Visible encryption and decryption method with image disguising function and tampering identification function
A technology of disguising images and tampering with authentication, applied in the field of information hiding, can solve the problem of being unable to distinguish between false secret images and real secret images, and achieve the effect of protecting copyright and copyright attribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
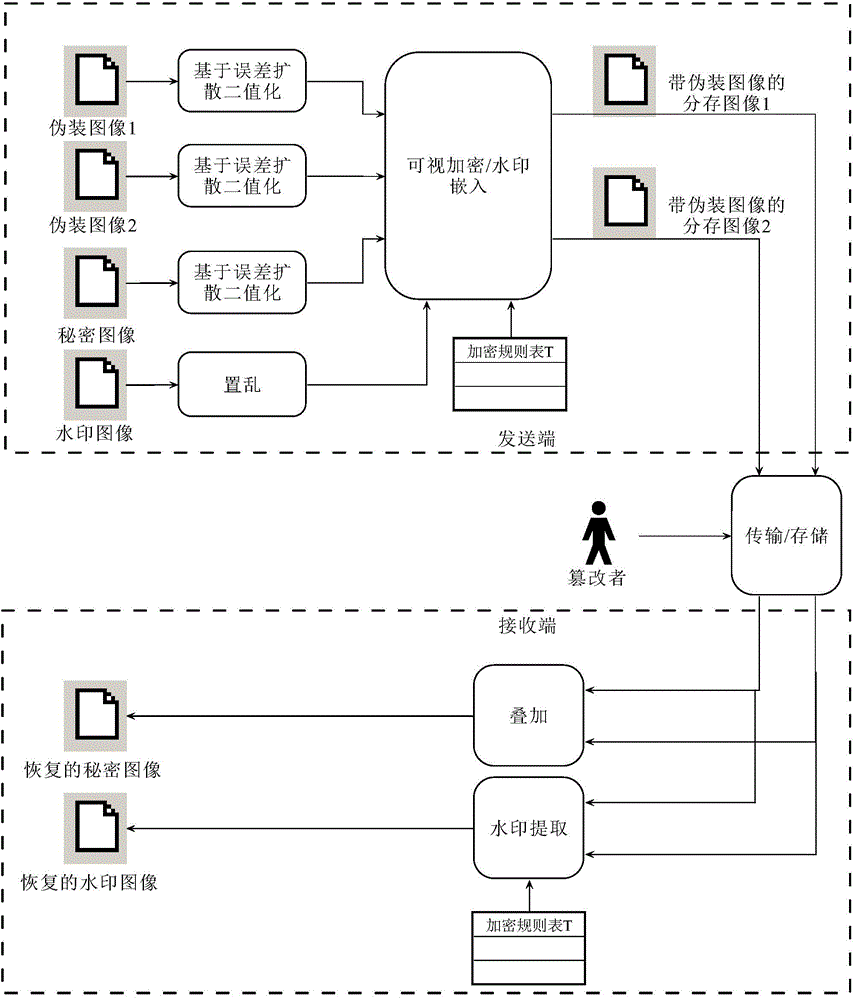
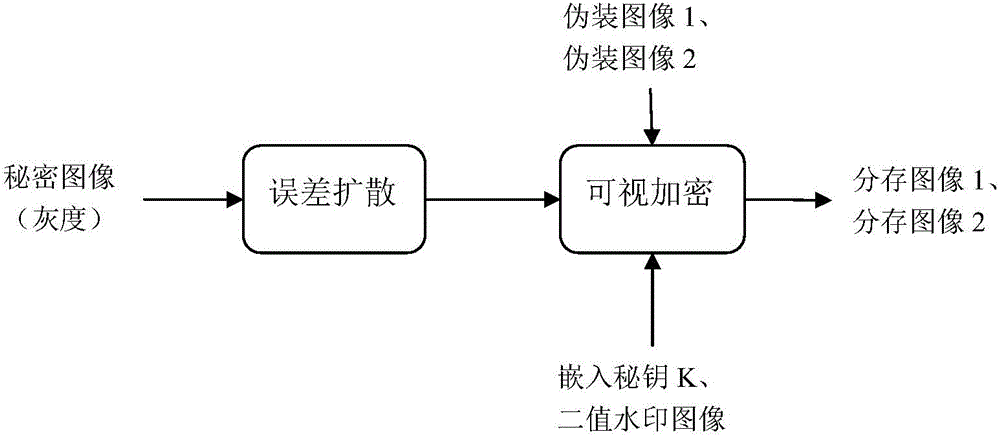
[0039] Such as figure 1 and figure 2 As shown, a visual encryption method with camouflage image and tampering authentication function includes the following steps:
[0040] a1 Input a secret image, two camouflage images and a watermark image, use the error diffusion method to binarize each image, and generate a binarized image for each input image;
[0041] a2 uses the key Kw to scramble the watermark image with random numbers to generate a scrambled watermark image of the same size;
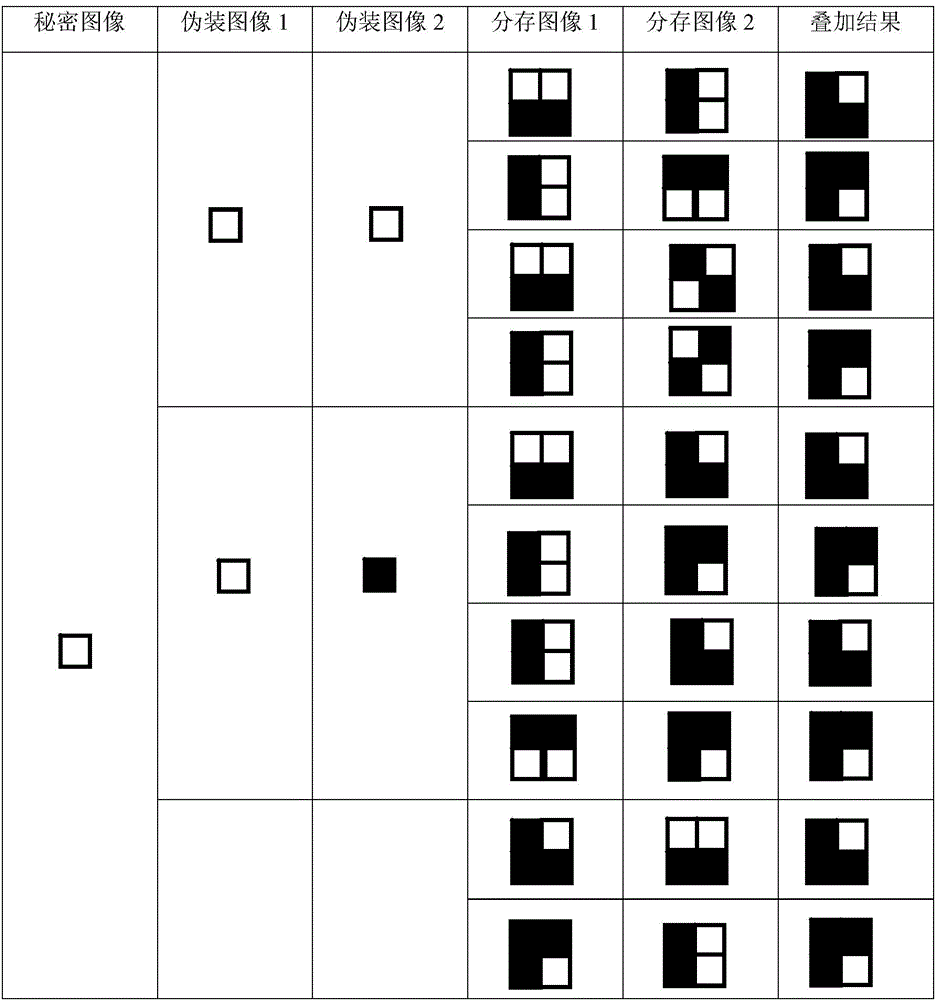
[0042] a3 According to the following requirements, construct the visible encryption rules and watermark embedding rules, called the encryption rule table T, such as image 3 Shown:
[0043] 1) If the bit of the secret image is 0, it is necessary to ensure that there is at least one 0 after the 2x2 pixel blocks corresponding to the two shared images are superi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com