A wireless network attack detection method based on mathematical morphology
A mathematical morphology, wireless network technology, applied in wireless communication, electrical components, security devices, etc., can solve the problems of high layout cost and computational overhead, high key energy consumption, security restrictions, etc., to reduce the layout cost and Calculation overhead, simple calculation method, and the effect of reducing detection cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to facilitate the following description, first give the following noun explanation:
[0029] LQI: Link Quality Indicator, stands for link quality indicator, used to indicate the level of communication connection strength, the unit is dBm. LQI can be directly read in the header file of each data packet received. It is a parameter sent by default when sending data. Its data is easy to collect and extract, and it is an integer between 0-255.
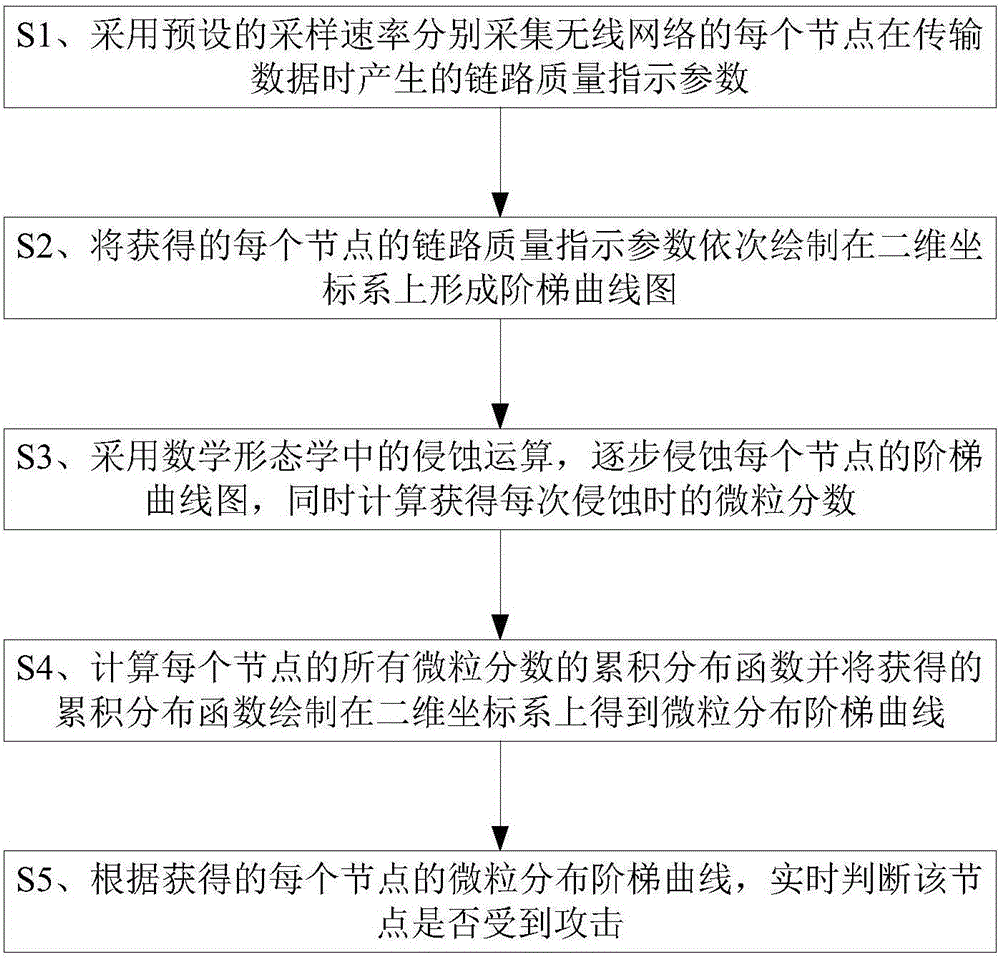
[0030] Reference figure 1 The present invention provides a wireless network attack detection method based on mathematical morphology, including:
[0031] S1. Use a preset sampling rate to separately collect link quality indicator parameters generated by each node of the wireless network when transmitting data;
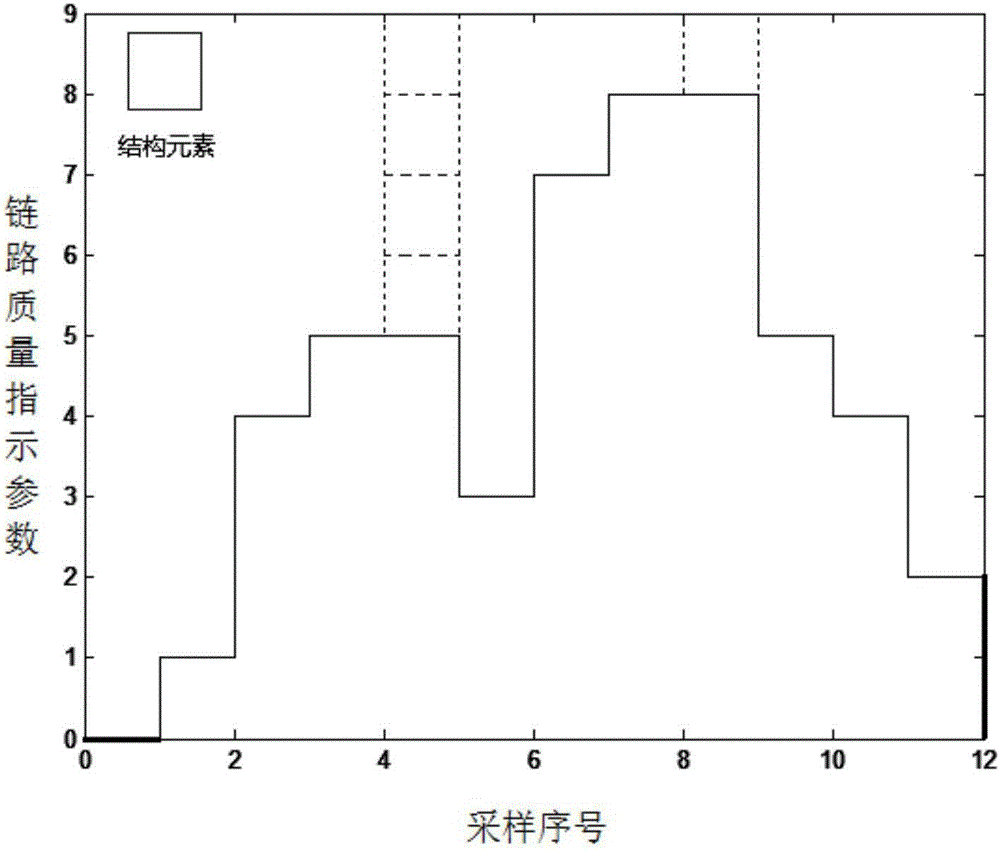
[0032] S2. The obtained link quality indicator parameters of each node are drawn in sequence on a two-dimensional coordinate system to form a step curve diagram;
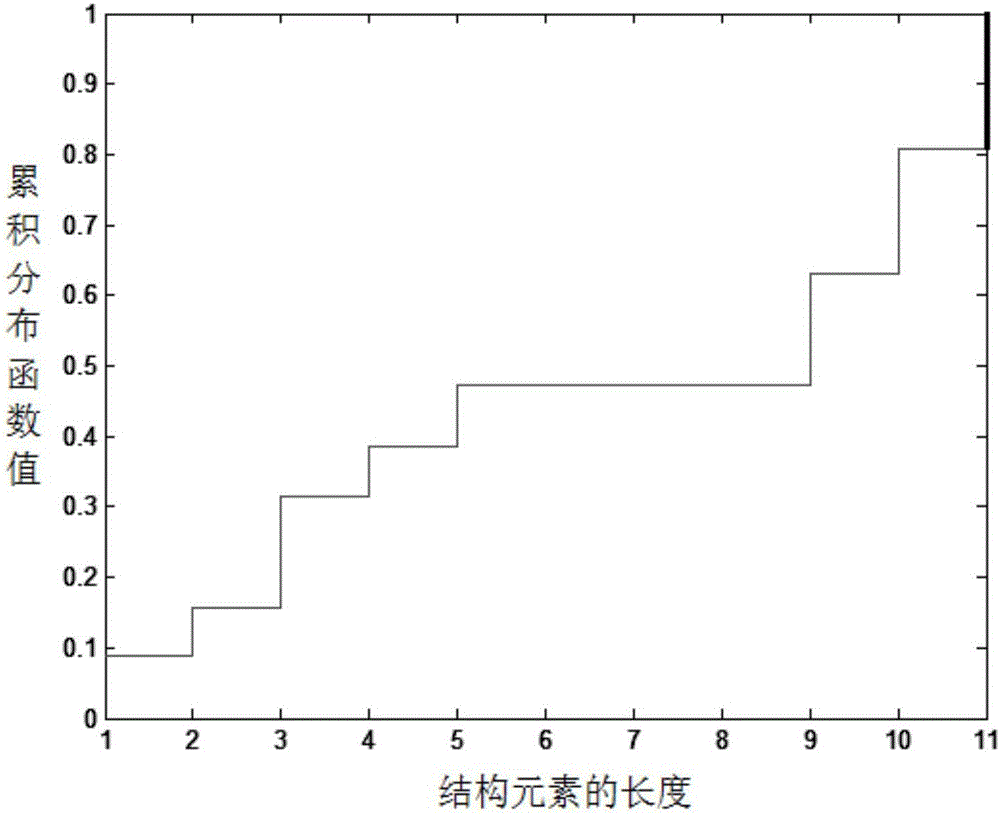
[0033] S3. Use the erosion calculation in mathematical morpho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com