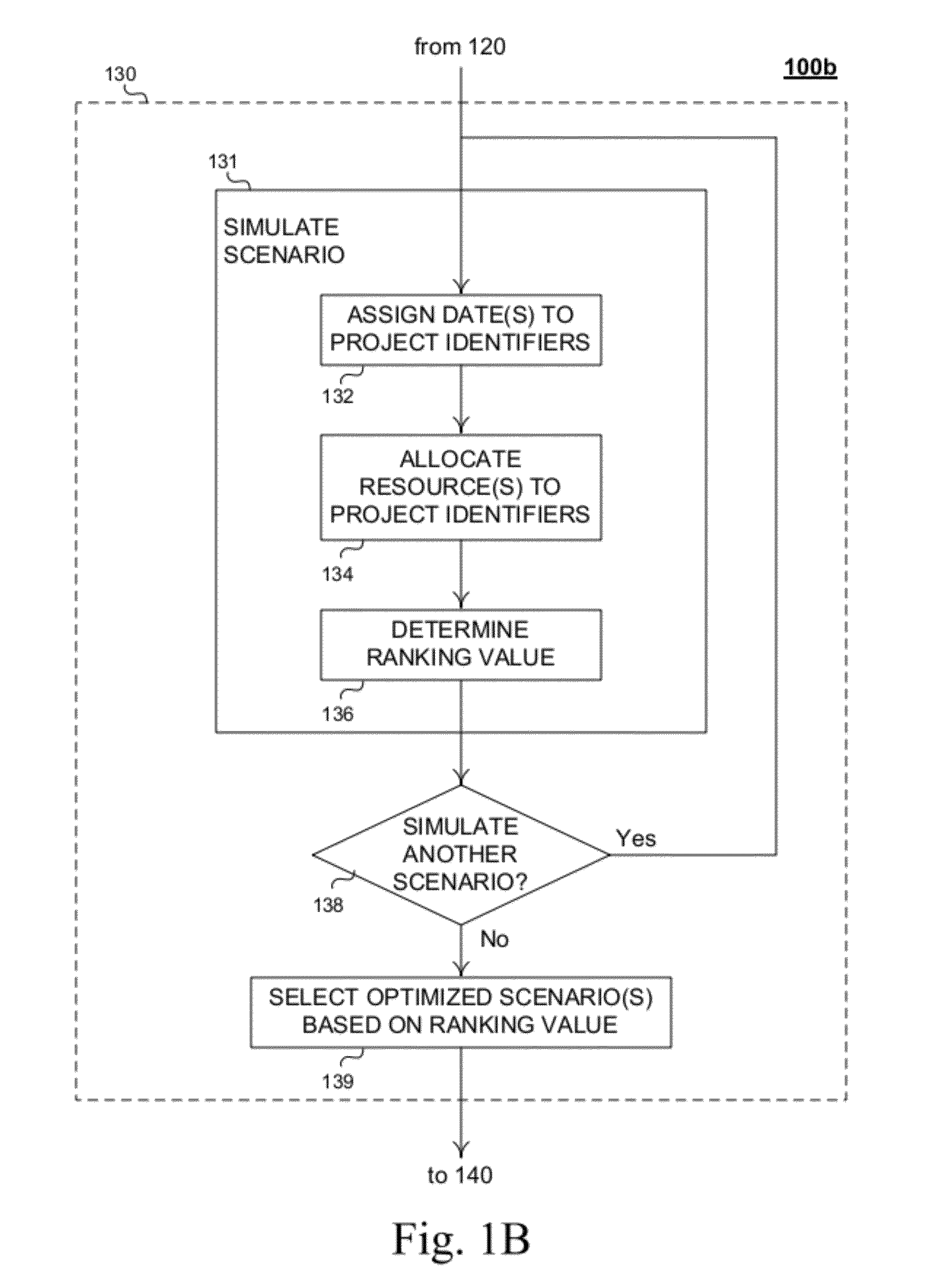
Method and system for allocation of resources in a project portfolio
ActiveUS7991632B1Low costFacilitates potential early cancellationMarket predictionsResourcesACROSS ProjectResource information
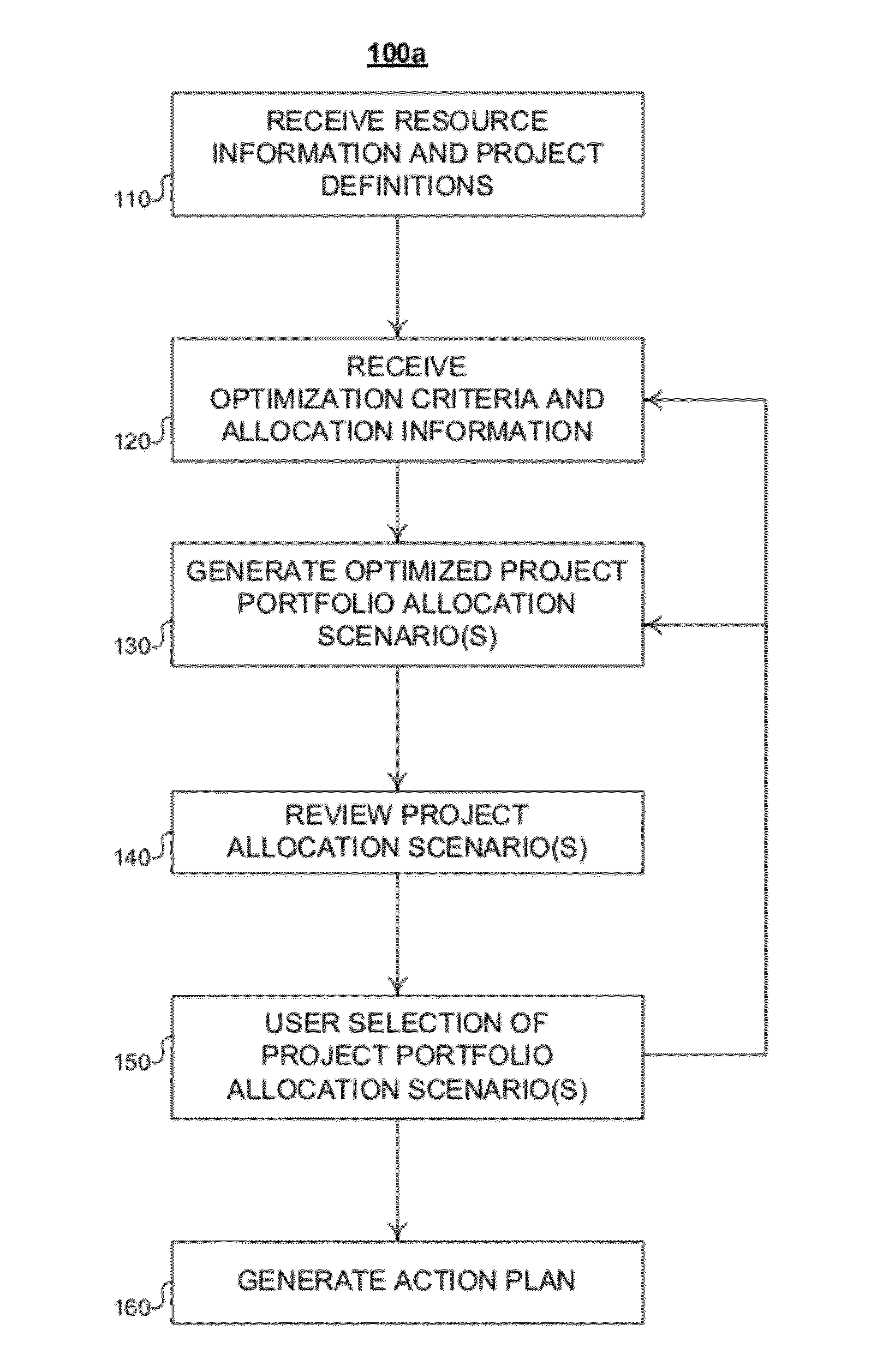
Described are methods and apparatuses, including computer program products, for optimizing allocation of resources across projects in a project portfolio. The method includes receiving, at a computing device, (i) resource information, (ii) a portfolio of project definitions and (iii) one or more portfolio-level optimization criteria. The resource information representing a plurality of resources available for allocation to the projects, and each project definition includes a unique identifier and one or more project-level constraints. The method also includes generating, using the computing device, a plurality of project portfolio allocation scenarios and determining one or more optimized project portfolio allocation scenarios from the plurality of project portfolio allocation scenarios. Each project portfolio allocation scenario satisfies the one or more project-level constraints associated with each project definition. Each optimized project portfolio allocation scenario optimizes a sequence of the projects to satisfy the one or more portfolio-level optimization criteria.
Owner:FMR CORP
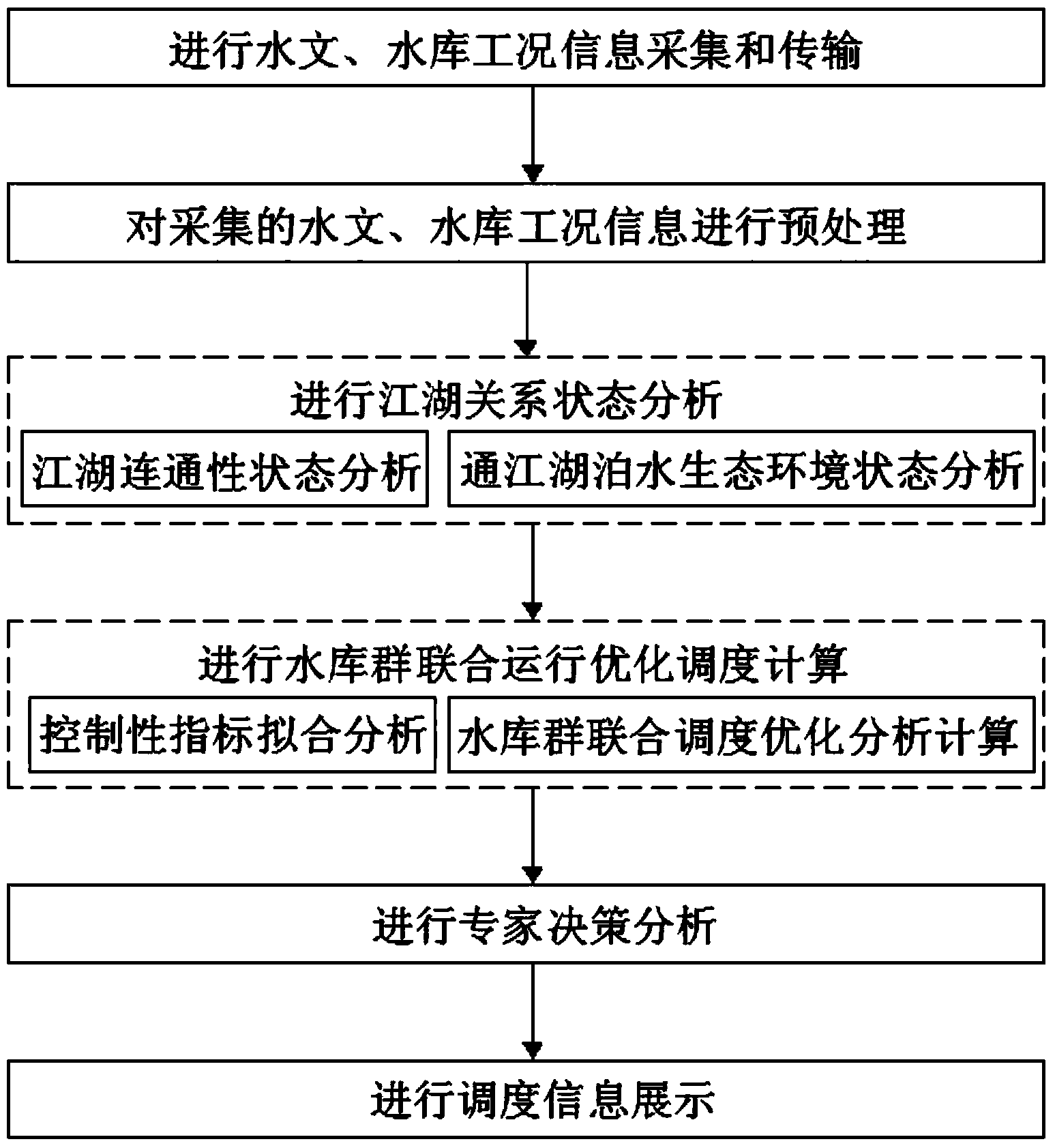
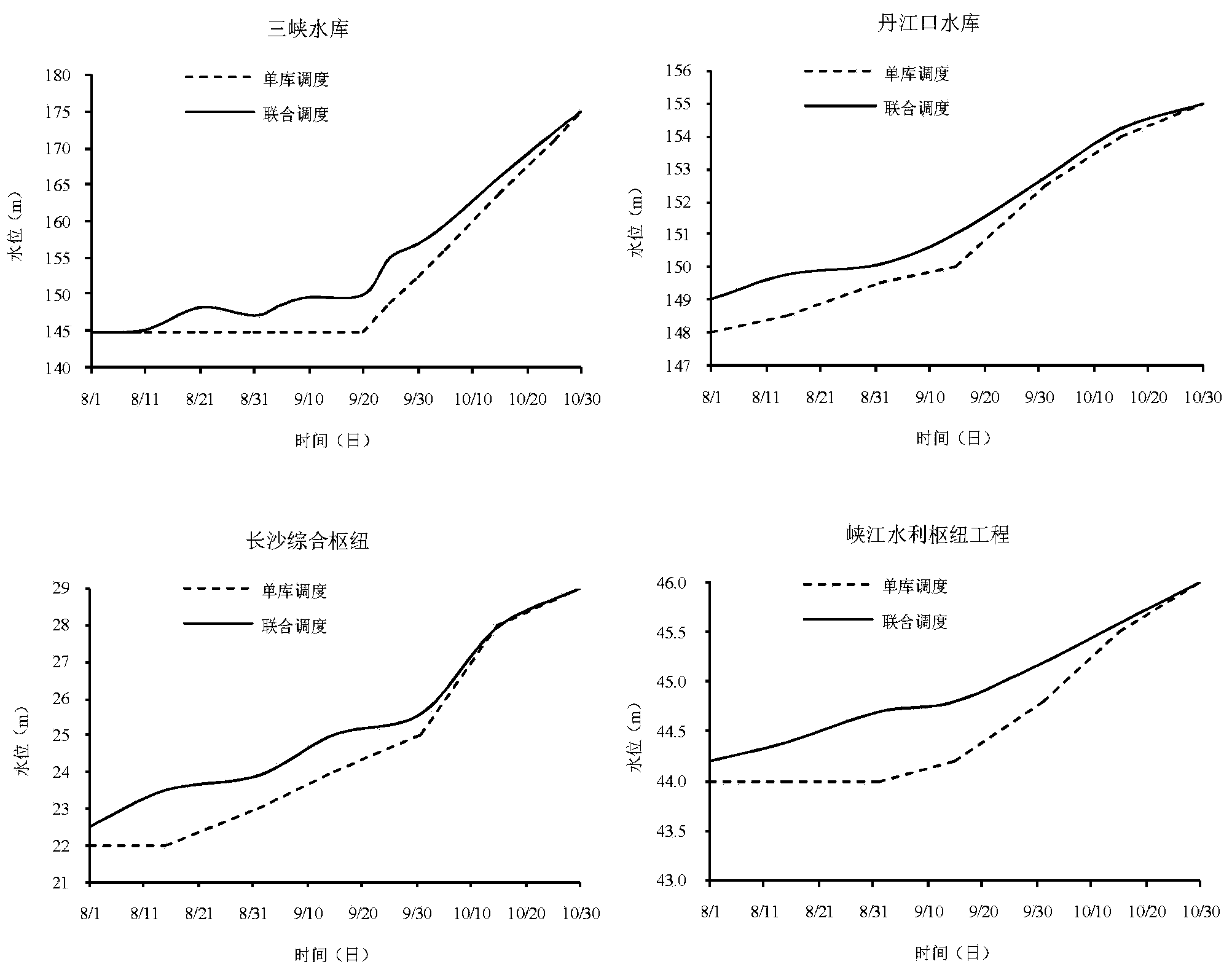
Reservoir group combined operation scheduling system and method for improving river and lake relationship
ActiveCN103679285AOvercoming the Insufficiency of Water Volume RegulationGuarantee the need for water for ecological environment protectionForecastingWater resource assessmentOperation schedulingInformation transmission
The invention discloses a reservoir group combined operation scheduling system and method for improving a river and lake relationship. The system is characterized by comprising a hydrological information acquisition module, a reservoir working condition access module, an information transmission module, a data preprocessing module, a river and lake relationship scheduling and decision-making module and a display terminal module. By the system and method, shortcomings of an existing reservoir scheduling technique are overcome so as to realize the objective of benefiting both rivers and lakes, the river midstream-upstream and river-communicated lake reservoir group combined operation scheduling system and method is in favor of improving the river and lake relationship, multi-objective optimal regulation and control is carried out aiming for controlled hydrology and water ecological parameters for representing the river and lake relationship, and cross-basin, multi-objective and integrated water conservancy project group remote combined regulation and control in favor of improving the river and lake relationship is realized.
Owner:HOHAI UNIV +1
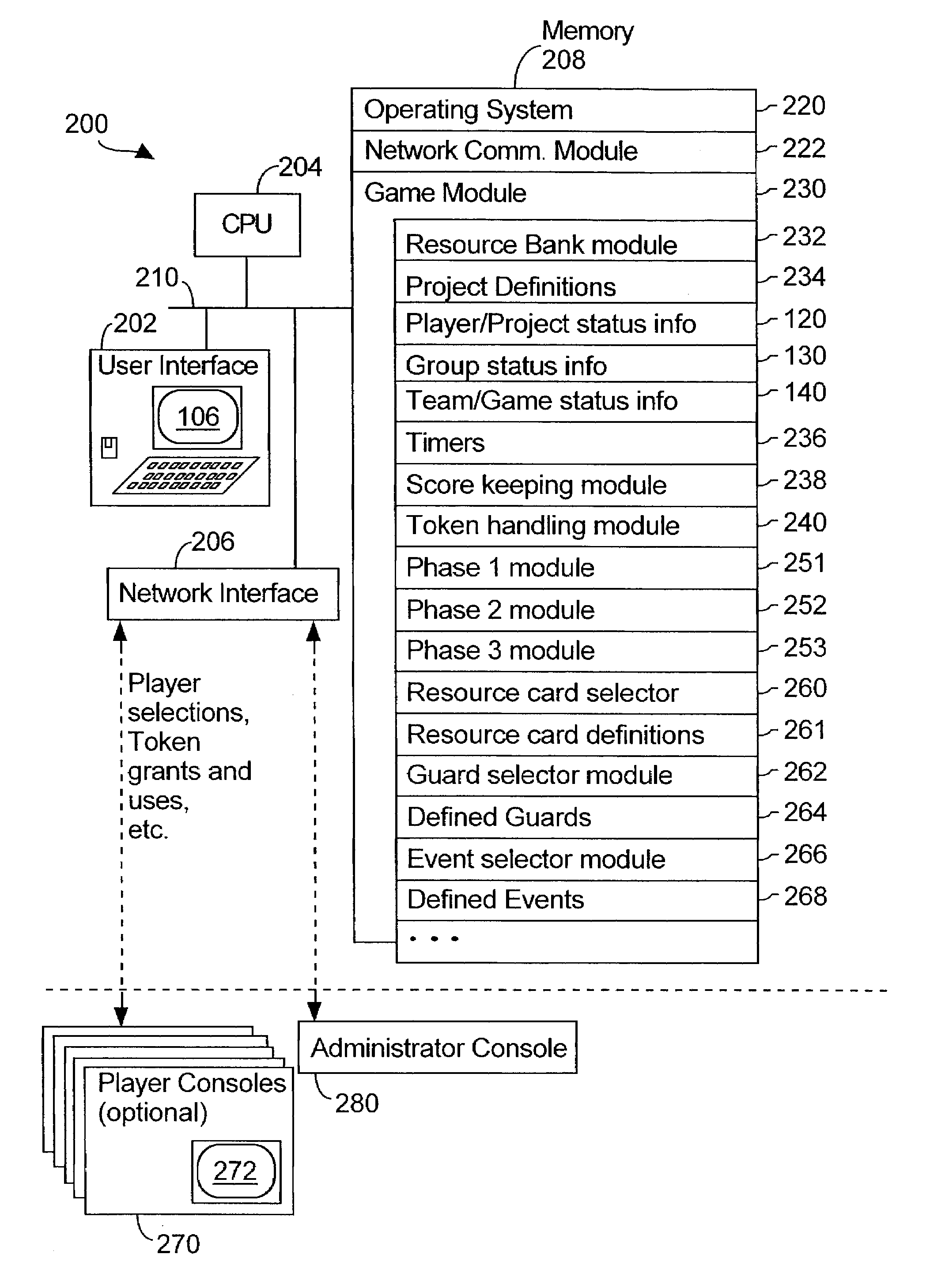
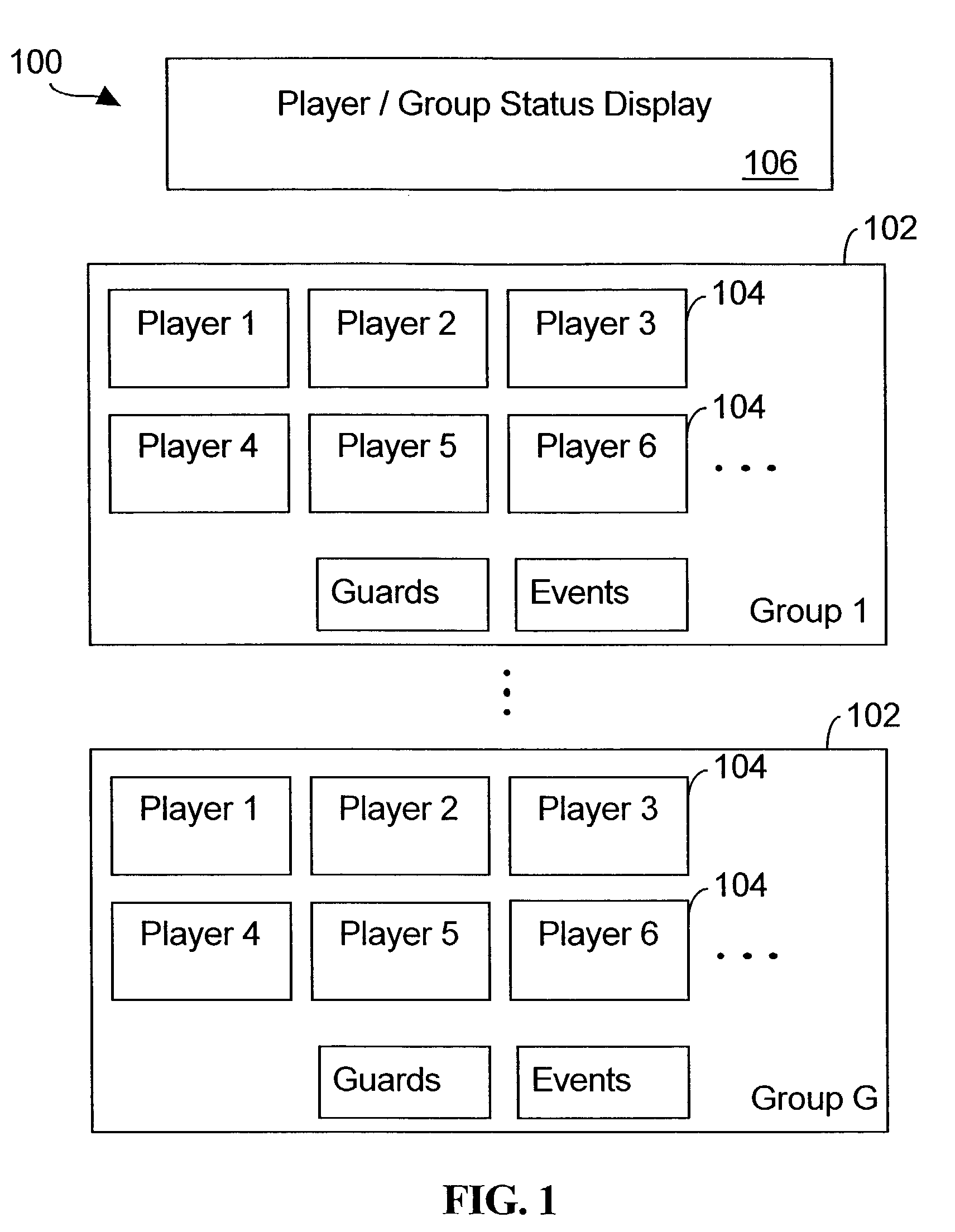
Computer assisted game for teaching cooperative resource allocation and multi-party negotiation skills
A multiple player game has objects corresponding to projects to which resources are allocated by the players of the game. The players include a plurality of groups. A resource bank mechanism determines a bank of resources to be made available to each group of players for allocation to the projects controlled by the players the group. A first game mechanism allows each player to make independent resource allocations to a project controlled by that player. A second game mechanism requires each group of players to make joint resource allocation decisions. A third game mechanism requires a plurality of the groups to make team level decisions affecting resource allocations to projects controlled by the groups of players. A scoring mechanism assigns a respective project score to each project of each group, a group score to each group of projects, and a team score to the plurality of projects.
