Ic Card for Encryption or Decryption Process and Encrypted Communication System and Encrypted Communication Method Using the Same
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
>>
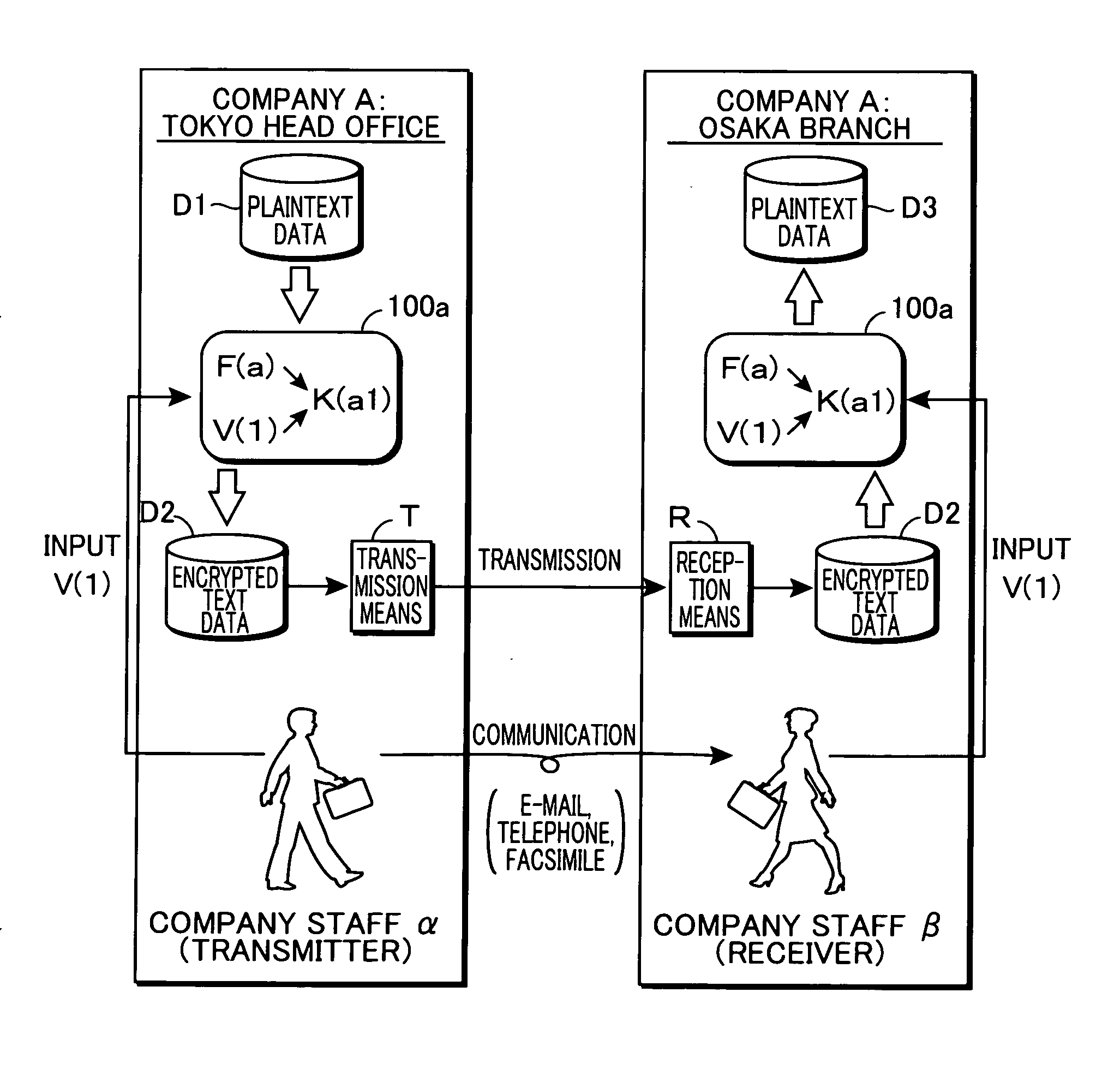
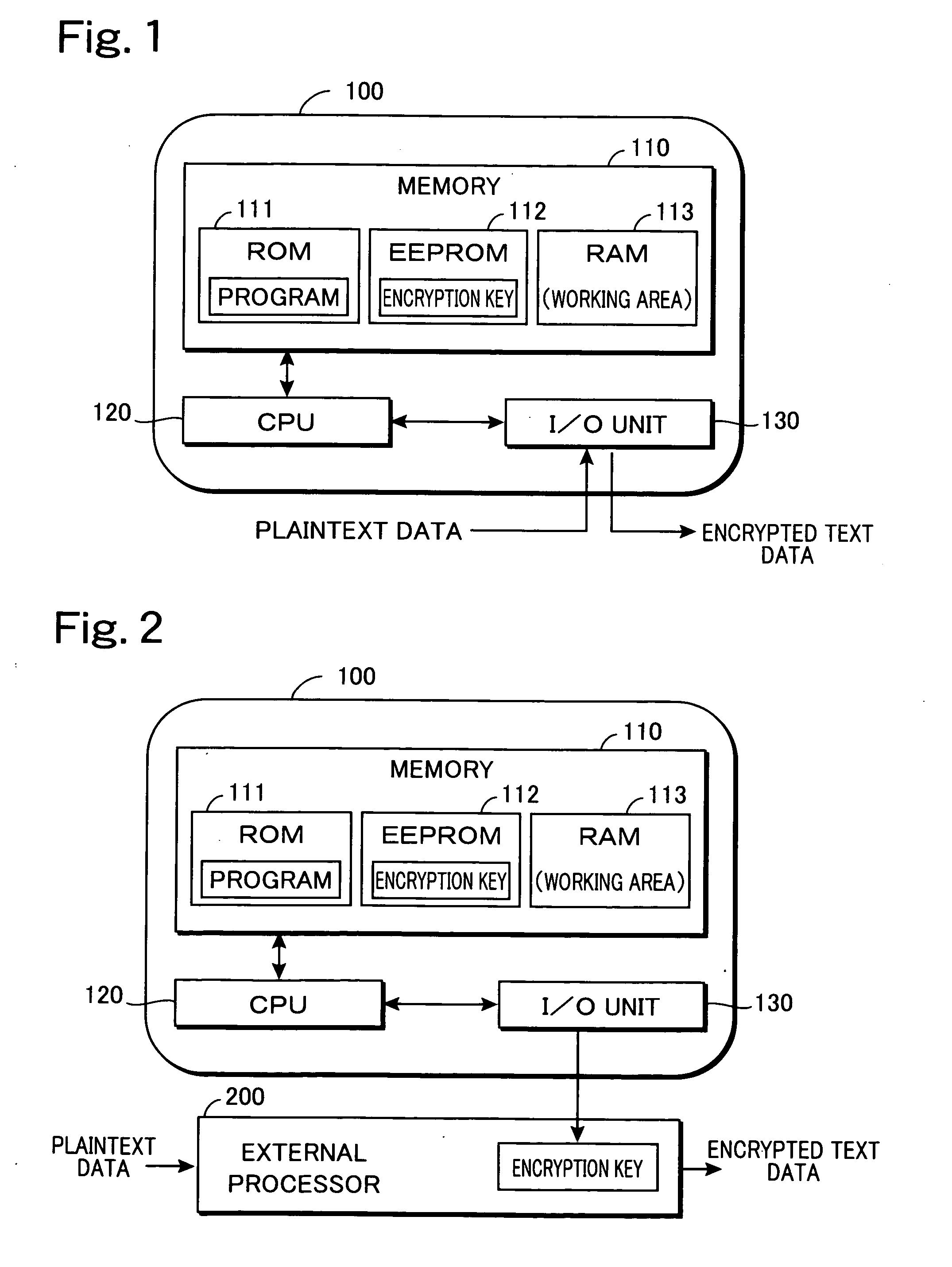
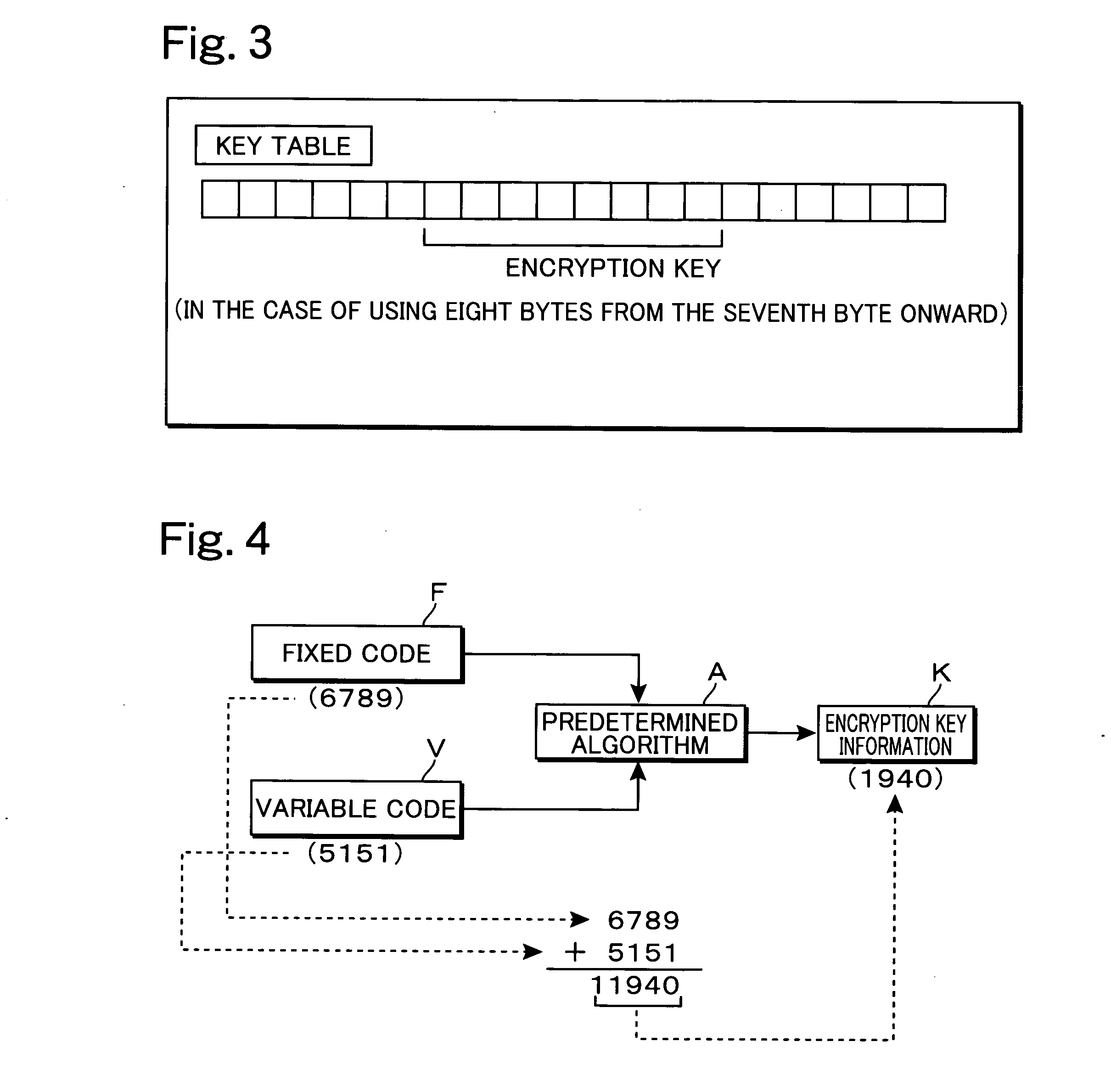
[0041] An encrypted communication system according to the present invention is a system for performing encrypted communication using IC cards for an encryption or a decryption process. Thus first, an arrangement of a general IC card that stores encryption key information and processes of encryption and decryption using this IC card shall be described briefly. FIG. 1 is a block diagram for describing an arrangement of a general IC card 100, that is widely used presently, and an encryption process using this IC card 100. As illustrated, this IC card 100 has a memory 110, a CPU 120, and an I / O unit 130. In this illustrated example, memory 110 is arranged from a ROM 111, which is a non-rewritable, nonvolatile memory, an EEPROM 112, which is a rewritable, nonvolatile memory, and a RAM 113, which is a rewritable, volatile memory. Programs for executing various processing functions that IC card 100 is equipped with are stored in ROM 111, and various data to be recorded in IC card 100 are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com