Method and device for recovering anomaly of application program in embedded system
An embedded system and application technology, which is applied in the direction of response error generation, redundant data error detection in calculation, etc., can solve the problems of poor reliability of application programs, and achieve the effect of avoiding separate installation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
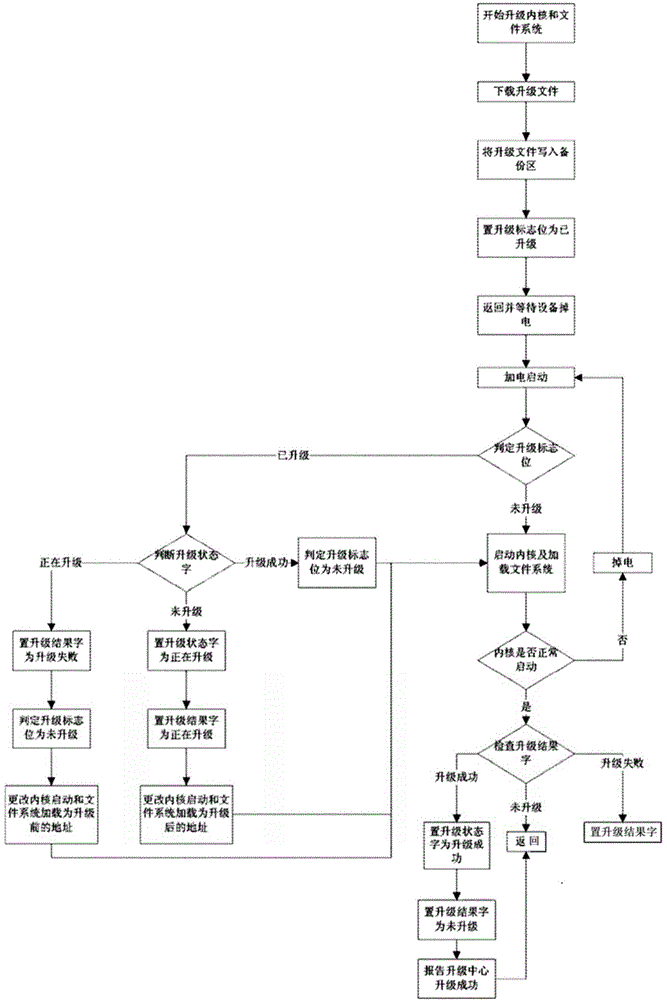
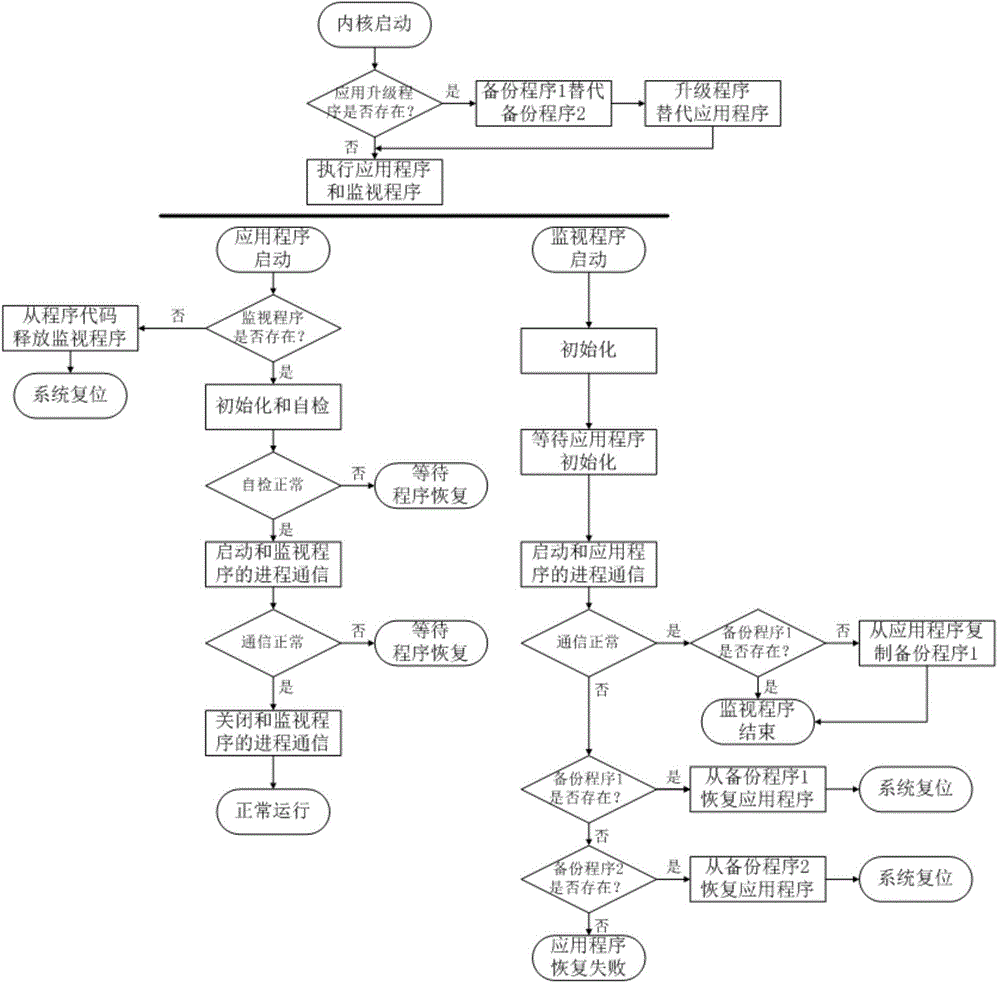
[0026] Such as figure 2 Be the concrete flowchart of embodiment 1, method of the present invention comprises the steps:
[0027] Step 1: After the kernel is started, the embedded system checks whether the application upgrade program exists. If the application upgrade program exists, replace the backup program 2 with the backup program 1, then delete the backup program 1, and replace the current application program with the application upgrade program. Then delete the application upgrade program, and then execute the application program and monitoring program; if the application upgrade program does not exist, directly execute the application program and monitoring program;
[0028] Step 2: After the application program is started, the application program performs initialization and self-test. If the self-test judgment of the application program is abnormal, the application program enters the process of waiting for the program to resume, and the process communication port with...
Embodiment 2
[0041] Embodiment 2 is actually a simplification of Embodiment 1: without upgrading, that is, when the application upgrade program is not involved, after the embedded system kernel starts, if the application program data in the non-volatile memory is damaged, the application The program will fail to run, or run self-test failure, or process communication interaction failure. After the monitoring program finds the failure, the application program can be restored from the backup program 1 or backup program 2, and the system can be resumed after the system is reset. When restoring the application program from backup program 1 or backup program 2, the corresponding backup program will be deleted, so as to avoid damage to the backup program and repeated recovery operations, resulting in repeated restarts and non-volatile memory failure.
[0042] Backup program 1 is automatically copied by the currently running application program if the backup program 1 does not exist after the moni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com