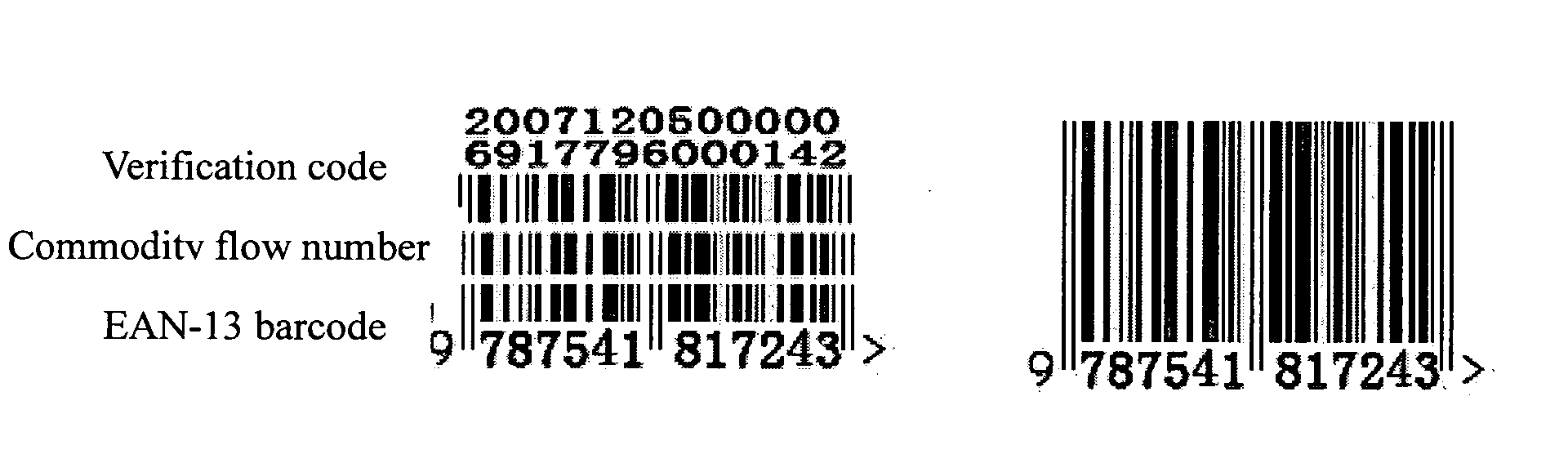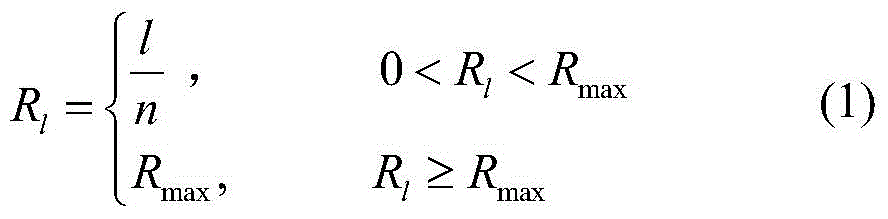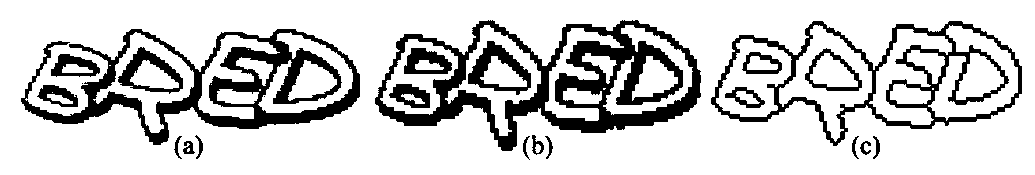Patents
Literature
69 results about "Verilog code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
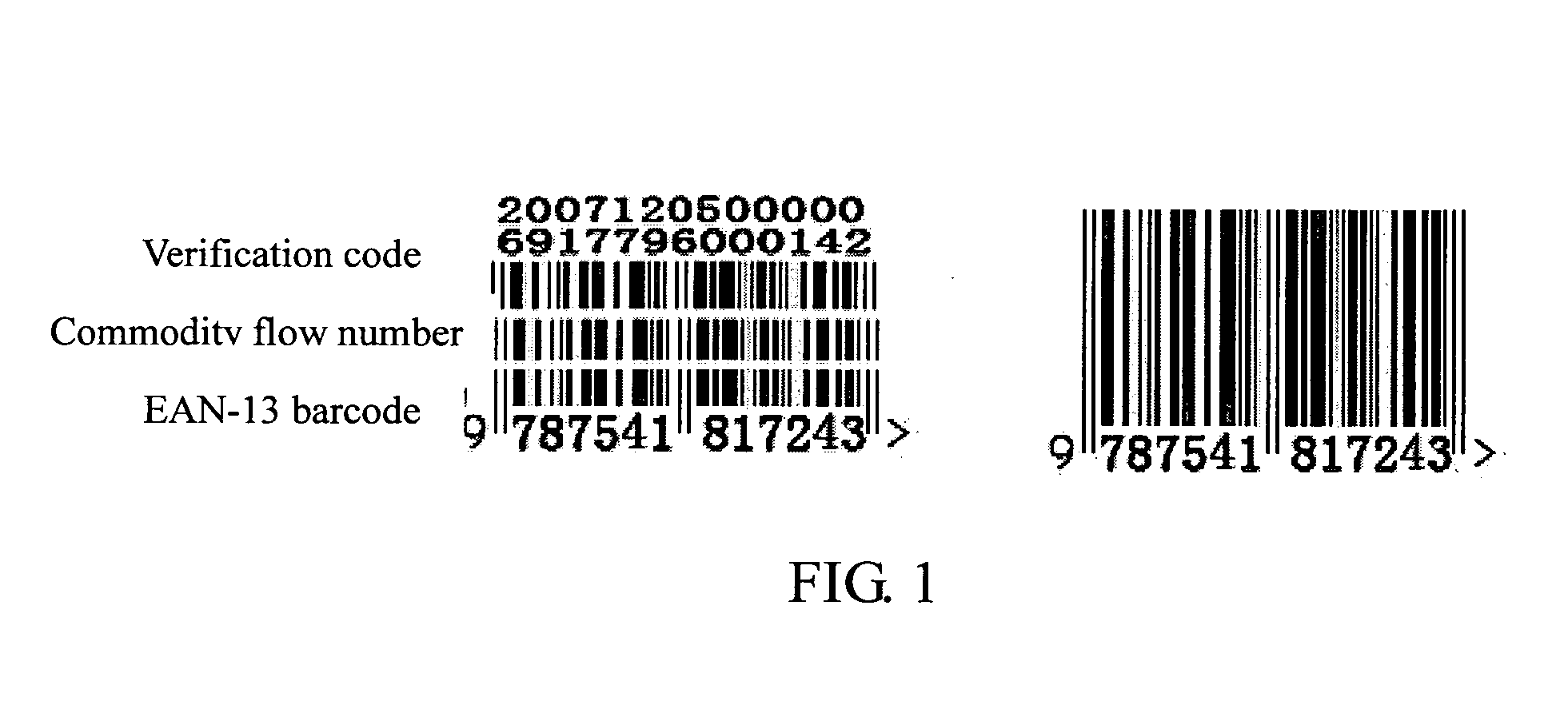
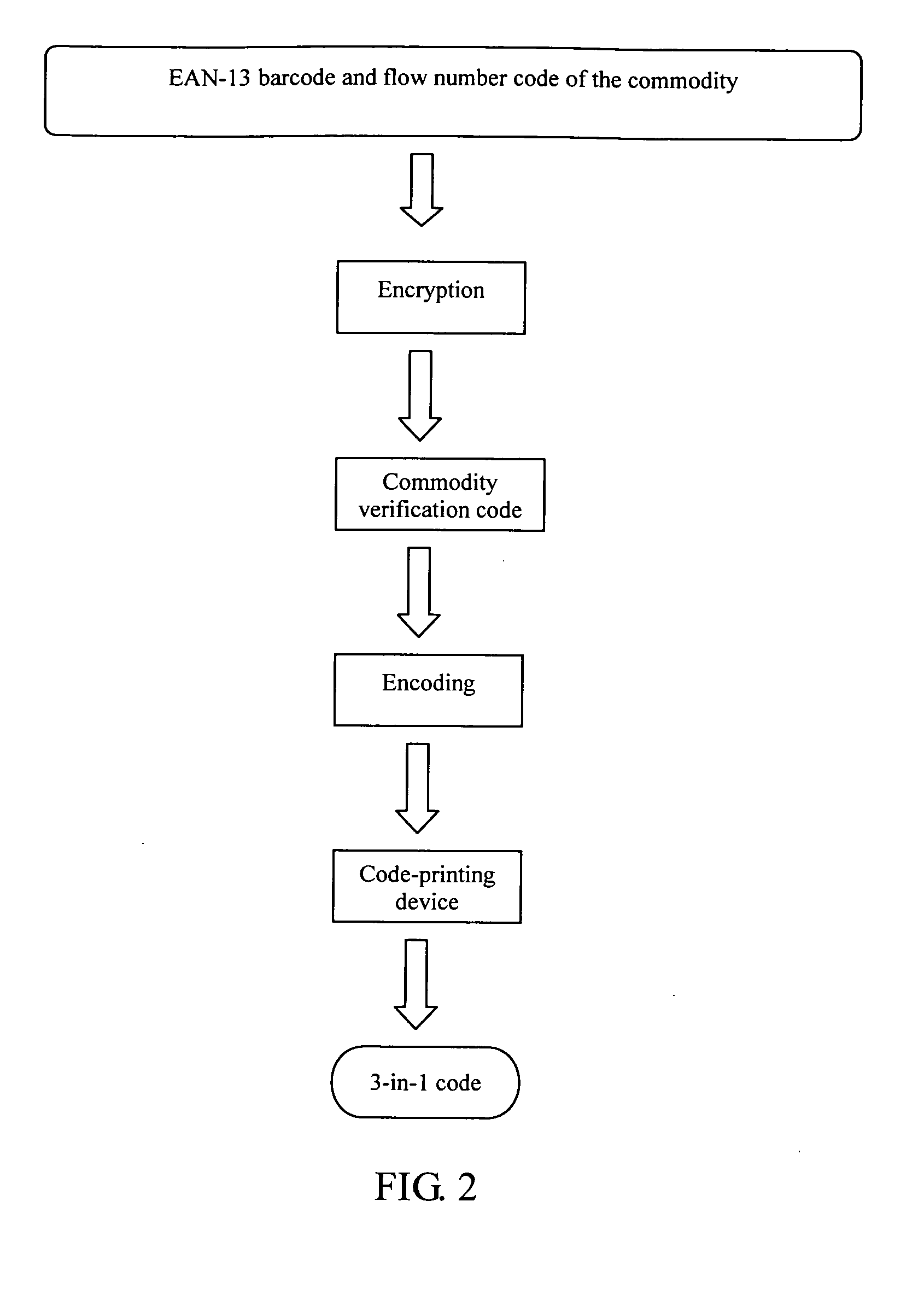
3-in-1 barcode for identifying commodity
InactiveUS20100258641A1Easy to identifyEasy to counterfeitResourcesRecord carriers used with machinesBarcodeComputer science
A 3-in-1 barcode for identifying a commodity, involving a commercial cipher technology, is implemented through the following steps: acquiring a first and second group of data in the form of 13-digit decimal number that are input into a computer for being processed; determining whether the first group of data satisfies an EAN-13 encoding principle or not, and whether the second group of data satisfies an commodity flow number encoding principle or not, if yes, proceeding to the next step, otherwise, generating an error prompt; performing an encryption operation on the first group of data satisfying the EAN-13 encoding principle and the second group of data satisfying the commodity flow number encoding principle through a commercial cipher algorithm, and generating a 13-digit decimal verification code data; dividing the first group of data, the second group of data, and the verification code data into three rows by the computer; and storing and printing the 3-in-1 barcode divided into three rows by the computer, for machine identification. The advantage of the present invention lies in that the 3-in-1 barcode has a plain part and a cipher part, which is easily identified by both the users and consumers, and cannot be easily counterfeited and forged.
Owner:YU ZHI
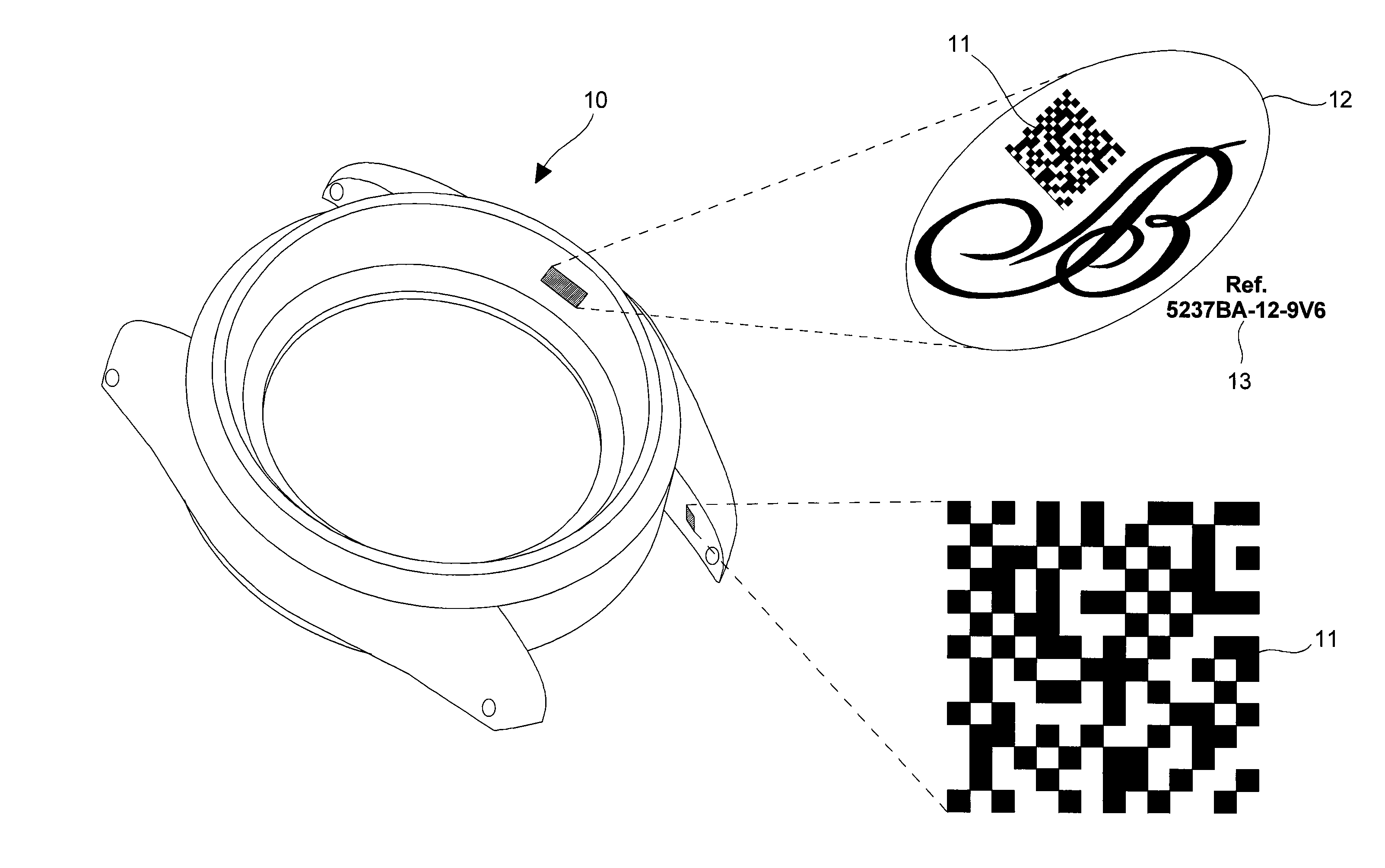
Method of coded marking of a product of small size, and marked product obtained according to said method
InactiveUS20090302123A1Small sizeImprove securityRecord carriers used with machinesBarcodeComputer science
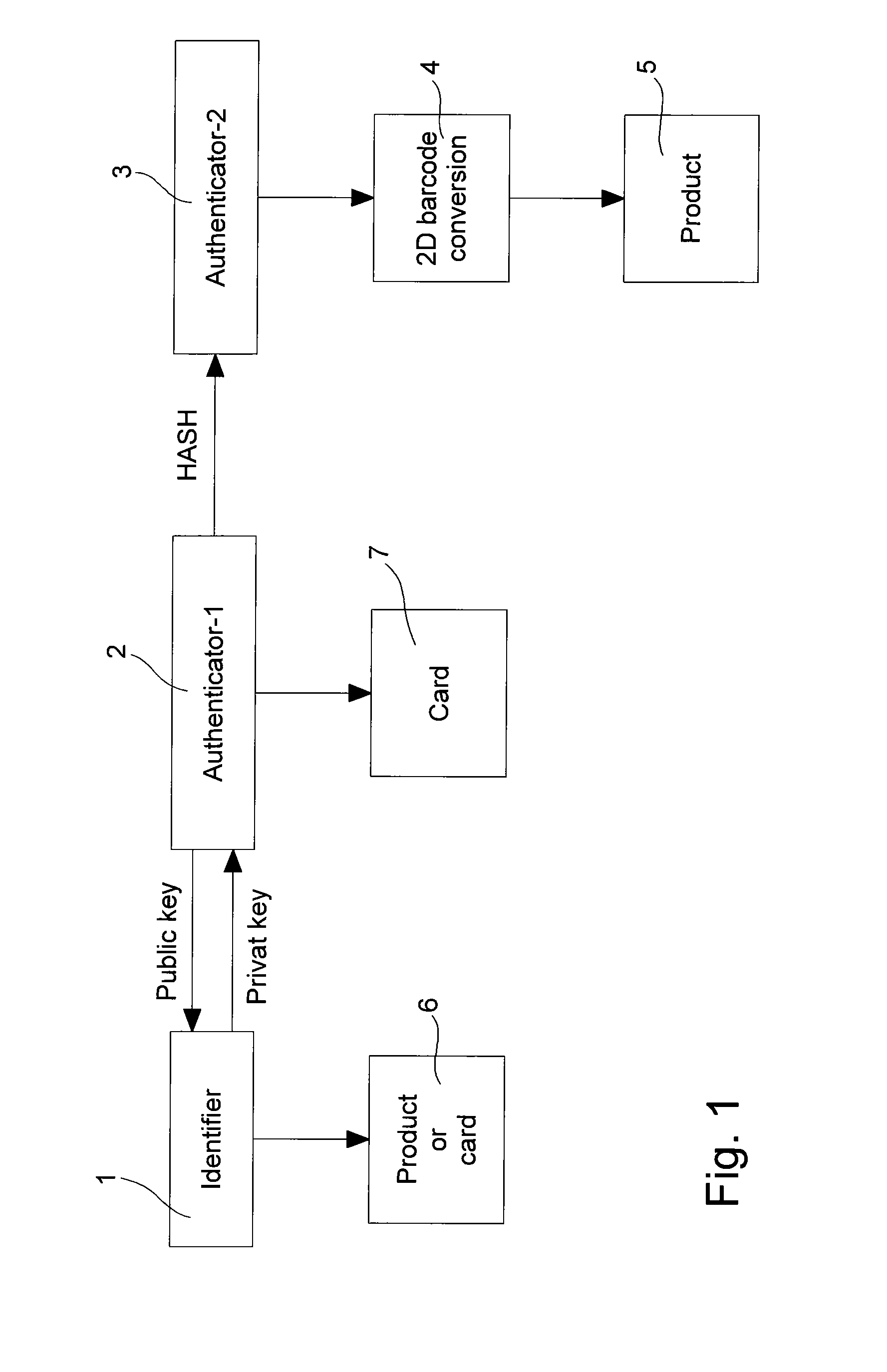
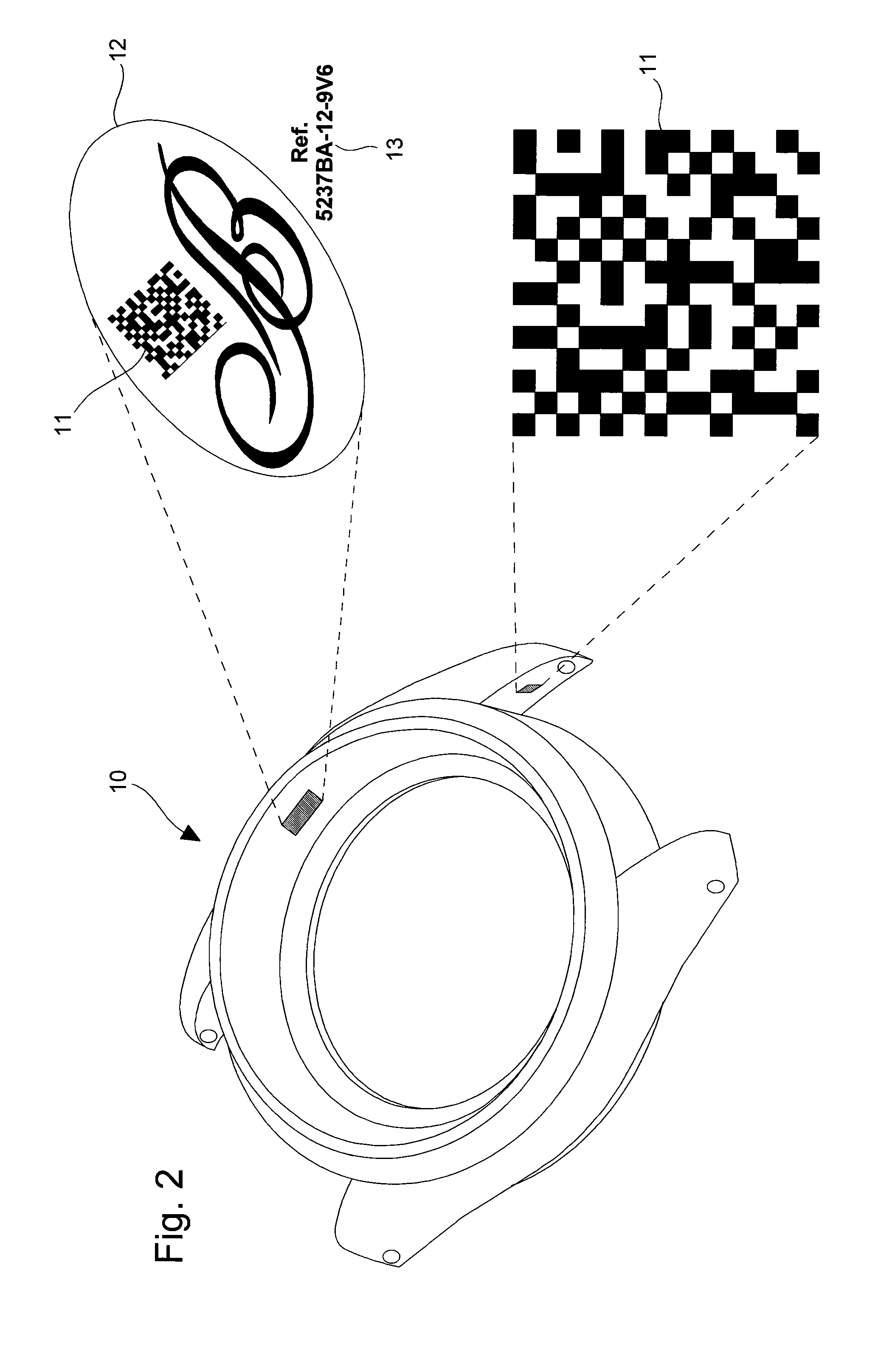
The method is for coded marking of a product of small size, such as horological or jewelry product (10). The method consists in carrying out a first mathematical operation of encrypting an identifier (13), such as a serial number of the product to be marked using a specific security algorithm key to obtain a first authenticator. The first authenticator includes a first data length defined by a first large number of alphanumerical characters. This first authenticator is encrypted using a second mathematical operation using a Hash type function into a second authenticator. This second authenticator includes a second data length defined by a second reduced number of alphanumerical characters shorter than the first number of characters. The second authenticator is converted into a coded image, which is preferably a two dimensional barcode (11) so as to be placed on the product as the coded mark in order to allow said product to be authenticated.
