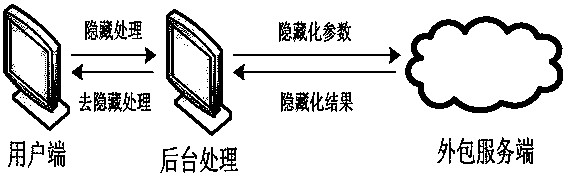
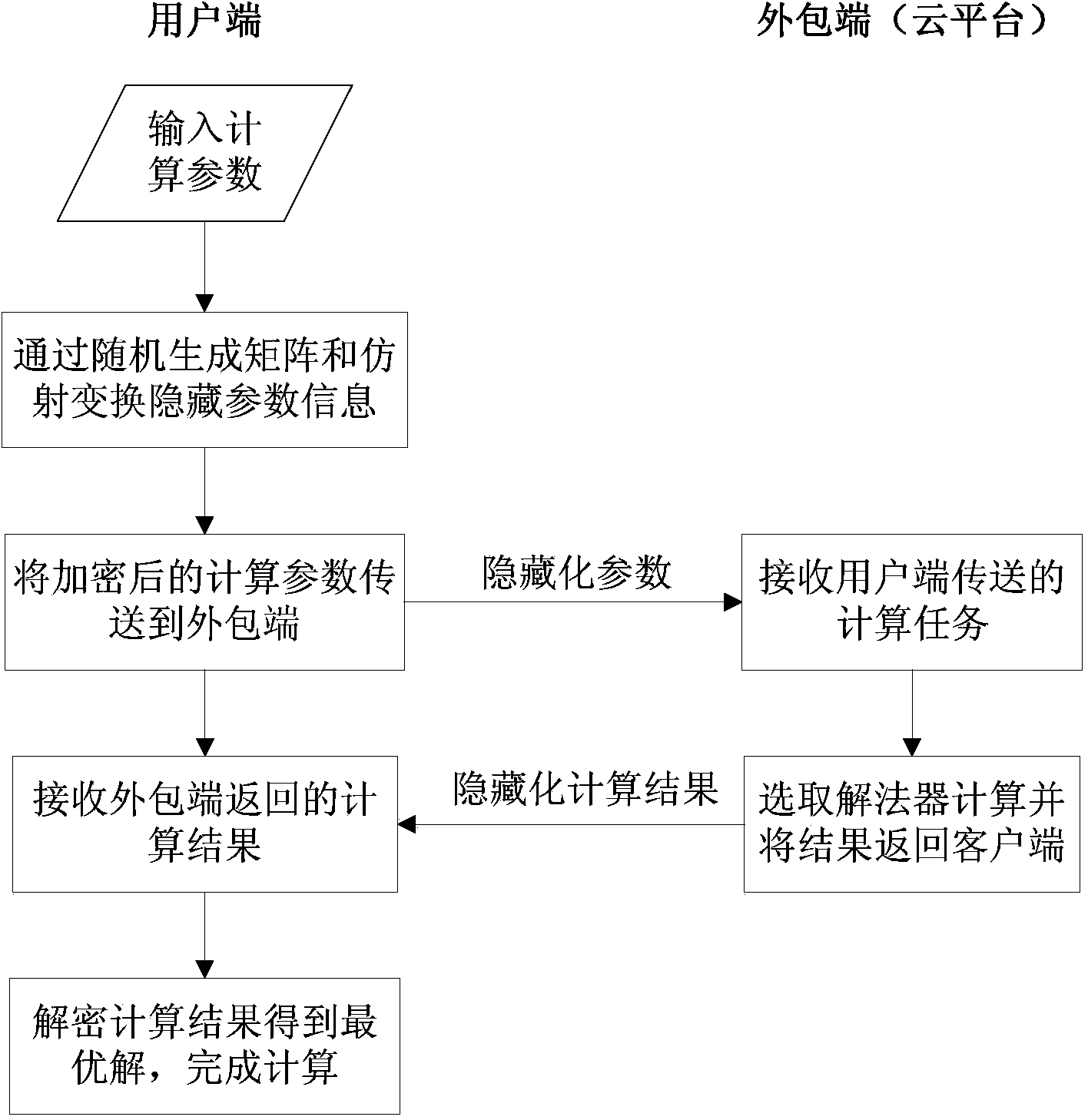
Method for protecting privacy in convex quadratic programming outsourcing on basis of affine transformation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Below in conjunction with accompanying drawing, the present invention is described in further detail:
[0027] At present, when users solve scientific computing problems such as convex quadratic programming, due to the complexity of the real problems, the scale is usually large, which exceeds the processing capacity of the PC, and requires users to spend a lot of money to build computing clusters and require dedicated personnel to maintain equipment. With the popularization of public cloud platforms and the concept of pay-as-you-go, the outsourcing of scientific computing tasks has great market potential, and the privacy and security of users is one of the many problems that need to be solved. The protection method of the present invention based on the affine transformation of the convex quadratic programming outsourcing calculation provides such a safety protection mechanism, the coordinate system of the original problem is converted to another domain through the affine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com