A security authentication method based on sram PUF and a terminal and authentication system
A security authentication and terminal technology, applied in the field of network security, can solve problems such as reduced efficiency and increased cost, and achieve the effects of improving security, reducing implementation costs, and simplifying the structure of software and hardware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
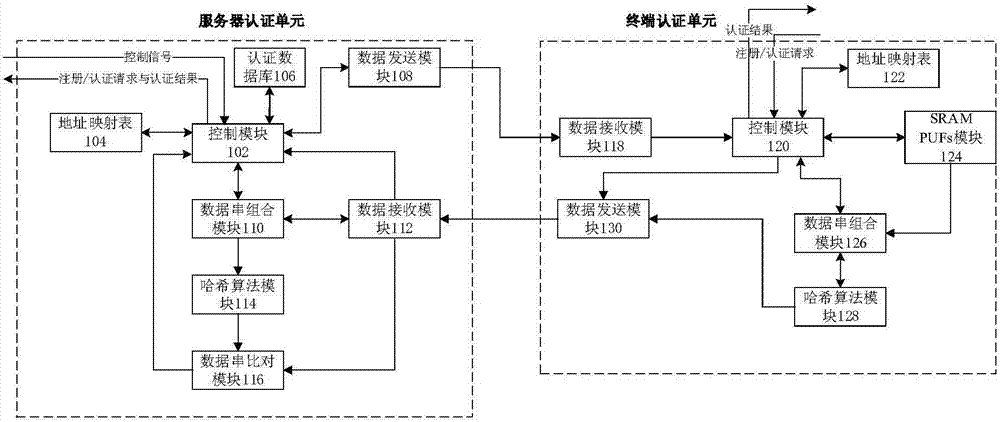
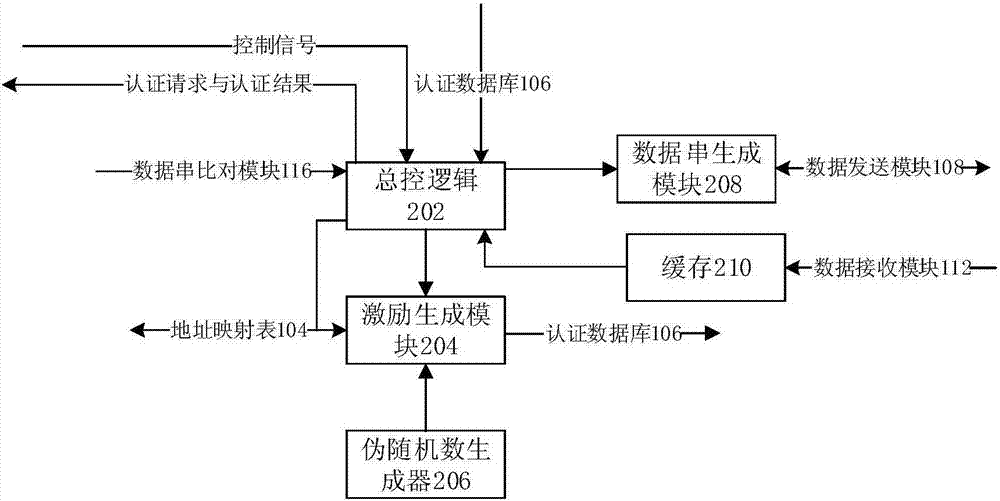
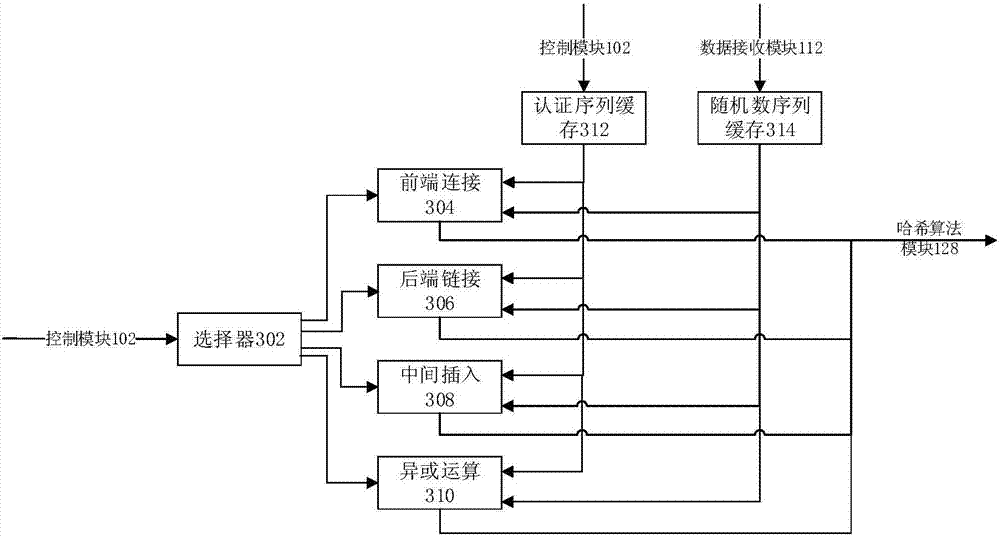
[0046] Aiming at the security problem of the existing SRAM PUF-based authentication system, the present invention proposes a security authentication method, which divides the nodes of the SRAM PUF module into random nodes and authentication nodes, and uses the authentication nodes and random nodes respectively when performing authentication. Generate an authentication sequence and a random number sequence, and then use the generated random number sequence to perform a salted hash operation on the authentication sequence, thereby effectively improving the security of the authentication process and reducing the complexity of the terminal device.
[0047] The security authentication method of the present invention includes a registration stage and an authentication stage,
[0048] The registration phase includes the following steps:
[0049] Step 1. The terminal with the SRAM PUF module divides each node in its own SRAM PUF module into random nodes and authentication nodes in adv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com