Owner:MONTRES BREGUET
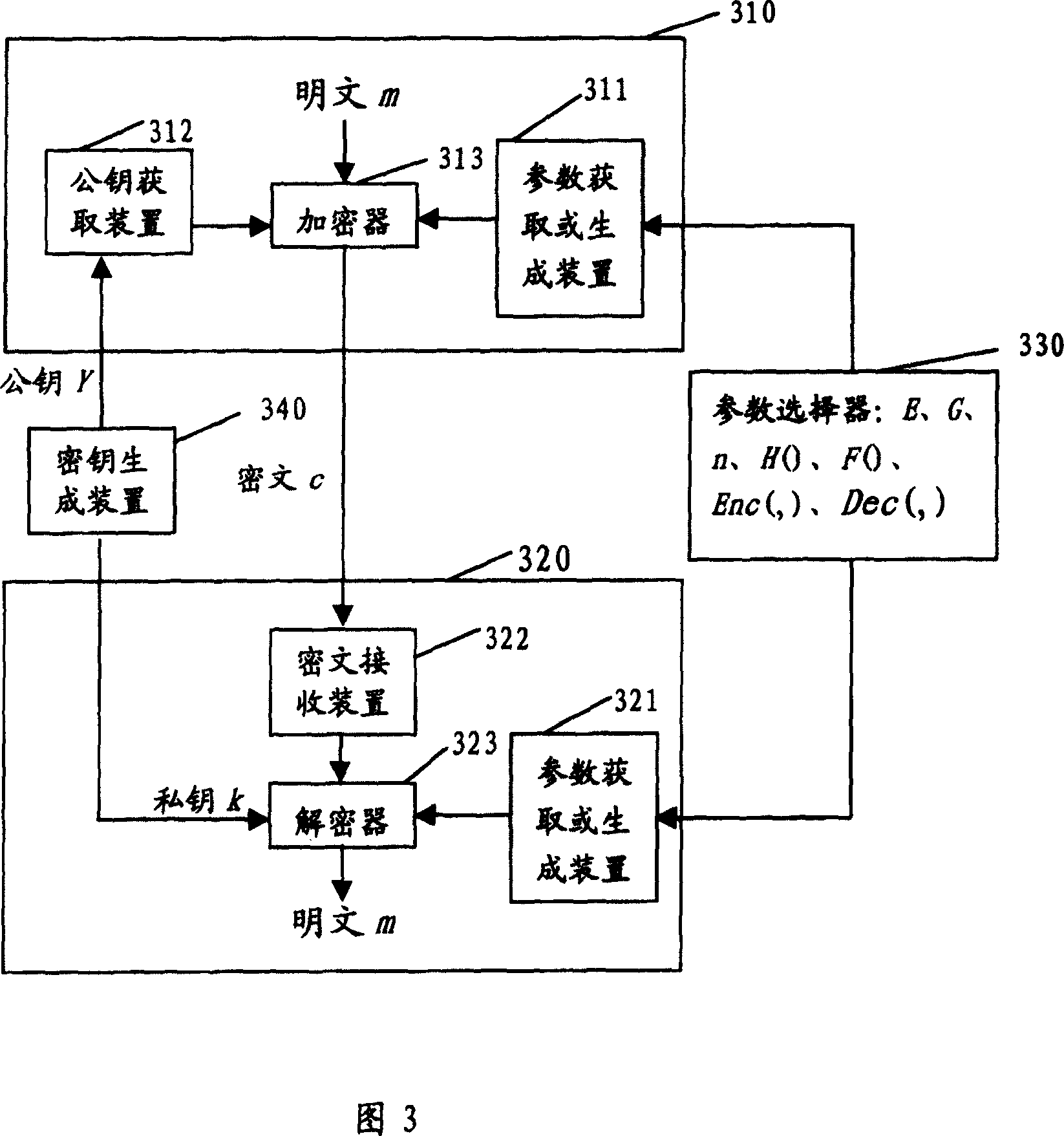
Highly secure ellipse curve encryption and decryption method and device
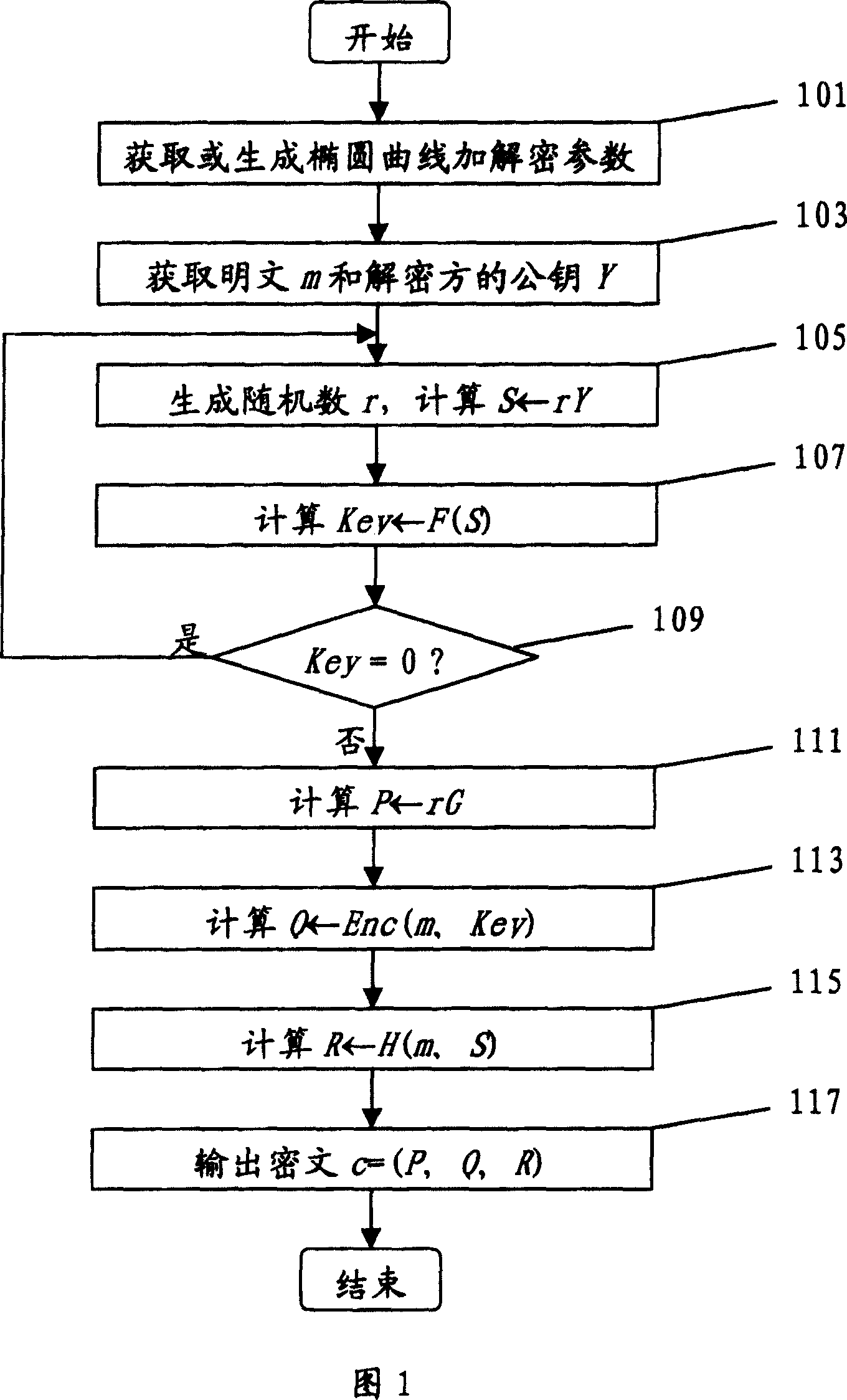
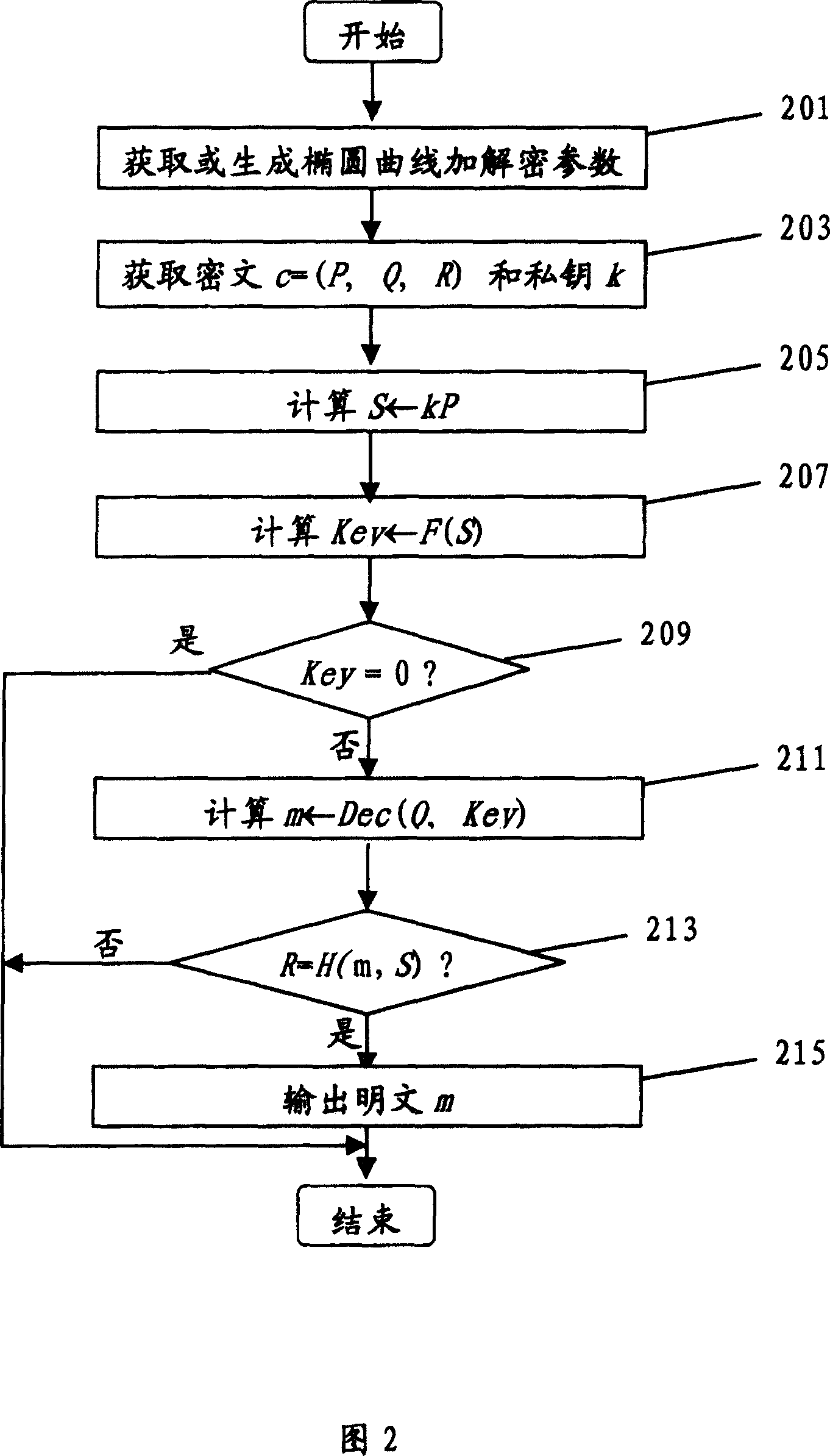
ActiveCN101079701AOvercoming security deficienciesPublic key for secure communicationDecoding methodsPlaintext
Owner:BEIJING HUADA INFOSEC TECH
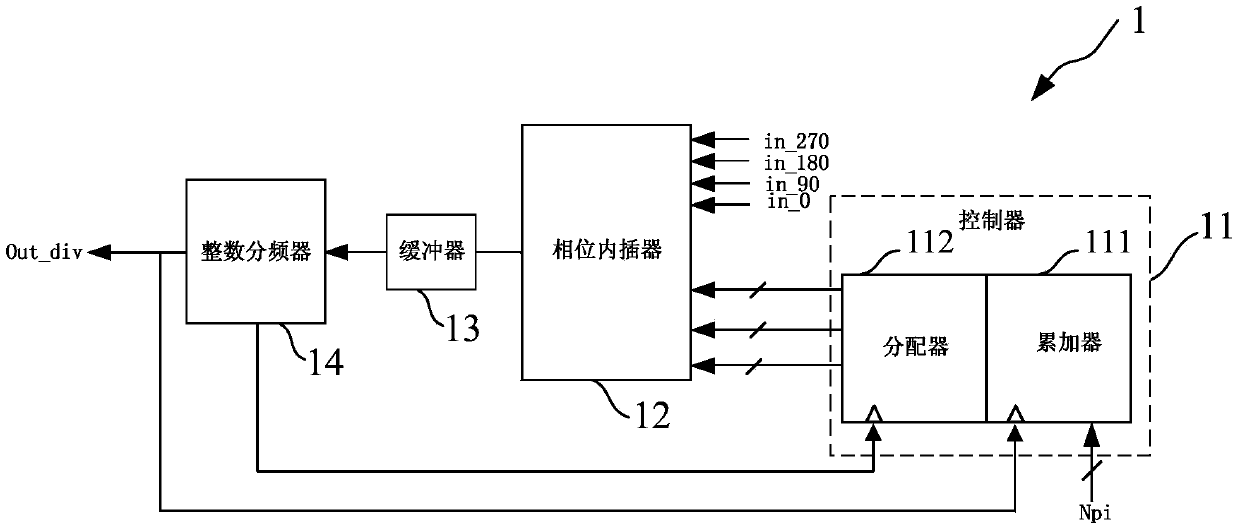
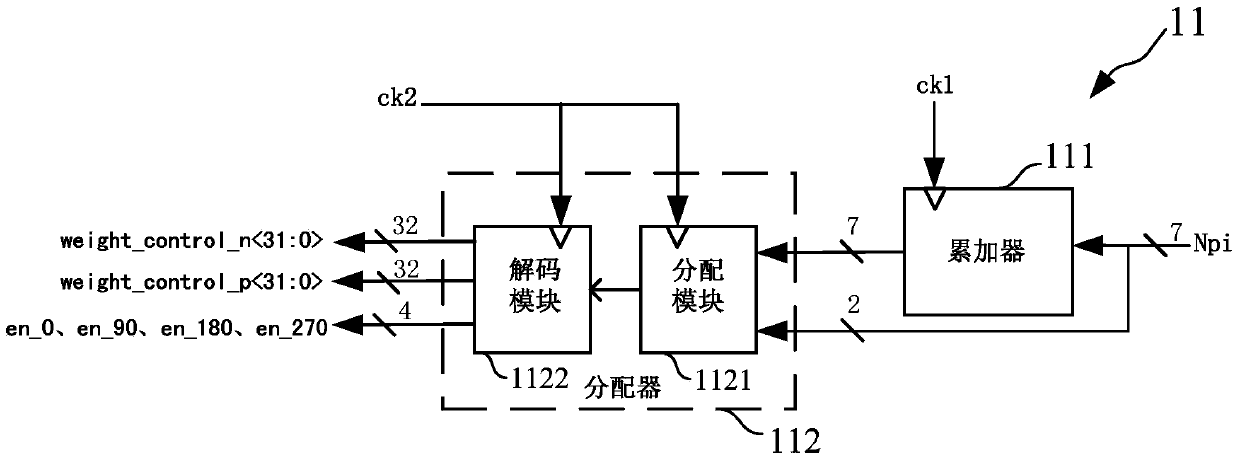
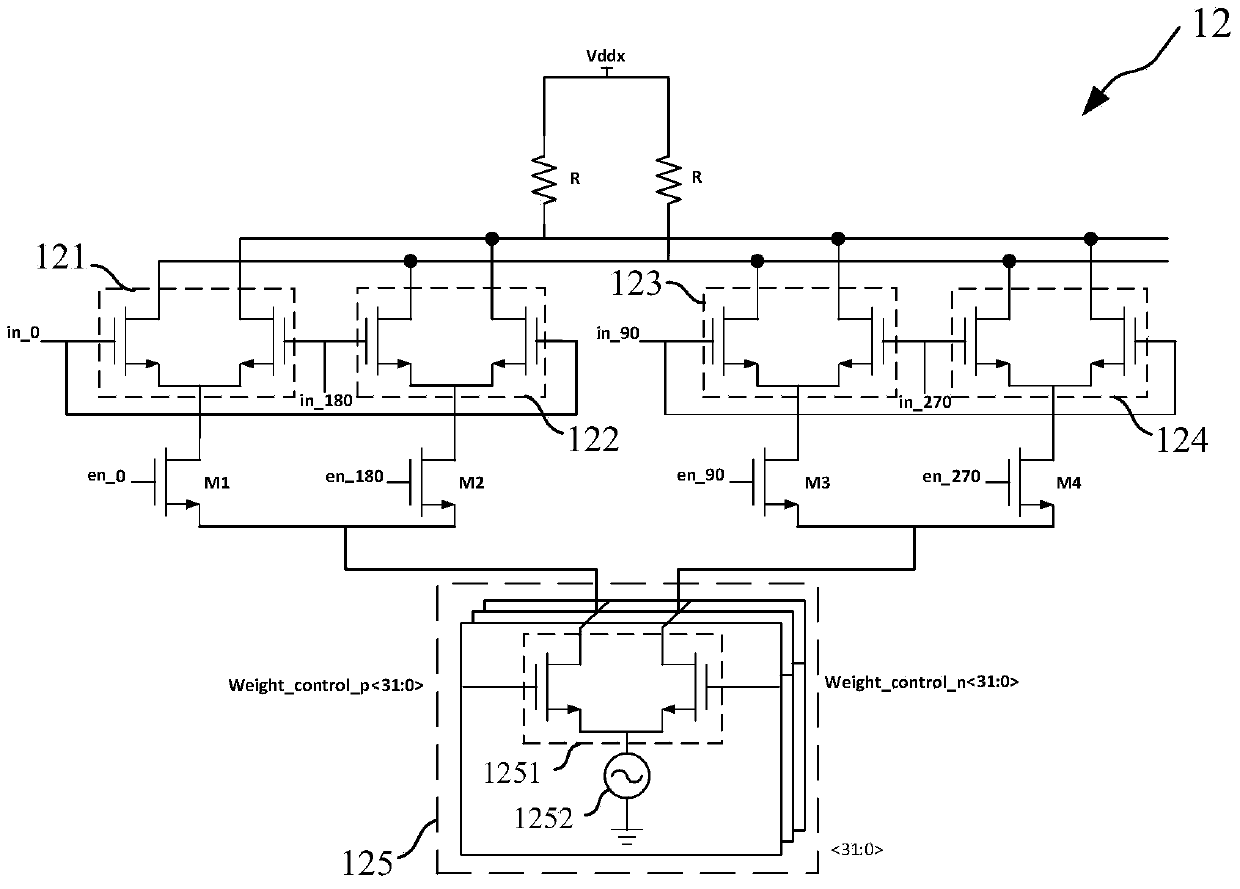
Fractional frequency divider
InactiveCN104184461AAvoid Quantization NoiseQuantization Noise ImprovementCounting chain pulse countersControl signalReusability
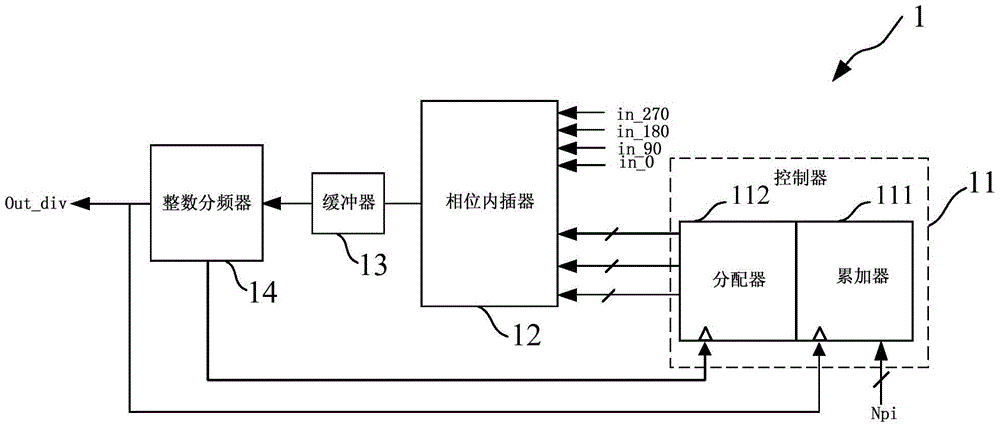
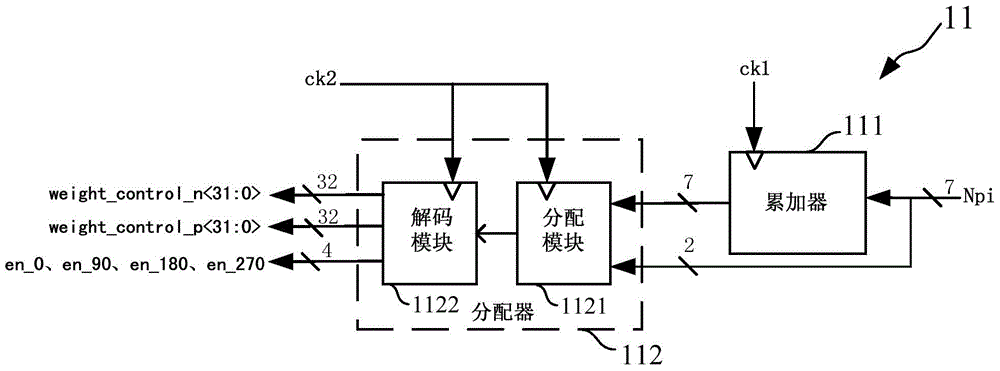
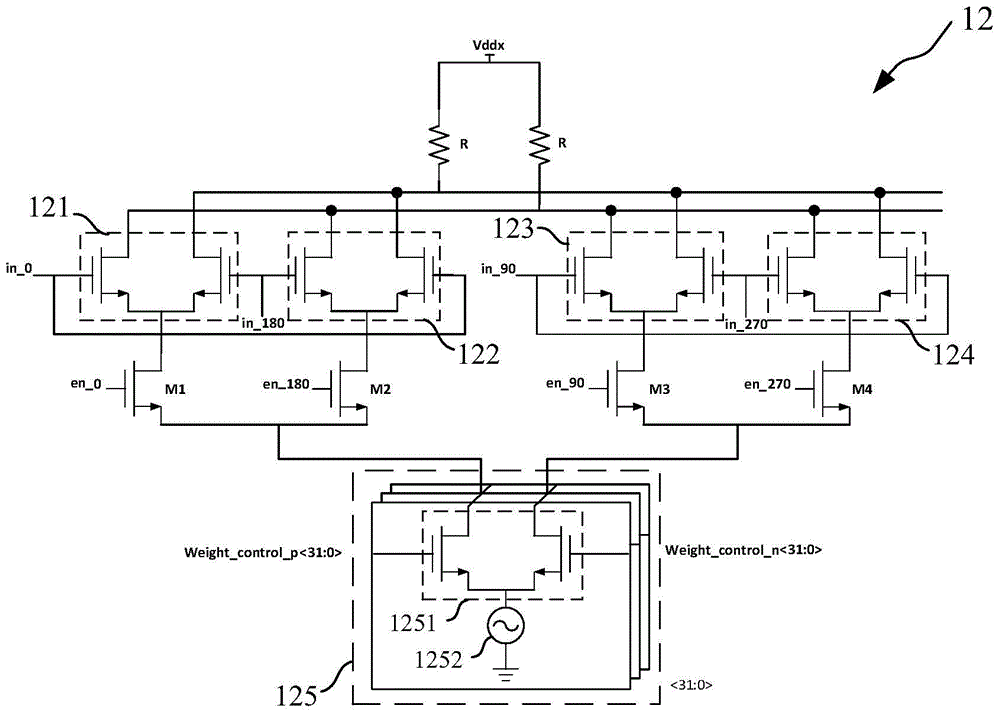
The invention provides a fractional frequency divider which comprises a controller, a phase interpolater, a buffer and an integer frequency divider. The controller generates control signals. The phase interpolater is controlled by the controller to achieve frequency division of a fractional part. The buffer is used for shaping signals output by the phase interrpolater, and the integer frequency divider is connected to the buffer and achieves frequency division of an integer part. The fractional frequency divider can be used in a digital phase-locked loop system and also can be used in a simulation phase-locked loop system, a digital phase-locked loop system difficult to deign based on a TDC is avoided, and the design of a full digital phase-locked loop system is greatly simplified. Quantizing noise generated by a delta-sigma modulator is avoided, the quantizing noise of the system is greatly improved, and the system performance