Owner:AGILEMATH
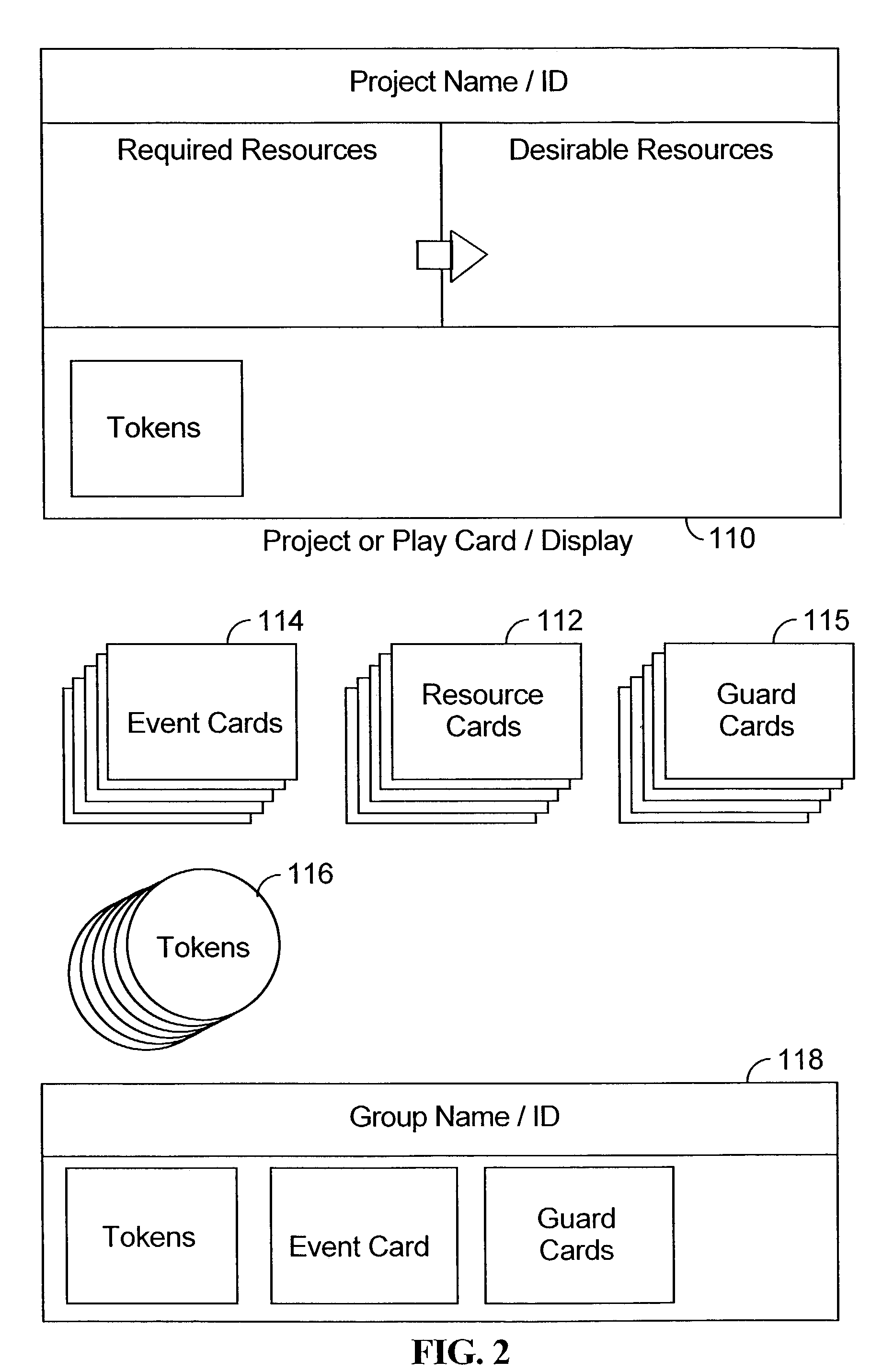
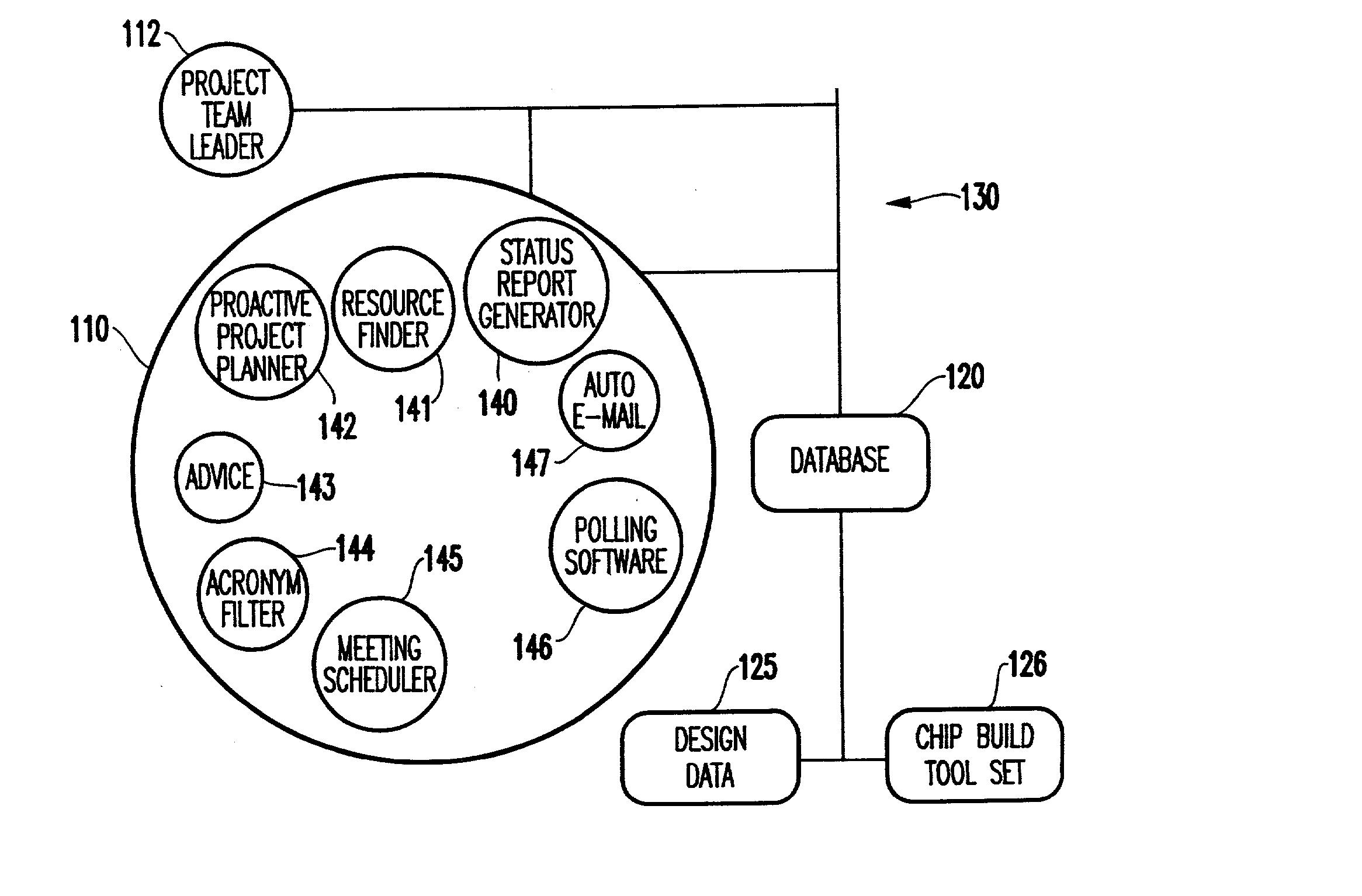
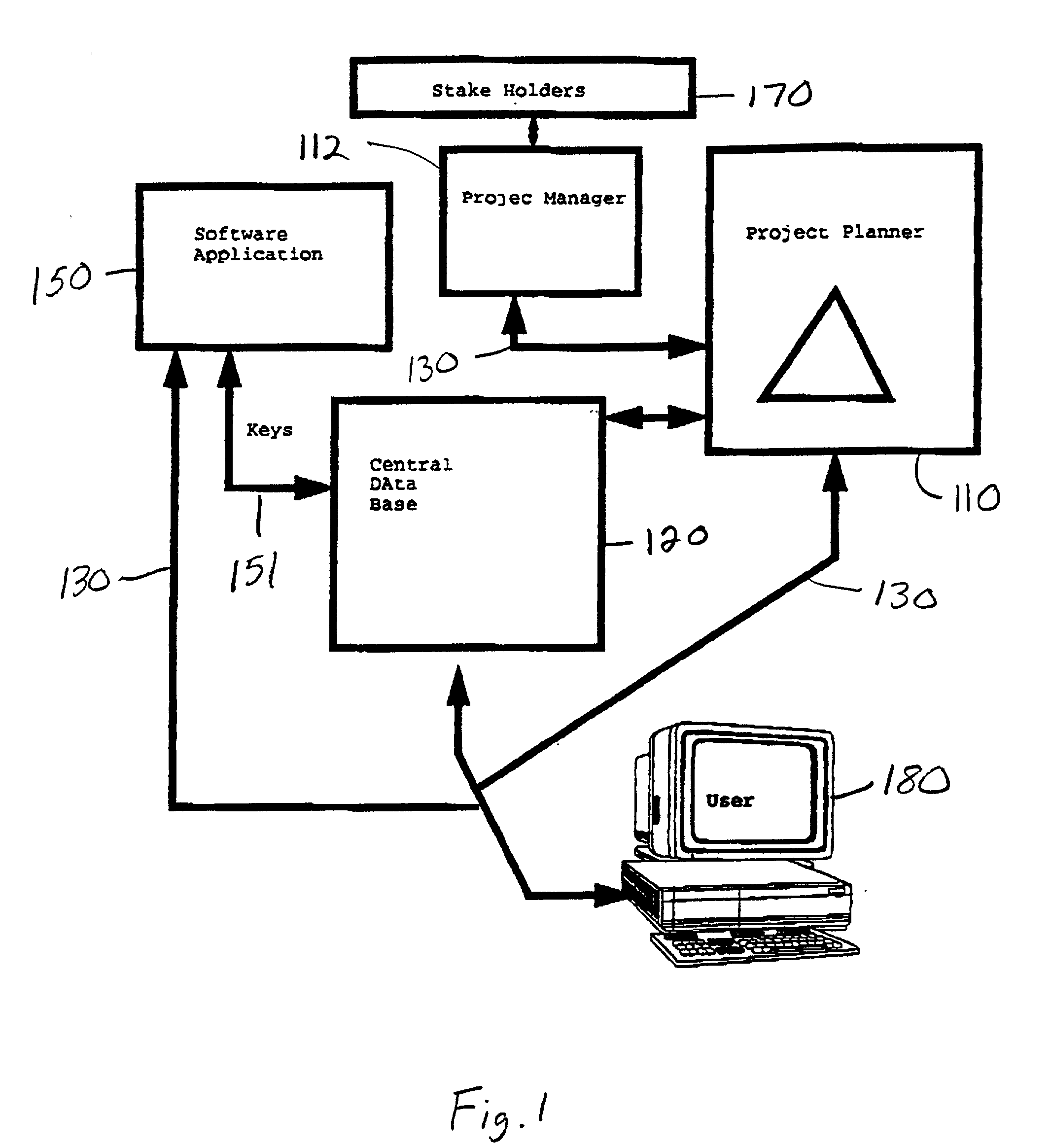
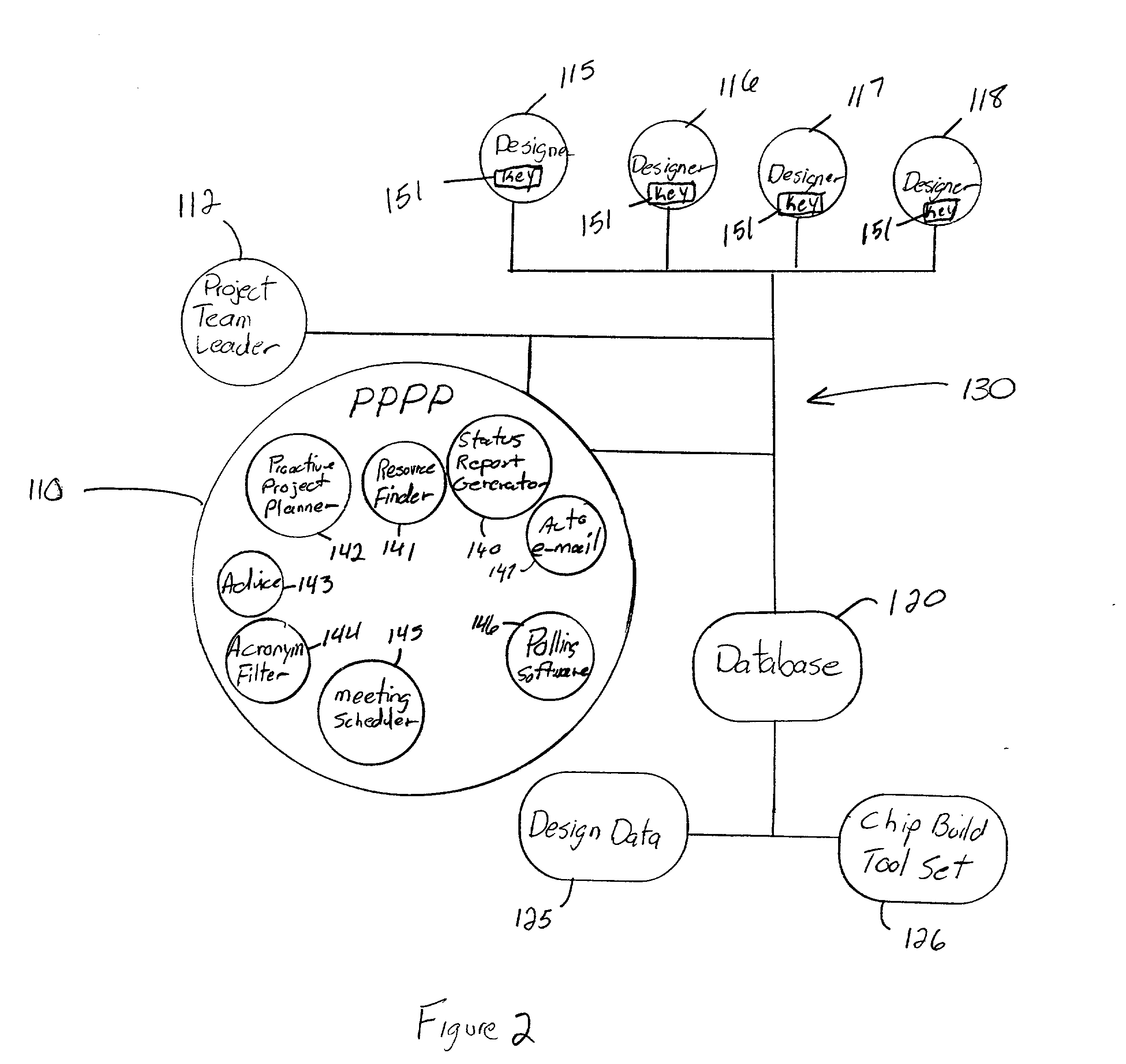
Pervasive proactive project planner
InactiveUS20030078826A1Increase probabilityResourcesSpecial data processing applicationsTask completionComputer science
A method and structure for coordinating resources to complete a design project prioritizes tasks to create a project plan, automatically notifies resources of task responsibilities and associated due dates based on the project plan through the use of encryption keys, controls access to the design data through the use of the encryption keys assigned to the resources, automatically monitors work being performed on tasks through a computerized network, and automatically notifies a project team leader of task completion status, overdue tasks, and tasks being ignored, based on the monitoring.
