Dynamic password authentication method and system based on two-dimensional code
A technology of dynamic password and authentication method, applied in the direction of digital data authentication, user identity/authority verification, etc., can solve the problems of input error, inconvenience and time-consuming, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
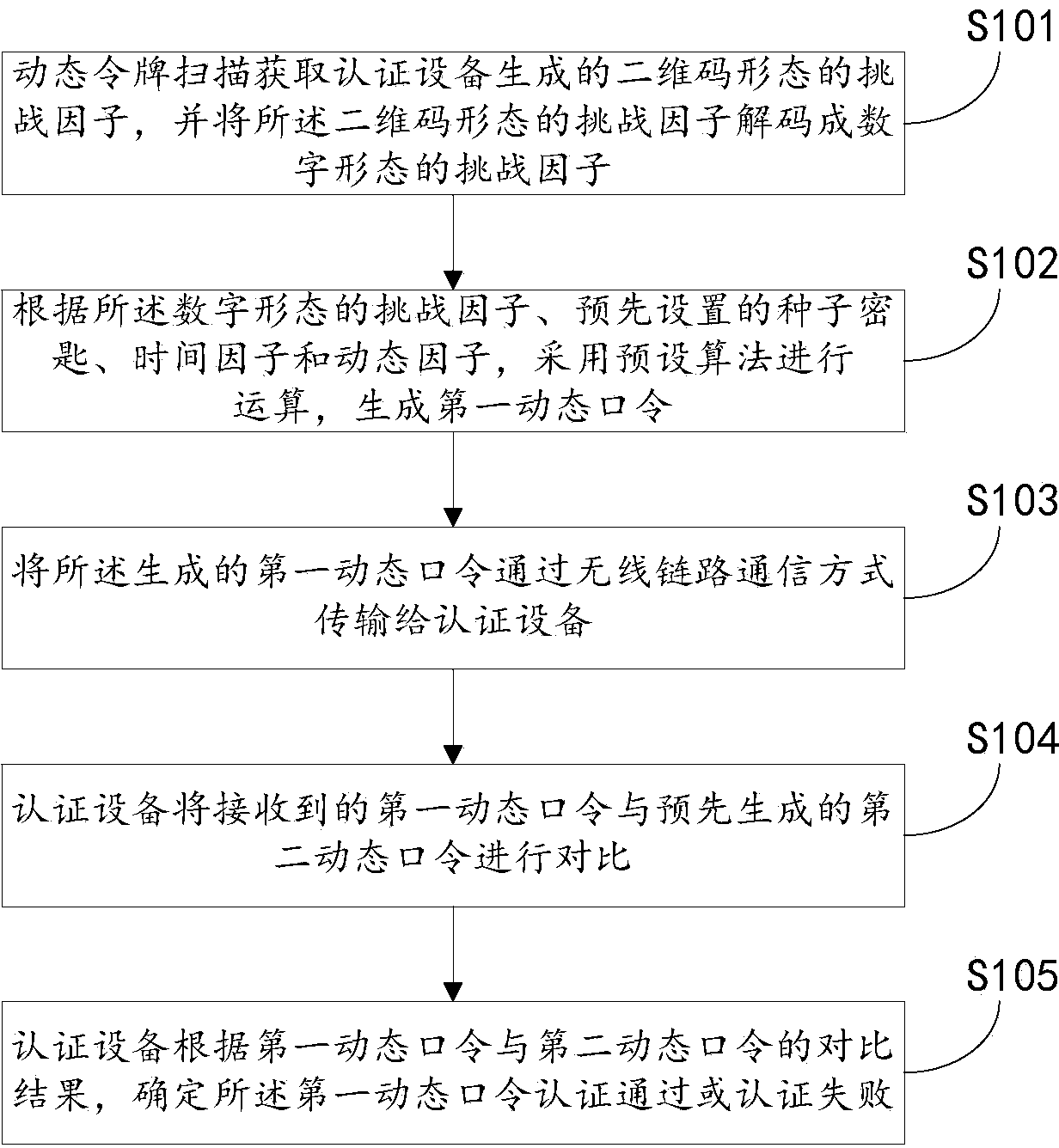
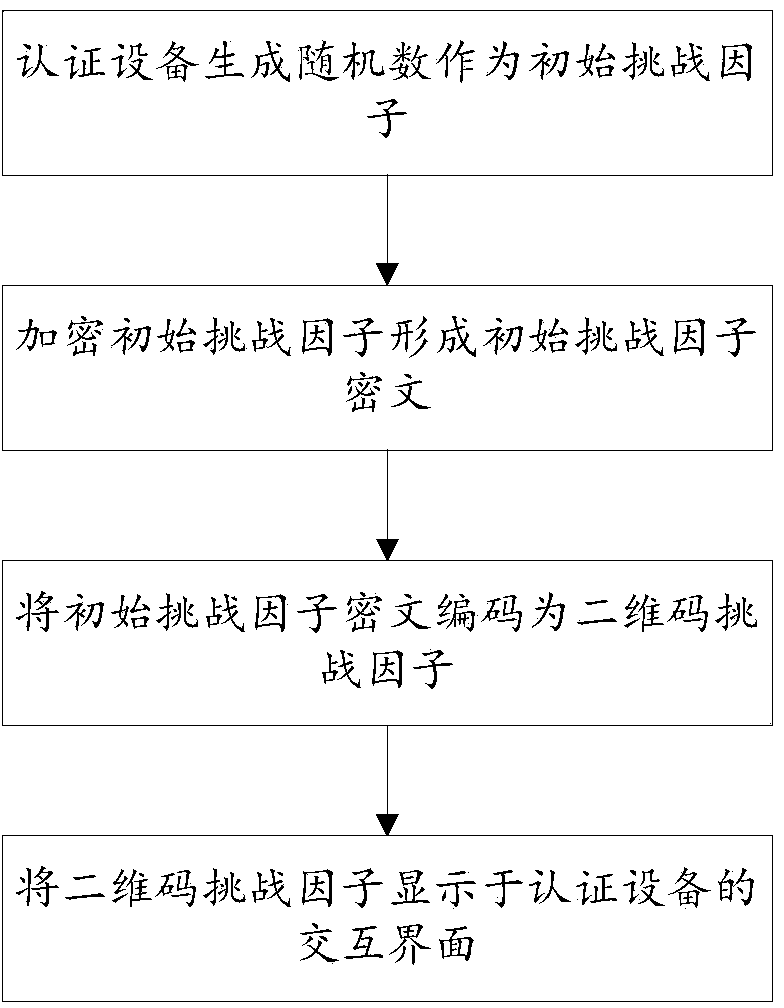
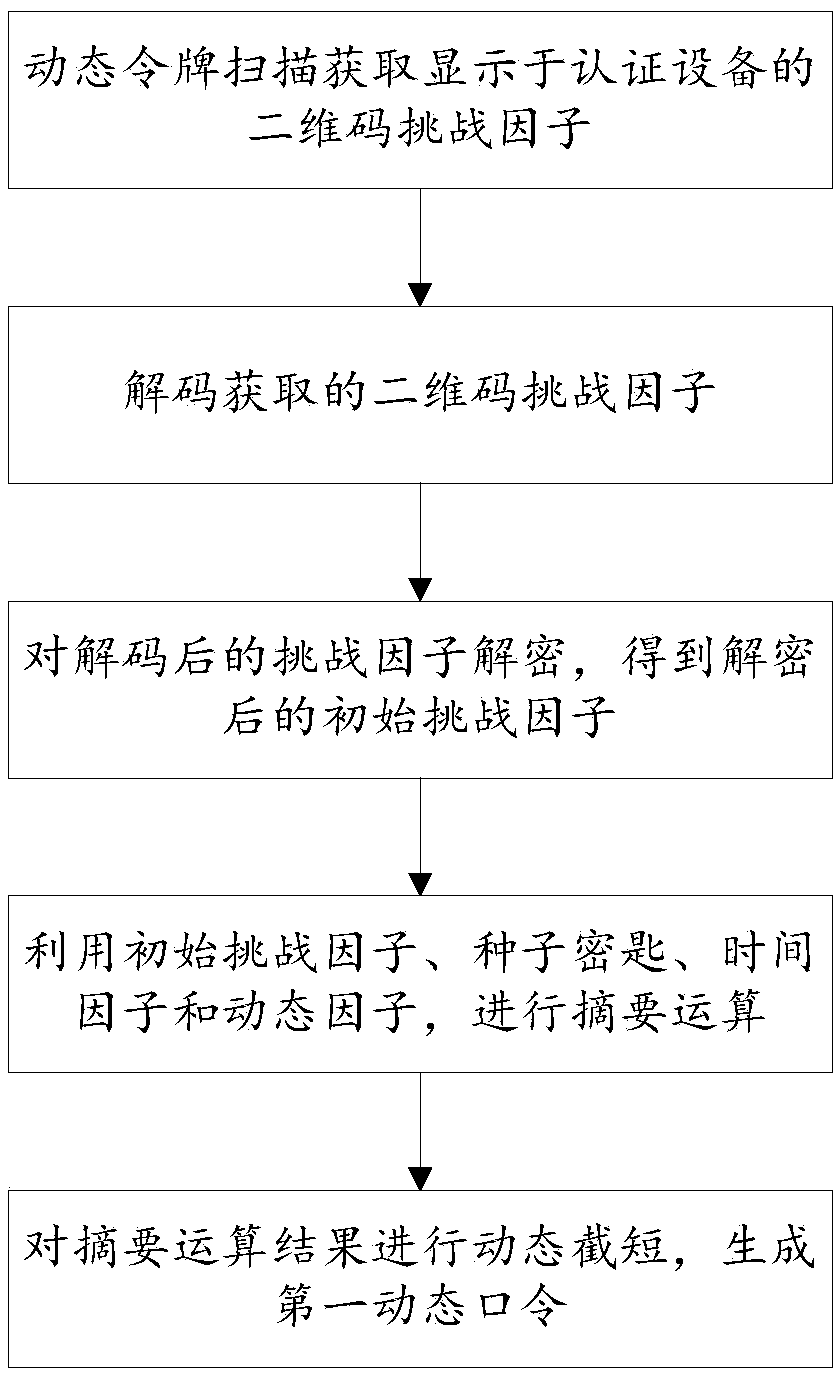
[0028] Embodiment 1. A dynamic password authentication method based on a two-dimensional code. Combine below Figure 1-Figure 4 The method provided in this embodiment will be described in detail.
[0029] see figure 1 , S101. Scanning the dynamic token to obtain a challenge factor in the form of a two-dimensional code generated by the authentication device, and decoding the challenge factor in the form of a two-dimensional code into a challenge factor in a digital form.
[0030] Specifically, see figure 2 , the authentication device randomly generates an initial challenge factor in digital form with a predetermined length, wherein the length of the initial challenge factor can be set by the user, which is not strictly limited in this embodiment; the generated initial challenge factor is encrypted using a predetermined encryption algorithm, such as , use the symmetric encryption algorithm to encrypt the initial challenge factor to form the challenge factor in the encrypted ...
Embodiment 2
[0045] Embodiment 2. A dynamic password authentication system based on a two-dimensional code. Combine below Figure 5 The system provided in this embodiment will be described in detail.
[0046] see Figure 5 , the system provided by this embodiment includes a dynamic token 500 and an authentication device 600, wherein the dynamic token 500 includes a challenge factor acquisition module 5001, a first dynamic password generation module 5002, a second encryption module 5003 and a transmission module 5004, and the authentication device 600 includes an initial challenge factor generation module 6001 , a first encryption module 6002 , a two-dimensional code encoding module 6003 , a display module 6004 , a decryption module 6005 , a second dynamic password generation module 6006 , a comparison module 6007 and an authentication determination module 6008 .
[0047] The initial challenge factor generating module 6001 in the authentication device 600 is mainly used to randomly genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com