Private key protection method based on asymmetric secret key system
An asymmetric key and private key technology, applied in key distribution, can solve the problem of pure soft solutions without comparable technologies, and achieve the effect of avoiding theft of signatures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The technical solution of the present invention is specifically described below in conjunction with the accompanying drawings. It should be pointed out that the technical solution of the present invention is not limited to the implementation described in the examples. Those skilled in the art refer to and learn from the content of the technical solution of the present invention. Improvements and designs made on the basis of the invention shall belong to the protection scope of the present invention.
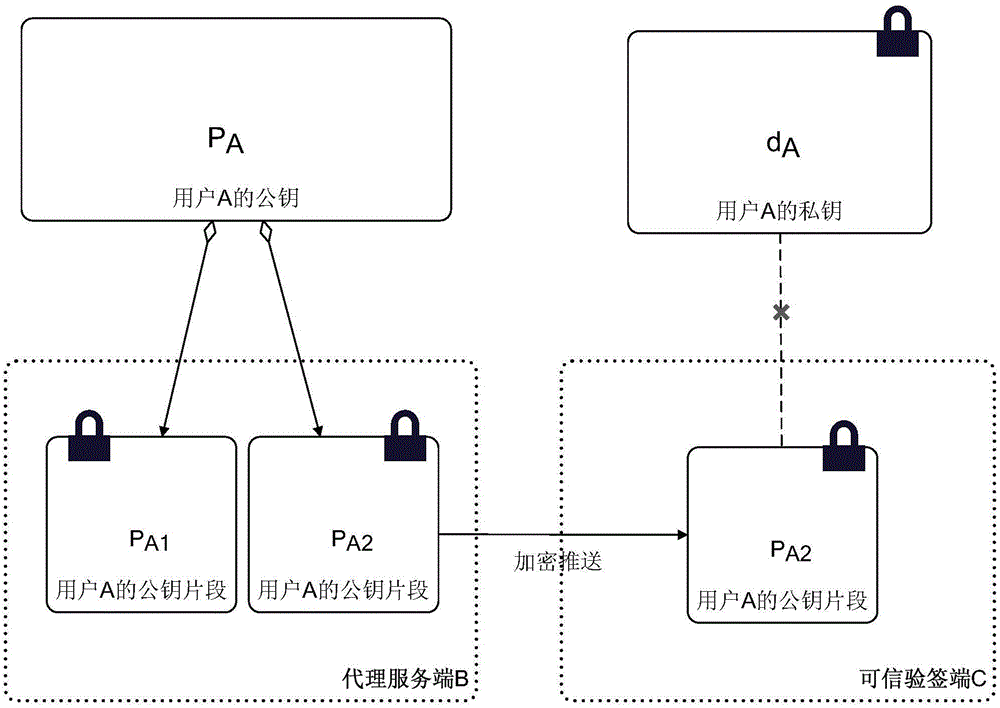
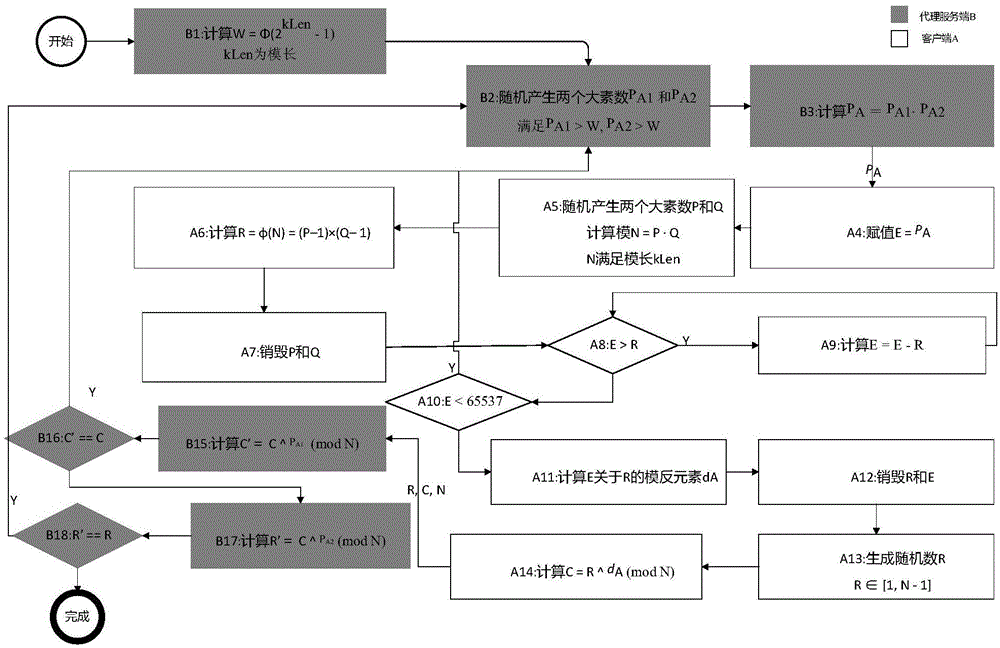
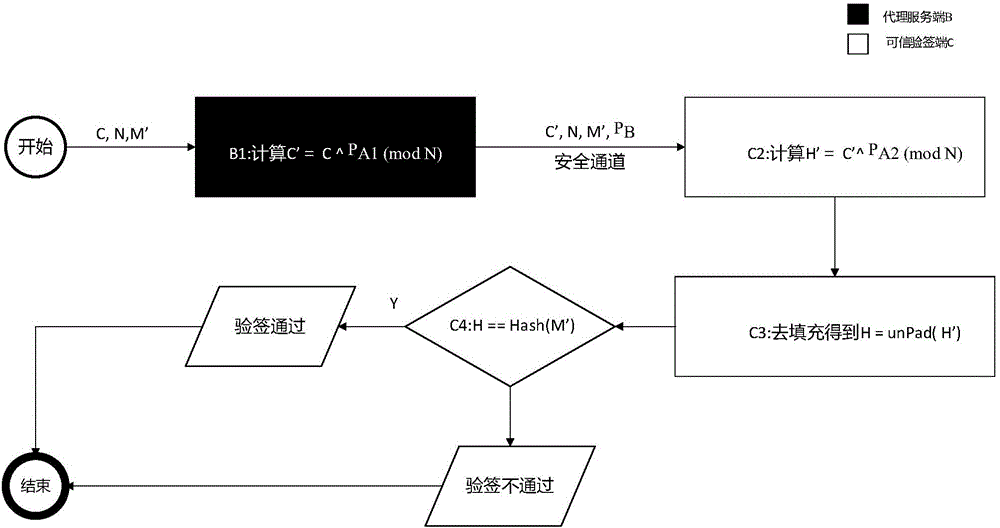
[0041] Such as figure 1 As shown, the private key protection method based on the asymmetric key system of the present invention:
[0042] Theoretical derivation, where M is the plaintext, N is the public modulus, and P A is the public key of user A, d A is the private key of user A, P A1 and P A2 is the public key fragment of user A, and C is the private key d A The generated ciphertext, C' refers to the second encryption of the ciphertext C by the proxy server side B...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com