Owner:IBM CORP
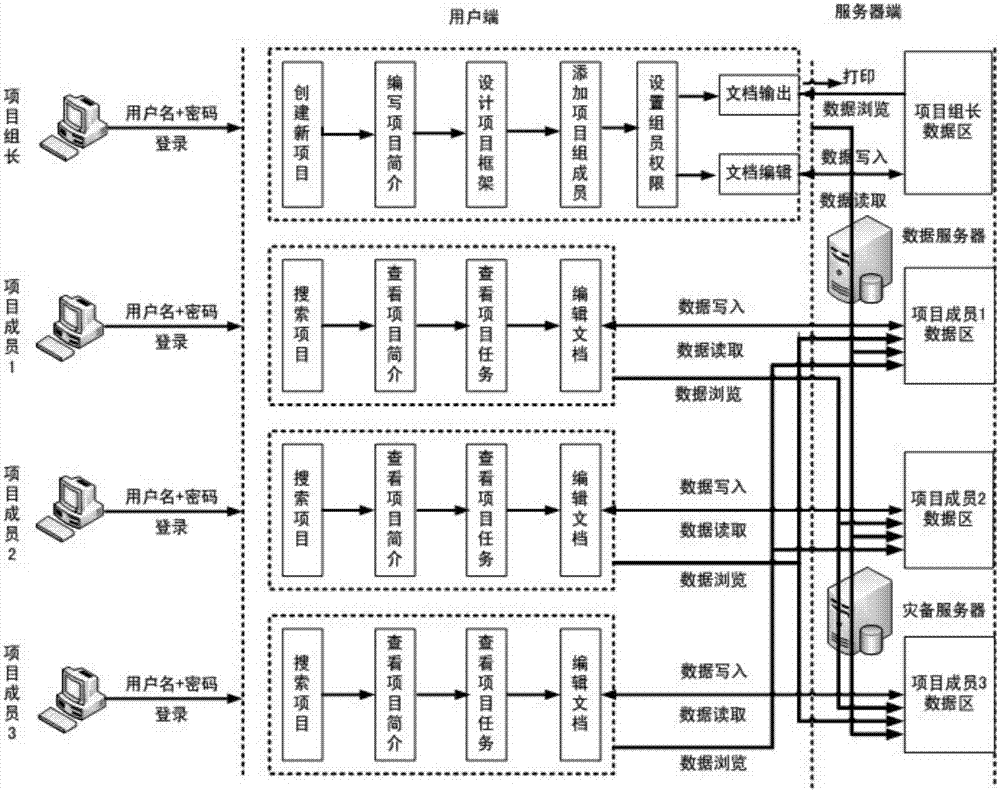
Method and system for organizing projects in an integral user environment
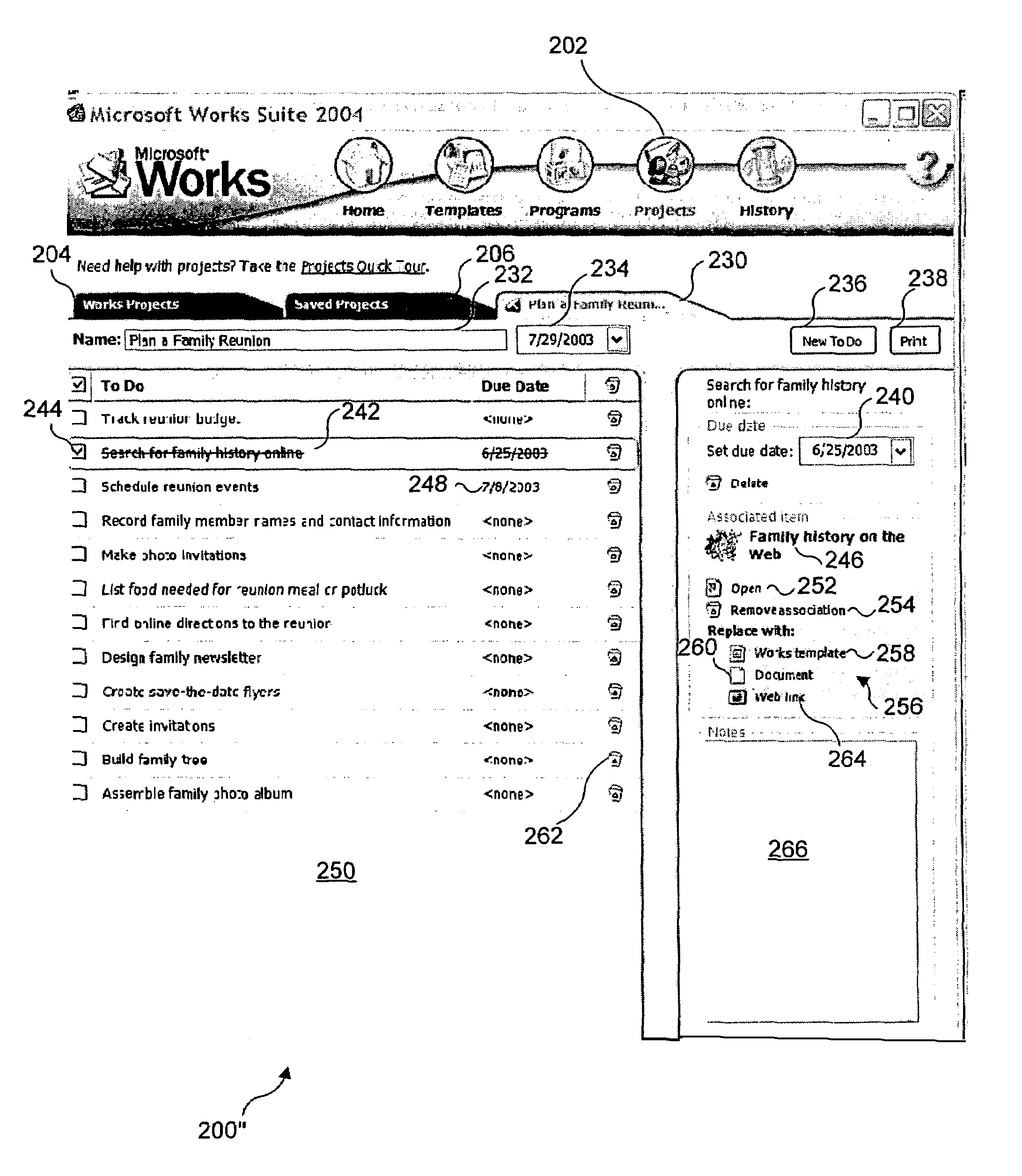
InactiveUS7467355B1Easy accessInput/output processes for data processingProject environmentUser environment
An integrated user environment for creating, managing, and organizing components of a project. A user is able to select a predefined project that includes a list of to do items, or can start with a blank project and add to do items. Once a to do item has been added, the user can associate several different functions with the to do item, including a due date, a note, and one of several categories of entities. These entities include a task or template, a document, and a Web link. If the user selects a task or template, Answer Wizard technology returns options that may be relevant to the selected to do item. Since all of the components of the project are accessible by the user from within an integral project environment, it is relatively efficient for the user to manage the project and make any changes that are required.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for allocation of resources in a project portfolio
ActiveUS8214240B1Low costImprove efficiencyMarket predictionsResourcesACROSS ProjectResource information
Described are methods and apparatuses, including computer program products, for optimizing allocation of resources across projects in a project portfolio. The method includes receiving, at a computing device, (i) resource information, (ii) a portfolio of project definitions and (iii) one or more portfolio-level optimization criteria. The resource information representing a plurality of resources available for allocation to the projects, and each project definition includes a unique identifier and one or more project-level constraints. The method also includes generating, using the computing device, a plurality of project portfolio allocation scenarios and determining one or more optimized project portfolio allocation scenarios from the plurality of project portfolio allocation scenarios. Each project portfolio allocation scenario satisfies the one or more project-level constraints associated with each project definition. Each optimized project portfolio allocation scenario optimizes a sequence of the projects to satisfy the one or more portfolio-level optimization criteria.
Owner:FMR CORP
Cooperative editing system and method for document based on centralized data control
InactiveCN107273343AImprove access rateSpeed upNatural language data processingOffice automationData controlData synchronization
Owner:BEIJING INST OF COMP TECH & APPL
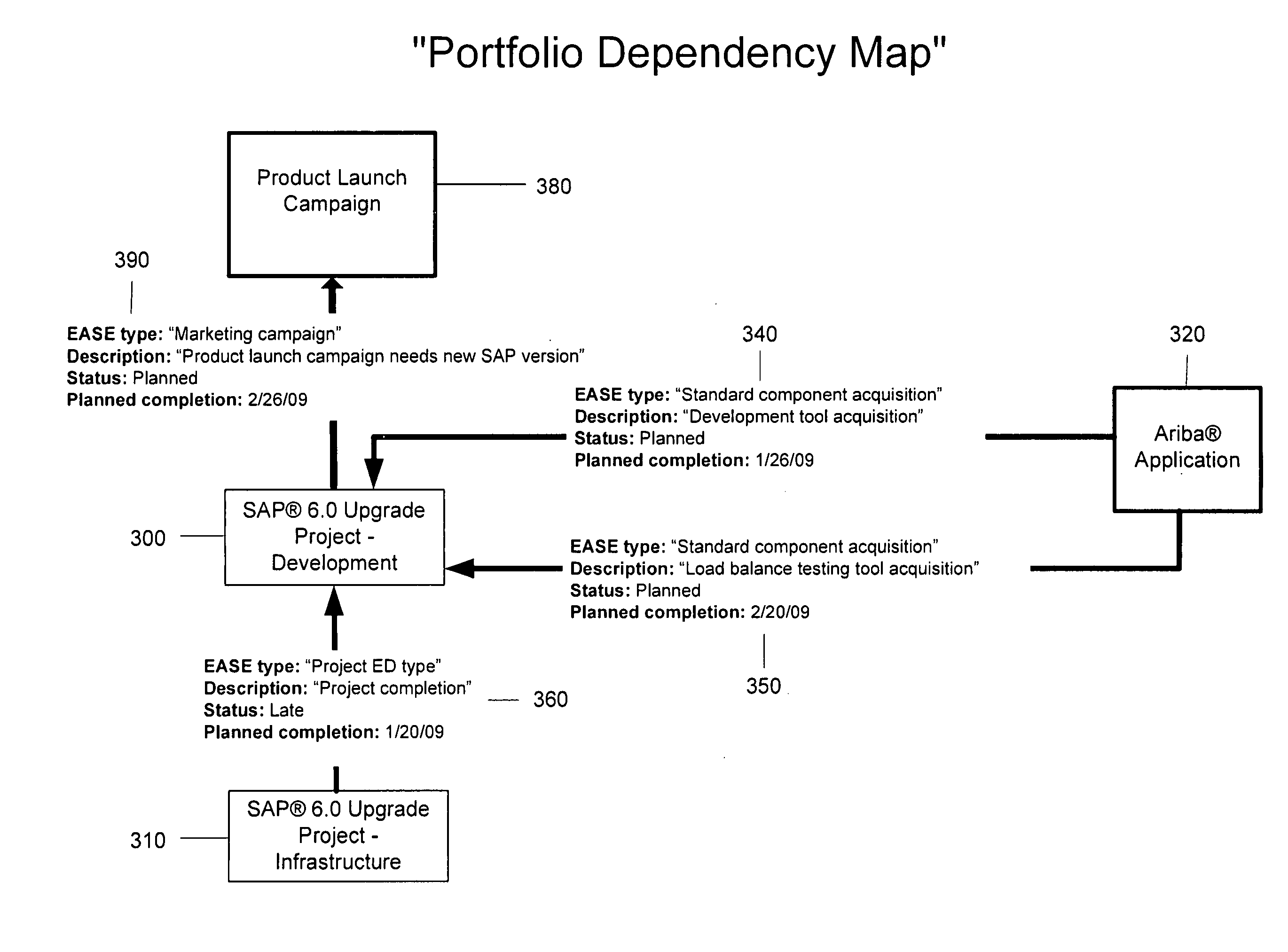
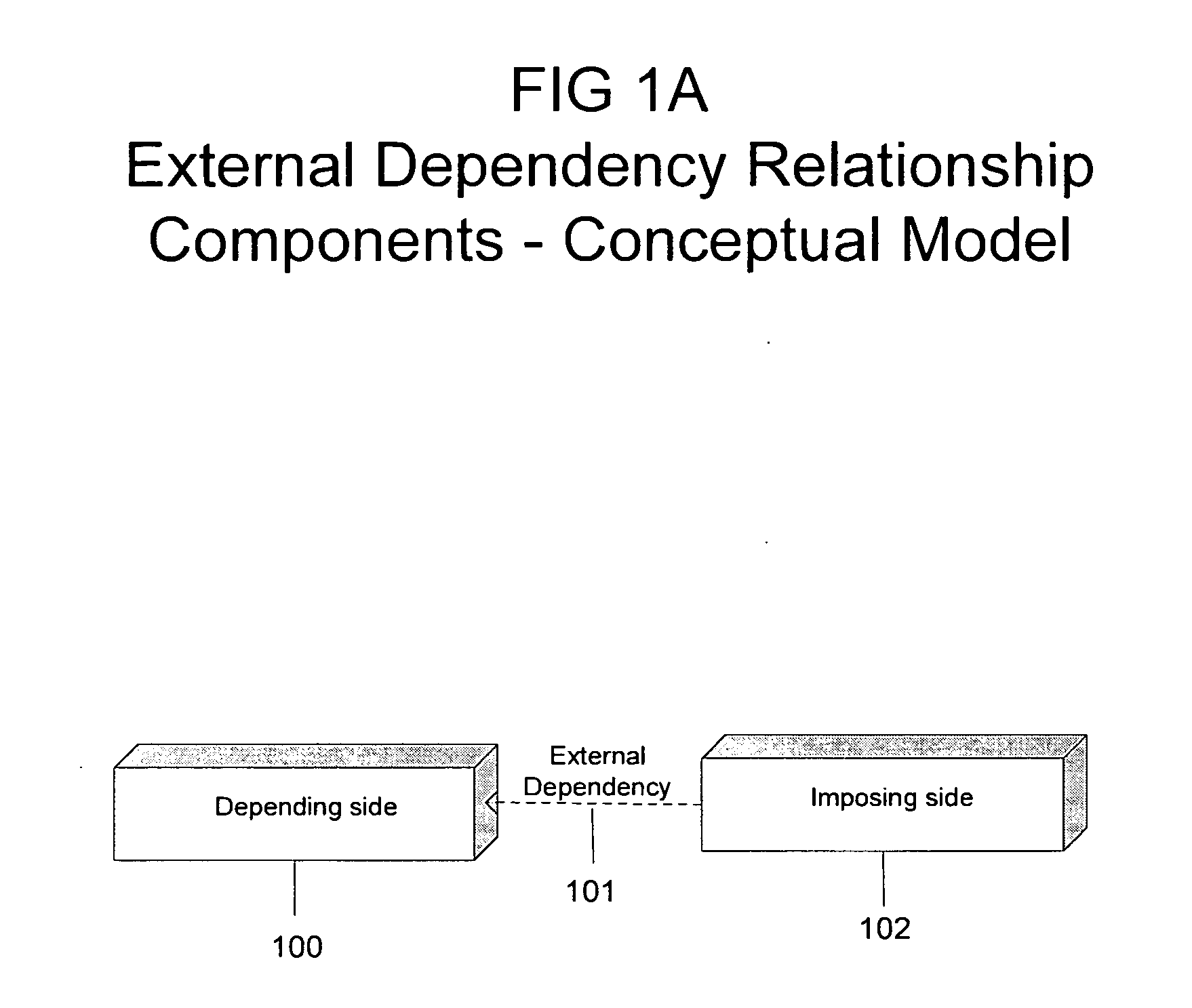
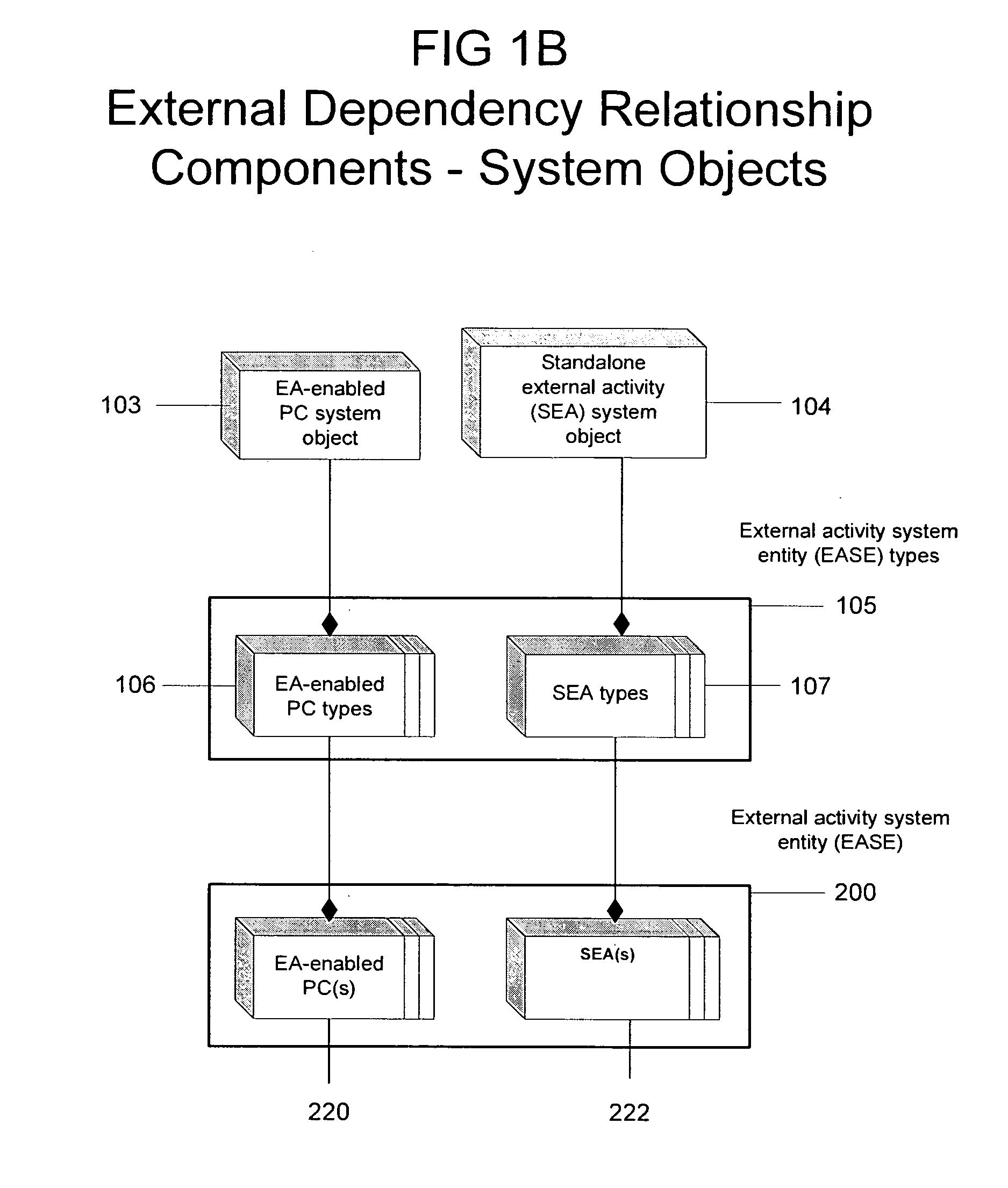
System and methods for management of external dependencies associated with a project portfolio
InactiveUS20110046992A1Rapid and broad adjustmentResourcesSpecial data processing applicationsProject groupVertex (graph theory)
The present invention applies concepts from the graph theory in mathematics and computer science to the management of external dependencies associated with a project portfolio. By viewing components of a project portfolio as nodes (vertices) of a graph, which may also include activities that are external to the project portfolio but depend or impose dependencies on it, a significant and unique business value can be realized. An exemplary embodiment of these concepts is described, demonstrating comprehensive, generic, and flexible system and methods.
Owner:ERHARD ITAY M
System and method for network-based project management
Owner:CHASE BANK USA NAT ASSOC +1
Combined type tasking time-driven chronic disease preventing control and health managing method
InactiveCN103218510AImprove participationPromote achievementSpecial data processing applicationsDiseasePDCA
The invention relates to a combined type tasking time-driven chronic disease preventing control and health managing method. The method is designed for a health managing project for a chronic disease preventing control and health managing service, planning an execution time rhythm of the health managing project in different managing stages for the chronic disease risk and risk grade, establishing a time-driven tasking health managing project group, and assembling, combining and forming a productized chronic disease preventing control and health managing service. According to the requirement of chronic disease management, the health managing service is matched and started for a managed object; the health information is collected and analyzed; the health state is assessed; PDCA cycle operation is performed in a time-driven health managing task sequence on the basis of health standard according to an energy balancing and psychological stress managing principle; a health managing technology is applied in a systematic, standard and processed form; a managing scheme is made; a health managing target is refined; the track is approached step by step; the intervening execution is enhanced; the health state is improved; the risk factor is controlled; and the purpose of chronic disease preventing control and health managing is achieved.
