IP voice steganography method based on speed modulation
A speed and voice technology, applied in the field of covert communication, which can solve the problems of personal privacy theft and abuse, communication content theft or tampering, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below through specific embodiments.
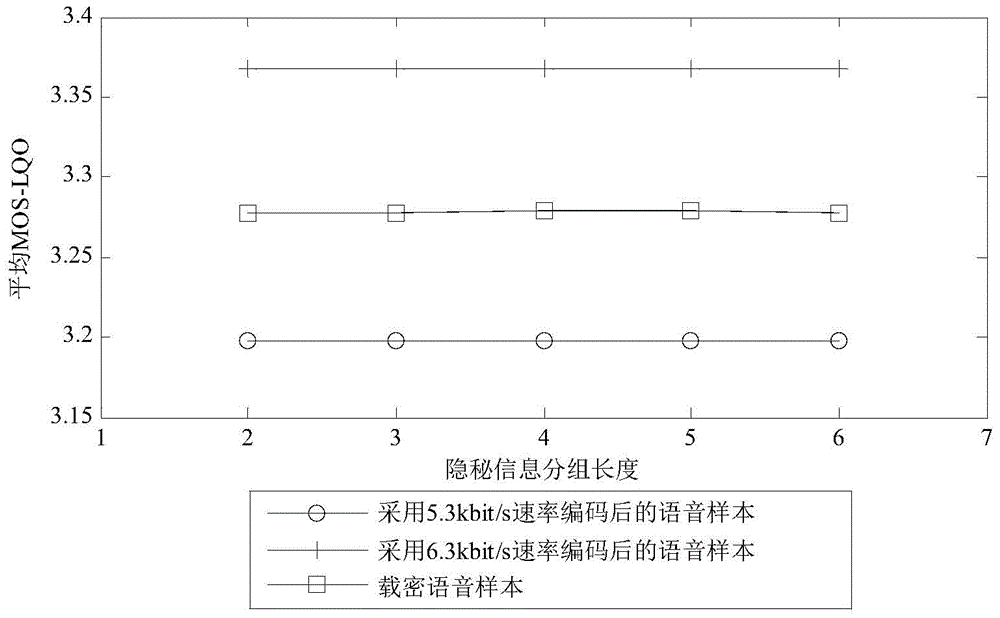
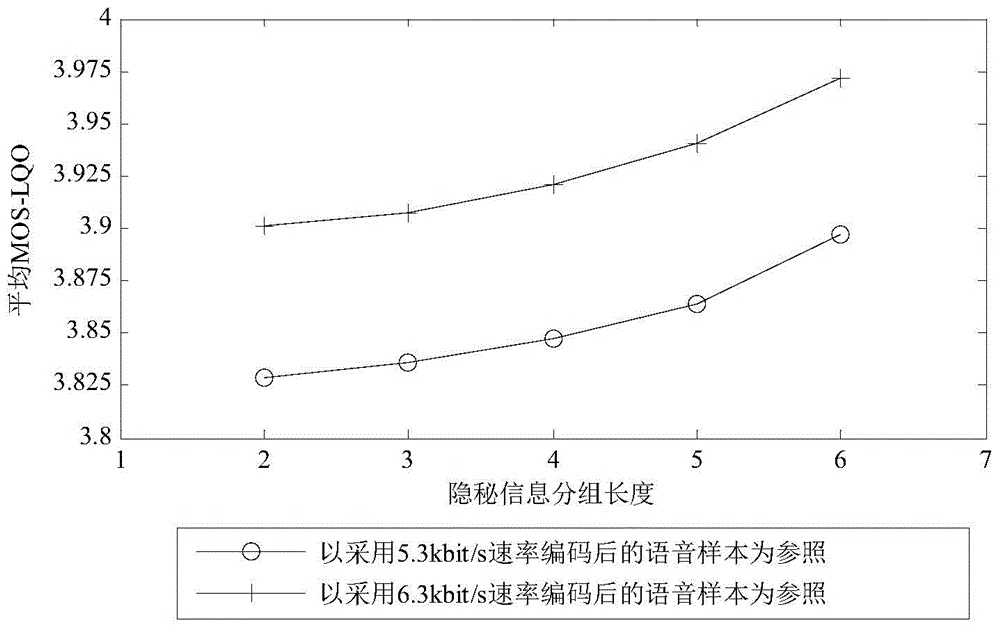
[0039] The present invention is applicable to any speech coder with variable rate coding function, such as ITUG.722.1, ITUG.723.1, IETFiLBC, GSMRTE-LTP and AMR, etc., and the widely used ITUG.723.1 speech coding will be taken as an example below, combined with the attached Figure further illustrates the present invention.
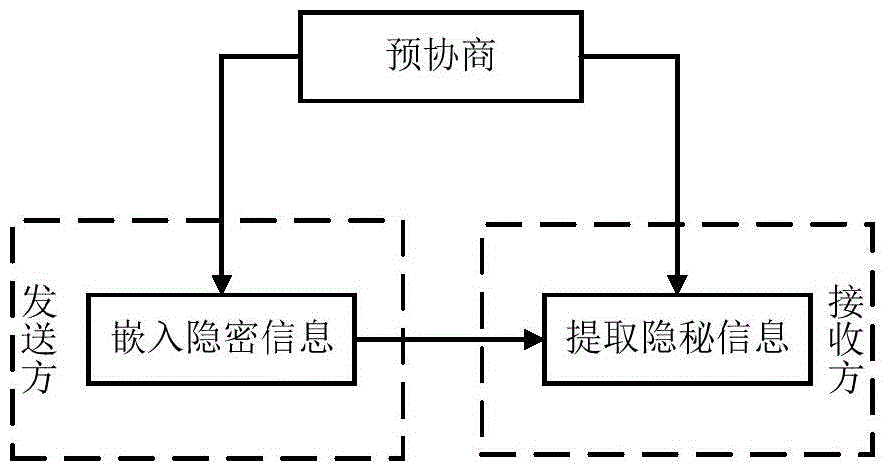
[0040] The processing flow of the present invention is as attached figure 1 As shown, it includes the pre-negotiation step, the step of embedding secret information and the step of extracting secret information.
[0041] 1. Pre-agreement steps: The communication parties pre-agreed that the speech coder used in the communication process is ITUG.723.1; agree to use low rate (5.3kbit / s) and high rate (6.3kbit / s) for voice communication, and use the high rate (6.3kbit / s) and low rate (5.3kbit / s) are marked as "0" and "1" respectively, and it is agreed to start transmi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com