is optimized. Meanwhile, extra circuit compensation is of no need in the design process of the phase interpolater, and therefore the design is simple. The logic of the controller is simple and can be achieved through a Verilog code, and the reusability is good.
Owner:SHANGHAI JIAO TONG UNIV
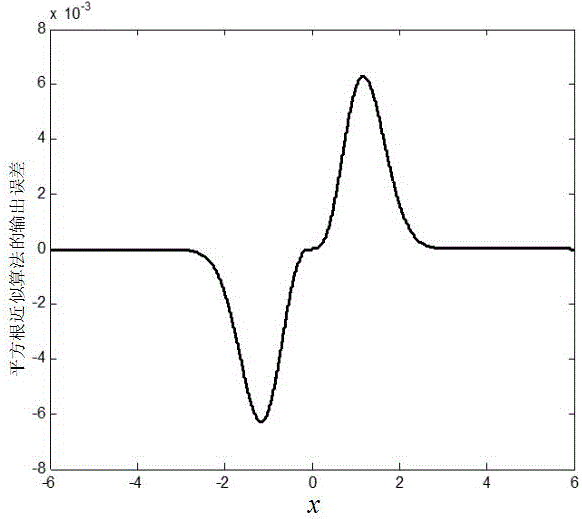
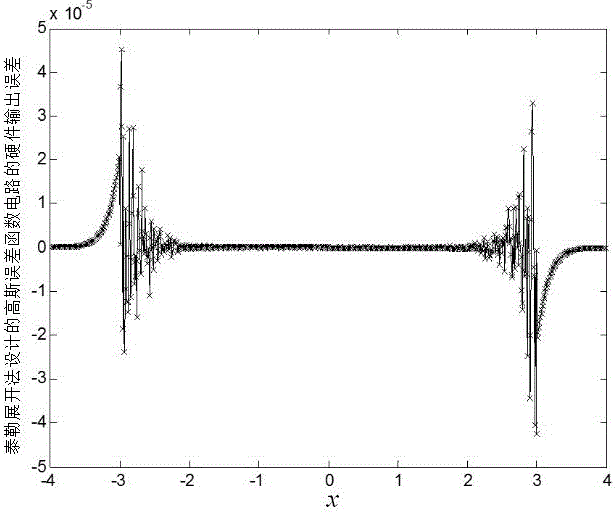
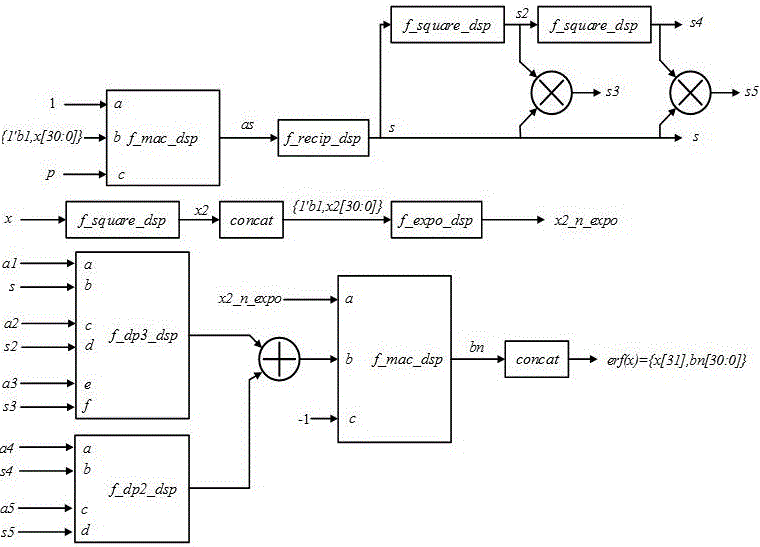
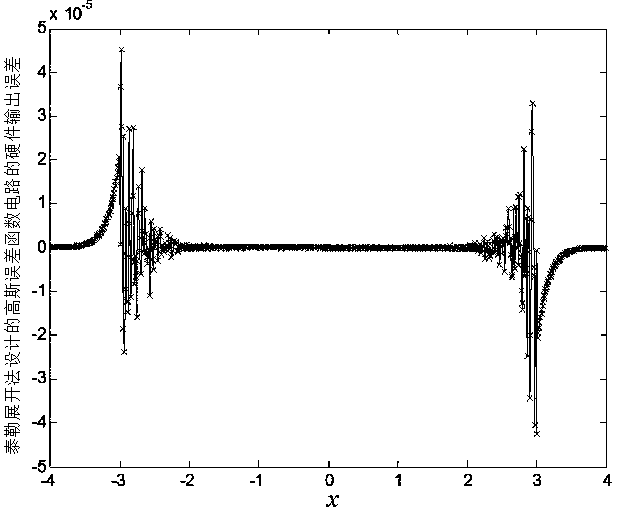
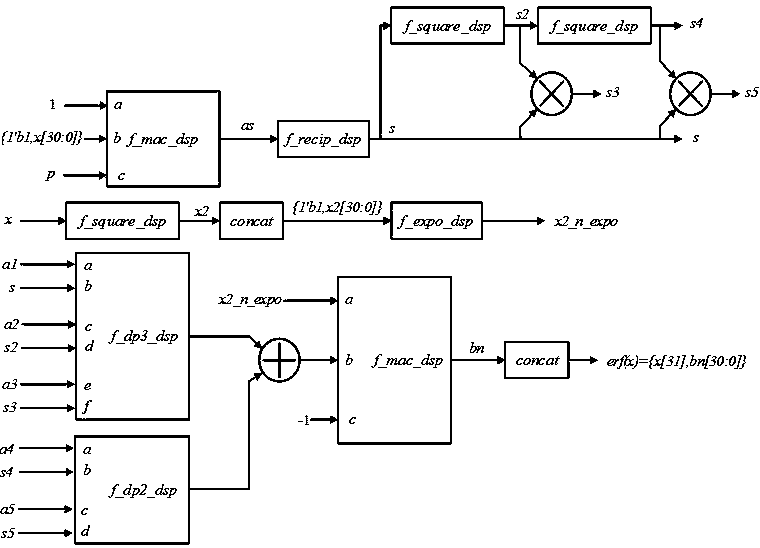
Gaussian error function circuit applied to neural networks
ActiveCN106682732AHigh precisionReduce complexityDigital data processing detailsPhysical realisationNerve networkBinary multiplier
The invention discloses a Gaussian error function circuit applied to neural networks. The Gaussian error function circuit comprises three squarers, two multipliers, two multiplier-adders, two dot product digital signal processors, an adder, a derivation DSP, and an exponent DSP. The DSPs are Design Ware floating-point DSPs from Synopsys. The circuit has a simple structure, uses DSPs easy to obtain, and is easy to implement. Compared with the traditional Taylor expansion method implementation scheme, the circuit has very obvious advantages in terms of precision, area and speed, and especially, the precision is at least two orders of magnitude higher. Meanwhile, the circuit can be implemented using a Verilog code, and has nothing to do with any specific process, so that the circuit can be applied to different processes very easily and is of very strong portability. The Gaussian error function circuit can be applied to the design of various hardware circuits related to neural networks as a soft-core IP.