Owner:冯力新 +1
Automated construction method and device
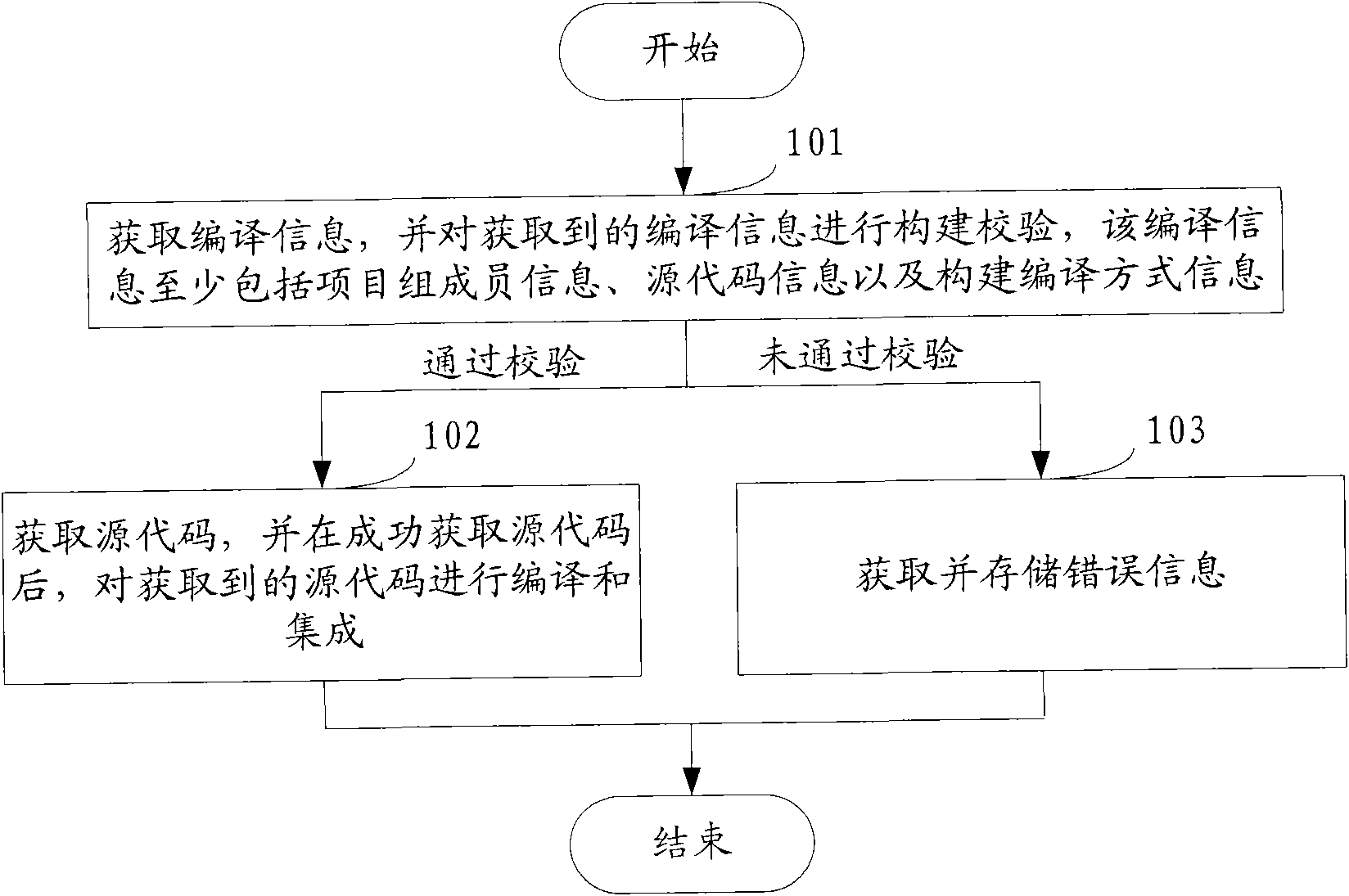
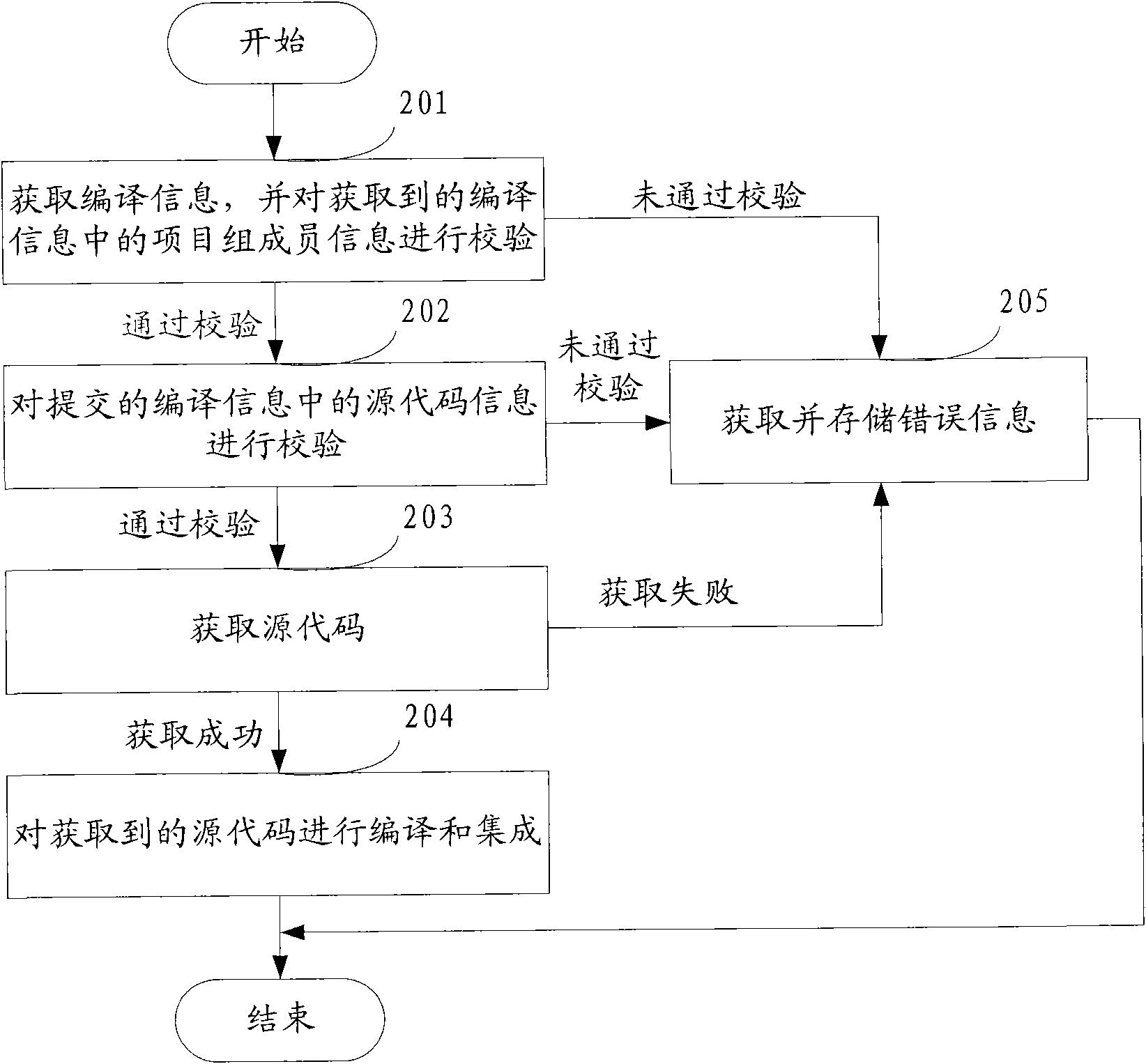
ActiveCN102135877AImprove information securityImprove development efficiencySpecific program execution arrangementsMemory systemsSoftware developmentSource code
The invention discloses an automated construction method and an automated construction device, which belong to the technical field of computers. The method comprises the following steps of: acquiring compilation information, and performing construction verification on the acquired compilation information, wherein the compilation information at least comprises project group member information, source code information and construction compilation mode information; if the compilation information passes the construction verification, acquiring a source code, and compiling and integrating the acquired source code after the source code is successfully acquired; and if the compilation information does not pass the construction verification, acquiring and storing error information. In the invention, the construction verification is performed on the acquired compilation information, and the source code can be acquired after the construction verification is passed, so that the information safety of the source code can be improved, the development efficiency of software can be improved, and the quality of the software can be ensured.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Recommendation method and system based on a generative adversarial network and double clustering
InactiveCN109657149AStrong targetingThe result of clustering is diverseSpecial data processing applicationsText database clustering/classificationData setIntegration algorithm
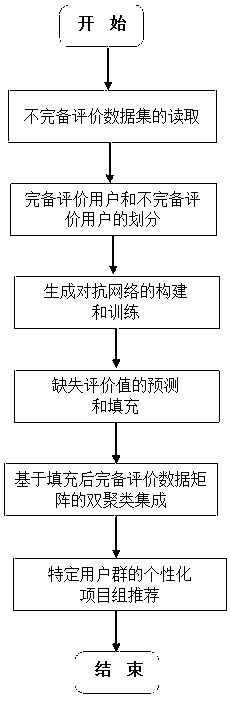
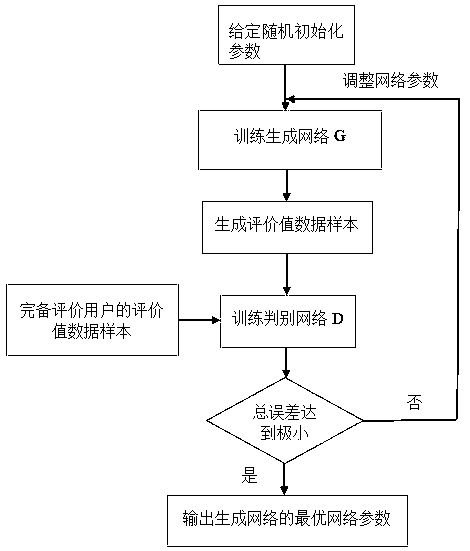
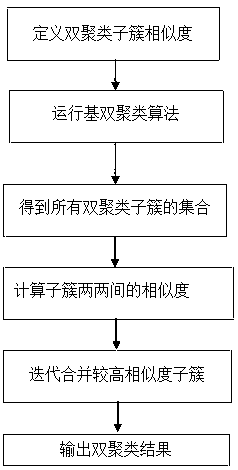
The invention discloses a recommendation method and system based on a generative adversarial network and double clustering, and belongs to the technical field of computer application. The method comprises the following steps: firstly, reading the incomplete evaluation data set of a user-project establishing an incomplete evaluation data set of a project, then constructing a generative adversarialnetwork consisting of a generative network and a discriminant network, then predicting and filling missing evaluation values by utilizing the trained generative network, finally carrying out double clustering, and carrying out corresponding project group recommendation on different user groups according to sub-clusters obtained by the double clustering. According to the recommendation method and system, the trained generation network is used for filling the missing evaluation value, and the defects that a traditional method for filling the missing evaluation value such as the mean value (or the number of people) and linear interpolation is low in precision and large in error are overcome; And the filled complete evaluation data is clustered by using the double-clustering integration algorithm, so that the clustering result is more effective than that of a single double-clustering algorithm, the pertinence of a project group recommended to a specific user group is stronger, and the recommendation effect is improved.
Owner:HEFEI UNIV +1
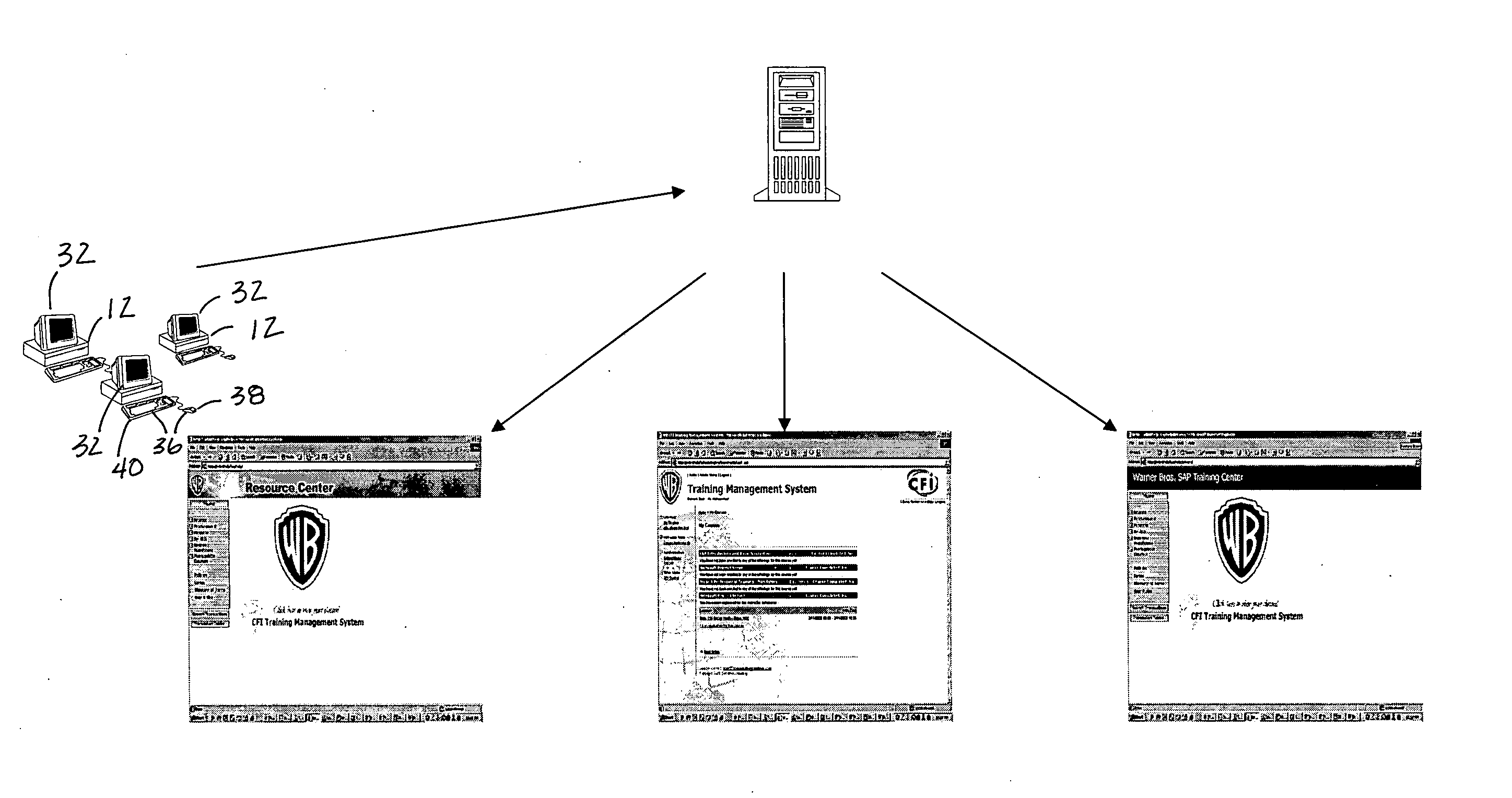
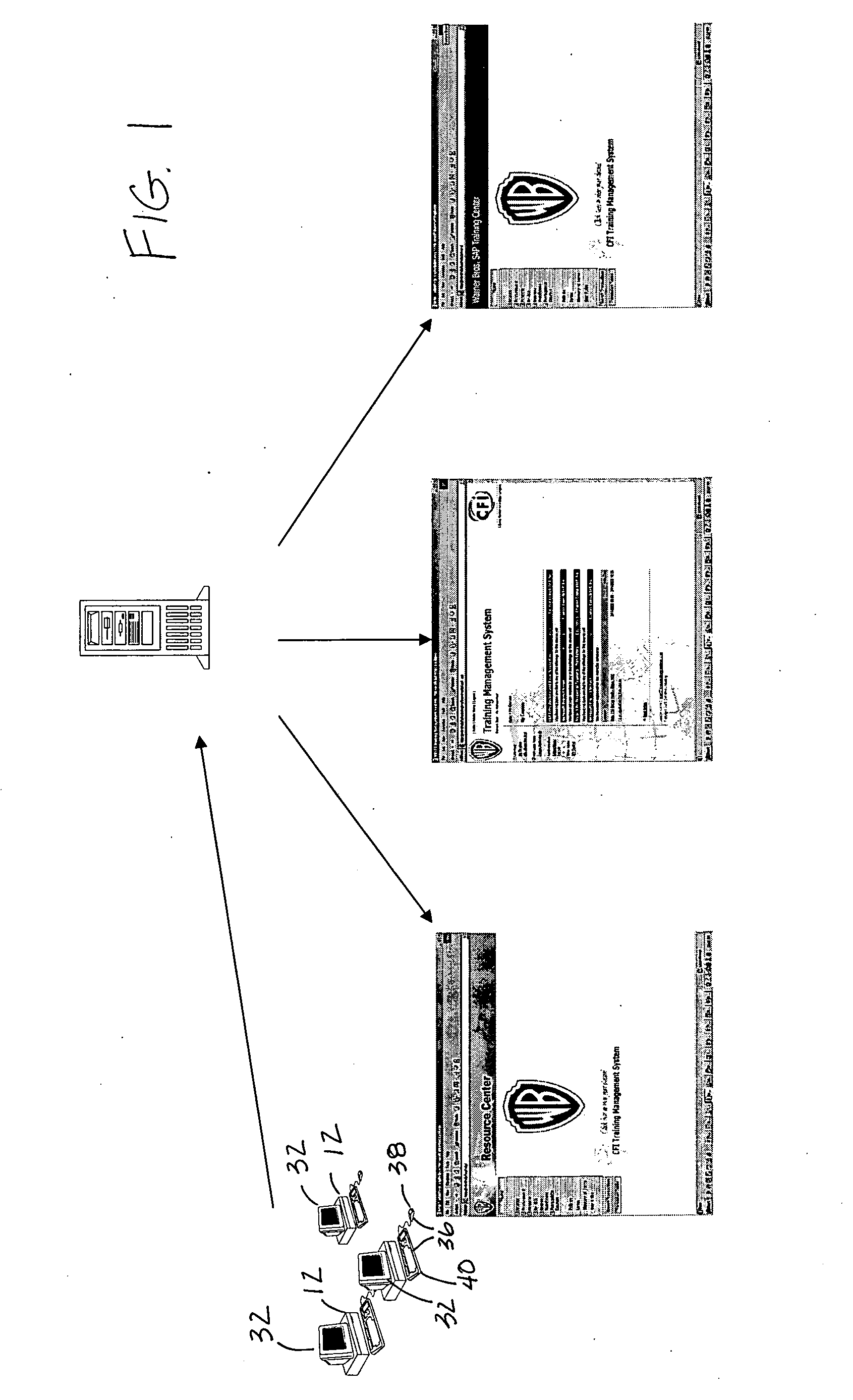
Database software program and related method for using it
InactiveUS20070027868A1Easy to displayFast dataDigital data processing detailsResourcesSoftware engineeringWorkstation
A computer-readable medium included in a server that has a database and to which a workstation having a monitor is coupled for viewing by a user. The computer-readable medium includes instructions for database management. The database includes project data related to multiple tasks handled by more than one project group. The instructions prompt a display of the project data on the monitor. The instructions prompt a display of a filter on the monitor that the user can use to perform sorting of the project data.
Owner:WARNER BROS ENTERTAINMENT INC
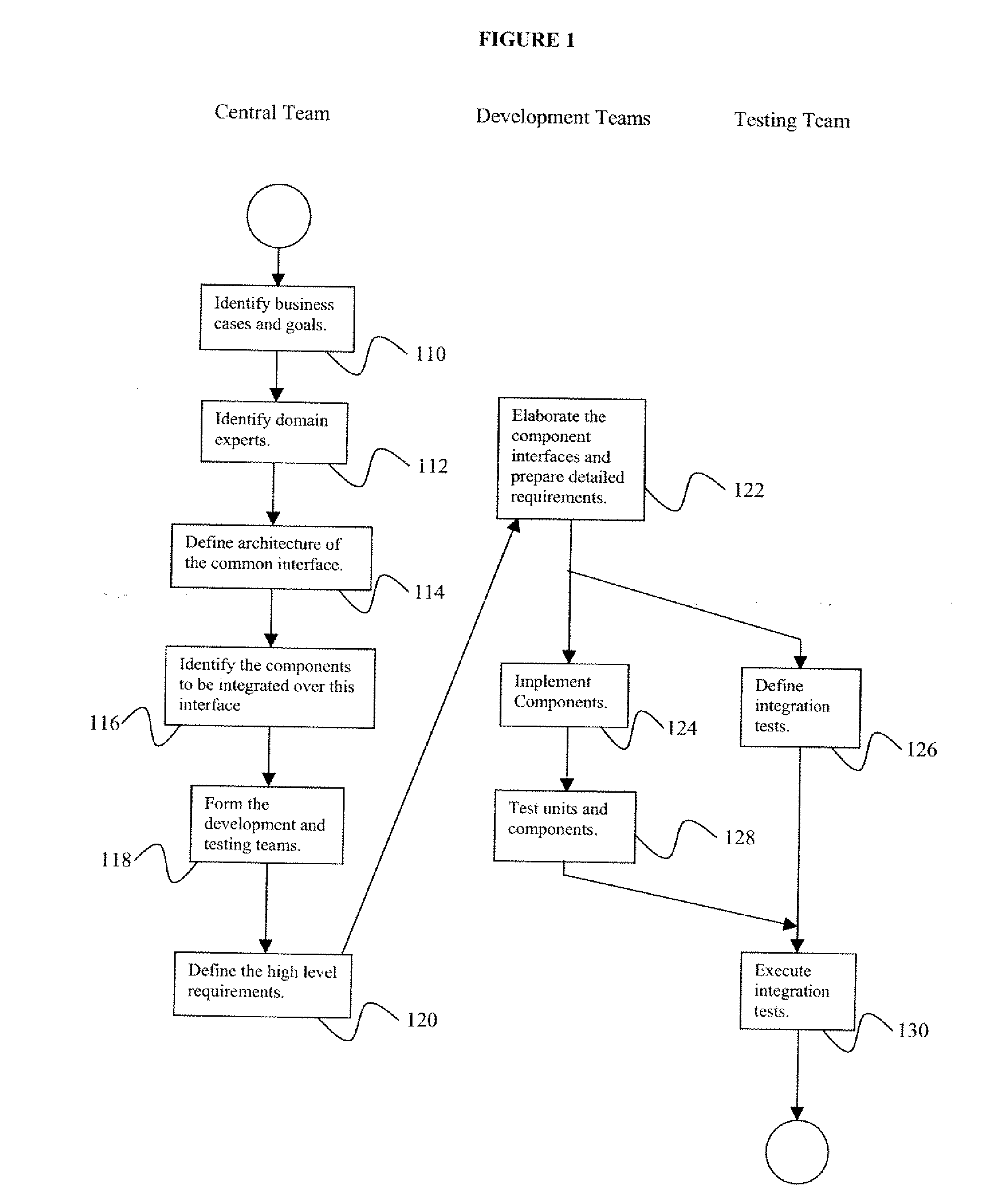
Test Driven Architecture Enabled Process For Open Collaboration in Global
InactiveUS20080134134A1Increase team productivityRate performanceError detection/correctionSpecific program execution arrangementsPublic interfaceIntegration testing
A method for developing a software project includes identifying business cases and goals for the software project, defining a common interface architecture through which components of the software project are to be integrated, identifying software project components to be integrated over the common interface, defining high level requirements of the project components, elaborating the component interfaces and defining detailed component requirements, implementing the project components, testing the project components individually, defining integration tests for testing integrated components, and executing the integration tests on a set of integrated components.
