Encryption method and device
An encryption method and encryption device technology, applied in the field of communication, can solve problems such as unreadable data, data confusion, severe information security, etc., and achieve the effect of improving management efficiency and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
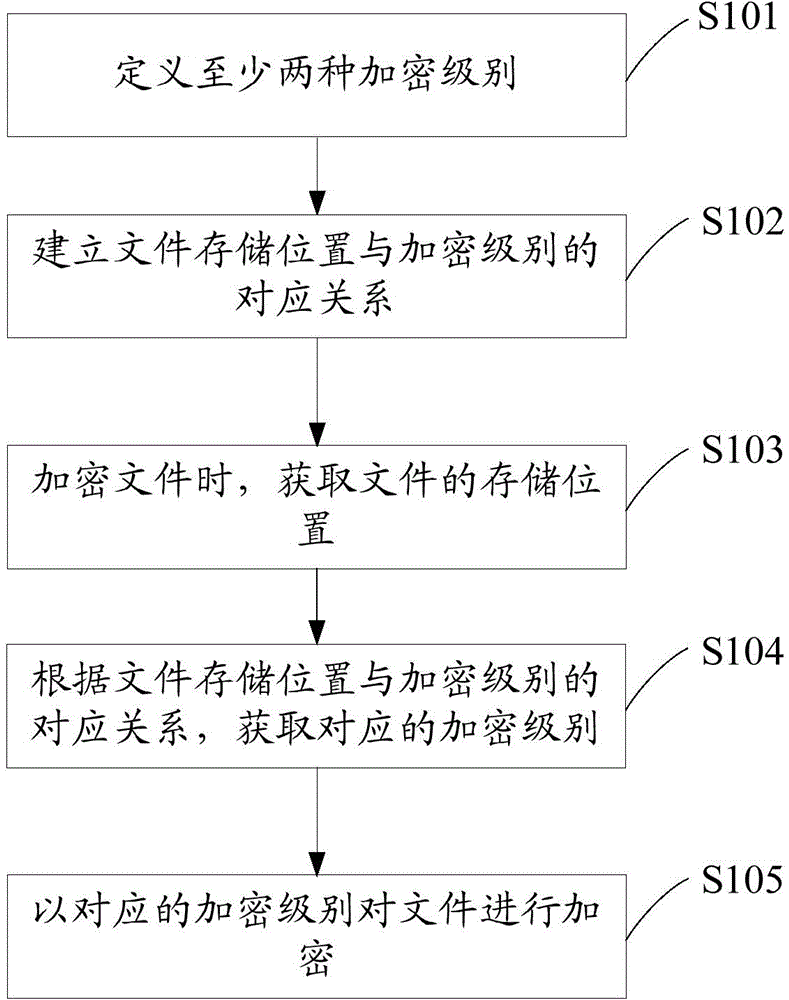
[0028] See figure 1 , The first embodiment of the encryption method of the present invention is proposed. The encryption method includes the following steps:
[0029] Step S101: Define at least two encryption levels
[0030] For example, three levels of encryption can be defined, namely primary encryption, secondary encryption, and tertiary encryption. The primary encryption only encrypts the file header, the secondary encryption encrypts the file content, and the tertiary encryption simultaneously encrypts the file. The header and file contents are encrypted. Or, primary encryption uses general key encryption, which can be decrypted by users with general authority; secondary encryption uses intermediate key encryption, and users with intermediate authority can decrypt; level three encryption uses advanced key encryption, and users with advanced authority can decrypt. Of course, you can define more encryption levels as needed.
[0031] Step S102: Establish a correspondence between ...
no. 2 example
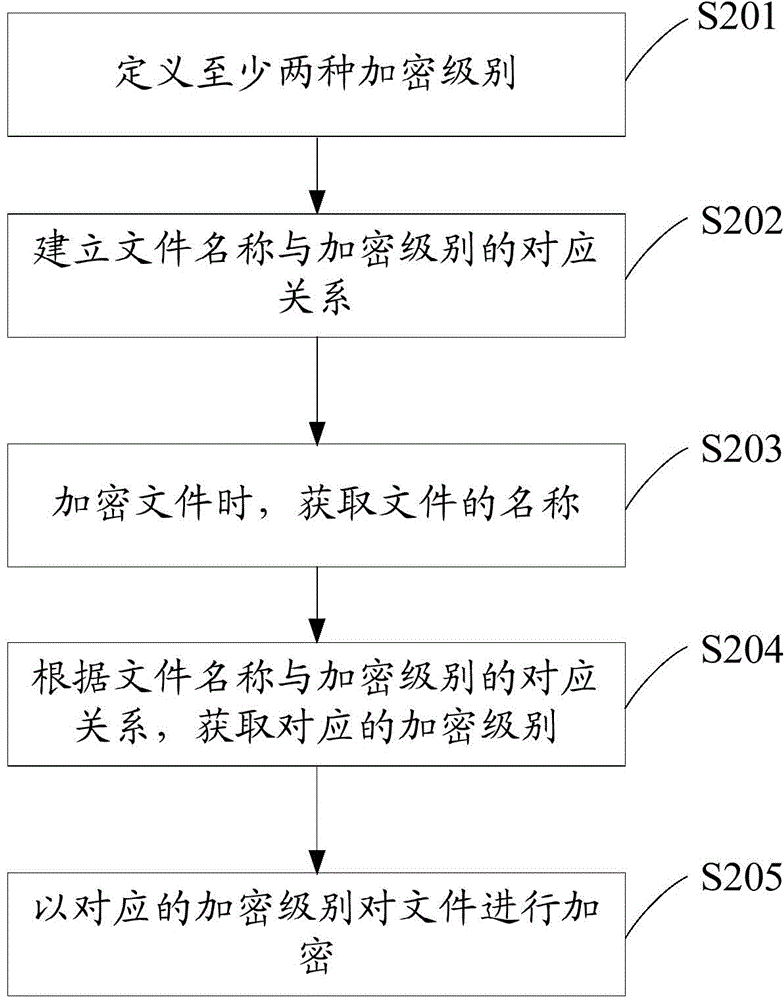
[0039] See figure 2 , The second embodiment of the encryption method of the present invention is proposed. The encryption method includes the following steps:
[0040] Step S201: Define at least two encryption levels
[0041] Step S202: Establish the correspondence between the file name and the encryption level
[0042] This embodiment uses the file name in the file attribute to establish a correspondence with the encryption level.
