Method and system for encrypting/ decrypting IP (Internet Protocol) short messages based on SMS (Short Messaging Service) over IMS (IP Multimedia Subsystem)
An encryption and decryption algorithm, short message technology, applied in electrical components, wireless communications, security devices, etc., can solve the problems of terminal theft, increase costs, etc., and achieve the effect of low operation and maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
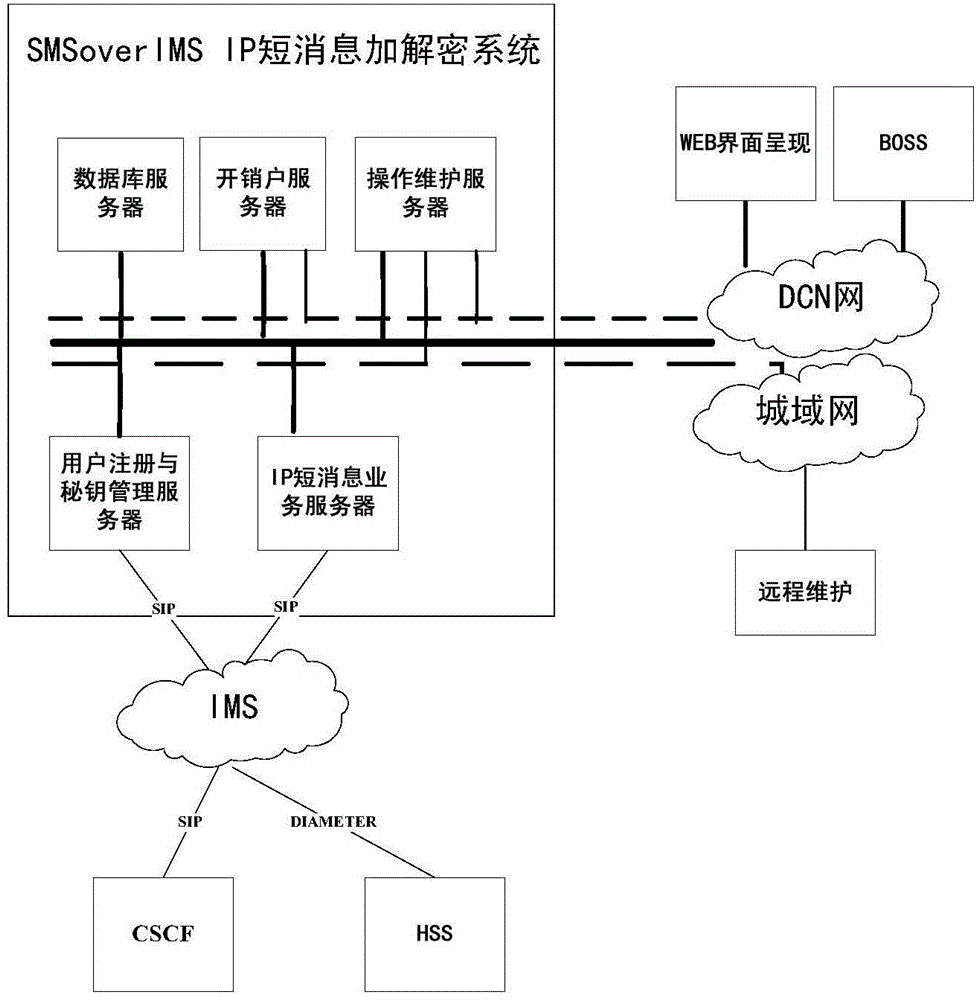
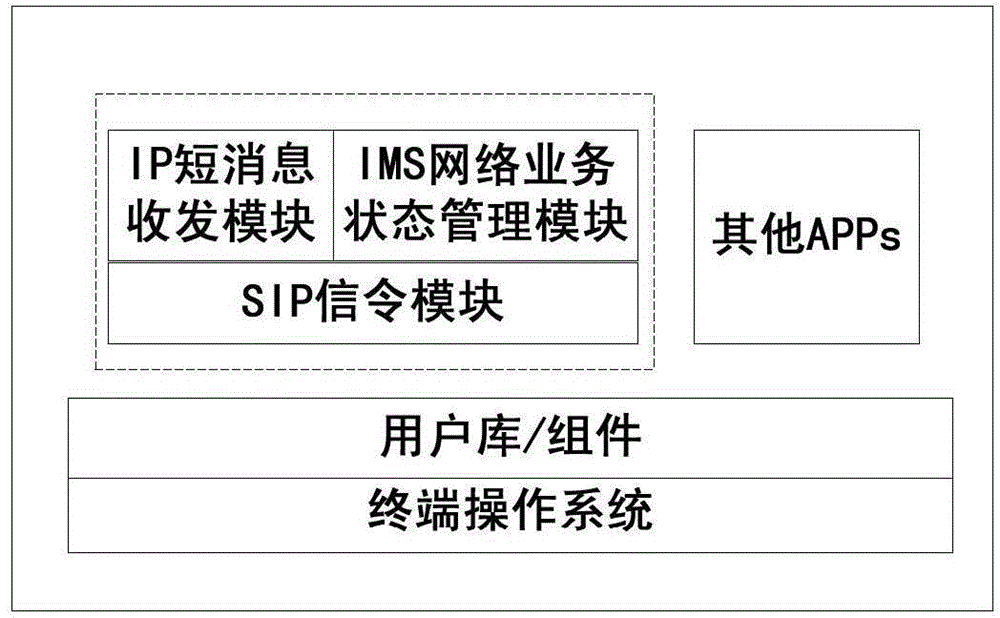
[0071] For the convenience of description, the "SMSoverIMS IP short message encryption and decryption system" hereinafter will be collectively referred to as "this system".