Owner:ZHEJIANG UNIV
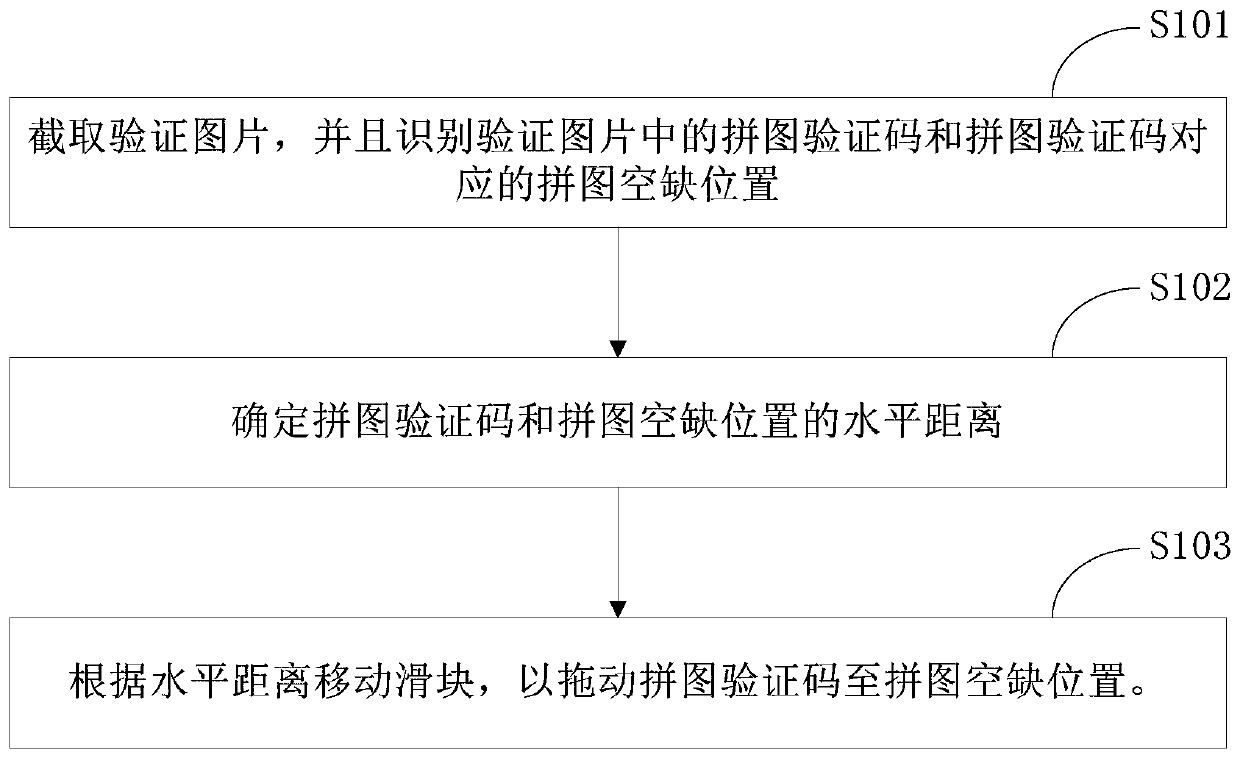
Method and device for realizing slider verification
PendingCN111311619AEfficient verificationImprove experienceImage enhancementImage analysisSoftware engineeringVerilog code
The invention discloses a method and a device for realizing slider verification, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: intercepting a verification picture, and identifying a jigsaw verification code in the verification picture and a jigsaw vacancy position corresponding to the jigsaw verification code; determining a horizontal distance between the jigsaw puzzle verification code and the jigsaw puzzle vacancy position; and moving the sliding block according to the horizontal distance to drag the jigsaw verificationcode to the jigsaw vacancy position. According to the method, slider verification can be completed quickly and efficiently, and the user experience is improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Automatic Verilog HDL code generator of parallel CRC (Cyclic Redundancy Check) algorithm and method thereof
InactiveCN101826011APromote generationSpecific program execution arrangementsParallel computingVerilog code
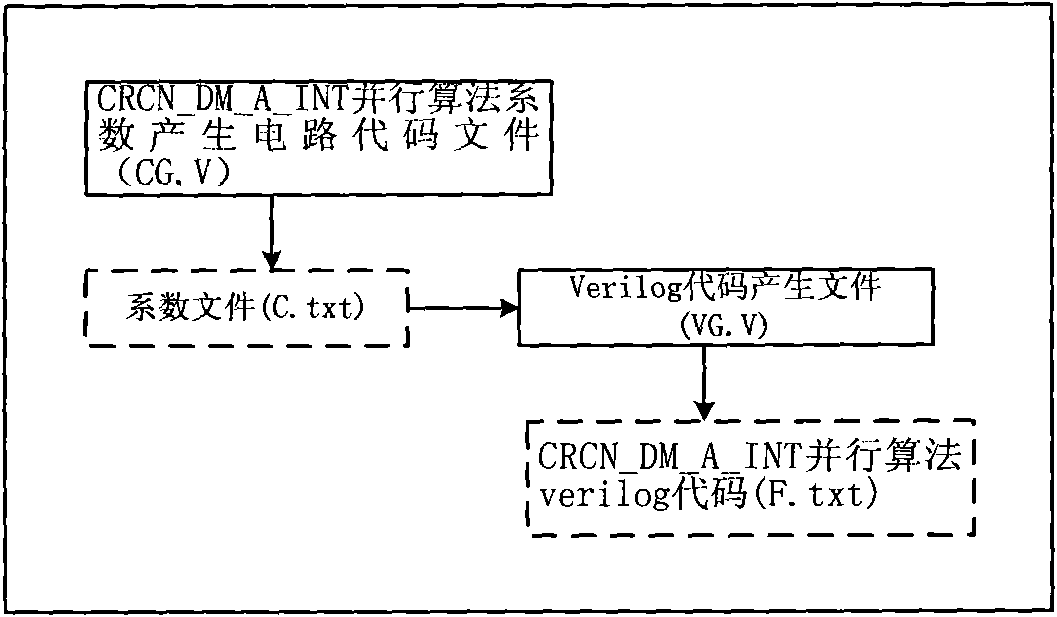
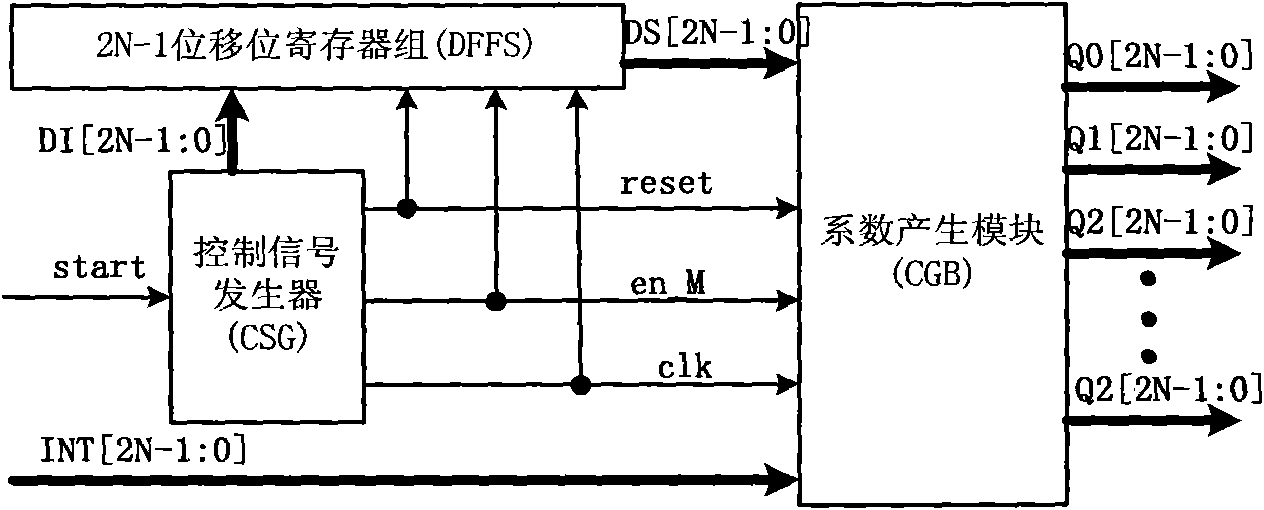
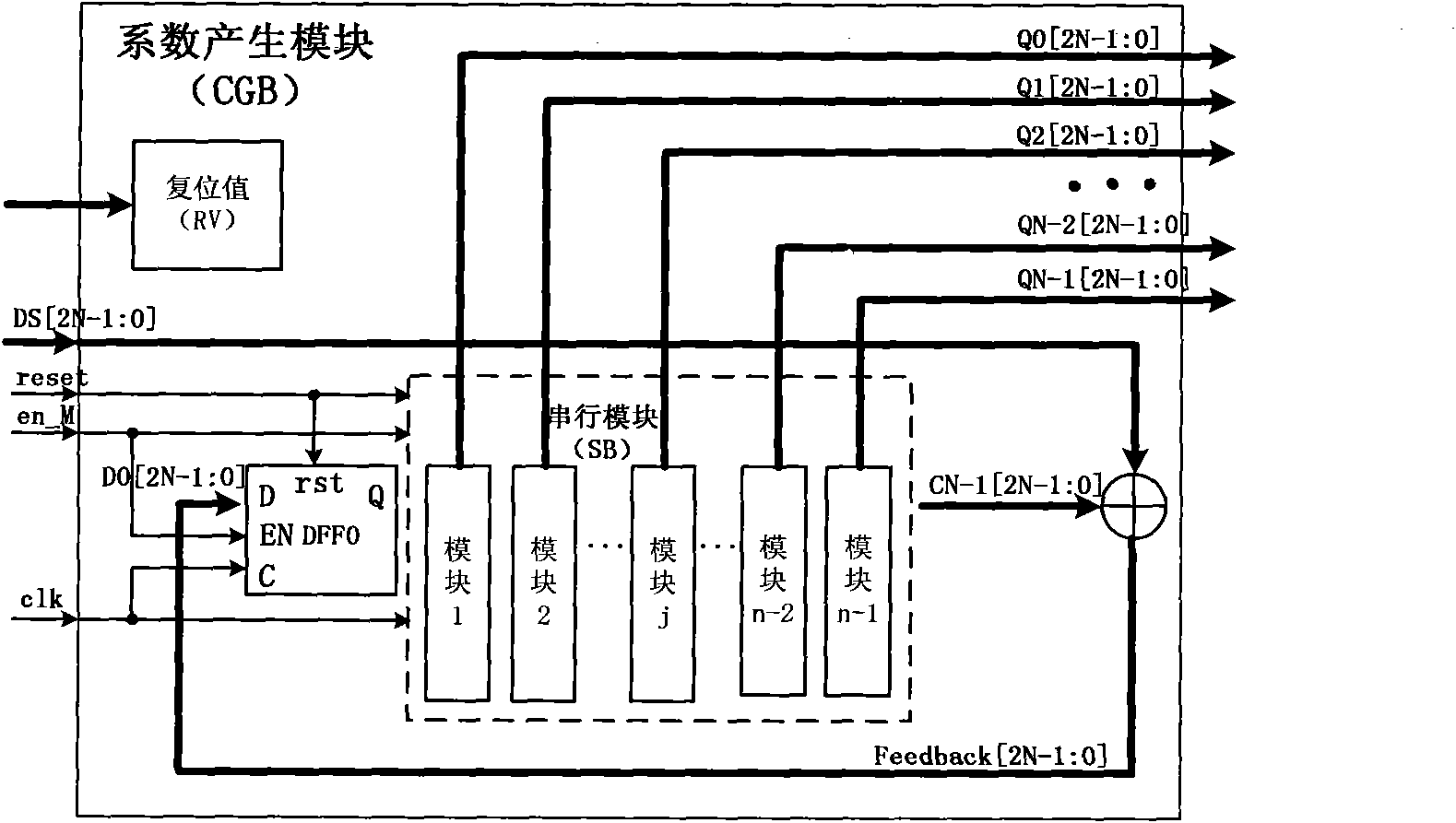
The invention relates to an automatic Verilog HDL code generator of a parallel CRC (Cyclic Redundancy Check) algorithm and a method thereof. The generator comprises a coefficient generation circuit based on a modelsim simulation platform, a coefficient file C.txt generated by operating a coefficient generation circuit code CG.v and a Verilog code file F.txt generated by operating a Verilog code generation file VG.v. The method comprises the following steps of: (1) extracting design parameters of N, M, A and INT; (2) obtaining the coefficient generation circuit by the design parameters of N, M, A and INT according to the design steps of the coefficient generation circuit; (3) expressing the coefficient generation circuit as CG.v by using the Verilog code; (4) obtaining the coefficient file C.txt by operating the CG.v; and (5) obtaining a Verilog code F.txt of the parallel CRC circuit by operating VG.v. In the invention, the Verilog HDL code generation of the parallel CRC algorithm is simplified.
Owner:XIAN KEYWAY TECH
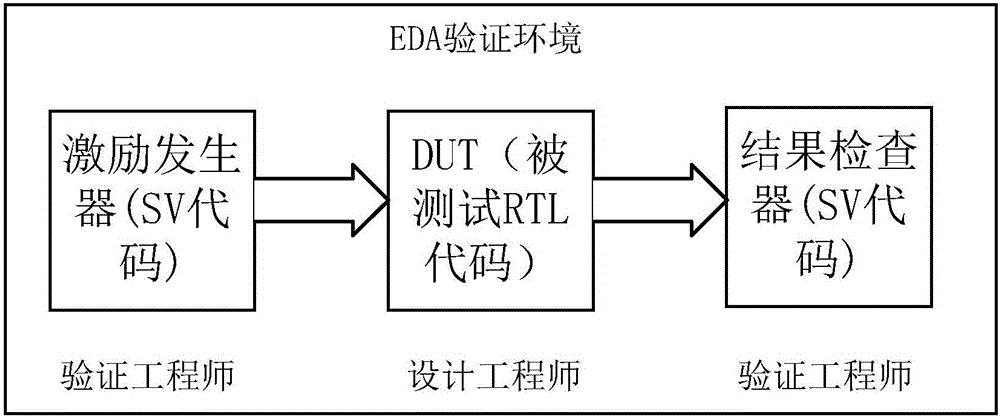
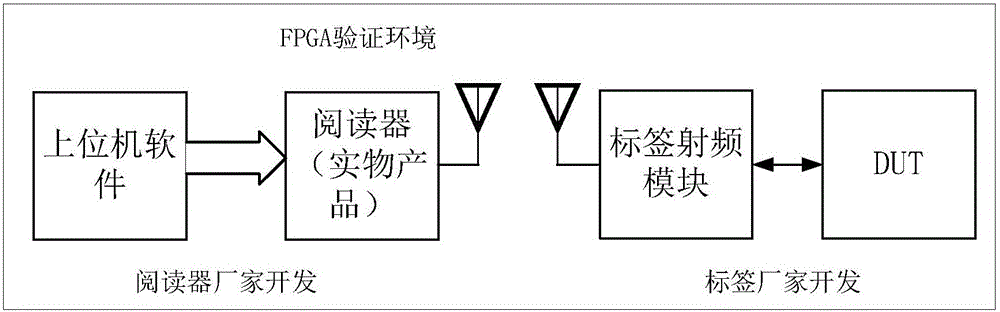
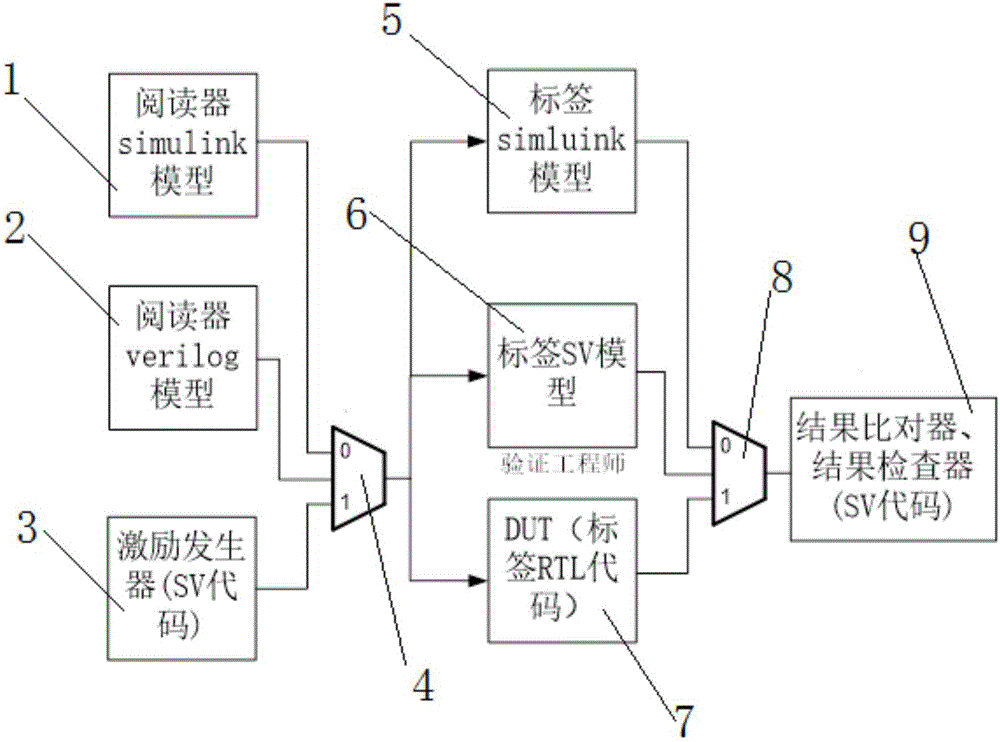
EDA (electronic design automation) and FPGA (field programmable gate array) reusable verification system for passive tag chips
ActiveCN106095675ARealize comparison verificationFully verifiedSoftware testing/debuggingVerilog codeVerification system
The invention relates to an EDA (electronic design automation) and FPGA (field programmable gate array) reusable verification system for passive tag chips. The EDA and FPGA reusable verification system comprises an EDA environment verification system and an FPGA environment verification system. A reader verilog model (2) and a DUT (device under test) (7) in the EDA environment verification system and a reader verilog model (1-3) and a DUT (1-10) in the FPGA environment verification system can be reused mutually. The EDA and FPGA reusable verification system has the advantages that the readers and verilog codes of tags can be reused in EDA and FPGA verification environments in the verification systems, accordingly, codes for EDA and FPGA are identical, RTL (resistor transistor logic) codes do not need to be modified between the two verification systems, and high risks due to little modification can be prevented.
