Verification code generation method, login verification method and login verification system
A technology for login verification and verification code, which is applied in the fields of login verification method, login verification system and verification code generation method, and can solve problems such as poor verification code security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
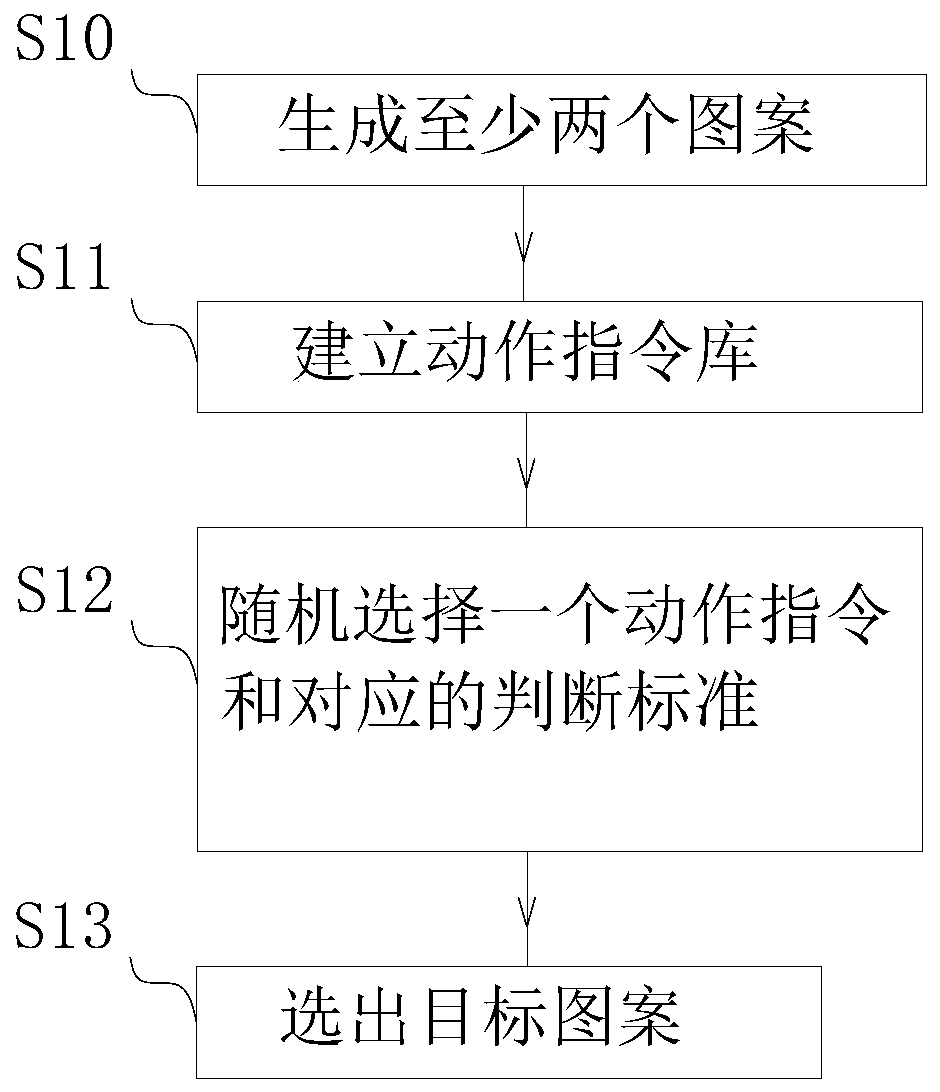
[0053] Such as figure 2 As shown, the verification code generation method of this embodiment includes the following steps:
[0054] S40: generating four spherical patterns;
[0055] S41: Control the four spherical patterns to move in translation at different speeds;
[0056] S42: selecting the fastest moving speed among the four spherical patterns as the target pattern.