Owner:SIEMENS CORP
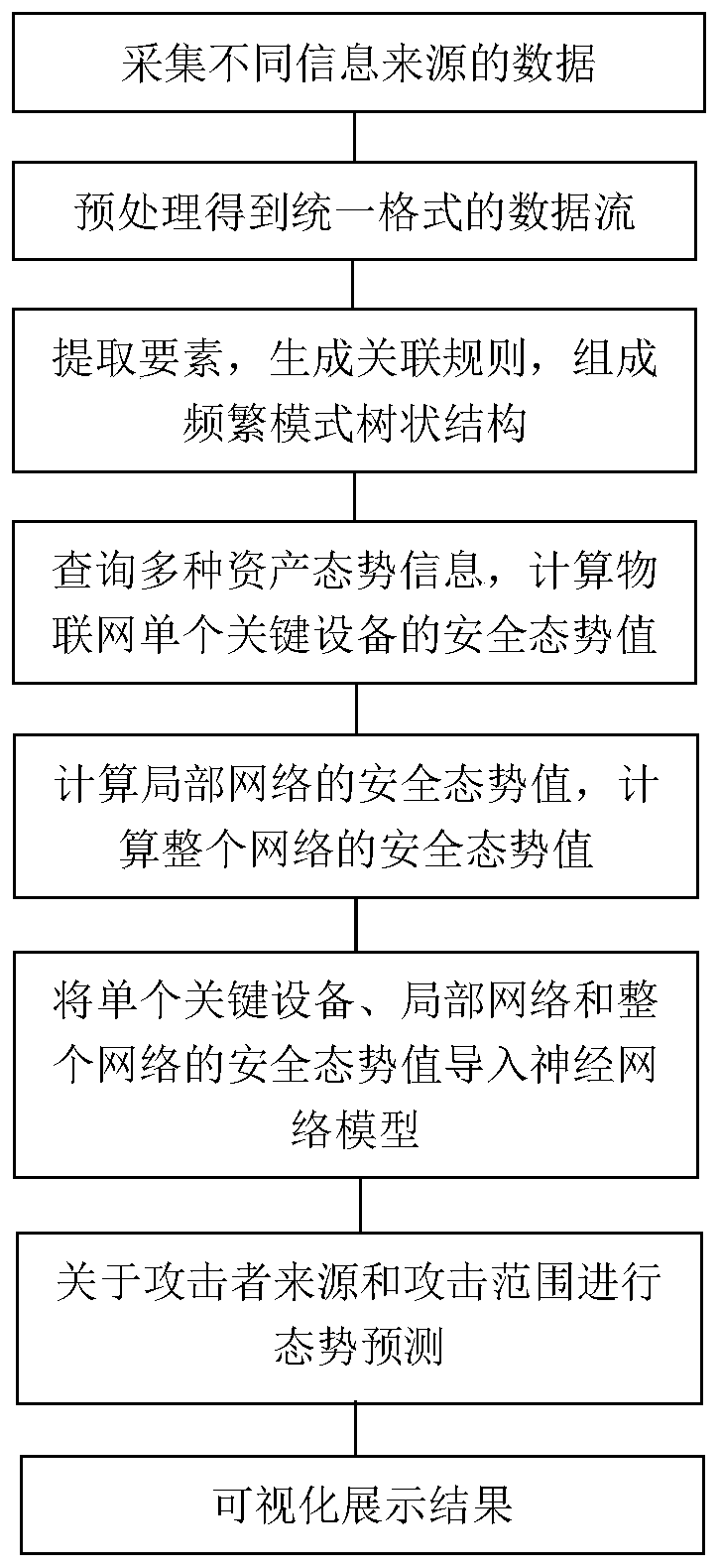
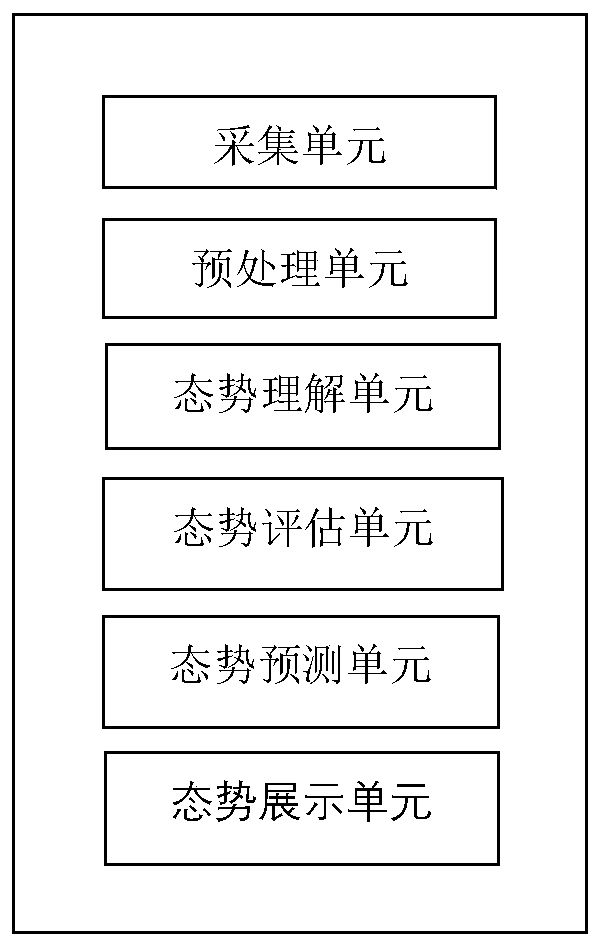
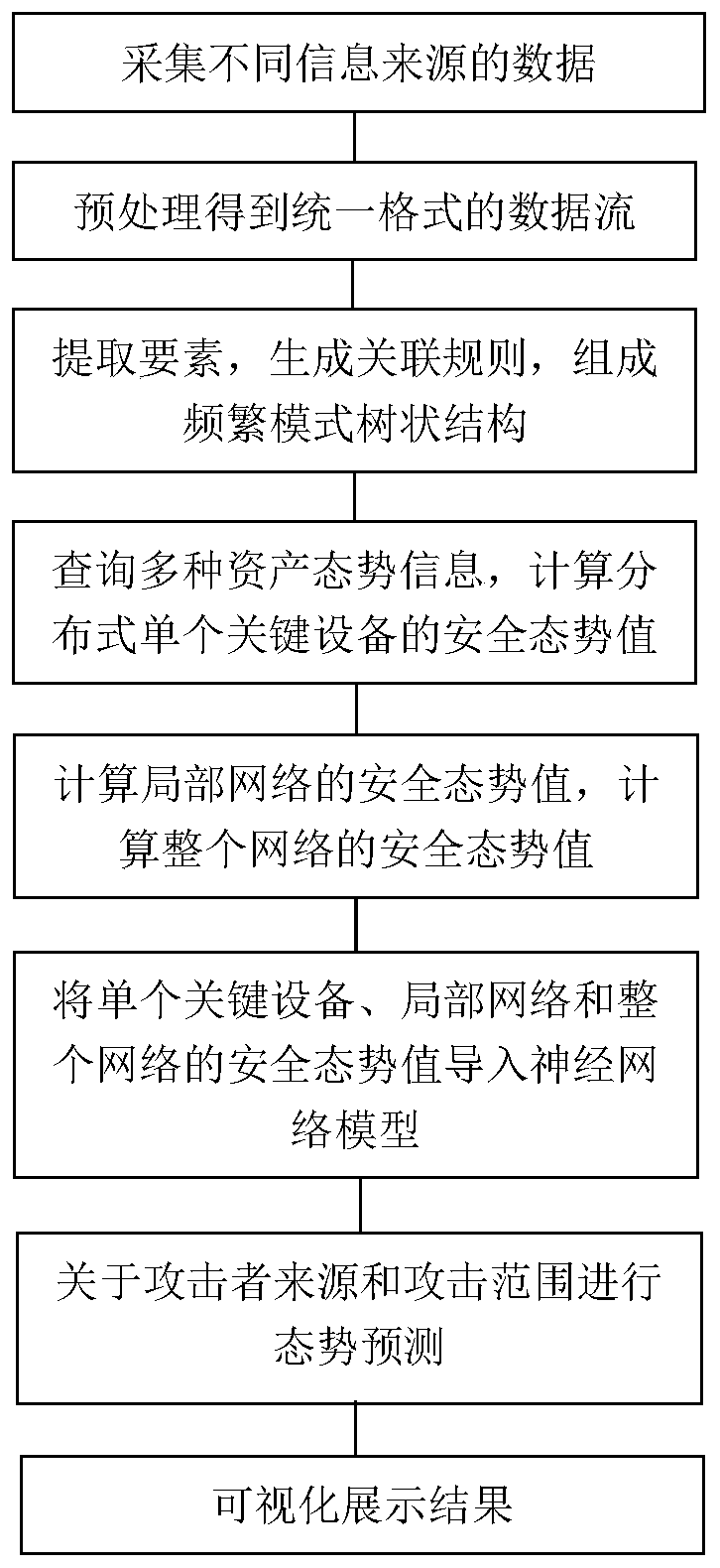
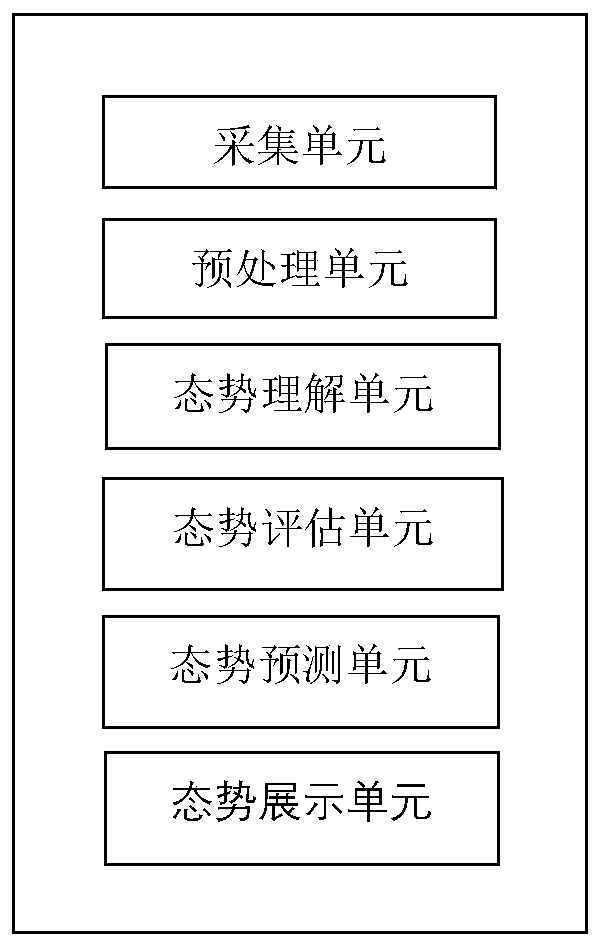
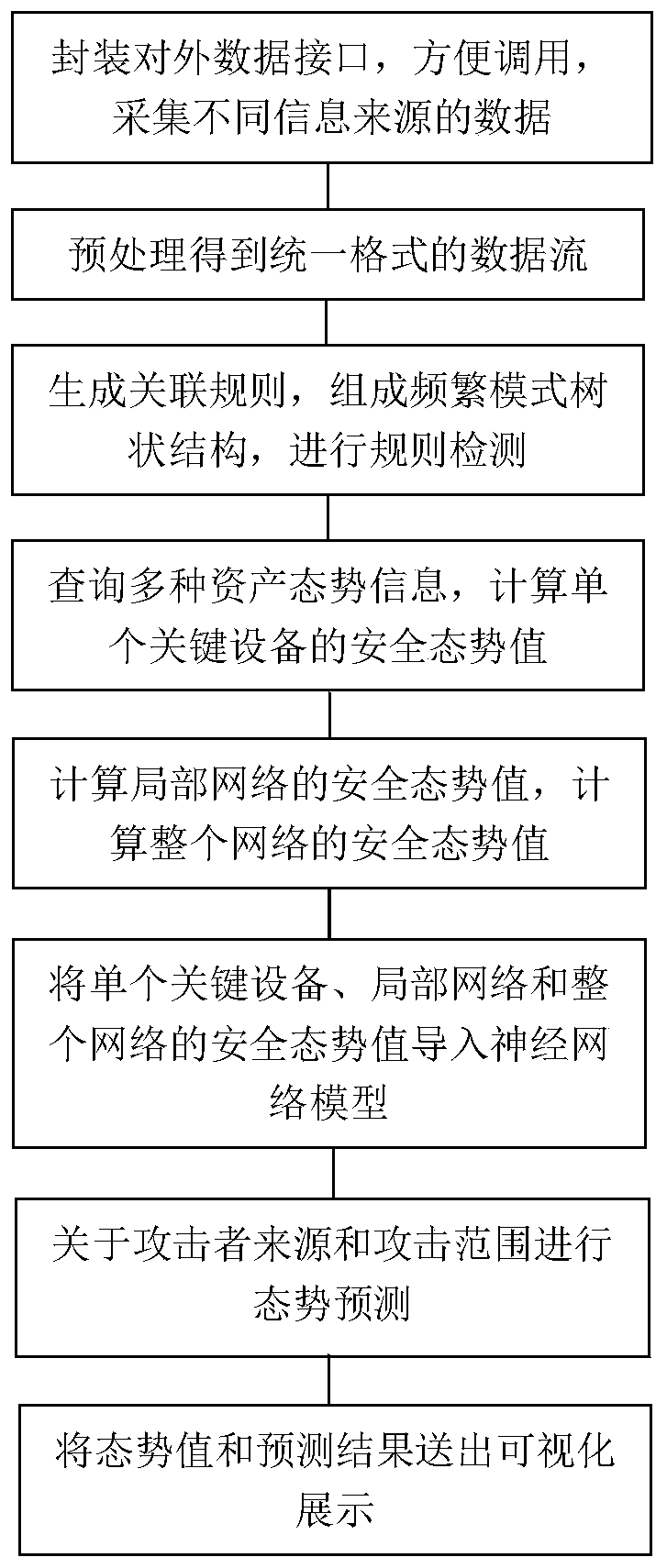
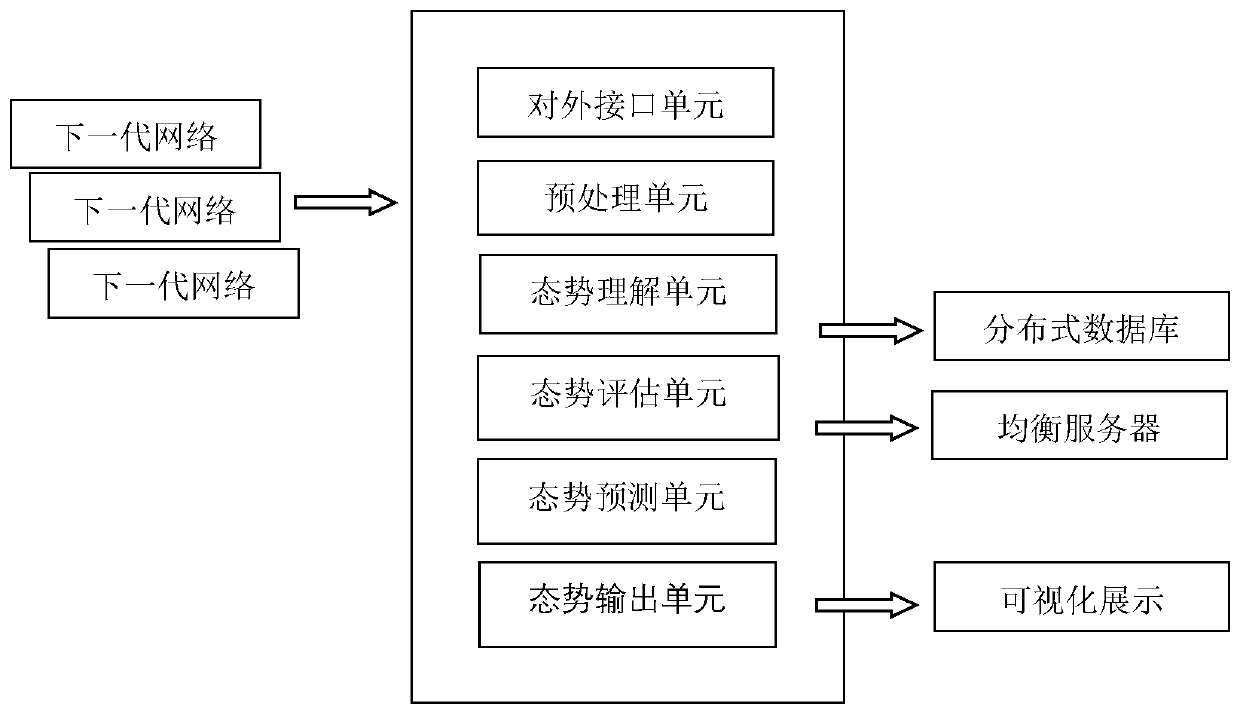
Situation awareness method and system of Internet of Things
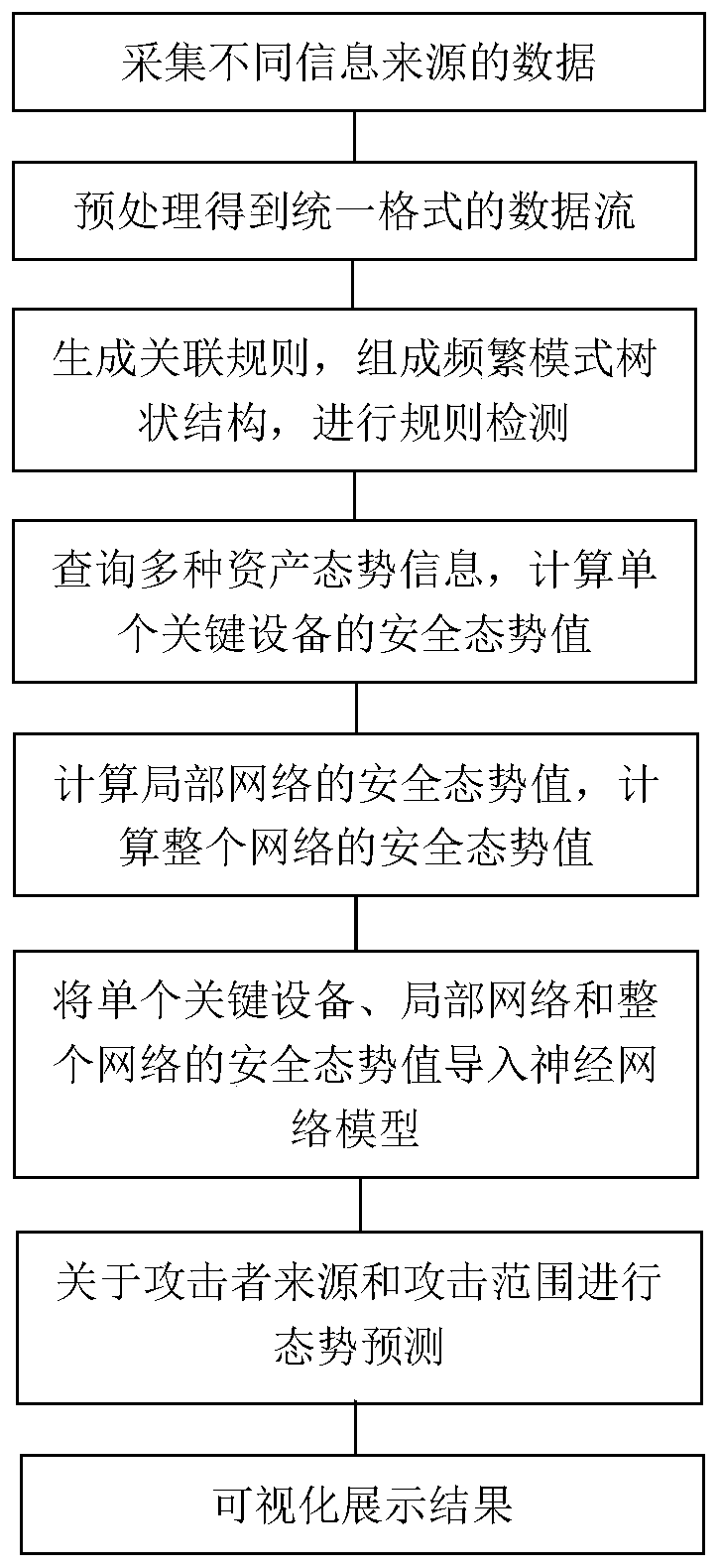
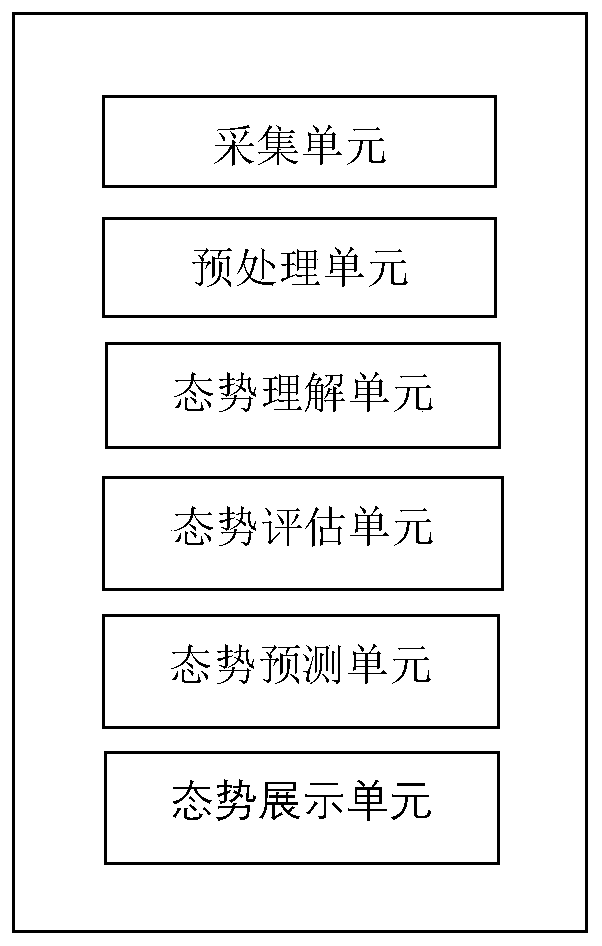
The invention provides a situation awareness method and system of the Internet of Things. The method comprises steps of collecting data of different information sources; obtaining data streams in a unified format through preprocessing; extracting high-frequency project group elements from the data stream; generating high frequency association rules, carrying out situation evaluation for evaluationquantification; through fusing with different evaluation systems and obfuscating the data elements, situation values of a single device and a local network are obtained, the architecture compositionof the whole network is combined; a situation value of the whole system is obtained; the situation values of different levels are imported into a neural network model for prediction; finally, the prediction result is visually displayed, the whole Internet of Things system and each single device are fully evaluated, and the prediction result can be associated with each device and each layer basedon the given situation value so that the future system can be scientifically predicted, and valuable reference suggestions can be provided for users.
