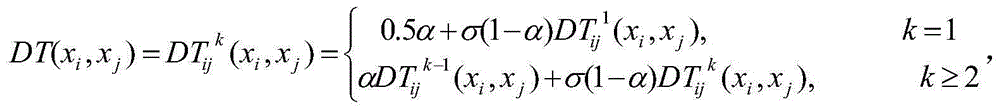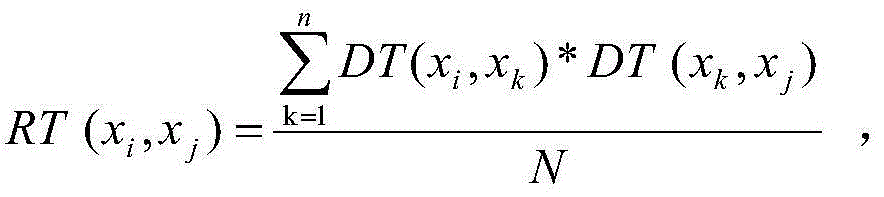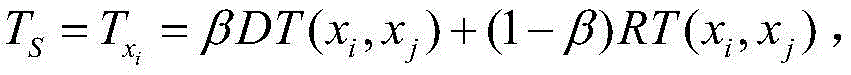Access control strategy composition method based on attribute
A technology of access control strategy and synthesis method, which is applied in the field of access control strategy synthesis, can solve the problems of not involving the subtraction operator and the security threat of the voting operator, and achieve the effect of preventing illegal operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] An attribute-based access control policy synthesis method, the specific synthesis steps are as follows:
[0022] 1. Decompose the attribute-based access control policy towards the attribute layer; first decompose each attribute in the policy, and use ap i *val represents an attribute constraint, where ap i Indicates the i-th attribute, *∈{≤,≥,=,}, val is the value of the attribute, which is a number or text. Attribute constraints include subject attribute constraints, object attribute constraints, environment attribute constraints, subject trust degree constraints, and operation attribute constraints.
[0023] 2. Transform the result of step 1 into an attribute-based access control policy algebraic expression; use SAP i Indicates the i-th attribute of the subject, using OAP j Indicates the jth attribute of the object, using EAP k Represents the kth attribute of the environment, with Ts m Indicates the trust degree attribute of the mth subject, and OP is used to acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com