Embedding and Extraction of Copyright Characters in Vector Graphics
A technology of vector graphics and characters, which is applied in the field of embedding and extraction of copyright characters of vector graphics, which can solve the problems of losing copyright character fragments, increasing the difficulty of copyright characters resisting attacks, and having no transformation domain, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
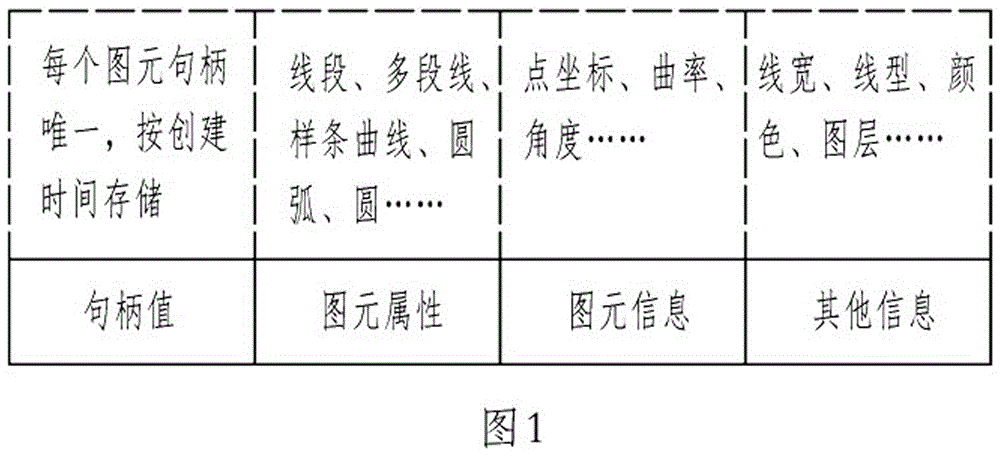
[0054] 1. Embedding
[0055] Step 1.1
[0056] In this embodiment, the vector graphic to be embedded with copyright characters includes N graphic elements, and its length is N. The copyright holder is represented by the string "#xmhd". In order to prevent the character string from being illegally identified, the character string "#xmhd" is encrypted. Preferably, the existing encryption algorithm uses the character string "#xmhd" as input to obtain an encrypted character string. In this embodiment, the length of the encrypted character string remains unchanged, that is, 5 bytes. Divide the encrypted character string into L consecutive digital fragments, that is, the character fragment e, and obtain the 1 ~e L The character sequence E, the number of bits of the character fragment e is its length t. For security reasons, the character fragment e can also be further encrypted, which is omitted in this embodiment. Calculate the ratio of the length N of the vector graphics to ...
Embodiment 2
[0145] 1. Embedding
[0146] Compared with the first embodiment, the steps 1.1 to 1.4 of this embodiment are the same; starting from step 1.5, the difference is that the first embodiment is to modify the primitives whose alignment order is earlier, and this embodiment is to modify the primitives For the graphics primitives in the center and the sequence, and thus different, the extraction steps of this embodiment are different. When this embodiment embeds traversal, it also embeds one by one according to the character sequence E. After embedding a set of character sequence E, continue to embed the traversal point and continue to embed a new set of character sequence E, the same as Embodiment 1. After the embedding of this embodiment is completed, the entire vector The graph contains G complete character sequences E.
[0147] This implementation intends to use Figure 10 The 12 primitives in the graph are exaggerated, and the schematic diagram changes before and after embeddi...
Embodiment 3
[0152] This embodiment is not intended to exemplify embedding and extraction. This embodiment mainly explains how the present invention can resist geometric attacks and why it is robust to interference attacks.
[0153] 1. Resistance to geometric attacks
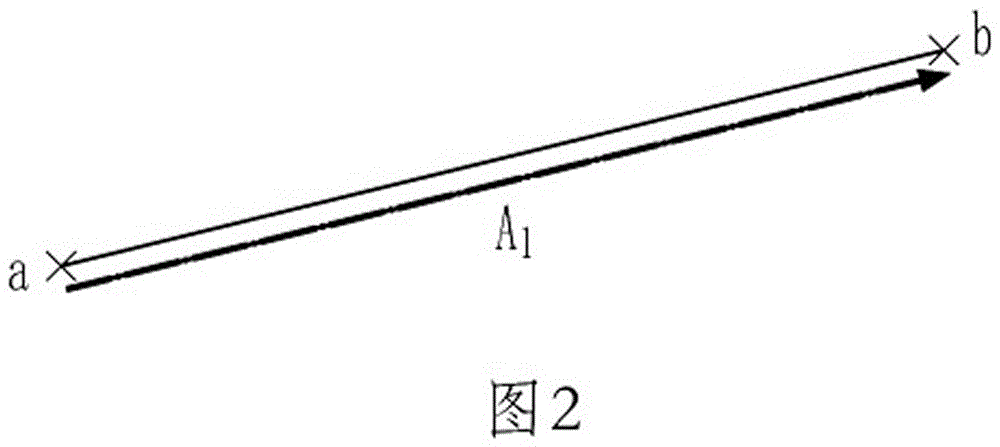
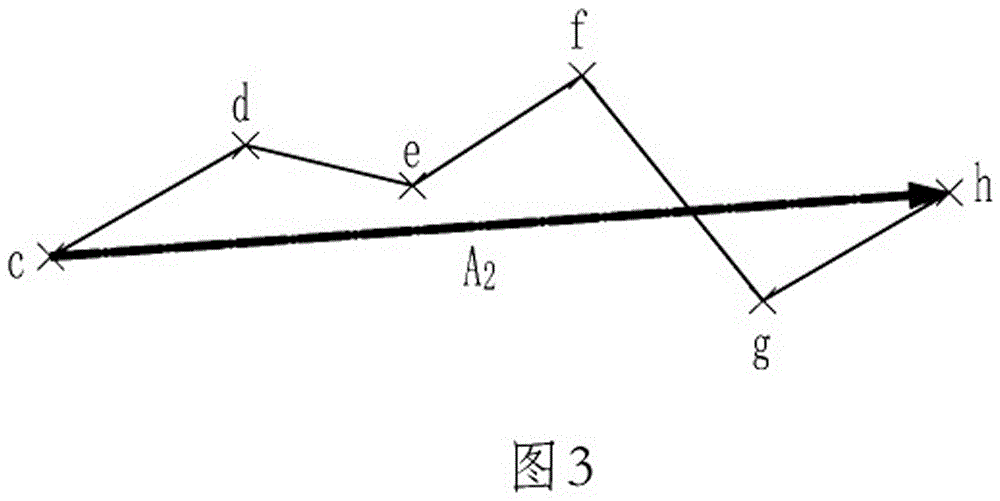
[0154] Geometry attacks refer to global scaling, rotating, translating, or a combination of the above operations on the entire vector graphics, in order to modify the primitive function parameters and intend to destroy the character fragments embedded in the function parameters; due to global scaling, rotating, and translating Or after the combination operation, although the graph element function parameters are changed, the graph as a whole remains unchanged, which does not affect the reading, so this method is the first choice for attackers.
[0155] The present invention constructs a complex vector operator, calculates the complex ratio of the primitive pair, and embeds character fragments into the complex ratio. Fragmen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com