Owner:武汉思普崚技术有限公司
Ic Card for Encryption or Decryption Process and Encrypted Communication System and Encrypted Communication Method Using the Same
InactiveUS20070226513A1Key distribution for secure communicationComputer security arrangementsProject groupComputer hardware
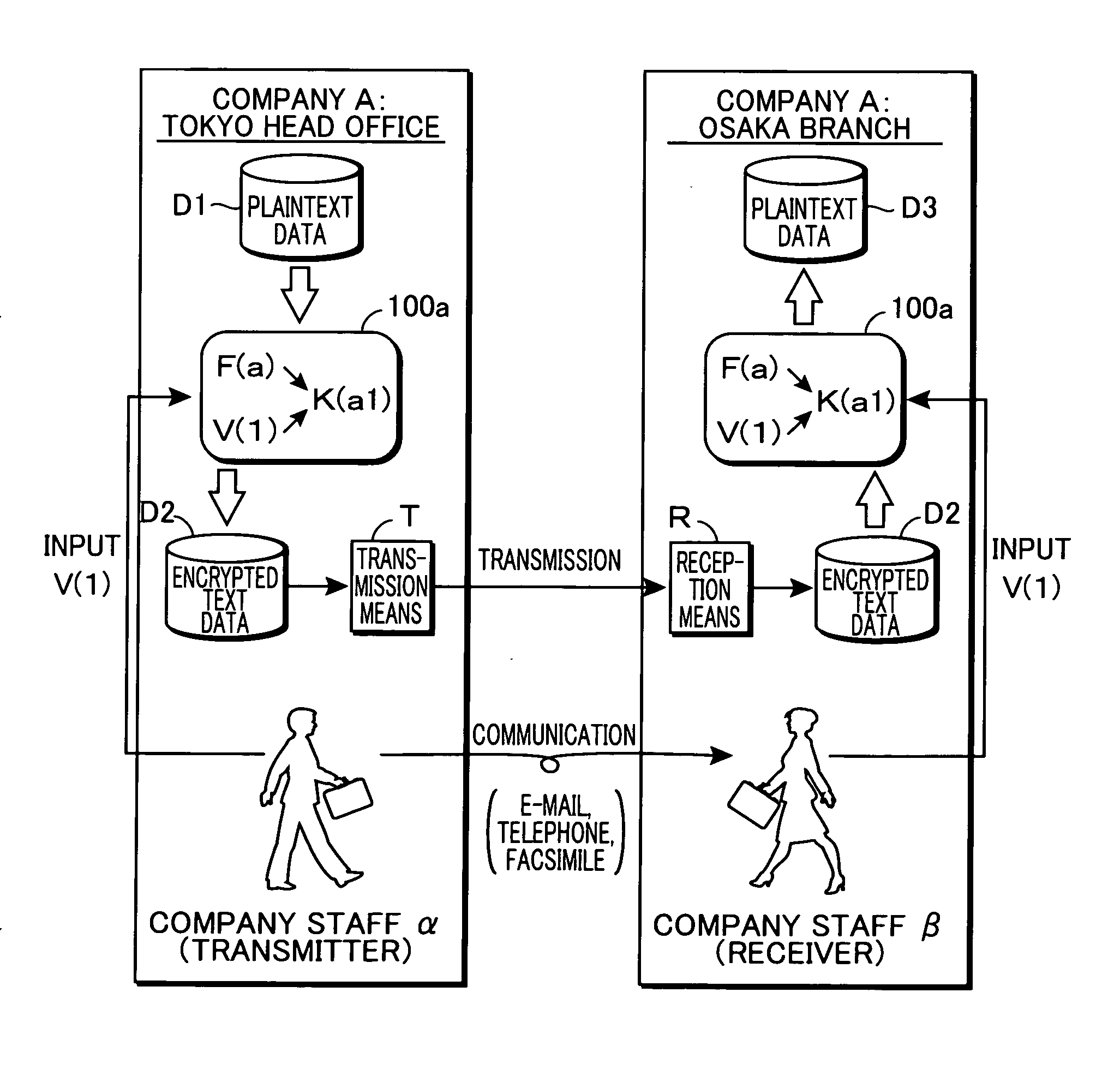
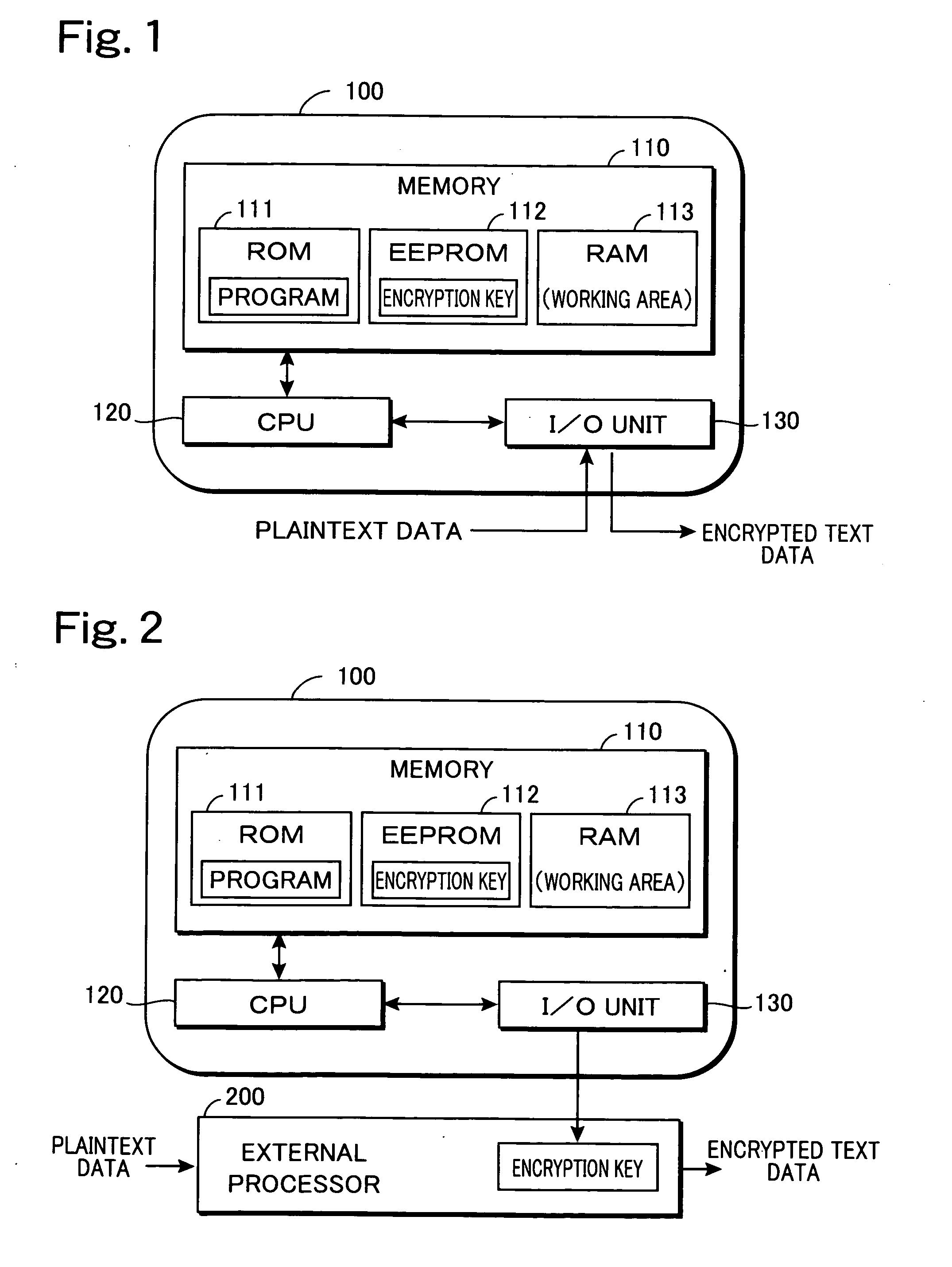
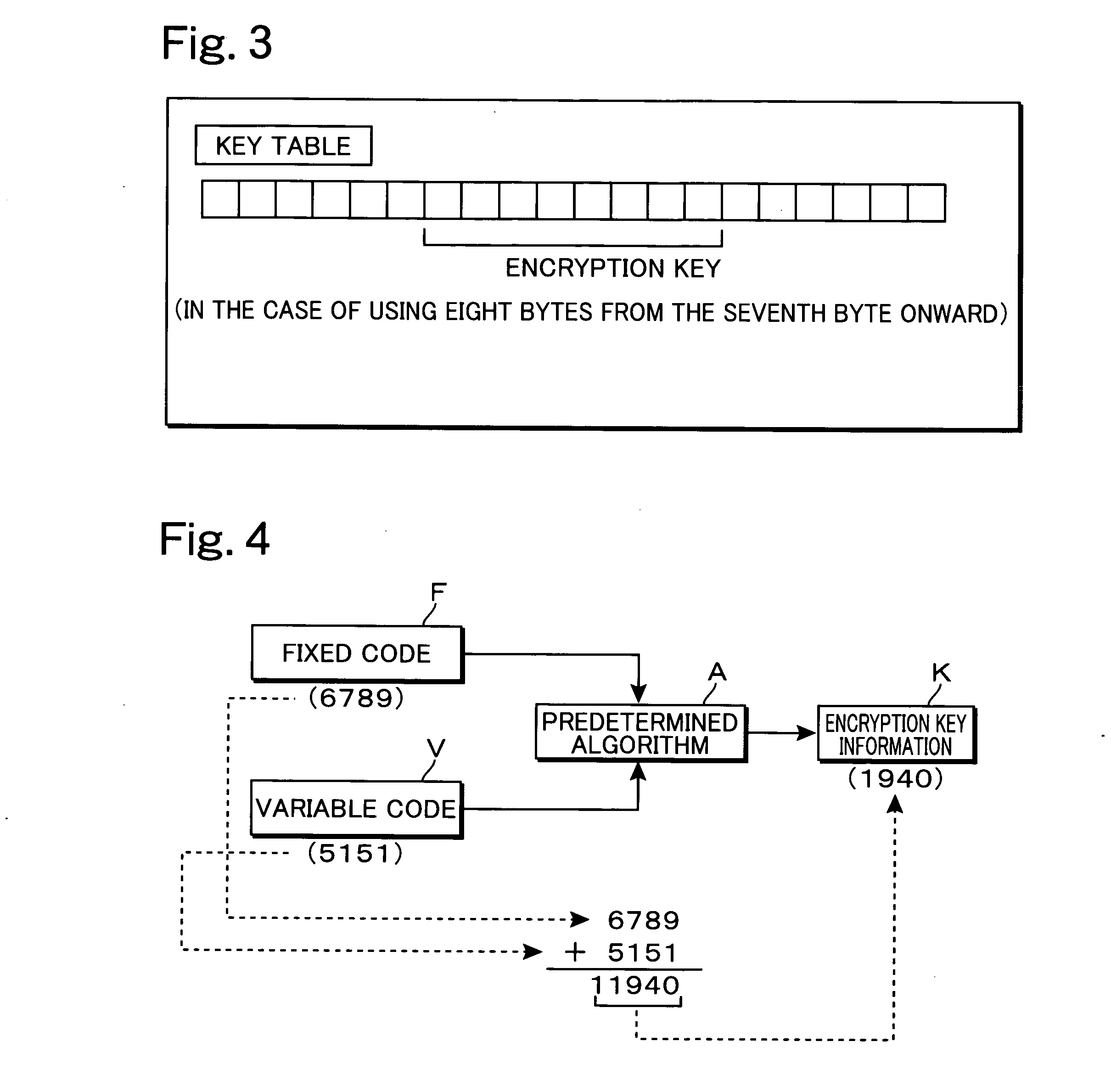
It is possible to perform encrypted communication between members of a group while assuring a sufficient security compatible with a change of the members. An IC card having the same fixed code F(a) is distributed to all the staffs of company A. When communication is performed between a staff α and a staff β belonging to the same project group, α of the transmission side writes an arbitrary variable code V(1) in the IC card (100a) so as to generate encryption key information K(a1) according to F(a) and V(1) in the IC card and encrypt data D1 by using K(a1). β of the reception side writes the variable code V(1) received from a in the IC card (100b) so as to generate encryption key information K(a1). By using this K(a1), the encrypted data D2 received is decrypted to obtain data D3. The fixed code F(a) is different for each of the companies and rewrite-disabled so as to assure security.
Owner:DAI NIPPON PRINTING CO LTD
0-1 integer programming-based oil field project group optimal deployment method
InactiveCN107368910AMeet the needs of optimized deploymentImprove scienceForecastingResourcesDecision makerBase oil
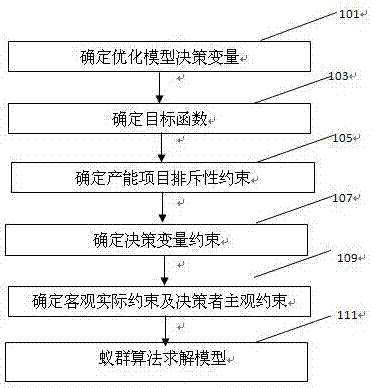
The present invention provides a method for optimal deployment of oilfield project groups based on 0-1 integer programming. The method for optimal deployment of oilfield project groups based on 0-1 integer programming includes: step 1, determining the decision variables of the optimization model; step 2, after deployment The maximum total net present value after conversion of all projects is the optimization goal, determine the objective function; Step 3, determine the exclusion constraints of capacity projects; Step 4, determine the decision variable constraints, to avoid the possibility of re-commissioning in subsequent years after the project is put into production; Step 5 , to determine the objective practical constraints and the subjective constraints of decision makers; step 6, use the ant colony algorithm to solve the optimization model, and obtain the optimal deployment of capacity construction projects. The optimal deployment method of oilfield project groups based on 0‑1 integer programming can meet the needs of optimal deployment of production capacity construction projects, improve the scientificity and rationality of deployment of oilfield production capacity investment projects, and provide strict and reliable Methods.
Owner:CHINA PETROLEUM & CHEM CORP +1
Method and device for recommending items to user and storage medium
ActiveCN111242748AImprove experienceRealize accurate recommendationCharacter and pattern recognitionBuying/selling/leasing transactionsRecommendation modelEngineering
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for driving a research and development task based on a flow
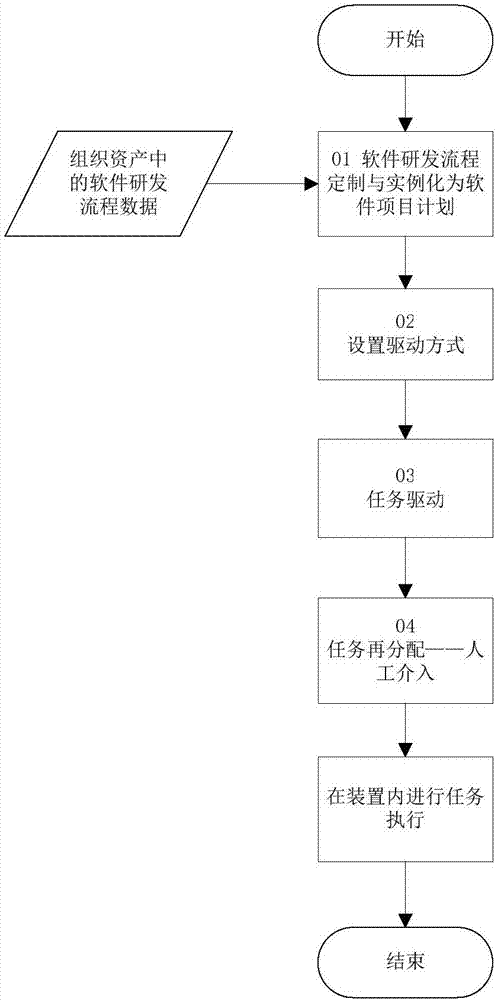
InactiveCN107153944AEasy to manageEasy maintenanceOffice automationResourcesProject groupData science
The invention discloses a method and system for driving research and development task based on flow. The method comprises a research and development activity generation module and a research and development task allocation module. The research and development activity generation module is used for driving all research and development activities involved in a software research and development flow according to flow data customized by a project; and the research and development task allocation module is used for realizing detailing of the research and development activities into research and development tasks and distributing the research and development tasks to corresponding project group members. According to the method and system disclosed by the invention, the research and development tasks can be generated automatically according to the software research and development flow, so that the task distribution efficiency and precision can be improved.
