A computer system and method for managing computer user rights
A technology for managing computers and computer systems, applied in the field of computer systems and managing computer user rights, can solve the problems of not distinguishing user rights, single functions, and no association between equipment and user rights, so as to protect important data and personal privacy, and save costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
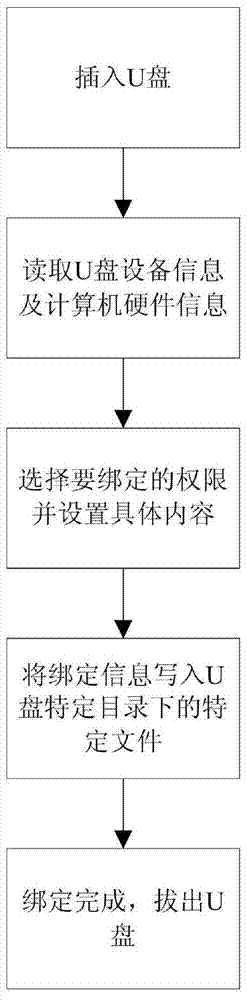
[0056]Embodiment 1 provides a computer user rights management method for identifying user rights based on different USB disks.
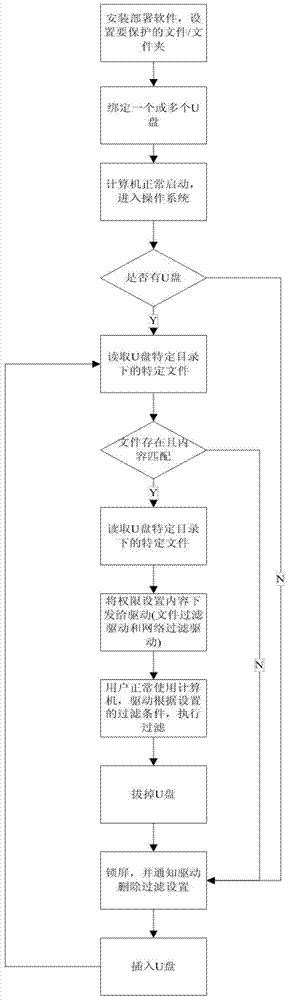
[0057] combine Figure 1-2 The U disk binding computer and operation flow chart describe the realization process of the overall technical solution:
[0058] 1) Install the software system
[0059] Install software packages, including setup programs, network filter drivers, file system filter drivers, and service programs. The setting program is used to set the U disk binding and permission association; the network filter driver is used to filter network access; the file system filter driver is used to protect files and folders; the service program is used to detect the U disk and communicate with the driver.
[0060] After installation, use the setup program to pass all files / folders to be protected to the file system filter driver.
[0061] 2) Bind U disk
[0062] (1) Open the setup program, insert the U disk, read the device information of the ...
Embodiment 2
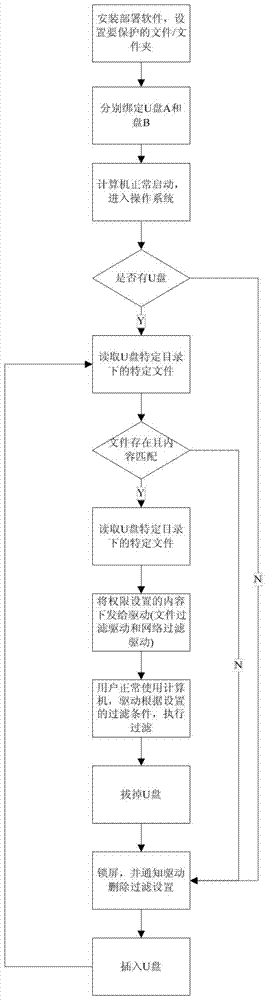
[0119] combined with Figure 4-5 The USB peripheral binding computer flowchart in the description describes the implementation process of the overall technical solution of embodiment 2:
[0120] 1) Install the software system
[0121]Install software packages, including setup programs, network filter drivers, file system filter drivers, and service programs. The setup program is used to set the removable device binding and permission association; the network filter driver is used to filter network access; the file system filter driver is used to protect files and folders; the service program is used to detect the removable device and communicate with the driver.
[0122] After installation, use the setup program to pass all files / folders to be protected to the file system filter driver.
[0123] 2) Bind the removable device
[0124] (1) Open the setting program, insert the USB removable device, and read the information of the USB device and the hardware information of the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com