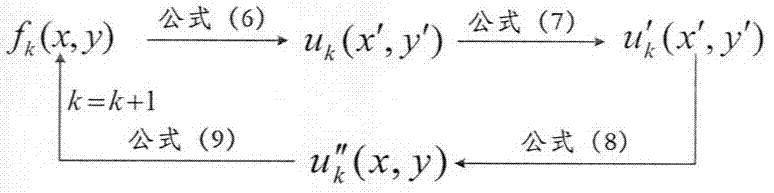A Binary Image Encryption Method Based on Aperture Encryption and Phase Recovery Algorithm
A phase recovery and encryption method technology, applied in the field of information security, can solve the problems of phase recovery calculation convergence stagnation, serious problems, and reduced flexibility of the optical encryption system, so as to improve security, restore high quality, and simplify optical devices Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific implementation of method of the present invention is as follows:
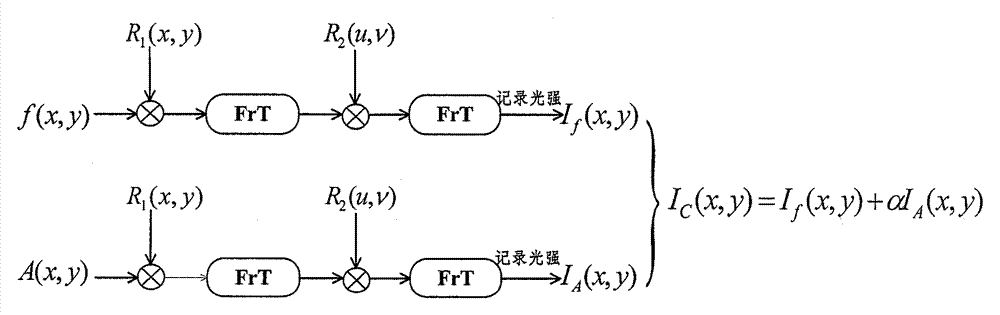
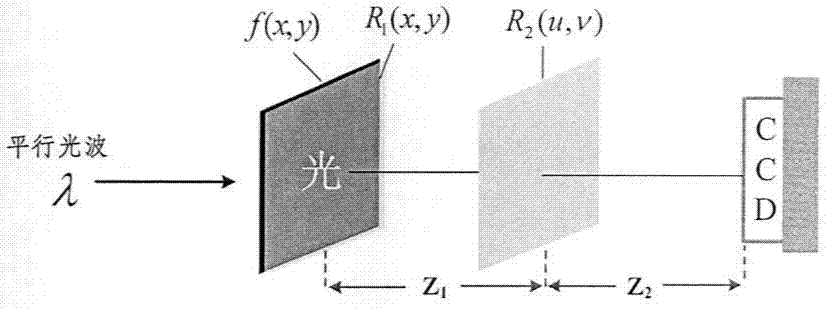
[0048] (1) The encryption process of the image (such as figure 1 shown) in the following steps:
[0049] (i) A(x, y) is an aperture function, f(x, y) represents the original image to be encrypted, R 1 (x, y) and R 2 (u, v) are two phase plates used as encryption keys in the optical encryption process, specifically expressed as exp[2πr 1 (x,y)] and exp[2πr 2 (u, v)], r 1 (x, y) and r 2 (u, v) represent two random matrices with a uniform probability distribution on the interval [0, 1] and are statistically independent, where (x, y) and (u, v) represent the input plane and the Fresnel diffraction output plane, respectively The coordinates of f(x, y) and the encryption key R 1 The product of (x, y) is once the wavelength is λ, and the distance is z 1 The Fresnel transform, the result obtained with R 2 (u, v) multiplied and then do it again The wavelength is λ, and the distance is z 2 T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com