Owner:上海爱韦讯信息技术股份有限公司
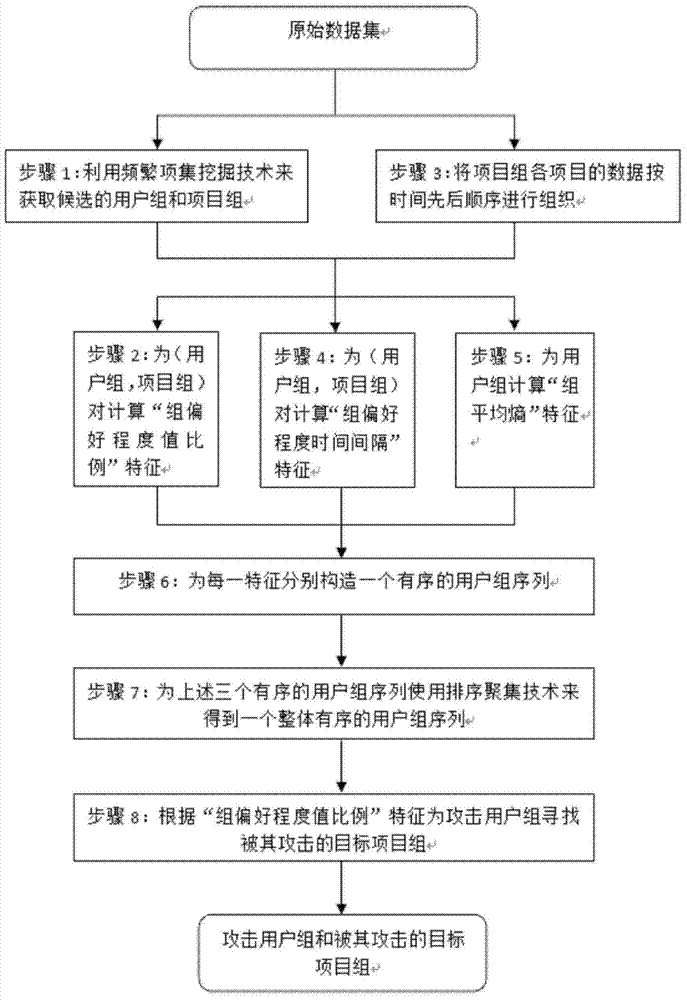
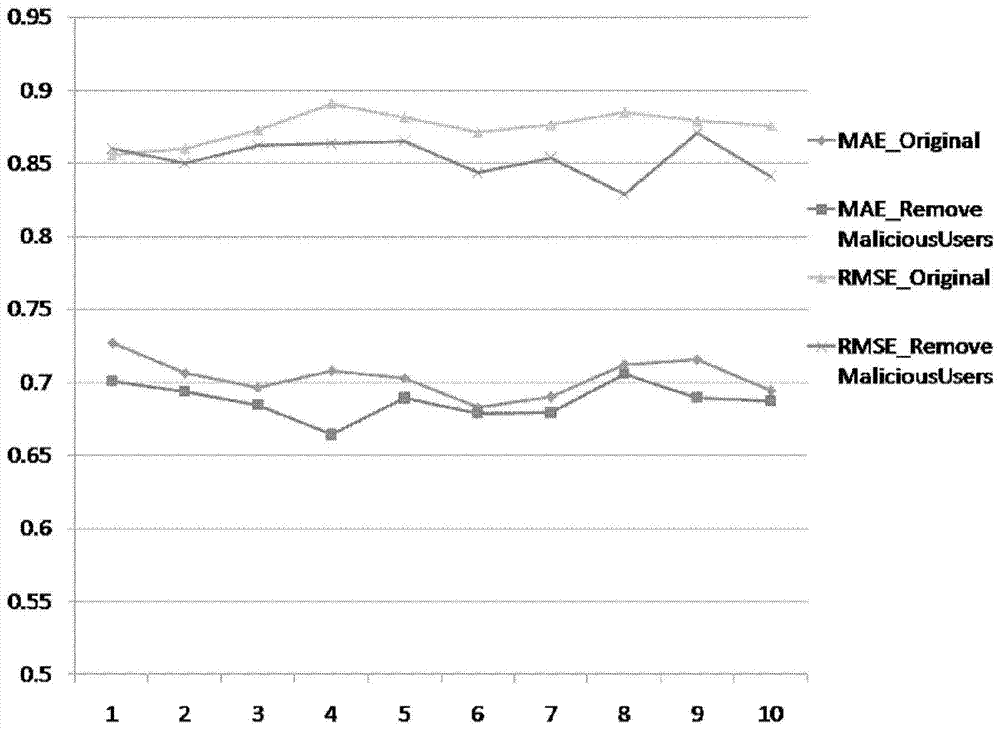
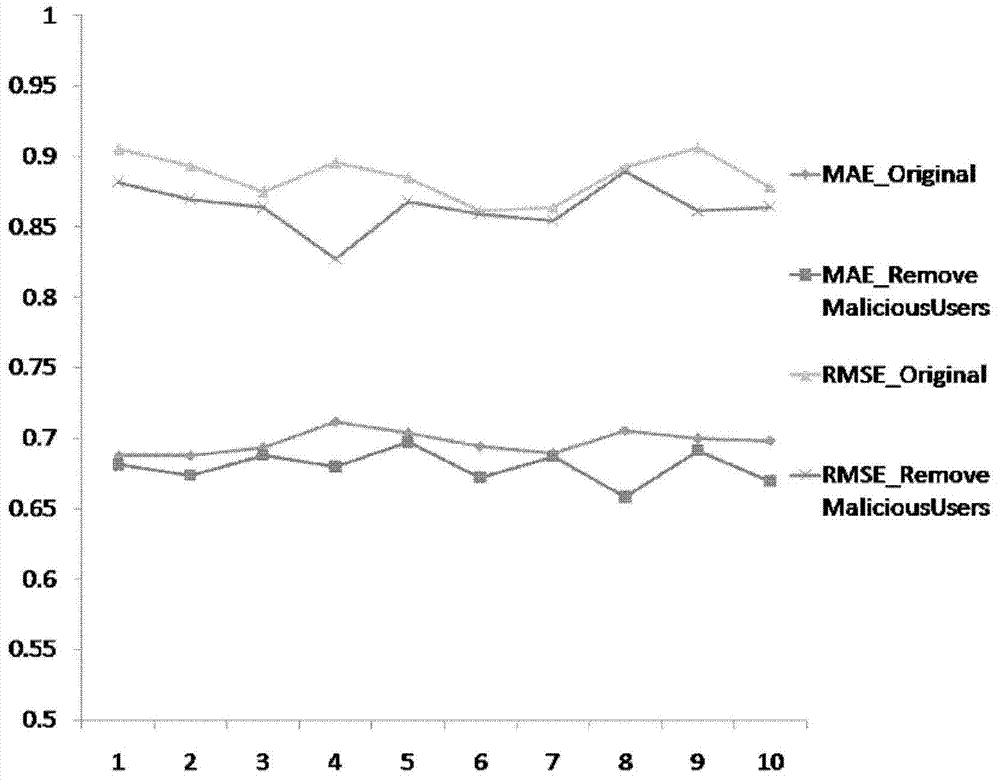
Recommendation system attack detection method based on time series data
The invention discloses a recommendation system attack detection method based on time series data. The method includes the steps that a user-project preference degree data set and a frequent item set excavation technology are utilized to acquire user groups and project groups; group preference degree value proportional characteristics are calculated for the pairs of user sets and the pairs of project sets; all preference degrees of projects in the project groups form time series preference degree data according to operating time; group preference degree time interval characteristics are calculated for the pairs of user sets and the project sets; group average entropy characteristics are calculated for the user groups; for the user groups, maximum group preference degree value proportional characteristics corresponding to the user groups and maximum group preference degree time interval characteristics corresponding to the user groups are selected, and the user groups are sequentially ranked through the three characteristics, and then three ordered user group sequences are acquired; the three ordered user group sequences are integrated to acquire a wholly ordered user group sequence, and the most probably attack user groups are acquired; the most probably target project groups are acquired through the group preference degree value proportional characteristics.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Situation awareness method and system containing correlation analysis
The invention provides a situation awareness method and a system containing correlation analysis. The method comprises the steps of collecting data of different information sources; obtaining data streams in a unified format through preprocessing; extracting high-frequency project group elements from the data stream; generating high frequency association rules, situation evaluation is carried outfor evaluation quantification; performing fusion with different evaluation systems; and obfuscating the data elements, obtaining situation values of a single device and a local network; obtaining a situation value of the whole system according to the architecture composition of the whole network; importing the situation values of different levels into a neural network model for prediction; and finally, visually displaying a prediction result, fully evaluating the whole system and each single device, establishing association between each device and each layer, and performing rule detection andrisk value calculation on different rules, thereby scientifically predicting a future system and providing valuable reference suggestions for users.
Owner:武汉思普崚技术有限公司
Landslide hazard monitoring and early warning earth surface clinometer threshold value judgment method
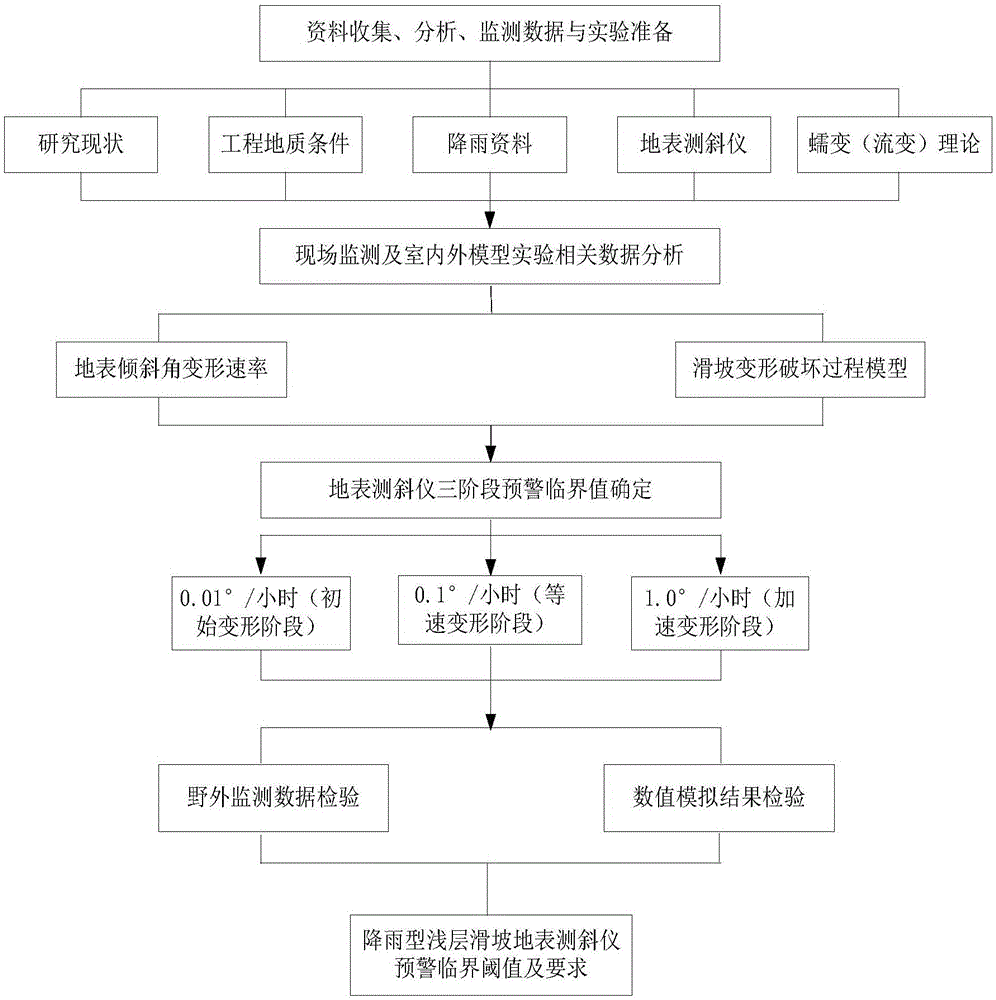
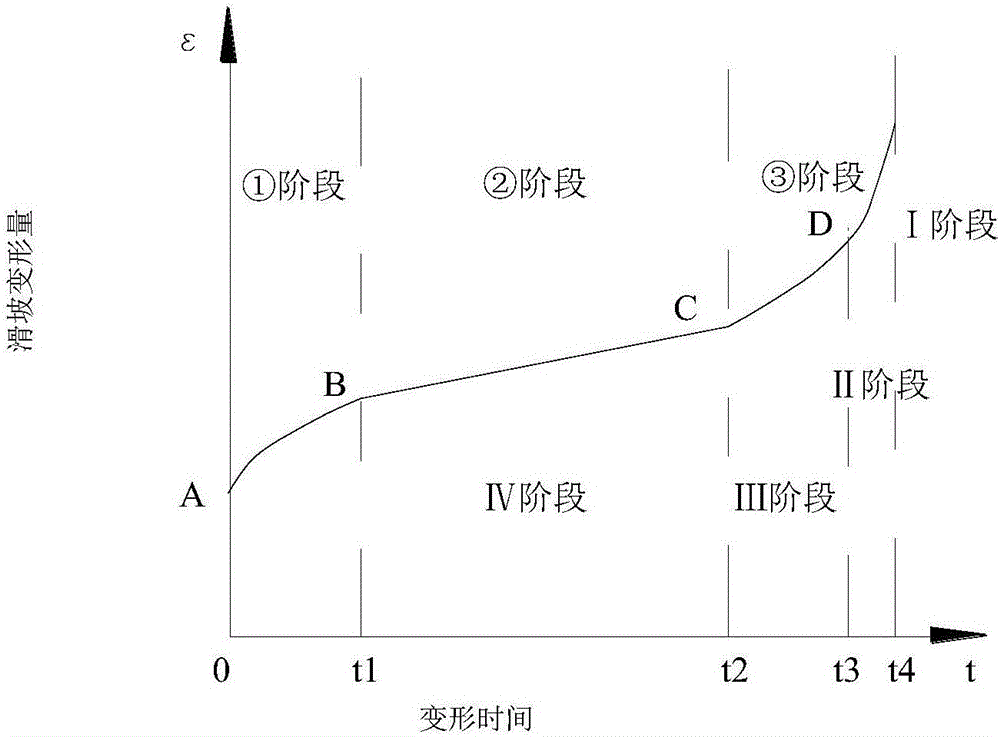
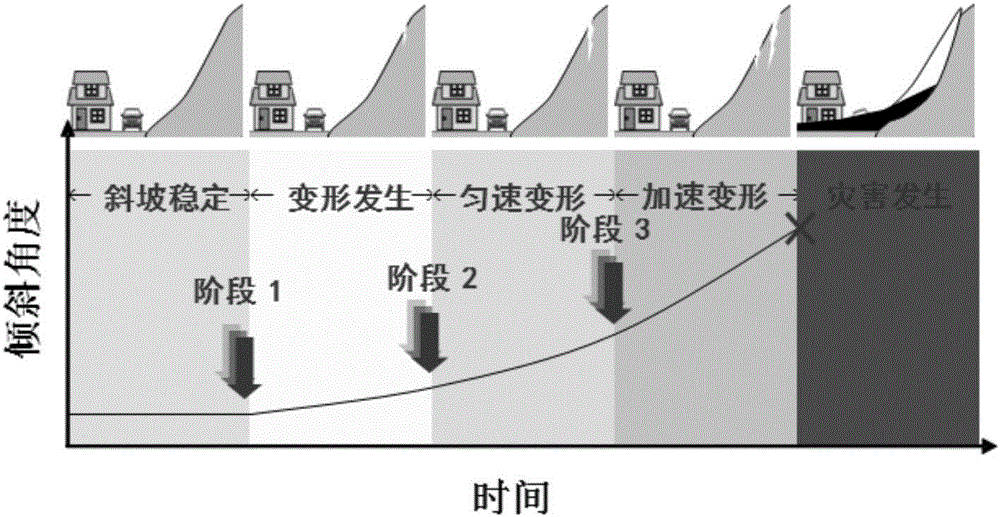
InactiveCN106295040ADesign optimisation/simulationSpecial data processing applicationsMonitoring dataProject group
The invention discloses a landslide hazard monitoring and early warning earth surface clinometer threshold value judgment method, and relates to a rainfall-induced landslide critical value early warning method. Monitoring data and in-situ experiment and model experiment examples during destruction of a large number of slopes are adopted as the basis, by means of the rock-soil body creep (rheology) theory, a landslide creep deformation process model is built, the relation between the rainfall landslide creep (rheology) three-stage and the slope earth surface inclination angle is analyzed, three-stage early warning critical reference values of a rainfall landslide earth surface clinometer are obtained, inspection is performed through a numerical simulation method and a field landslide remote monitoring and early warning system built by a project group, the requirement for four-stage deformation standards and early warning is met, and the scientific basis is provided for geological hazard monitoring comprehensive early warning technology decision making.
Owner:INST OF MOUNTAIN HAZARDS & ENVIRONMENT CHINESE ACADEMY OF SCI
Three-layer risk assessment-based drought disaster risk coping method
InactiveCN105930954AGradual reduction of regional drought riskShould applyClimate change adaptationResourcesEngineeringDrought risk
The invention discloses a three-layer risk assessment drought disaster risk coping method. The method includes the following steps that: regulatable feature and regulation approach analysis is performed on drought disaster risk factors from the four aspects of dangerousness, exposure degree, vulnerability and disaster prevention and mitigation capability involved in a drought formation process; a drought disaster one-layer risk assessment system is established; a drought disaster two-layer risk assessment system is established; a drought disaster three-layer risk assessment system is established; and drought risk coping strategies are put forward. Based on historical evolution rules and future evolution trends of drought disasters, the drought disaster risk coping method is established according to drought disaster risk region division and risk prediction results from aspects such as urban population size, regional water resource carrying capacity, industrial structure adjustment, water conservancy project group optimized layout, disaster prevention and mitigation capacity construction, soil and water resource regulation and risk prevention and control management. With the method adopted, regional drought risks can be lowered level by level.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
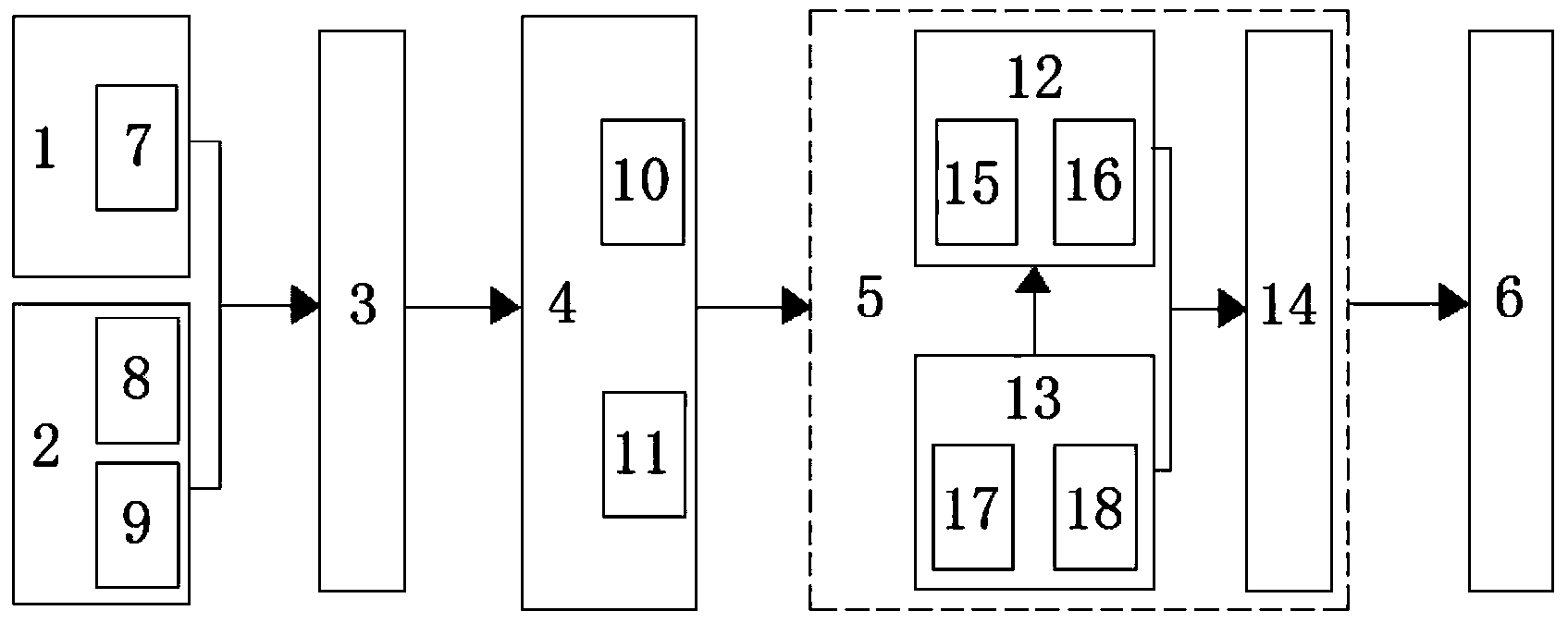
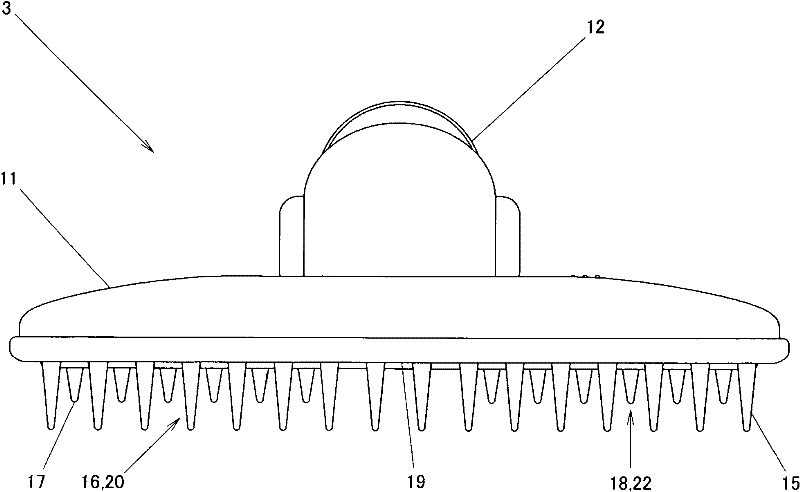
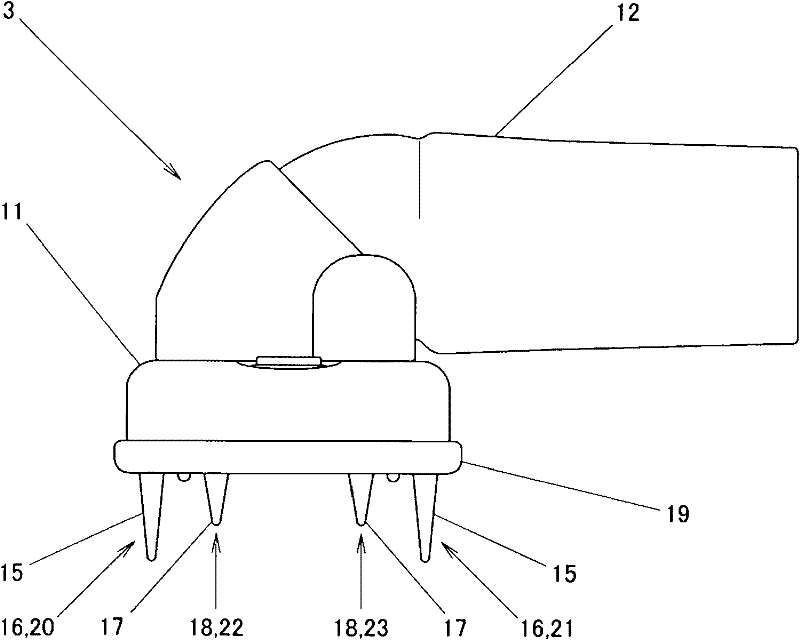
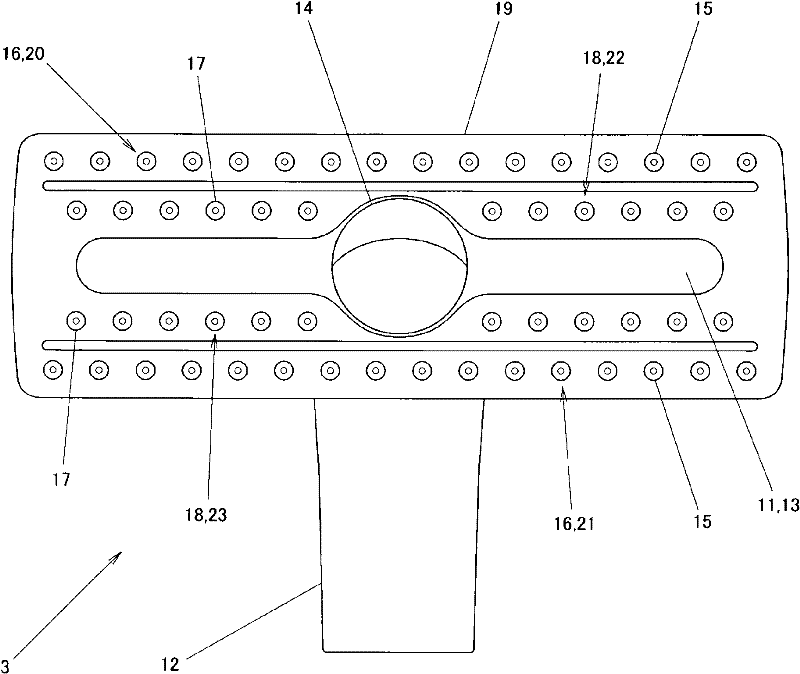
Suction Nozzle Used For Electric Cleaner
The invention discloses a suction nozzle used for an electric cleaner. The invention provides the suction nozzle used for the electric cleaner that does not damage carpet and the like and capable of cleaning hairs and furs adhering on the carpet and pads well in a gentle manner. In the invention, a long project group formed by a plurality of long projects (15) and a short project group (18) formed by a plurality of short projects (17) are arranged near a suction opening (14) of a suction nozzle body (16). The projects (15)(17) are made of flexible materials. One face of the long project group (16) bends and the other face cleans the furs and hairs deep in the carpet (c). The short project group (18) cleans furs and hairs in the surface of the carpet (c). Thus, not only the carpet (c)is damaged, but also the furs and the hairs adhered on the carpet (c) can be collected effectively. And the short project group (18) cleans the surface of the project group (18) in a rubbing manner. Thus, resistance between the project group (18) and the carpet (c) can be reduced. Therefore, even when the project number is increased, the furs and the hairs can be cleaned from the carpet(c) well in a gentle manner.