Embodiment 2
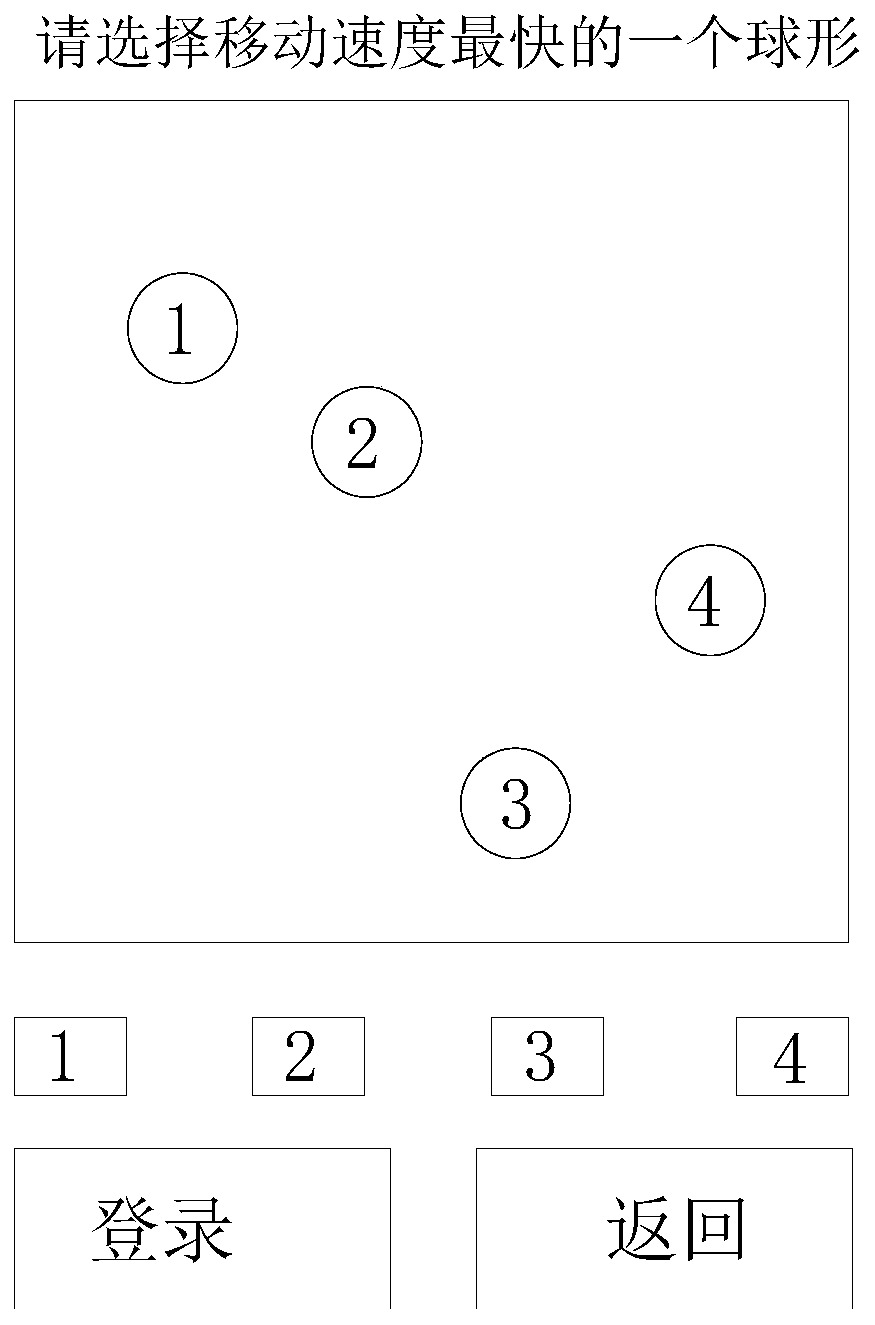
[0058] Such as image 3 As shown, the verification code generation method of this embodiment includes the following steps:
[0059] S50: generating three spherical patterns and one square pattern;
[0060] S51: selecting a square pattern as the target pattern.
Embodiment 3
[0062] Such as Figure 4 As shown, the verification code generation method of this embodiment includes the following steps:
[0063] S60: generating four square patterns with arrows, wherein the arrows on three square patterns point to the left, and the arrows on the other square pattern point to the right;
[0064] S61: A square pattern with an arrow pointing to the right is selected as the target pattern.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com