Owner:WUXI KEYBRIDGE ELECTRONICS TECH CO LTD
Debugging interface management method and device and electronic equipment
PendingCN111756703AAvoid crackingImprove securityMessaging/mailboxes/announcementsTransmissionSoftware engineeringVerilog code
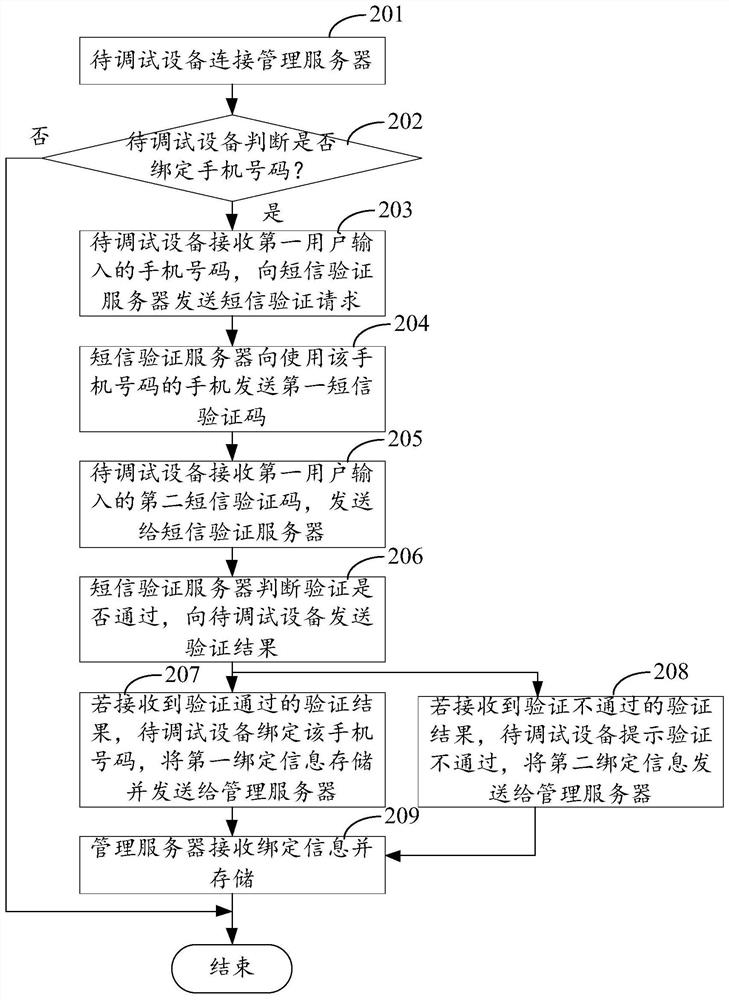
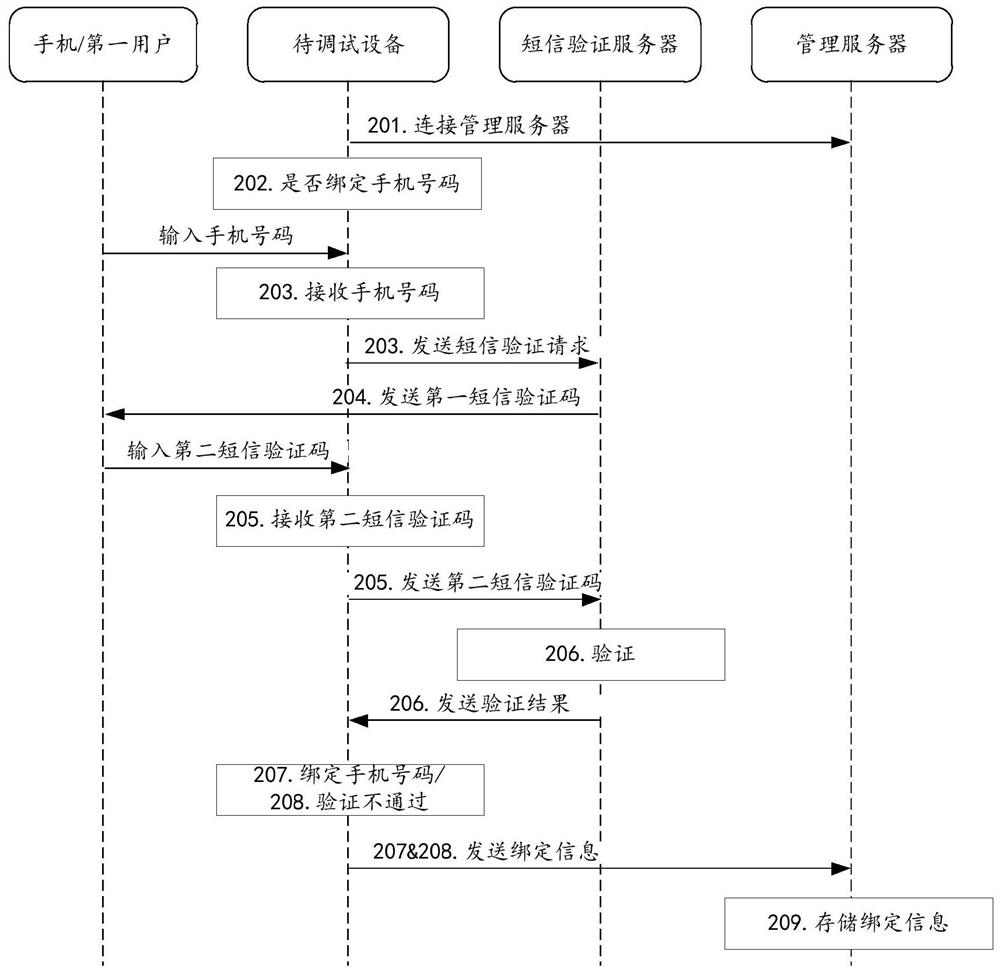
The invention relates to the technical field of computers, and discloses a debugging interface management method and device and electronic equipment. The method comprises the following steps: receiving an instruction input by a user for opening an Android debugging bridge (ADB) interface of equipment; acquiring a communication number bound with a debugging interface management function of the equipment according to the instruction; sending a first verification code to the acquired communication number; receiving a second verification code input by the user; and if the second verification codeis matched with the first verification code, opening the ADB interface. By means of the mode, the safety of ADB interface connection is improved.
Owner:RAJAX NETWORK &TECHNOLOGY (SHANGHAI) CO LTD
Verification code processing method and device, terminal and storage medium
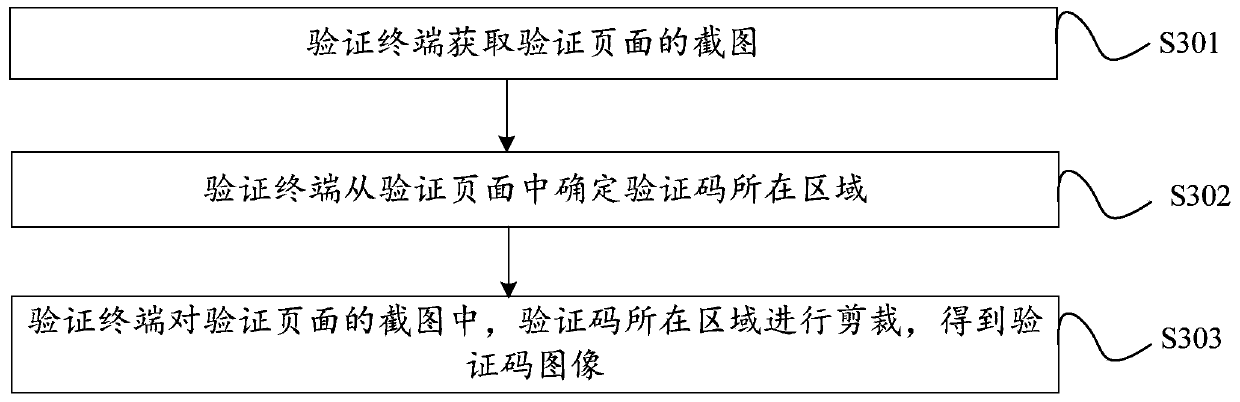
InactiveCN111404938AImprove test efficiencyLow costImage enhancementImage analysisProgramming languageTest efficiency
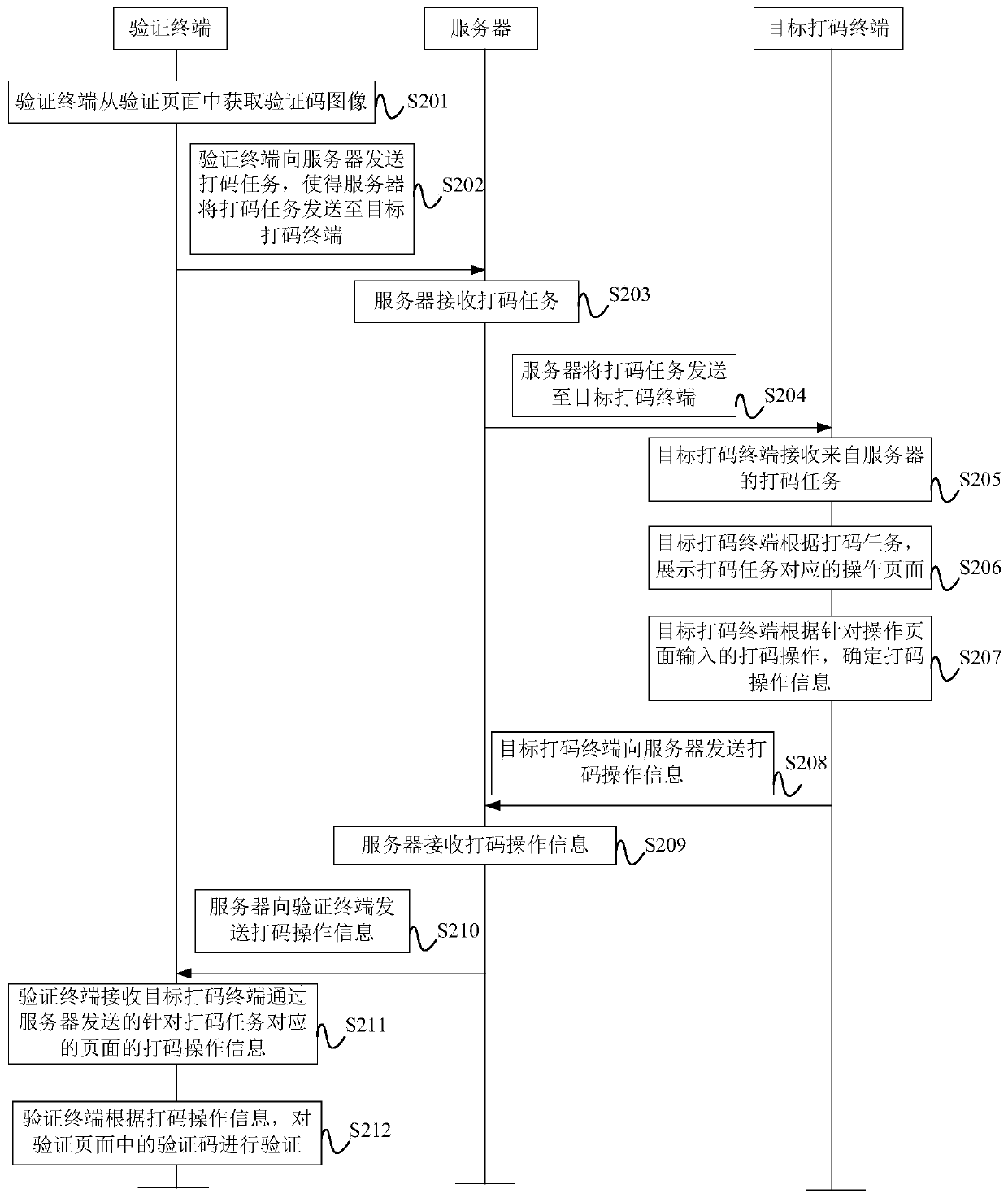
The invention provides a verification code processing method and device, a terminal and a storage medium, and relates to the technical field of data processing. The method comprises the steps of obtaining a verification code image from a verification page, wherein the verification code image is an image of an area where a verification code is located in the verification page; sending the coding task to a server, so that the server sends the coding task to the target coding terminal; receiving code printing operation information, sent by the target code printing terminal through the server, fora page corresponding to the code printing task; and verifying the verification code in the verification page according to the coding operation information. The verification terminal sends a coding task to the target coding terminal through the server; the target coding terminal determines the coding operation information according to the operation of the coding personnel, the verification terminal verifies the verification code according to the coding operation information, more professional testers are not needed, the cost is saved, the coding personnel do not need to have professional testskills, and the verification code test efficiency is also improved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Verification code generation method and device
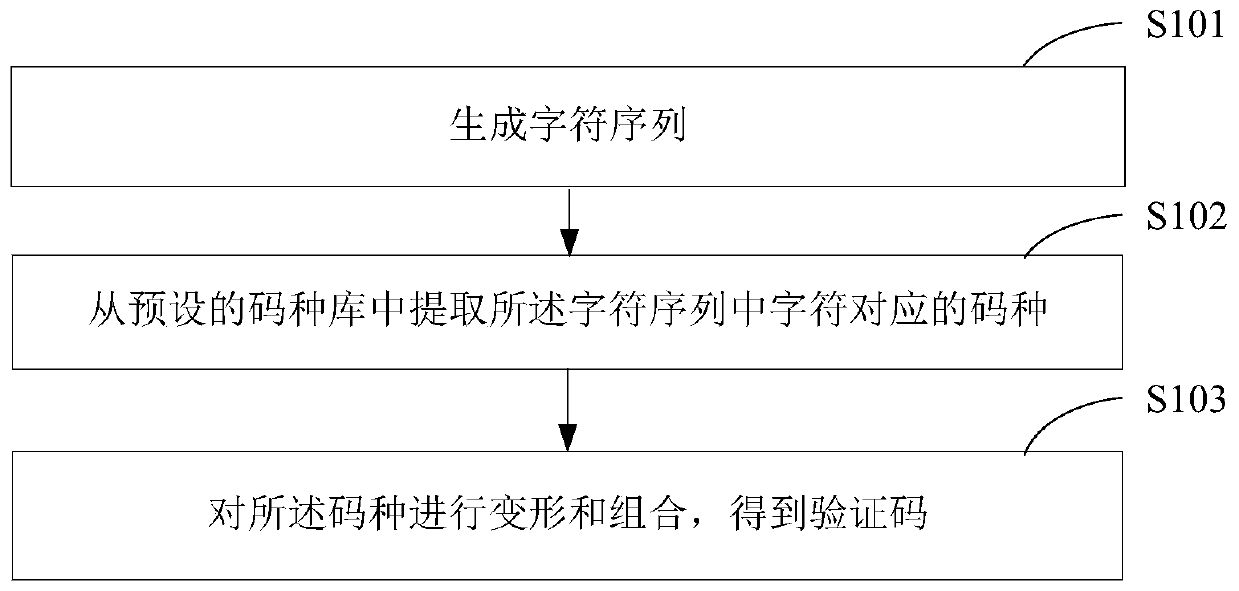
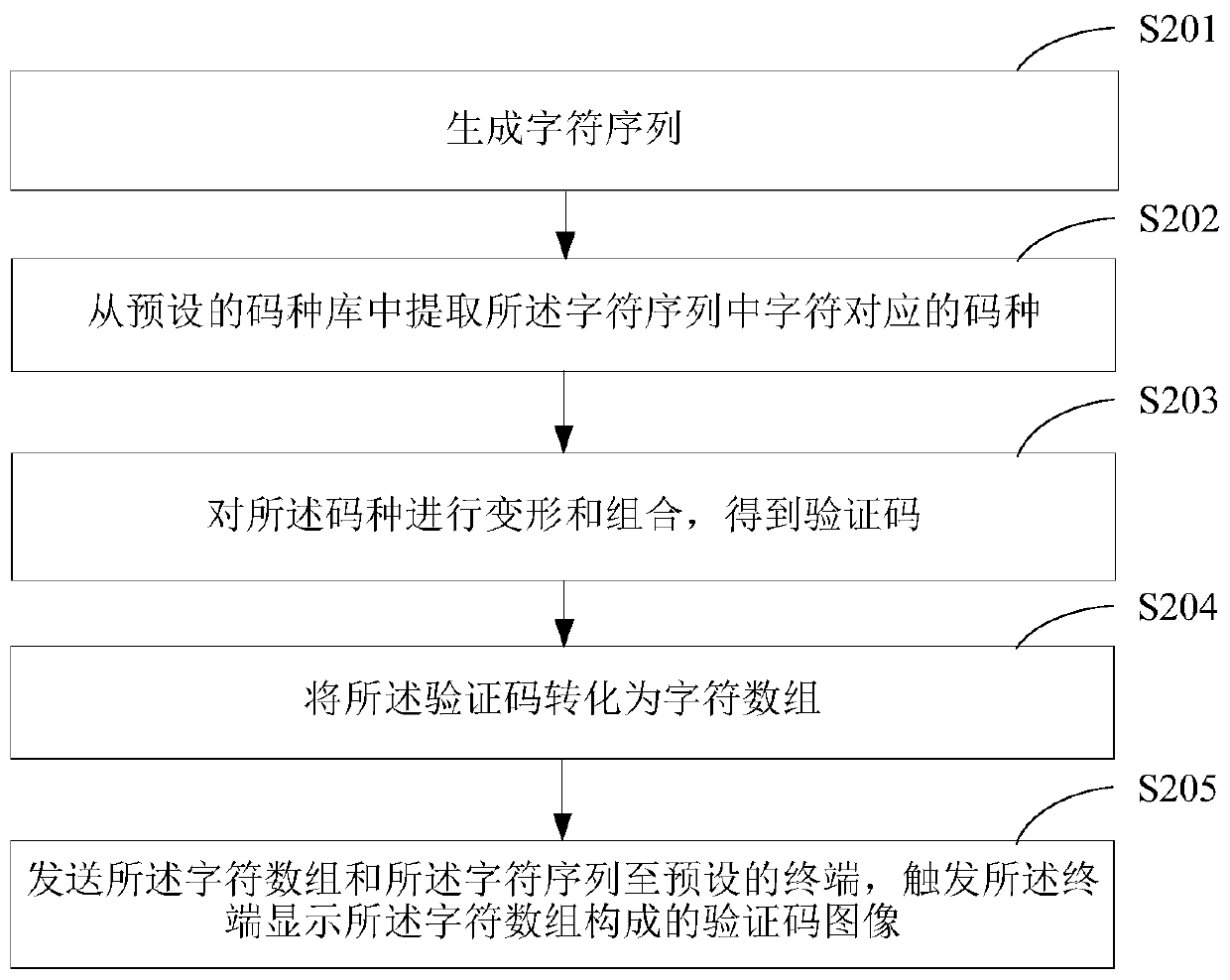
ActiveCN110677239AImprove securityMeet the needs of useKey distribution for secure communicationDigital data authenticationCode generationMorphing
