Method for resisting Sybil attack with multiple fake identity sources in car networking
A vehicle networking and identity technology, applied in the vehicle network field, can solve the problems of relying on the loyalty of neighbor vehicles and not meeting the needs of practical applications, and achieve the effect of eliminating Sybil attacks and preventing repudiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
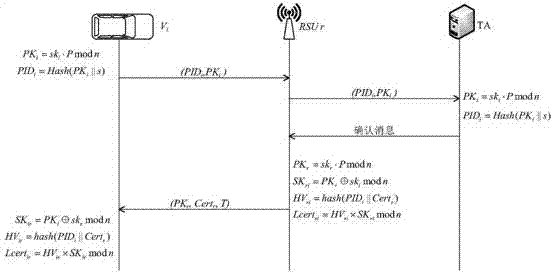
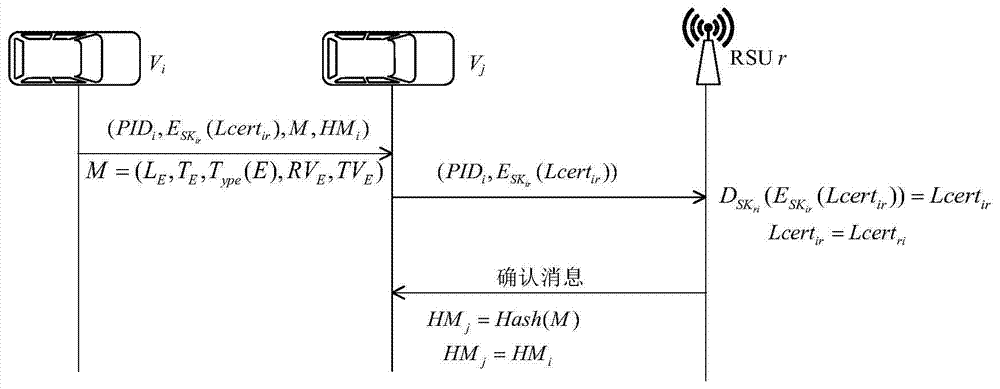
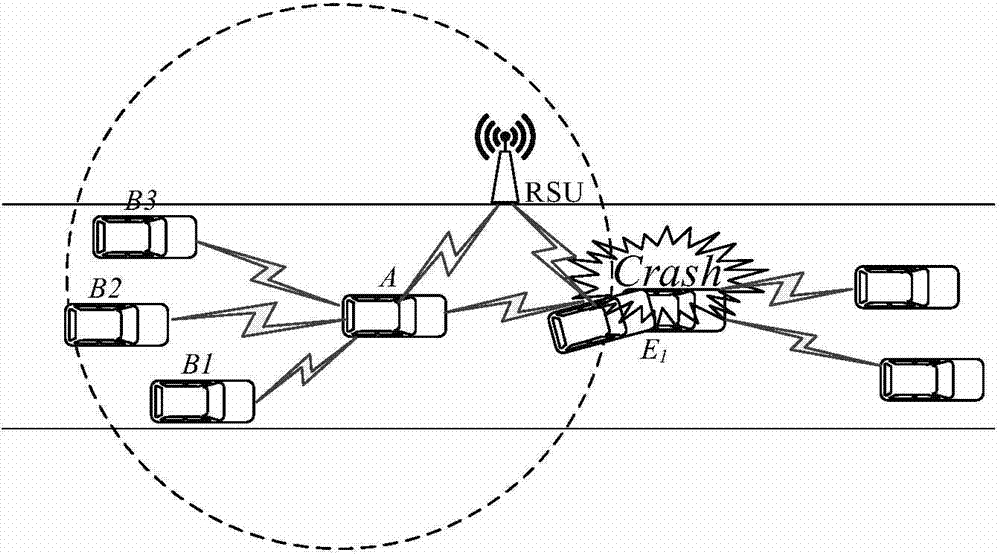
[0042] Such as Figures 1 to 3 As shown, the collision event E1 occurs in the traffic scene of this embodiment, assuming that the event E 1 The reputation value threshold is 8, and the credibility value threshold is 2. The nearby vehicle (assumed to be vehicle A) immediately sends an alarm message to other vehicles, and the vehicle behind the event (assumed to be vehicle B 1 , B 2 ,...,B n ) received an alert message.
[0043] (1) Vehicle A generates a local certificate to prepare for subsequent communication. The specific implementation steps are as follows:
[0044] 1) Vehicle A PK according to the ECC algorithm A =sk A · P mod n and PID A =Hash(PK A ||s) respectively calculate their own public key PK A and the pseudonym PID A , sending them to the local RSU r.
[0045] 2) After receiving the message sent by A, the local RSU r sends a message to TA to verify the public key and pseudonym of vehicle A. If it fails the TA verification, it means that vehicle A tries ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com