[0072] Such as figure 1 As shown, this system has user registration and secret key management server, IP short message service server, database server, operation management server and account opening server, etc. The relationship between each system component is as follows:
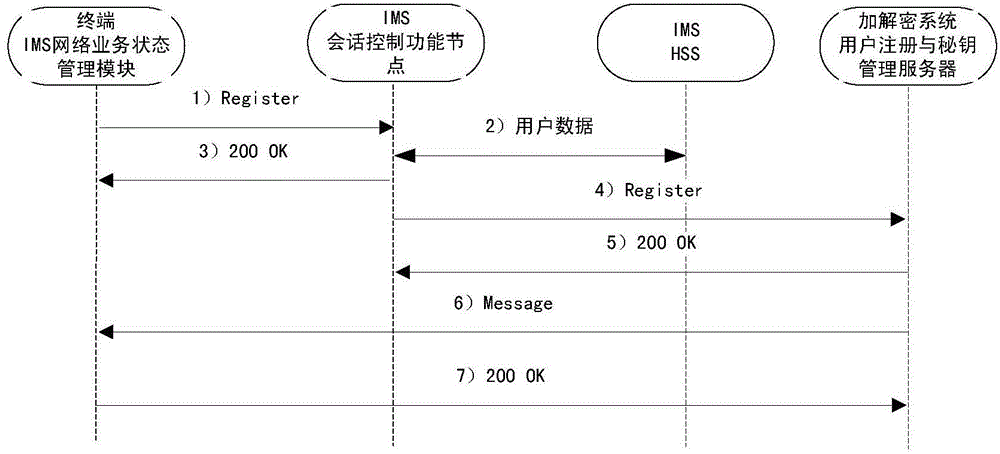
[0073] 1) The SIP signaling module, user registration management module, and secret key management module are set in the user registration and secret key management server; the user registration signaling sent by the IMS network is received by the SIP signaling module and analyzed and parameter extracted Afterwards, it is submitted to the user registration management module, and the user registration management returns a response instruction of successful registration to the IMS network through the SIP signaling module after successf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com