Method and device for monitoring leakage of memory
A memory leak and memory technology, applied in the electronic field, can solve the problems of missing the scene of the memory leak problem, the memory cannot determine the specific operation situation, etc., and achieve the effect of simple steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
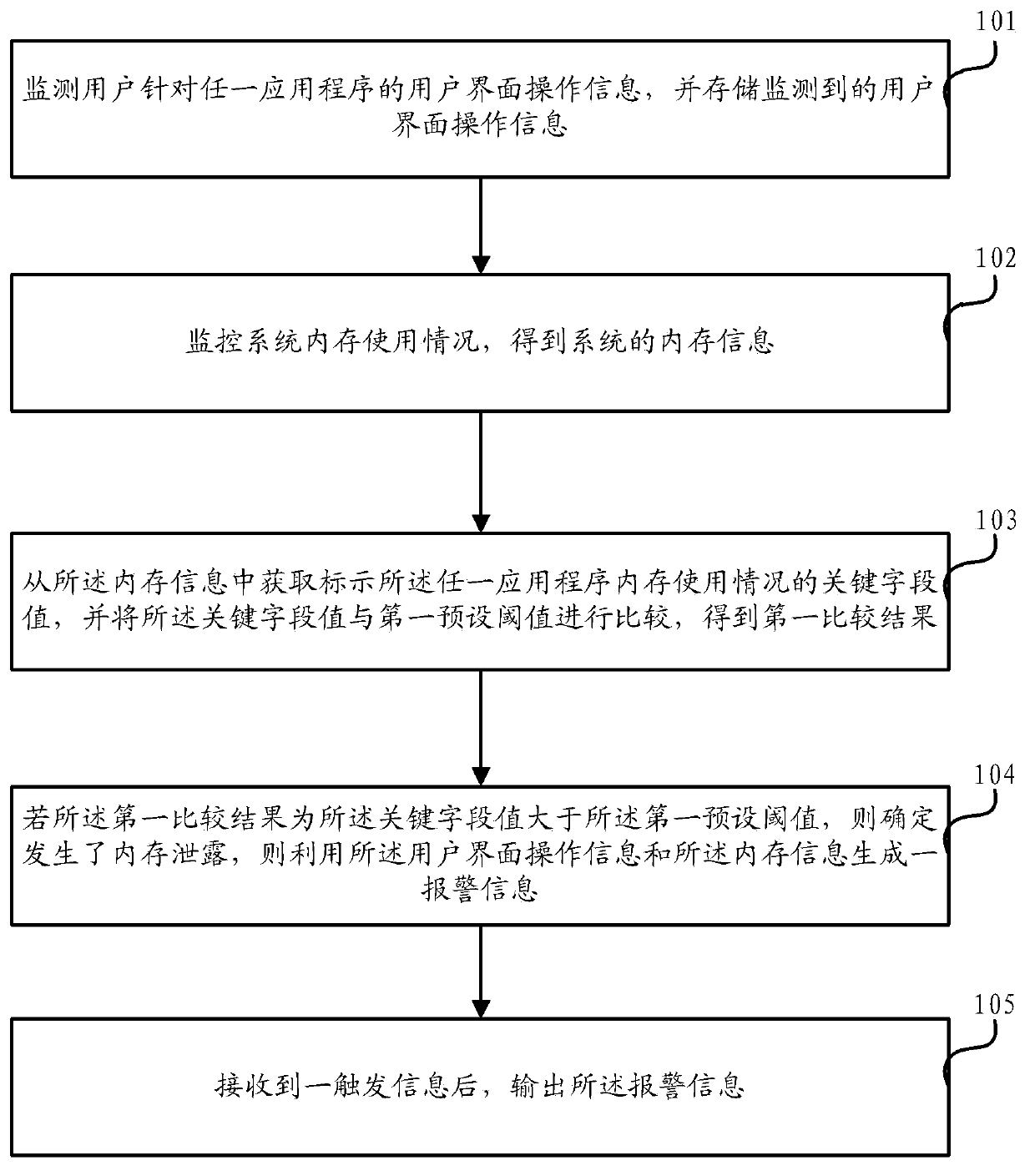
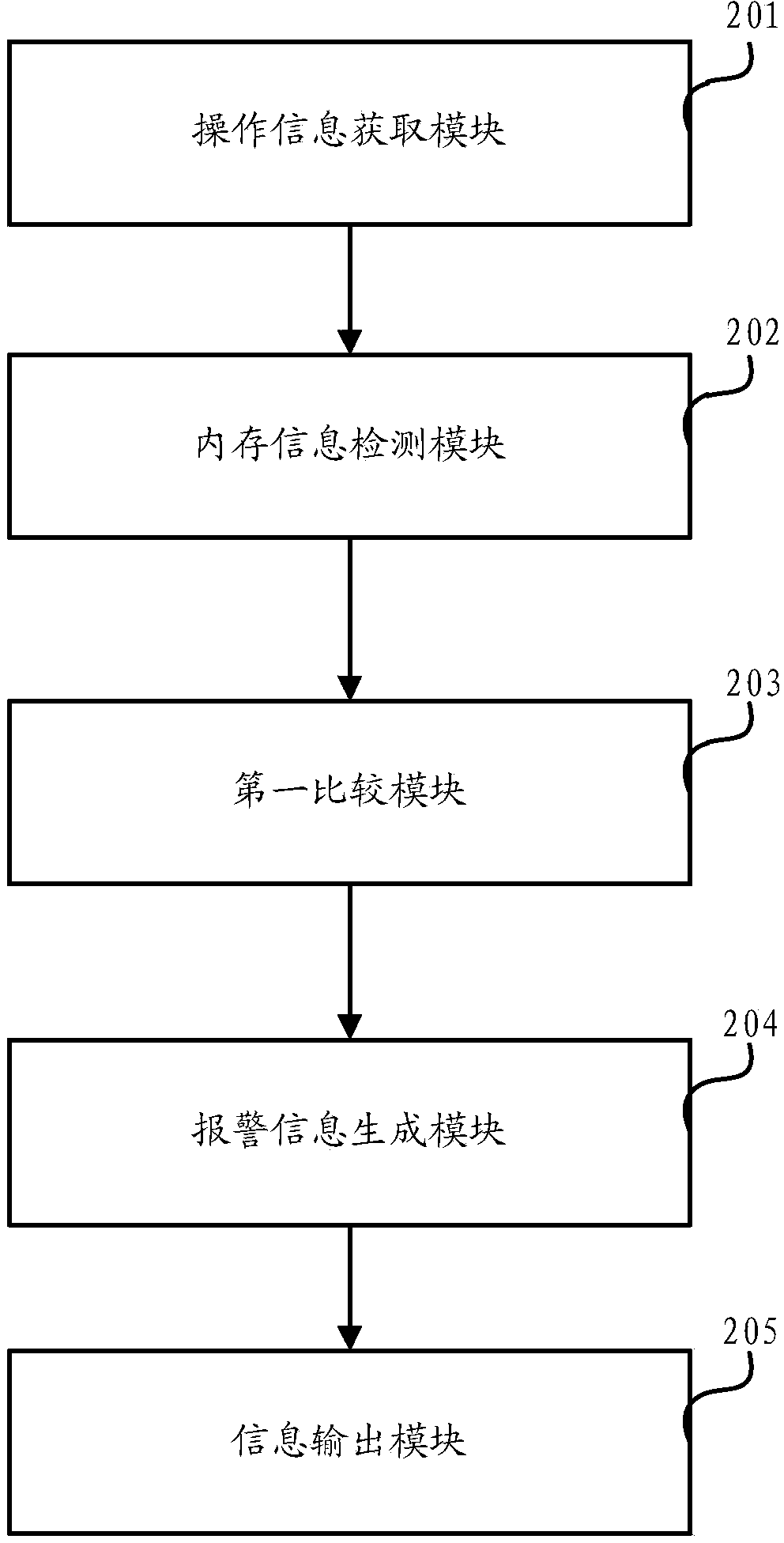
[0038] Aiming at the problem of memory leaks under the GC mechanism in the prior art, the existing solution is: use DDMS (Dalvik Debug Monitor Service, the Dalvik virtual machine debugging monitoring service in the Android development environment) or MAT memory provided by android analyzing tool. However, there are still some shortcomings in this solution, such as: it is necessary to connect to the mobile phone to monitor the memory changes, and the memory leak may occur in some specific scenarios, such as the case of free testing, so it cannot be caught when connecting. In the case of these specific operations, the scenario where a memory leak problem is found is missed. In addition, DDMS involves a more professional operation process, so it needs strong professional technical knowledge to be used flexibly, which leads to inconvenient operation.