The invention is suitable for the technical field of computer application, and provides a verification code generation method and device, and the method comprises the steps: generating a character sequence, wherein the character sequence is composed of letters and numbers; extracting code types corresponding to characters in the character sequence from a preset code type library; and deforming andcombining the code types to obtain the verification code. Through determining code type corresponding to a character sequence, deforming and combining the code types to obtain a verification code; and finally, generating a character matrix consisting of characters. In the character matrix, the characters with contrast form the image which can be recognized by human eyes and is composed of the characters, the requirement that the characters can be recognized by human beings but are difficult to recognize by machines is met through the display mode of the image, the use requirement of the character terminal is met, and the safety of verification code verification in the character terminal is also improved.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
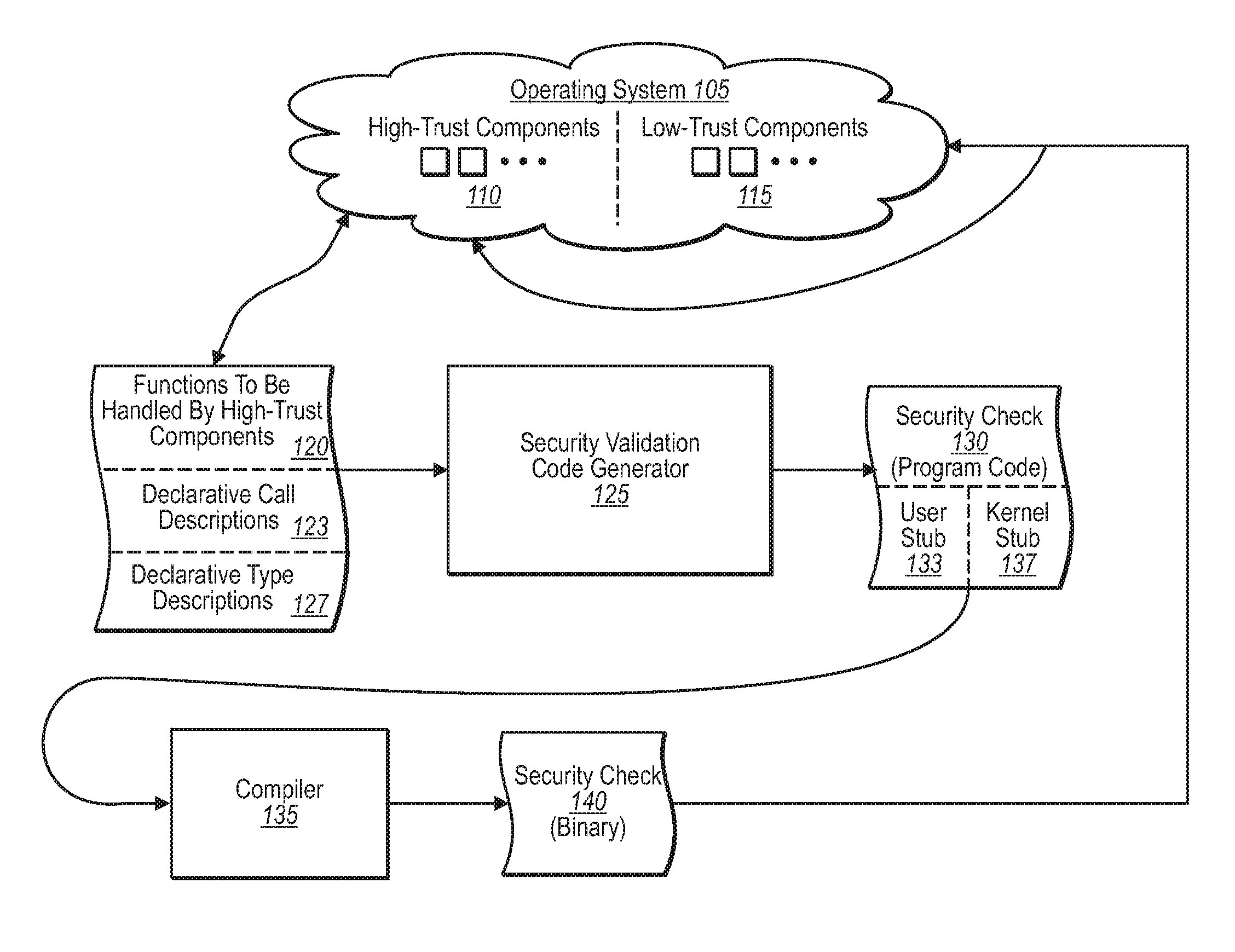
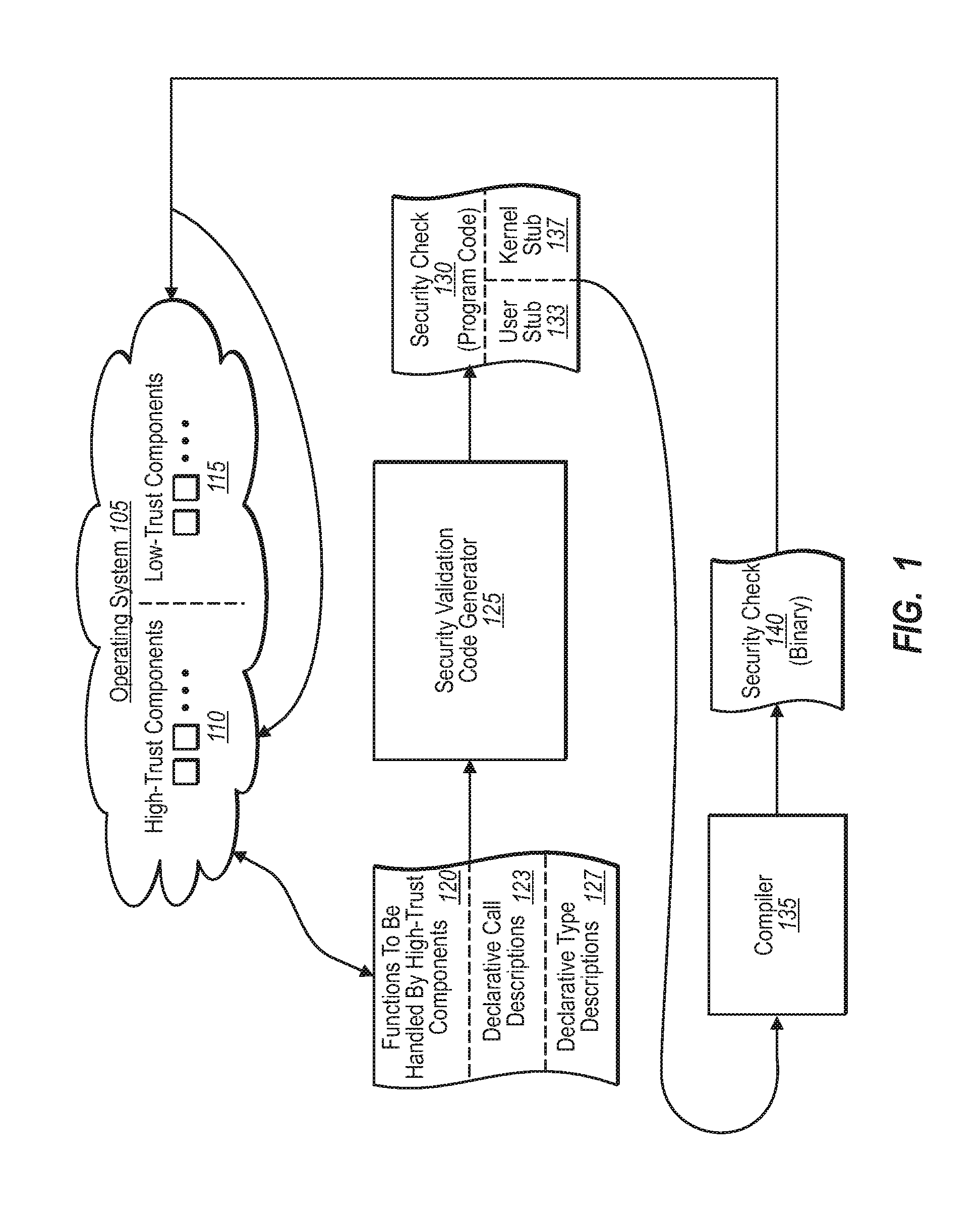
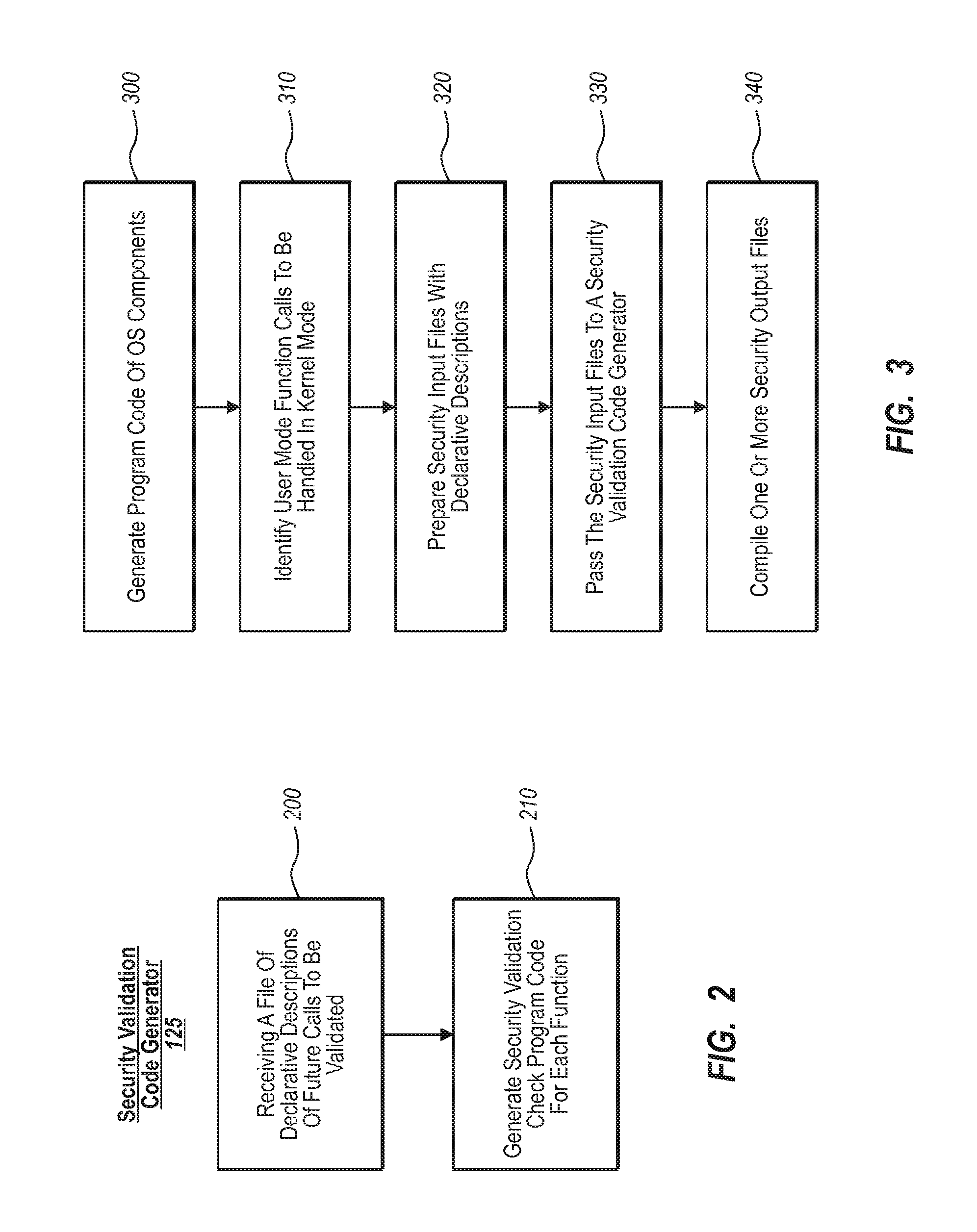
Generating security validation code automatically
A security program code generator is configured to automatically generate program code used to perform one or more validation checks of components operating in user mode. In one implementation, for example, the program code generator receives one or more files that include declarative values and parameters regarding one or more function calls made by any user mode component. The program code generator then takes the file of declarative call descriptions and automatically generates a user mode stub and a kernel mode stub for each function call of interest to be handled by a kernel mode component. The file(s) that include the user mode stub and the kernel mode stub can then be compiled and linked into the operating system components.
Owner:MICROSOFT TECH LICENSING LLC
Verification method and device
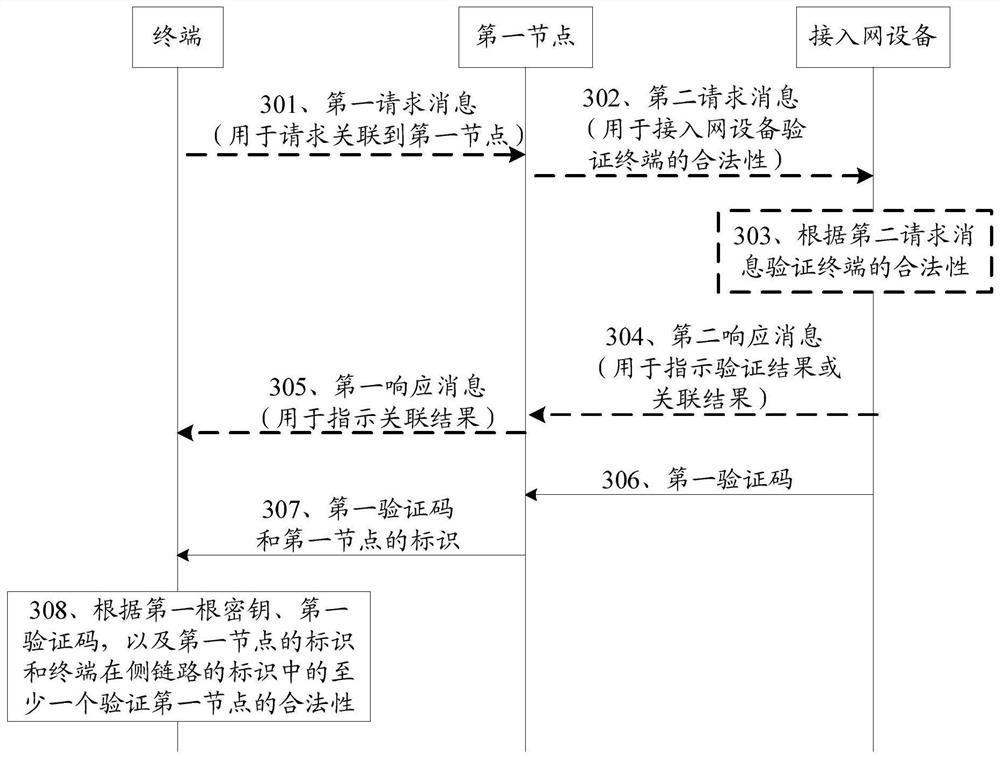
ActiveCN112019489AKey distribution for secure communicationUser identity/authority verificationAccess networkVerilog code
The invention provides a verification method and device, and relates to the technical field of communication. In the method, a terminal receives from a first node a first verification code generated according to a first root key and an identifier of the first node and the identifier of the first node, and verifies the legality of the first node according to the identifier of the first node, the first root key and the first verification code. The first root key is a root key used for communication between the terminal and the access network equipment.
Owner:HUAWEI TECH CO LTD
A standard answer generation method for an on-line Verilog code automatic decision system
ActiveCN109101239ACompilation supportedData processing applicationsReverse engineeringDecision systemVerilog code
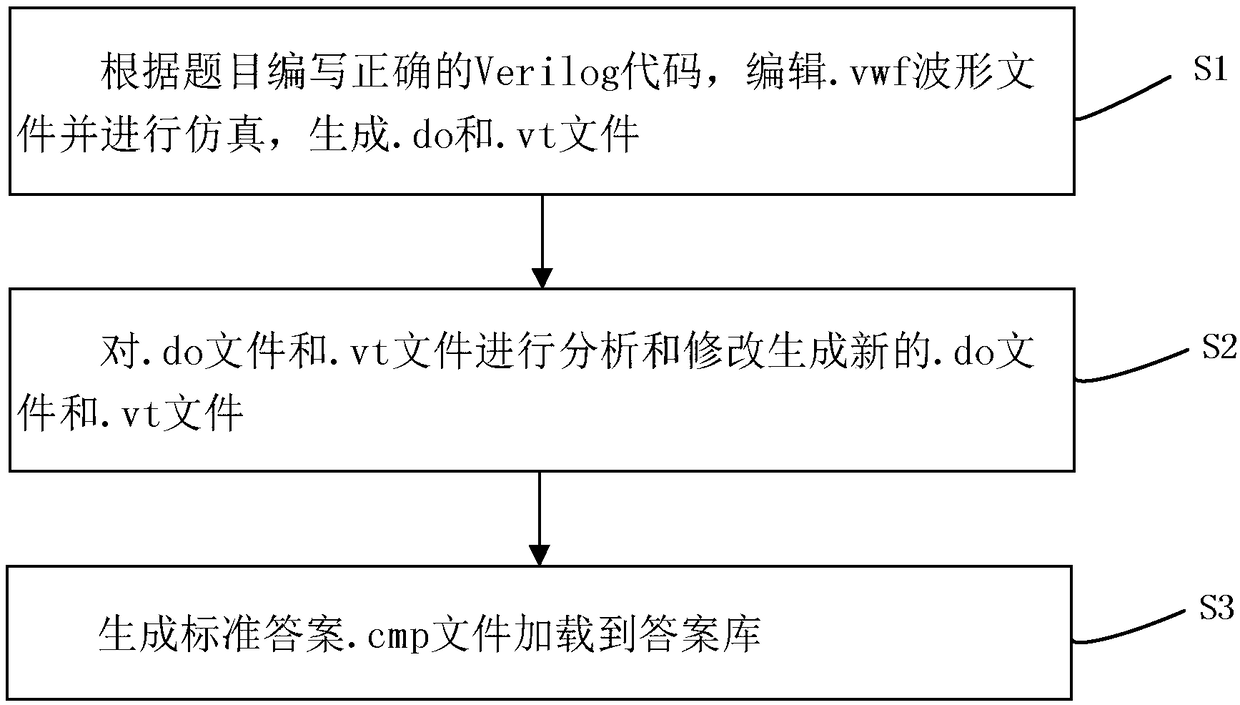
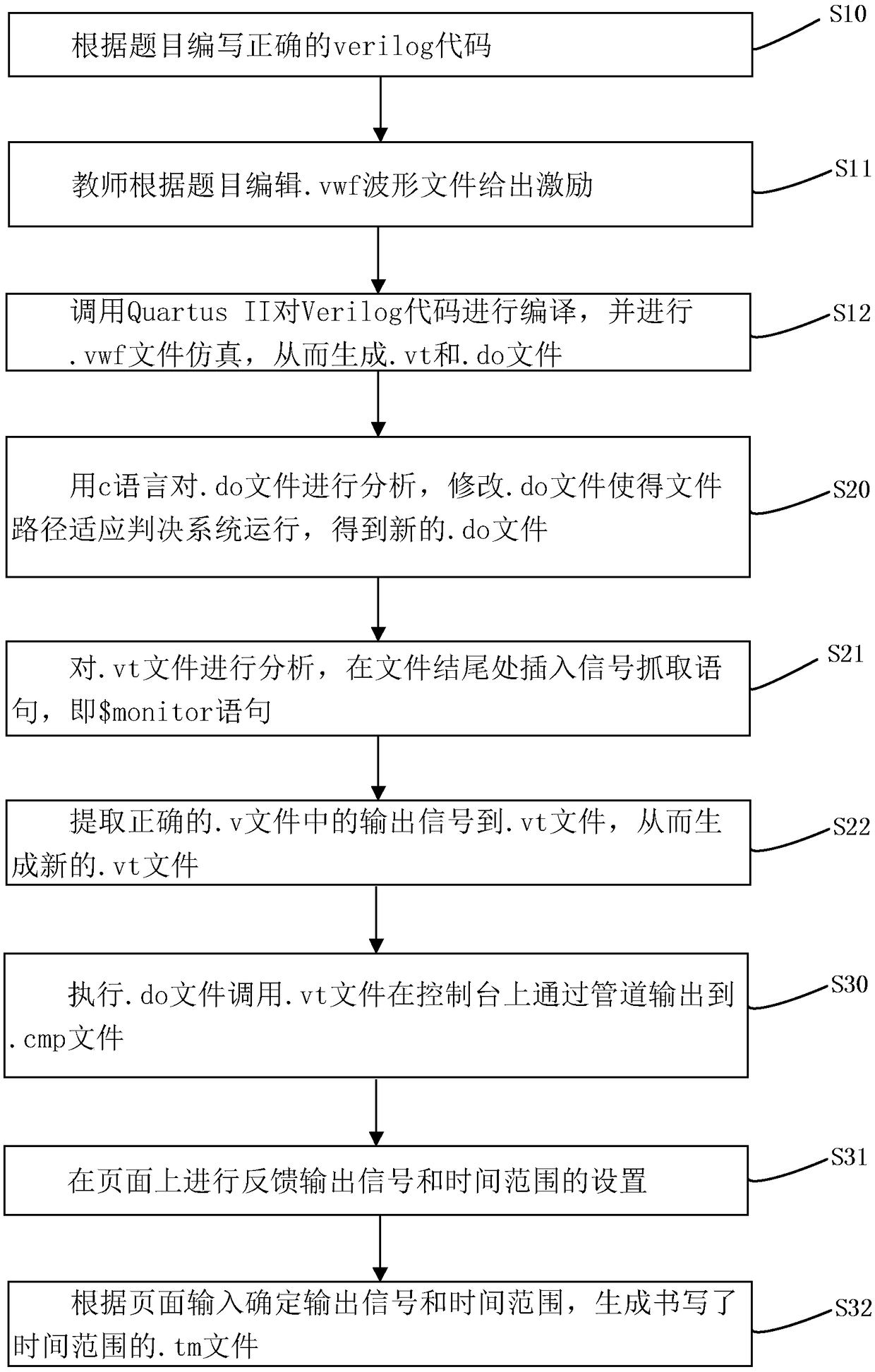
The invention discloses a standard answer generation method of an on-line Verilog code automatic judgment system. According to the title, correct Verilog code is compiled, a. Vwf waveform file is edited and simulated to generate. Do and. Vt files; . Do file and. Vt file are analyzed and modified to generate new. Do file and. Vt file; a standard answer.cmp file is generated to load into the answerlibrary; each file in the invention constructs the operation of the whole Verilog answer decision system, and ensures that the decision system can give a correct result.
