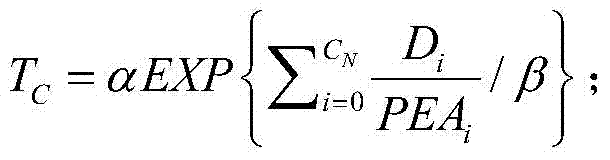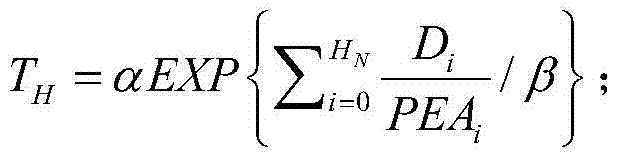A Code Security Evaluation Method Based on Defect Analysis
A security evaluation and defect analysis technology, applied in software testing/debugging, etc., can solve problems such as increasing the complexity and difficulty of code security evaluation, lack of evaluation factors, and generalization of code security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Embodiments of the present invention are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals designate the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary and are intended to explain the present invention and should not be construed as limiting the present invention.
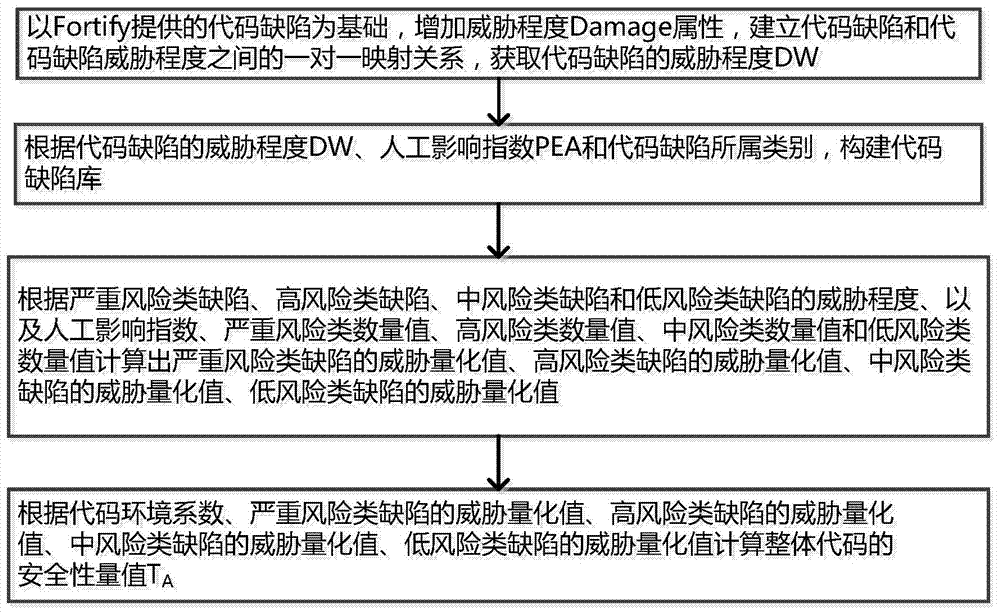
[0035] A code security evaluation method based on defect analysis provided by the present invention, the specific steps are as follows figure 1 Shown:
[0036] Step 1: Obtain the threat level DW of the code defect WA:
[0037] ①: Establish code defect classification through Fortify, including serious risk defect Critical, high risk defect High, medium risk defect Medium and low risk defect Low;
[0038] Code defect classification: AttributeSet = {Critical, Hight, Medium, Low};
[0039] Code defect classification set: Attribute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com