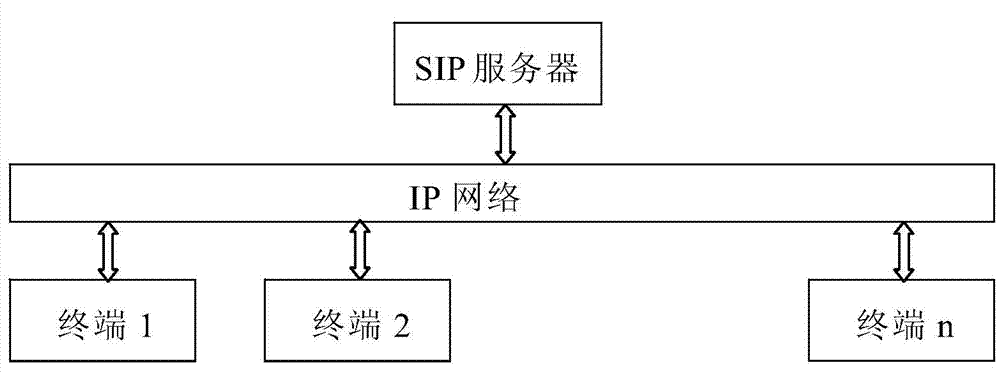
SIP protocol based session encryption method
A technology of SIP protocol and encryption method, which is applied in the field of information security, can solve problems such as complex implementation process, eavesdropping on call content, and poor flexibility, and achieve the effects of reducing complexity, saving configuration work, and simplifying the encryption process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
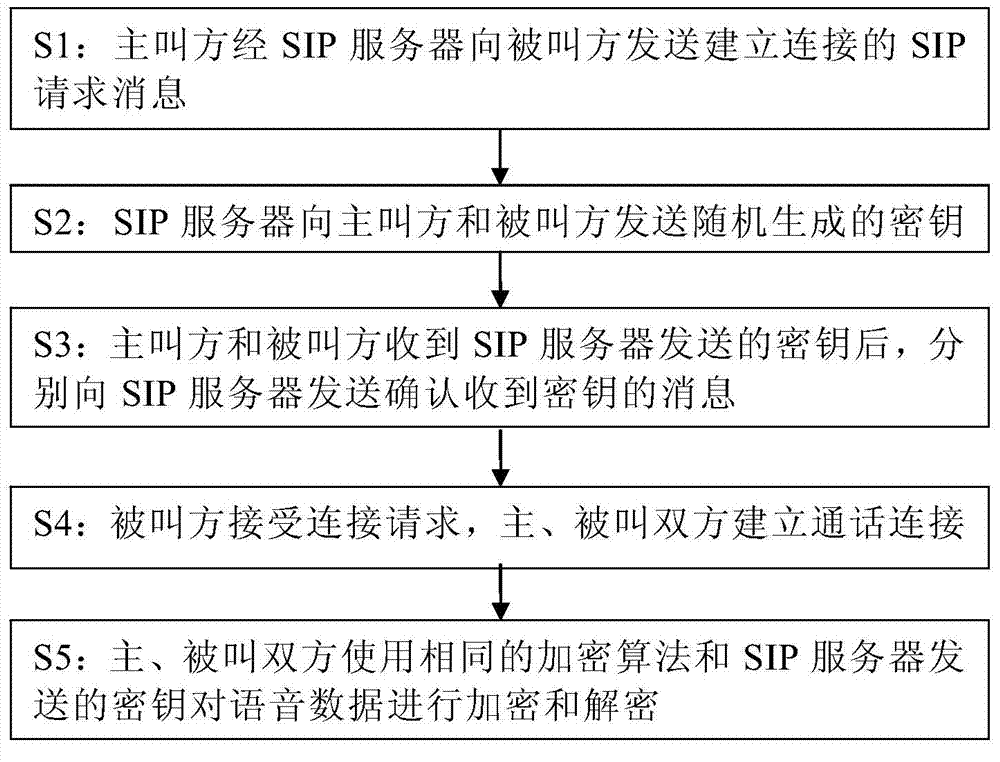
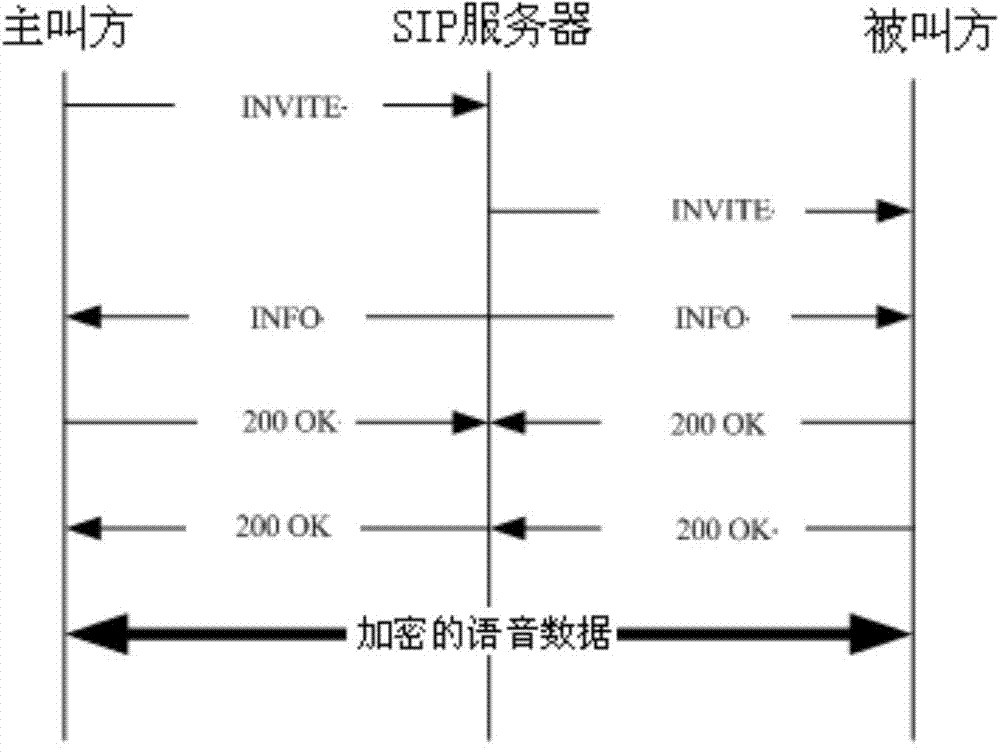
[0024] figure 2 is a flow chart of the method of the present invention, image 3 It is a message flow schematic diagram of a specific embodiment of the present invention, as shown in the figure, the method for encrypting calls based on the SIP protocol disclosed by the present invention, the steps are:
[0025] S1: The calling party initiates a SIP request message (INVITE message) to establish a connection to the SIP server. After receiving the request message, the SIP server finds the called party through a route search and sends a SIP request message (INVITE message) to the called party to establish a connection. information);
[0026] S2: The SIP server sends randomly generated keys to the calling party and the called party;
[0027] The SIP server generates a 16-bit random number through a random function as the key for this call conne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com