Owner:HANGZHOU DIANZI UNIV
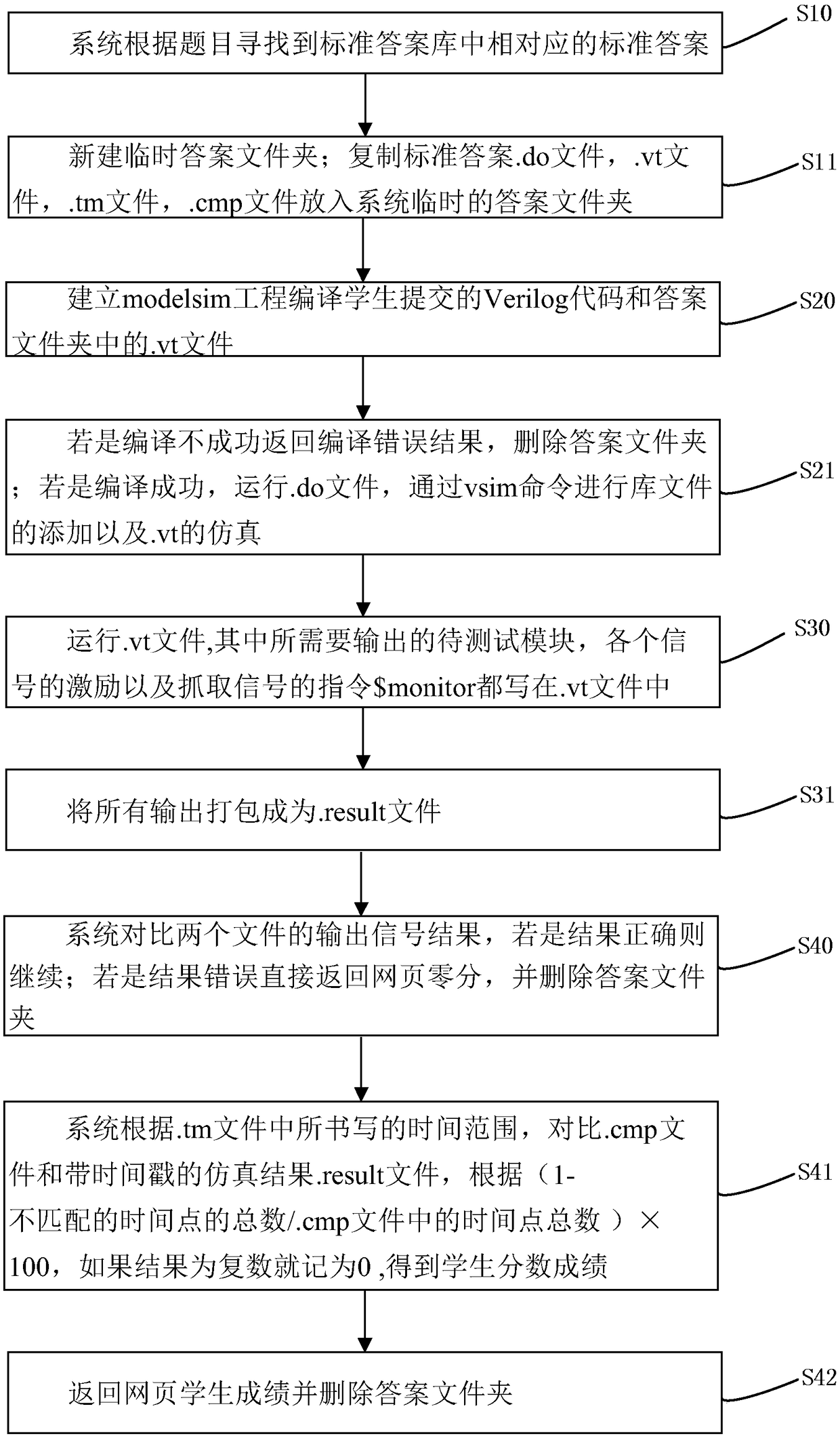
An automatic scoring method for an on-line Verilog code automatic judgment system
ActiveCN109190093ASimultaneous accessSimultaneous access satisfiesNatural language data processingFile/folder operationsTime rangeDecision system
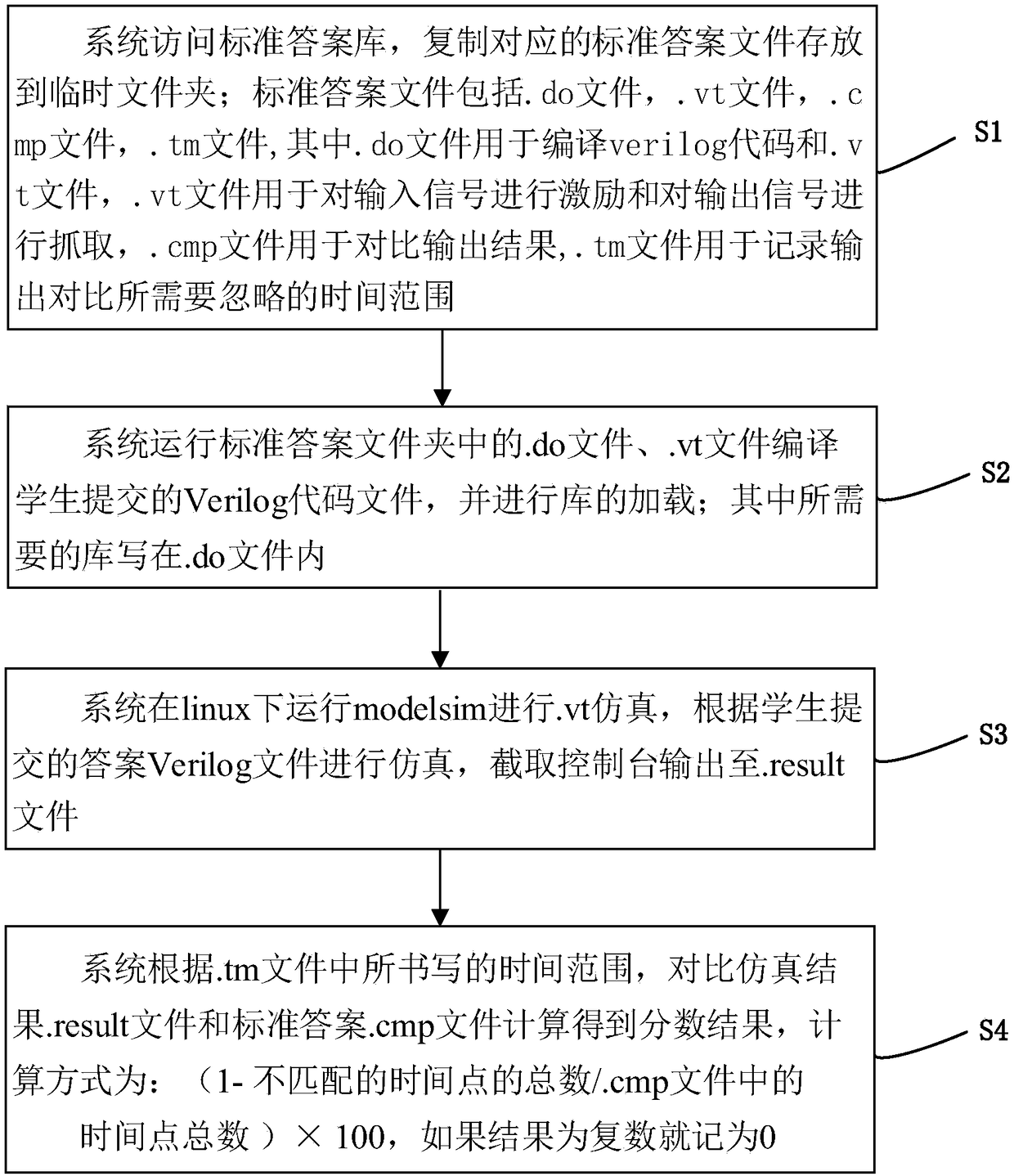
The invention discloses an automatic scoring method of an on-line Verilog code automatic judgment system. The system accesses a standard answer database and copies the corresponding standard answer file and stores it in a temporary folder. The system runs the. Do file in the standard answer folder, and the. Vt file compiles the Verilog code file submitted by the students, and loads the library. The system runs modelsim in Linux to simulate. Vt, performs simulatin according to Verilog file submitted by students, and intercepts the console to output to. Result file; according to the time range written in the. Tm file, the system compares the simulation results. Result file with the standard answer. Cmp file to get the score result The. Do file of the invention compiles the student answer. Vfile and the. Vt file in the answer folder by using the vsim instruction, and simulates according to the. Vt file. The modules to be tested, the excitation of each signal, and the instructions to grabthe signal are written in the. Vt file. Thus, the whole Verilog code decision system is constructed, and the cost of Verilog class decision is greatly reduced.
Owner:HANGZHOU DIANZI UNIV
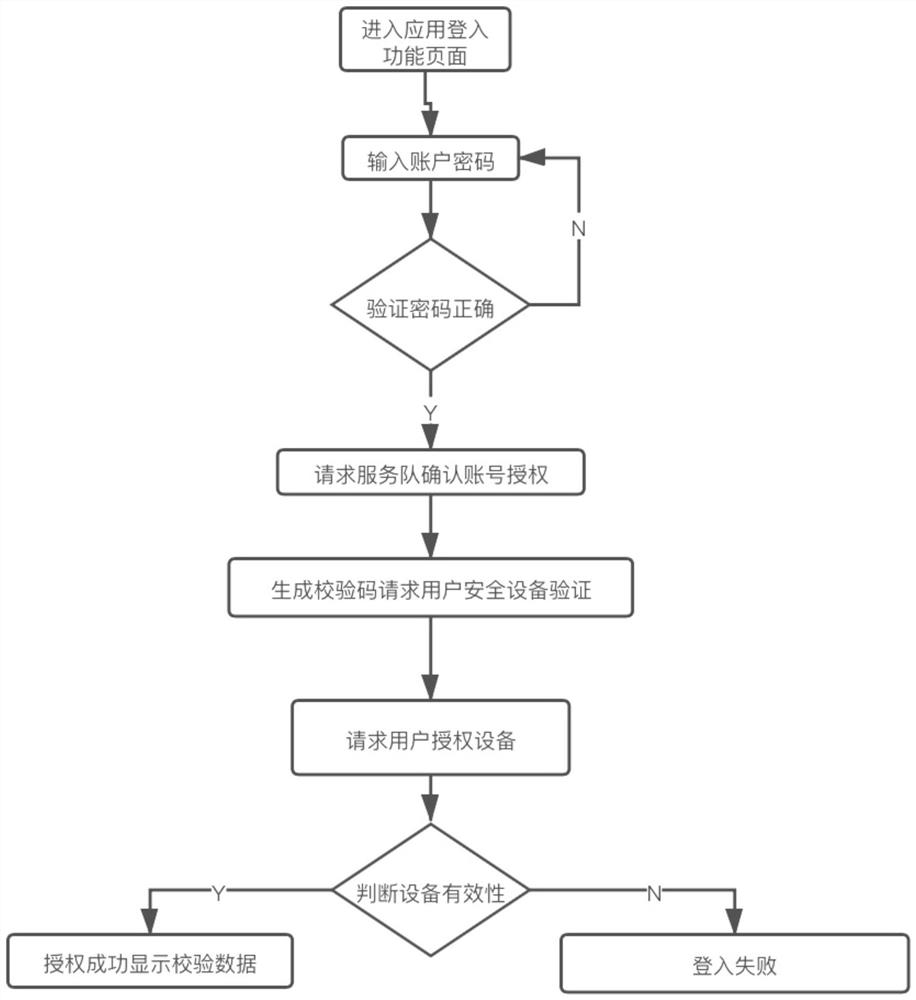
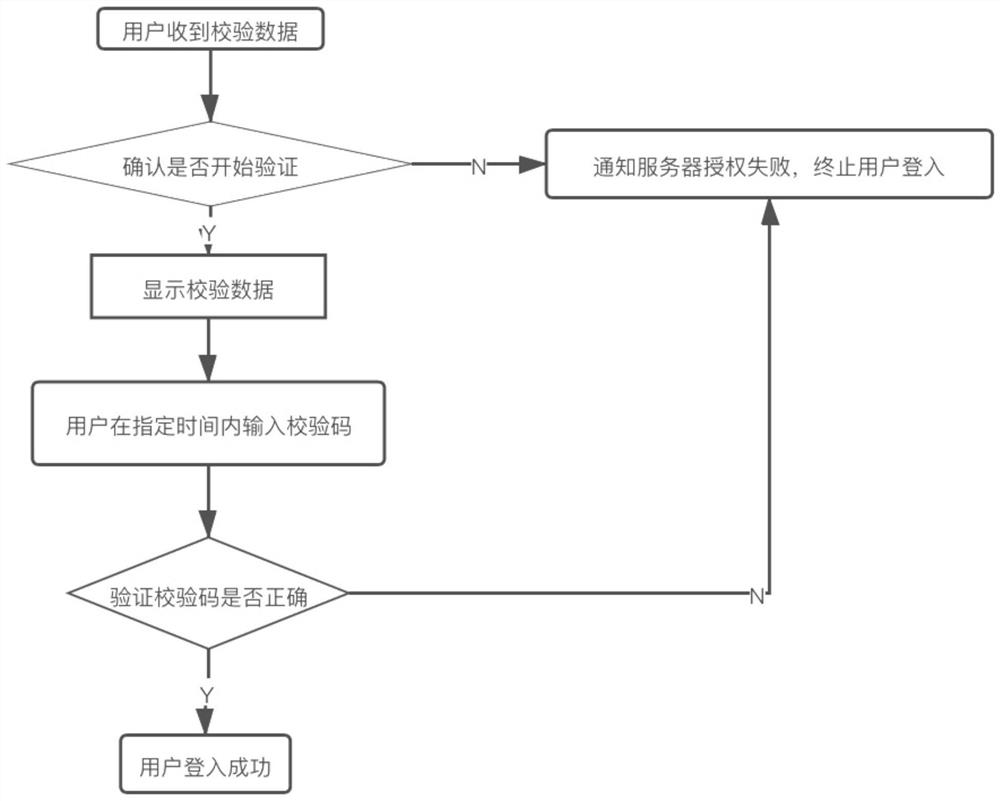
Dual verification method for trusted equipment access application
The invention provides a dual verification method for trusted equipment to access an application, which comprises the following steps that: when an existing account accesses a new unauthorized client mode, a verification server verifies a current client A by adopting the following modes: the verification server randomly generates a dynamic code plaintext, encrypts the dynamic code plaintext, a dynamic code ciphertext is obtained, and then the dynamic code ciphertext is sent to the authorized client; the authorization client carries out decryption operation on the received dynamic code ciphertext to obtain a dynamic code plaintext, and the dynamic code plaintext is displayed in a display area of the authorization client; and the verification server judges whether the dynamic code plaintext returned by the client A is received within a preset time. The double-verification method for the trusted equipment to access the application has the advantages that a double-verification mechanism of the password and the verification code of the user account is adopted, and the safety of the user account in using the application software is remarkably enhanced.