Owner:TWINBIRD CORP
Distributed situation awareness method and system
The invention provides a distributed situation awareness method and a distributed situation awareness system. The method comprises the steps of collecting data of different information sources; obtaining data streams in a unified format through preprocessing; extracting high-frequency project group elements from the data stream; generating high frequency association rules, carrying out situation evaluation for evaluation quantification; carrying out fusion with different evaluation systems; obfuscating the data elements, obtaining situation values of a single device and a local network; combining the architecture composition of the whole network; obtaining a situation value of the whole system; importing the situation values of different levels into a neural network model for prediction; and finally, visually displaying a prediction result, fully evaluating the whole distributed system and each single device, and establishing an association with each device and each layer based on thegiven situation value, thereby scientifically predicting a future system and providing valuable reference suggestions for users.
Owner:武汉思普崚技术有限公司
Method for realizing project group progress and investment general control management
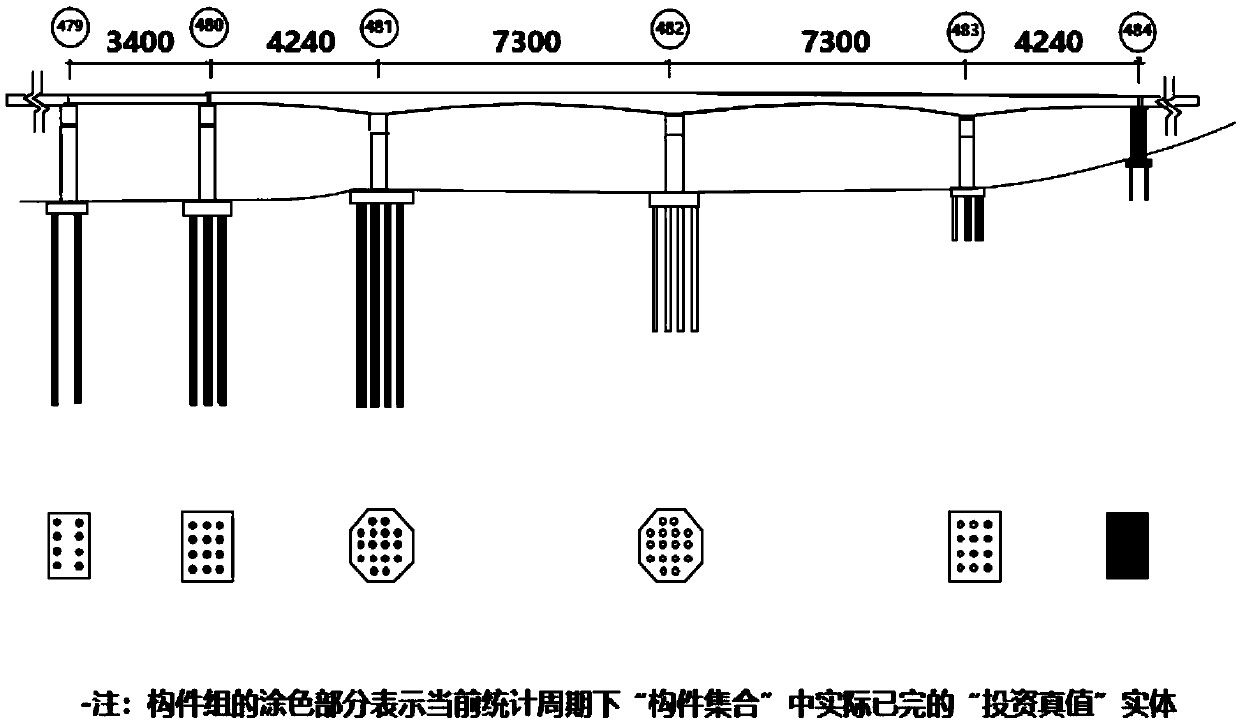
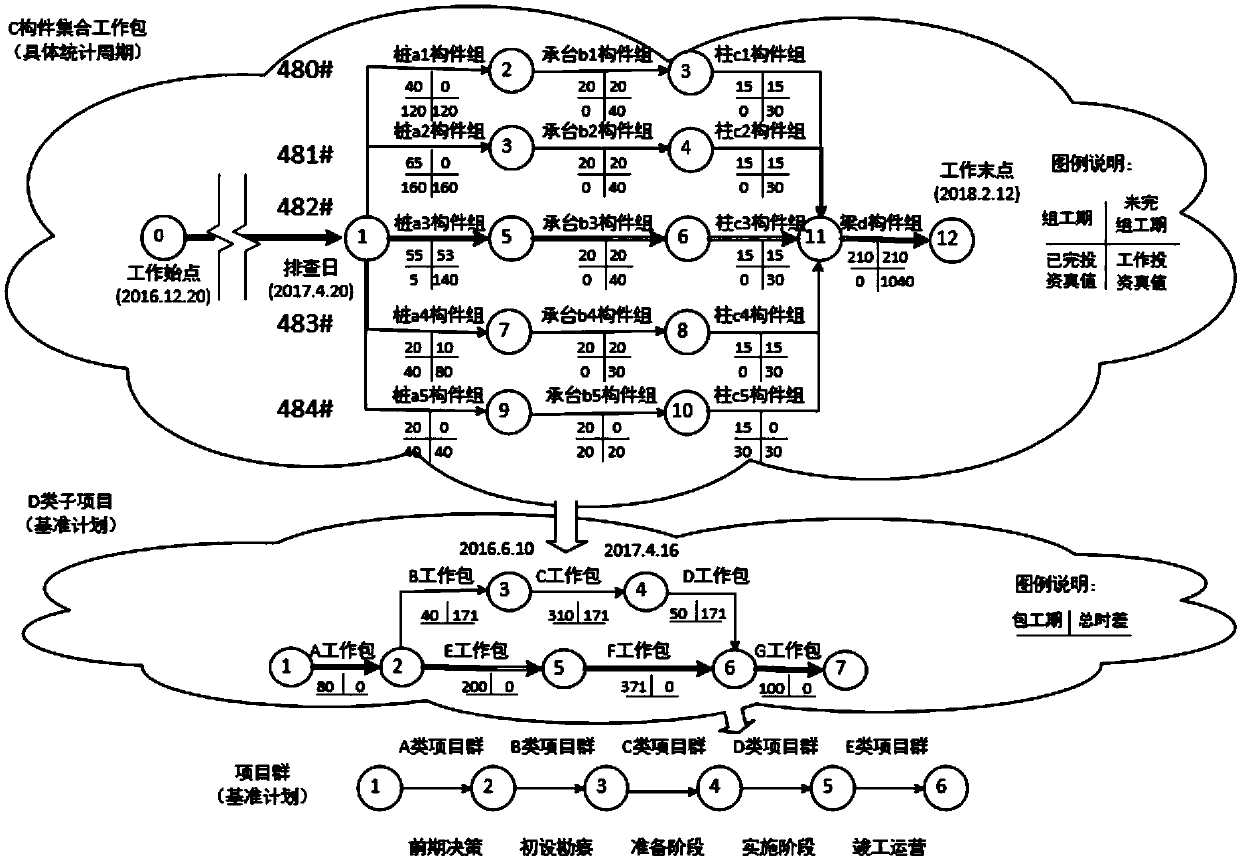
ActiveCN109636616ARealize the data deduction processProper control of precisionFinanceResourcesTruth valueProgram planning
The invention provides a method for realizing project group progress and investment general control management. According to the multi-dimensional progress information work package based on the network planning technology, information elements such as the investment truth value, the progress truth value coefficient and the restricting difficulty factors of the work package are collected, and a keygroup allowance approximation method of the package is applied to achieve the overall solution of project group progress and investment general control management. By implementing the method and thedevice, the problem that in the prior art, the complex fitting relation between project group investment and progress data cannot be deeply researched and the trap situation of the corresponding KPI index cannot be tracked is solved, and the decision-making level is effectively provided with the strategy direction for determining the current difficult restriction priority and the overall requirement for implementing the working target in the future period.
Owner:周剑毅
Distributed situation awareness calling method and device
ActiveCN110493043AEasy to callEvaluation scienceDatabase management systemsDatabase distribution/replicationData streamNetwork model
The invention provides a distributed situation awareness calling method and a distributed situation awareness calling device. The method comprises the steps of packaging interfaces for acquiring different information sources; facilitating customer calls, data streams in a unified format are obtained through preprocessing; extracting high-frequency project group elements from the data stream; generating high frequency association rules, situation evaluation is carried out for evaluation quantification; carrying out fusion with different evaluation systems; obfuscating the data elements, obtaining situation values of a single device and a local network; combining the architecture composition of the whole network; obtaining the situation value of the whole device; importing the situation values of different levels into a neural network model for prediction; and finally, visually displaying a prediction result, fully evaluating the whole distributed system and each single device, establishing association between each device and each layer, and performing rule detection and risk value calculation on different rules, thereby scientifically predicting future devices and providing valuablereference suggestions for users.
Owner:武汉思普崚技术有限公司
Page creation method and device, electronic device and computer readable storage medium
ActiveCN110333859AImprove experienceDiversified stylesSoftware engineeringProject groupComputer science
The invention provides a page creation method and device, an electronic device and a computer readable storage medium, and the method can comprise the steps: obtaining a first view container and project configuration information, and the project configuration information comprising the number of projects and project content information of a project group located at a first position; arranging at least one second view container in the first view container according to the number of the items, and the second view container being used for one item in the item group located at the first position;acquiring style information of the first view container and style information of each second view container; and generating a project group located at the first position according to the project content information, the style information of the first view container and the style information of each second view container. User-defined development and creation of the display style of the applet arerealized, so that styles are diversified, and the experience of using the applet by a user is improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
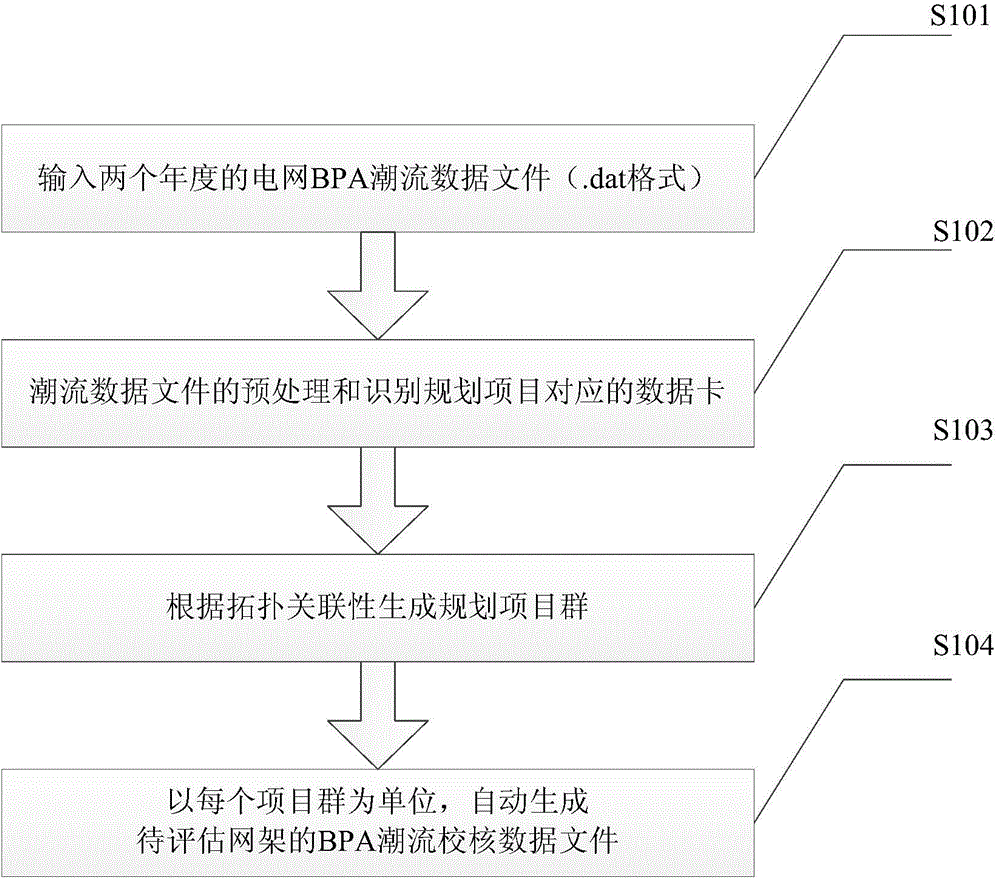
Automatic power flow check file generation method for power grid planning project
ActiveCN104484546AAvoid workloadAvoid operabilitySpecial data processing applicationsPower flowProgram planning
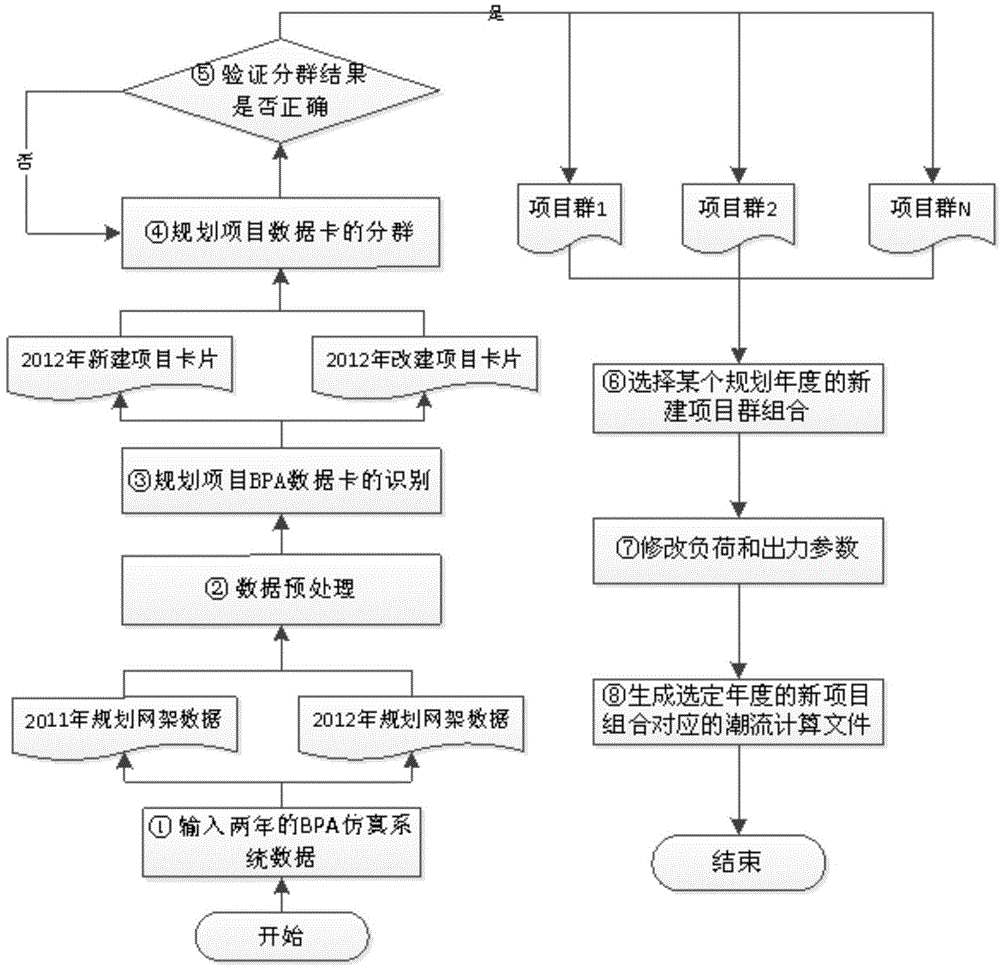
The invention discloses an automatic power flow check file generation method for a power grid planning project. The automatic power flow check file generation method for the power grid planning project includes steps that 1, inputting power grid BPA initial power flow data files of two years; step 2, pre-processing data of the power grid BPA initial power flow data files of the two years, and using a maximum common sub-graph algorithm to automatically compare the data to identify BPA check data cards corresponding to the planning project; step 3, judging the topological connection relations between the BPA check data cards, and generating a plurality of planning project groups according to the topological relevance; step 4, automatically generating a BPA power flow check data file of a net rack to be evaluated. The automatic power flow check file generation method for the power grid planning project can be used for the planning and design institute to optimize planning schemes in the design process and can also be used for the power grid planning management department to objectively evaluate the power grid planning schemes of the planning and design institute.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Project management method and device, electronic equipment, storage medium and product
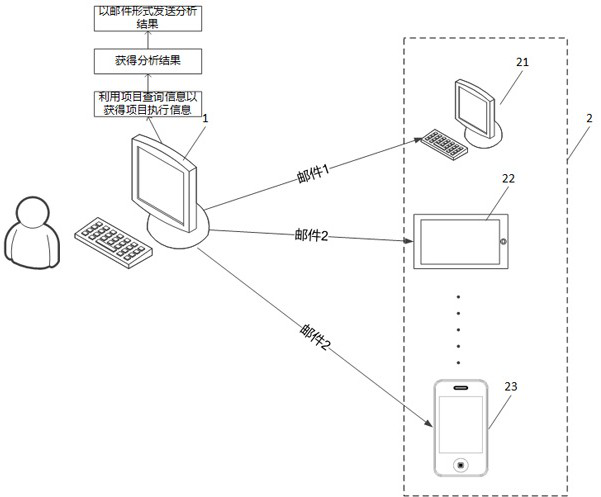
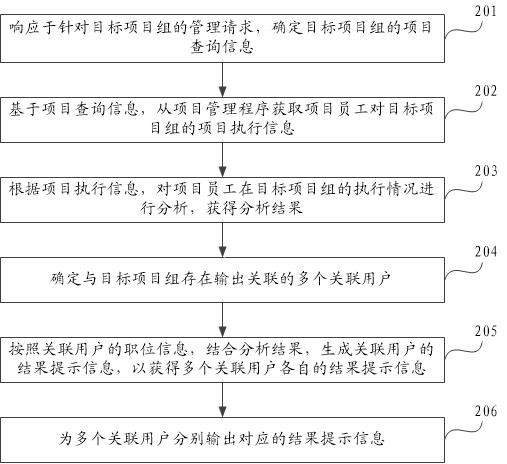
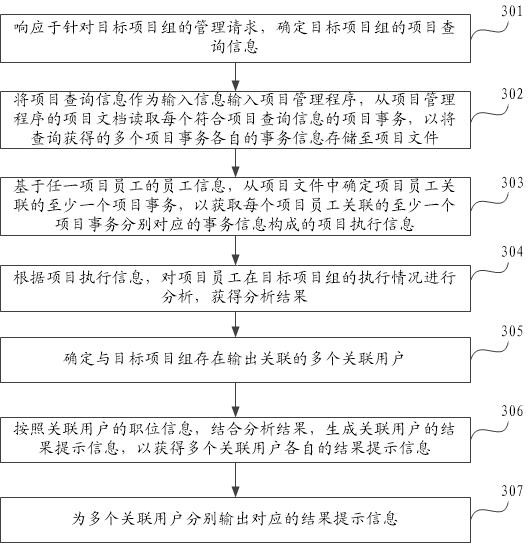
PendingCN114092056ARealize automatic queryAutomate analysisOffice automationInput/output processes for data processingProject managementKnowledge management
The embodiment of the invention provides a project management method and device, electronic equipment, a storage medium and a product, and the method comprises the steps of responding to a management request for a target project group, and determining the project query information of the target project group, where the project query information comprises a project group name and employee information of project employees; querying project execution information of the project employee on the target project group based on the project query information; according to the project execution information, analyzing the execution condition of the project employee in the target project group to obtain an analysis result; determining a plurality of associated users having output association with the target project group; according to the position information of the associated users, forming result prompt information of the associated users in combination with the analysis result, so that respective result prompt information of the multiple associated users is obtained; and respectively outputting corresponding result prompt information for the plurality of associated users. The problem of low project management efficiency is solved.
Owner:上海豪承信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com