Method, device and system for realizing identifying code
An implementation method and verification code technology, applied in the field of verification code implementation, can solve the problems of adding verification codes, high difficulty in verification code identification, and inability to meet the needs of the Internet, so as to achieve the effect of ensuring security and high anti-cracking ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
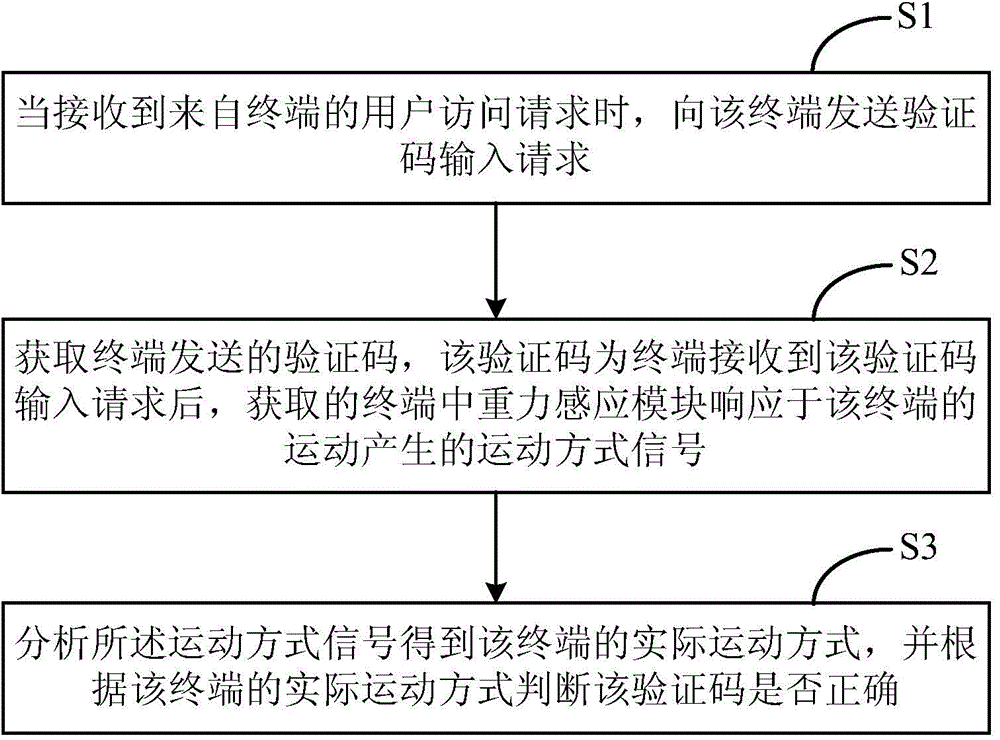
[0032] refer to image 3 As shown, the first embodiment of the present invention provides a verification code implementation method, the verification code implementation method includes the following steps:
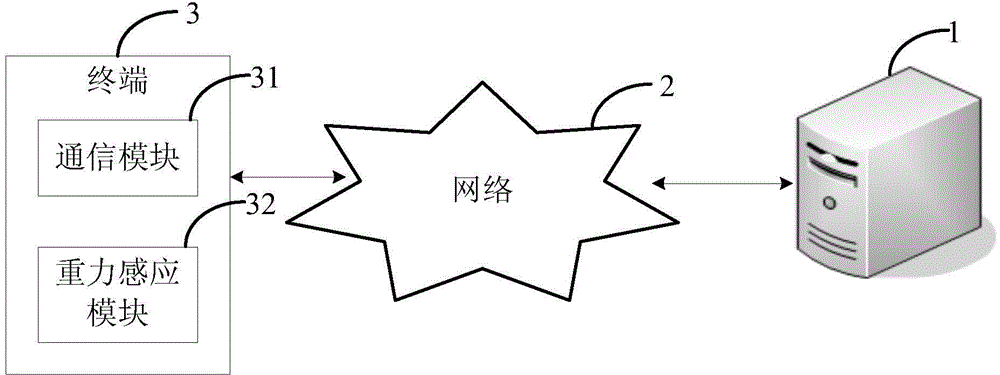
[0033] Step S1, when receiving a user access request from the terminal 3, sending a verification code input request to the terminal 3;
[0034] Step S2, obtaining the verification code sent by the terminal 3, the verification code being the movement mode signal generated by the gravity sensing module 32 in the terminal 3 in response to the movement of the terminal 3 after the terminal 3 receives the verification code input request;
[0035] Step S3, analyzing the motion mode signal to obtain the actual motion mode of the terminal 3, and judging whether the verification code is correct according to the actual motion mode of the terminal 3.