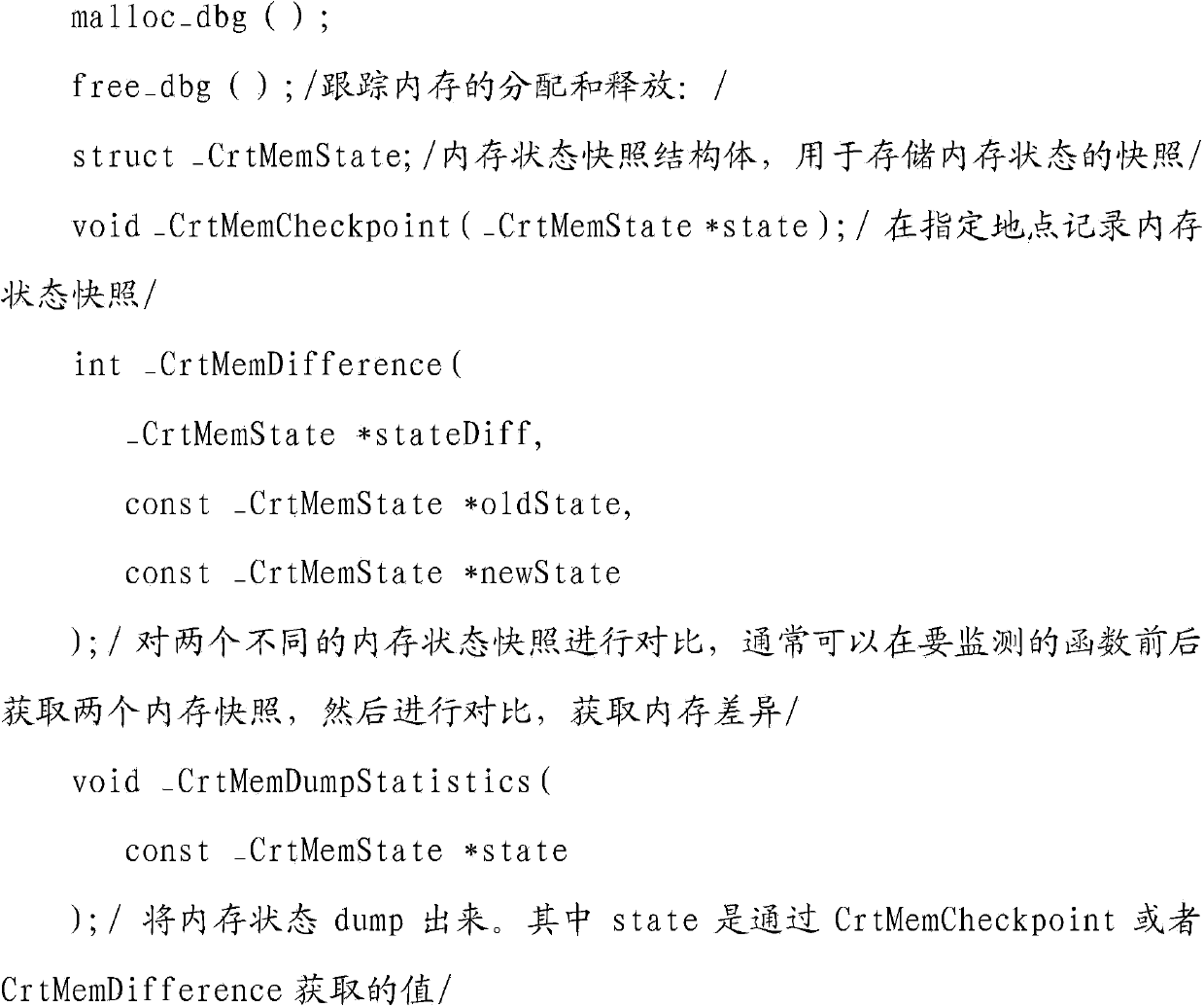
[0039] The key to detecting memory leaks is to be able to intercept calls to functions that allocate and free memory. By interce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com