Application access method and mobile terminal
An application program access and application program technology, applied in the field of mobile communication, can solve the problem of incapable mobile terminal protection, etc., and achieve the effect of improving security and privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
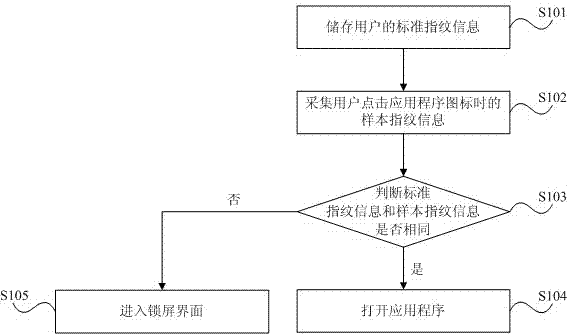
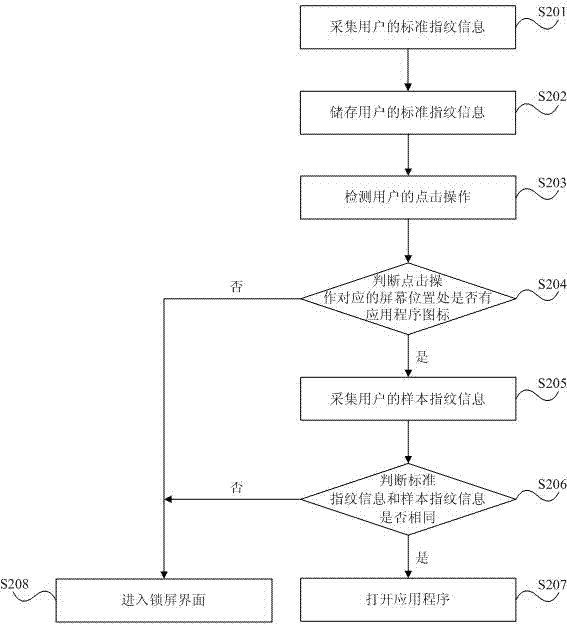
[0040] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings. It should be noted that the technical features or combinations of technical features described in the following embodiments should not be regarded as isolated, and they can be combined and combined with each other to achieve better technical effects. In the drawings of the following embodiments, the same reference numerals appearing in each drawing represent the same features or components, which can be applied in different embodiments.
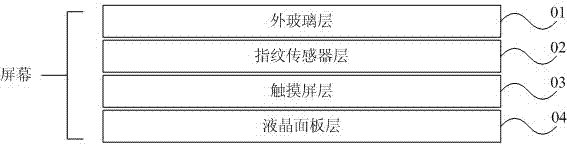
[0041] Fingerprints refer to the uneven lines on the skin on the front of the end of a human finger. The lines are regularly arranged to form different patterns.
[0042] The overall features of fingerprints refer to those features that can be directly observed by human eyes, including pattern shape, pattern area, core point, triangle point, and number of lines. According to the direction and distribution of the ridges, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com