[0036] According to the above-mentioned implementation method of the verification code, after receiving the verification code input ...
no. 2 example
[0052] refer to Figure 6 As shown, the second embodiment of the present invention provides a verification code implementation method, which is executed interactively by the server 1 and the terminal 3 . The implementation method of the verification code includes the following steps:
[0053] Step S11 , when receiving a user access request from the terminal 3 , the server 1 sends a verification code input request to the terminal 3 . The verification code input request includes a verification code prompt interface, and the verification code prompt interface prompts the preset motion mode of the terminal 3 . The preset motion mode includes a preset motion track or a preset rotation mode. The preset rotation mode includes a rotation direction and a rotation angle.
[0054] Step S12, after receiving the verification code input request, the terminal 3 obtains the movement mode signal generated by the gravity sensing module 32 in the terminal 3 in response to the movement of the ...
no. 3 example
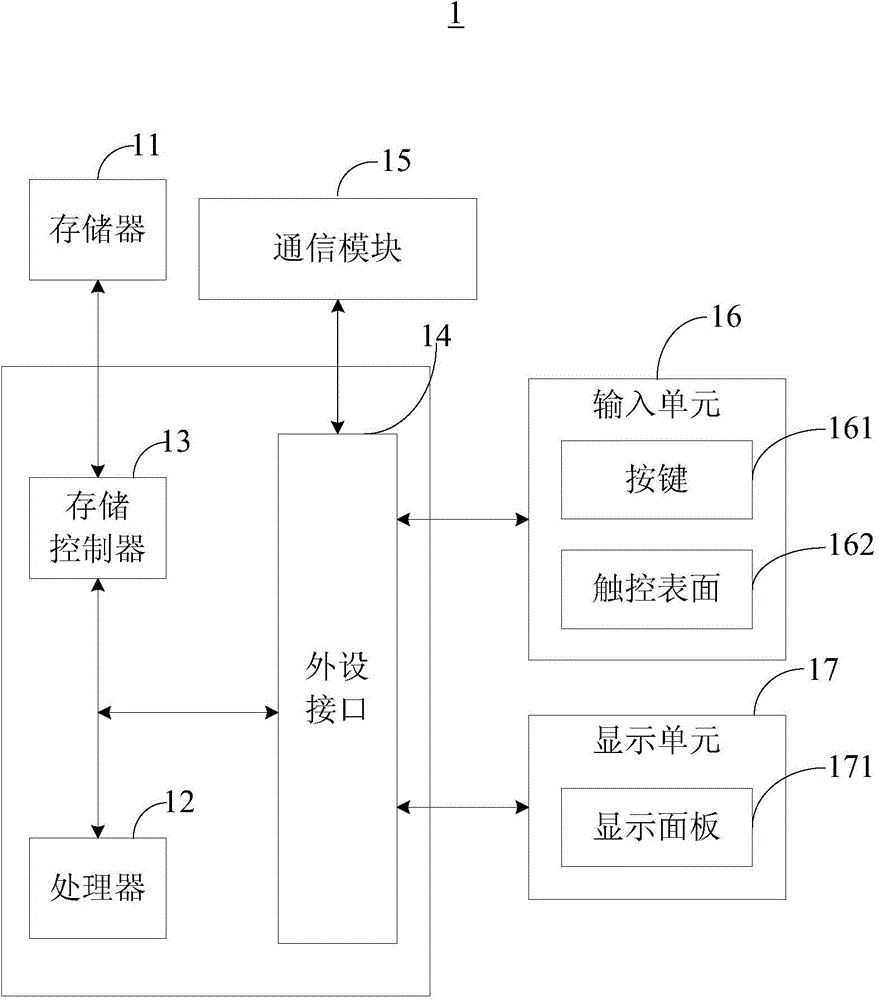
[0058] refer to Figure 7 As shown, the third embodiment of the present invention provides a device 100 for implementing a verification code. The device 100 for implementing a verification code runs in the server 1 and includes a sending module 101 , an obtaining module 102 and a judging module 103 . It can be understood that the above-mentioned modules refer to computer programs or program segments for performing one or more specific functions. In addition, the distinction between the above modules does not mean that the actual program code must also be separated.
[0059] The sending module 101 is configured to send a verification code input request to the terminal 3 when receiving a user access request from the terminal 3 . The verification code input request includes a verification code prompt interface, and the verification code prompt interface prompts the preset motion mode of the terminal 3 . The preset motion mode includes a preset motion track or a preset rotation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com