[0043] Specifically, it can be the specific characters "#1", "#2", and "#3" in the file name, corresponding to primary encryption, secondary encryption, and tertiary encryption, respectively; or, the keyword "important" in the file name "," "very important" and "very important" correspond to level 1 to level 3 encryption respectively.
[0044] Step S203: Obtain the name of the file when encrypting the file
[0045] Step S204: Obtain the corresponding encryption level according to the correspondence between the file name and the encryption level
[0046] Ste...
no. 3 example
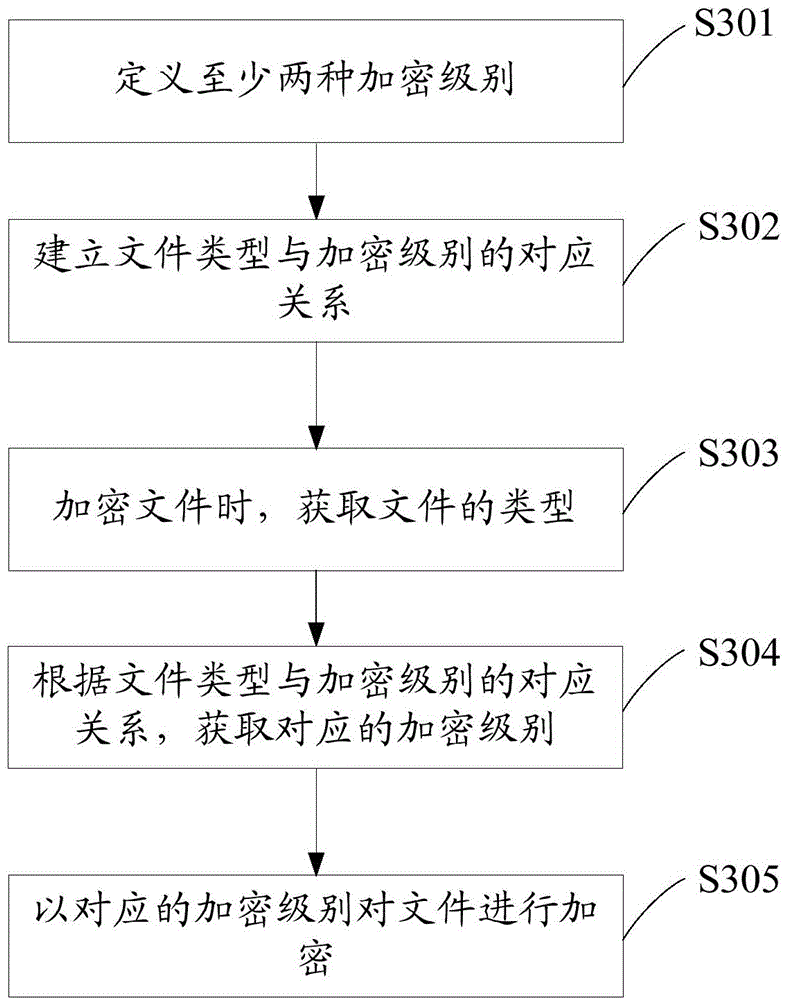
[0048] See image 3 , The third embodiment of the encryption method of the present invention is proposed. The encryption method includes the following steps:
[0049] Step S301: Define at least two encryption levels
[0050] Step S302: Establish the correspondence between the file type and the encryption level
[0051] This embodiment uses the file type in the file attribute to establish a corresponding relationship with the encryption level. The file type includes text files, multimedia files, application files, etc., among which text files can be subdivided into txt files, doc files, pdf files, etc. Files can be subdivided into graphic files, audio files, video files, etc.
[0052] Specifically, you can set text files to correspond to primary encryption, application files to correspond to secondary encryption, and multimedia files to correspond to tertiary encryption; or, doc files in text files correspond to primary encryption, and audio files in multimedia files correspond to Cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com