Owner:4399 NETWORK
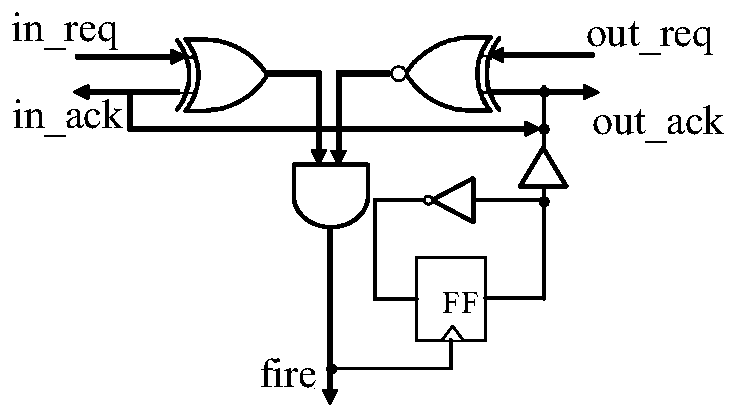
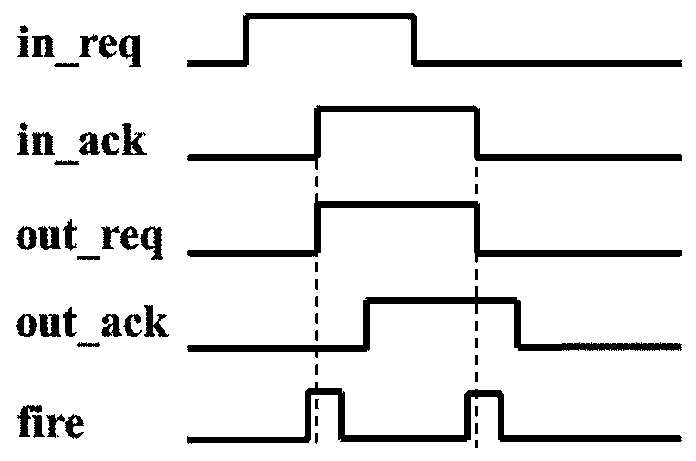
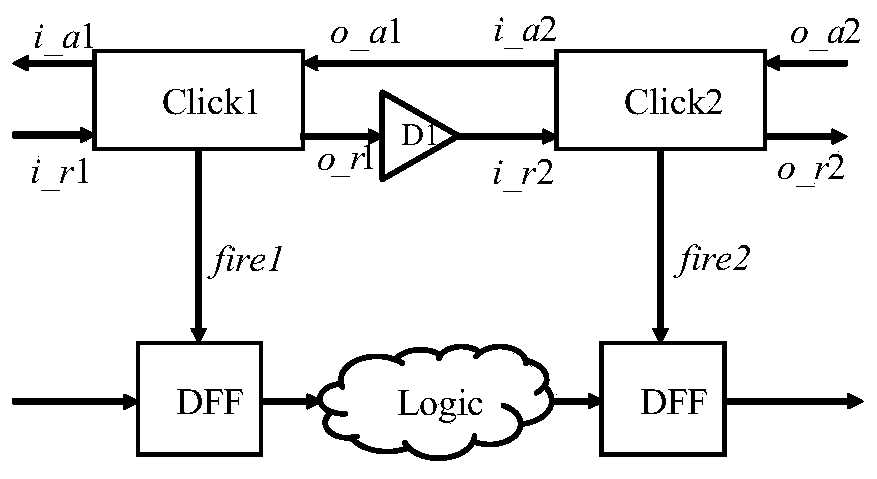
A method of converting a synchronization circuit into an asynchronous circuit
According to the invention, a synchronous assembly line circuit can be automatically converted into a Click unit-based bundled data asynchronous circuit. According to the method, firstly, by comparingthe difference between a synchronous assembly line and a Click unit-based binding data asynchronous circuit, a synchronous Verilog code is converted into a Verilog code of the Click unit-based binding data asynchronous circuit through a Tcl script; and then, the asynchronous circuit is integrated through a Synopsys Designn Compill (DC) tool. According to the invention, the synchronous pipeline circuit can be quickly converted into the Click-based bundled data asynchronous circuit, so that the design period of the asynchronous circuit is greatly shortened and the design difficulty of the asynchronous circuit is reduced.
Owner:TSINGHUA UNIV
Memory, verification code implementation method, device and equipment
InactiveCN111090849AReduce the chances of verificationImprove securityDigital data authenticationGraphicsTheoretical computer science
The invention discloses a memory, a verification code implementation method, a verification code implementation device and verification code implementation equipment. The verification code implementation method comprises the following steps: acquiring a verification picture comprising a preset graph; prompting a user to draw in the verification picture according to the track of the preset graph; generating a drawing result according to the drawing behavior of the user; judging whether the drawing result is matched with the track of the preset graph or not; and generating a verification resultaccording to the judgment result. According to the method and the device, the difficulty of obtaining the graph consistent with the preset graph by a malicious computer program in a traversal mode isgreat, the operand is very large, and the required time length is very long, so that the method and the device are difficult to realize in a verification process. Therefore, through the embodiment ofthe invention, the probability that the malicious computer program passes the verification can be effectively reduced, and the safety of identity verification is further improved.
Owner:WUHAN JIYI NETWORK TECH CO LTD
Software registration method and device, software registration code generation method and device
ActiveCN112685699AAccurately determineProgram/content distribution protectionCode generationVerification
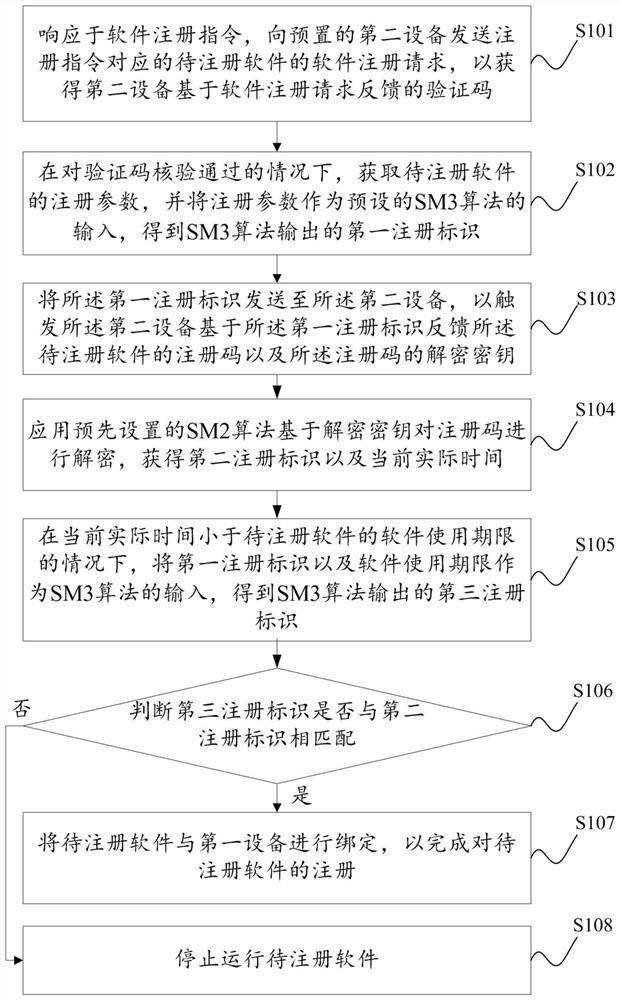
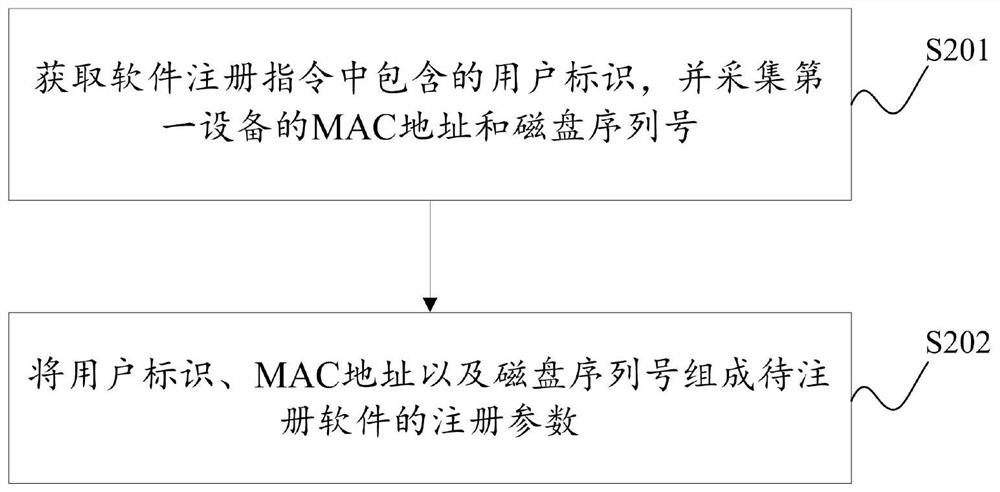
The invention provides a software registration method and a device, a software registration code generation method and a device. The software registration method is applied to a first device. The software registration method comprises the following steps: if verification of a verification code is passed, obtaining registration parameters of software to be registered, and processing the registration parameters by using an SM3 algorithm to obtain a first registration identifier; sending the first registration identifier to a second device to obtain a registration code and a decryption key; decrypting the registration code by using a decryption key through an SM2 algorithm to obtain a second registration identifier and current actual time; if the current actual time is less than the service life of the software, taking the first registration identifier and the service life of the software as inputs of an SM3 algorithm to obtain a third registration identifier; If the third registration identifier is matched with the second registration identifier, completing registration of the to-be-registered software. By applying the method provided by the invention, whether the to-be-registered software is overdue or not can be accurately determined in the process of verifying the registration code.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
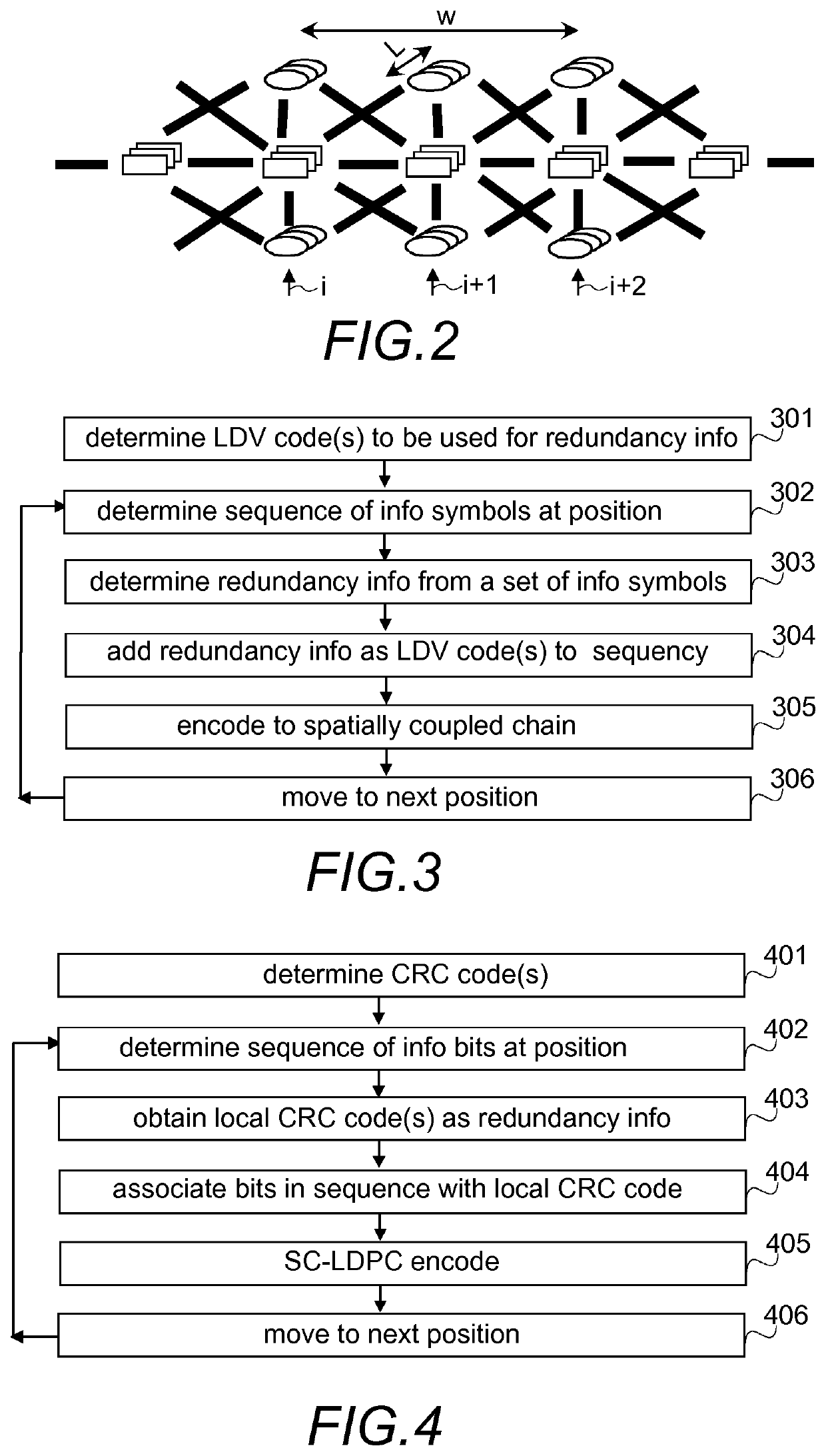
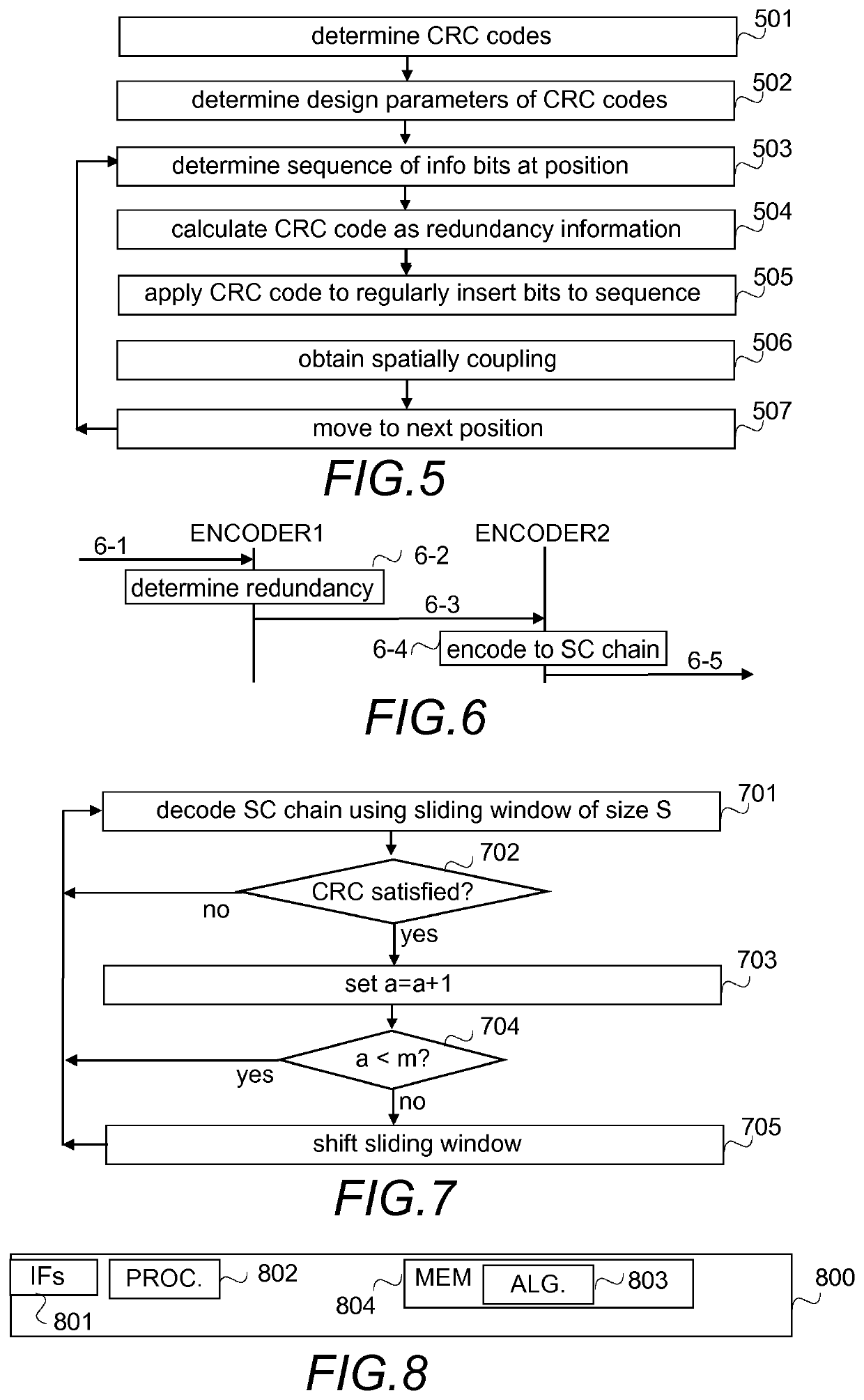
Coding and decoding of coupled chains
InactiveUS20210058094A1Error preventionError correction/detection using multiple parity bitsAlgorithmVerilog code
Redundancy information is added to information to be sent over a medium and sent as spatially coupled chain with the redundancy information as local decision verification codes. In the receiving end, when the local decision verification code has been satisfied a preset number of times, a sliding window is shifted.
Owner:NOKIA TECHNOLOGLES OY
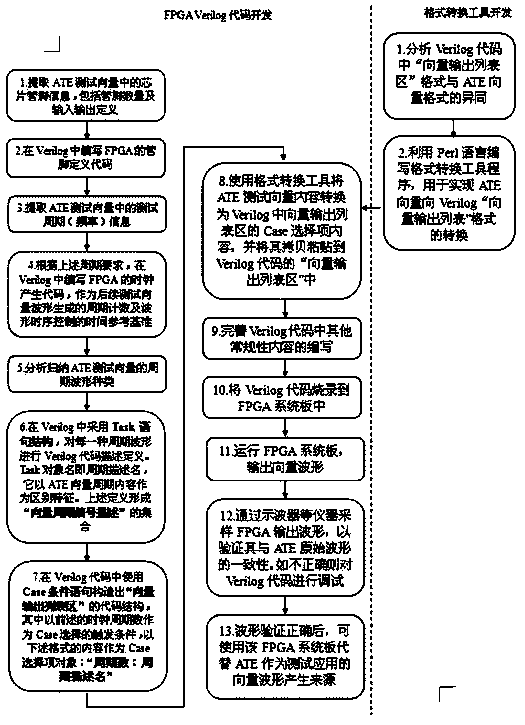
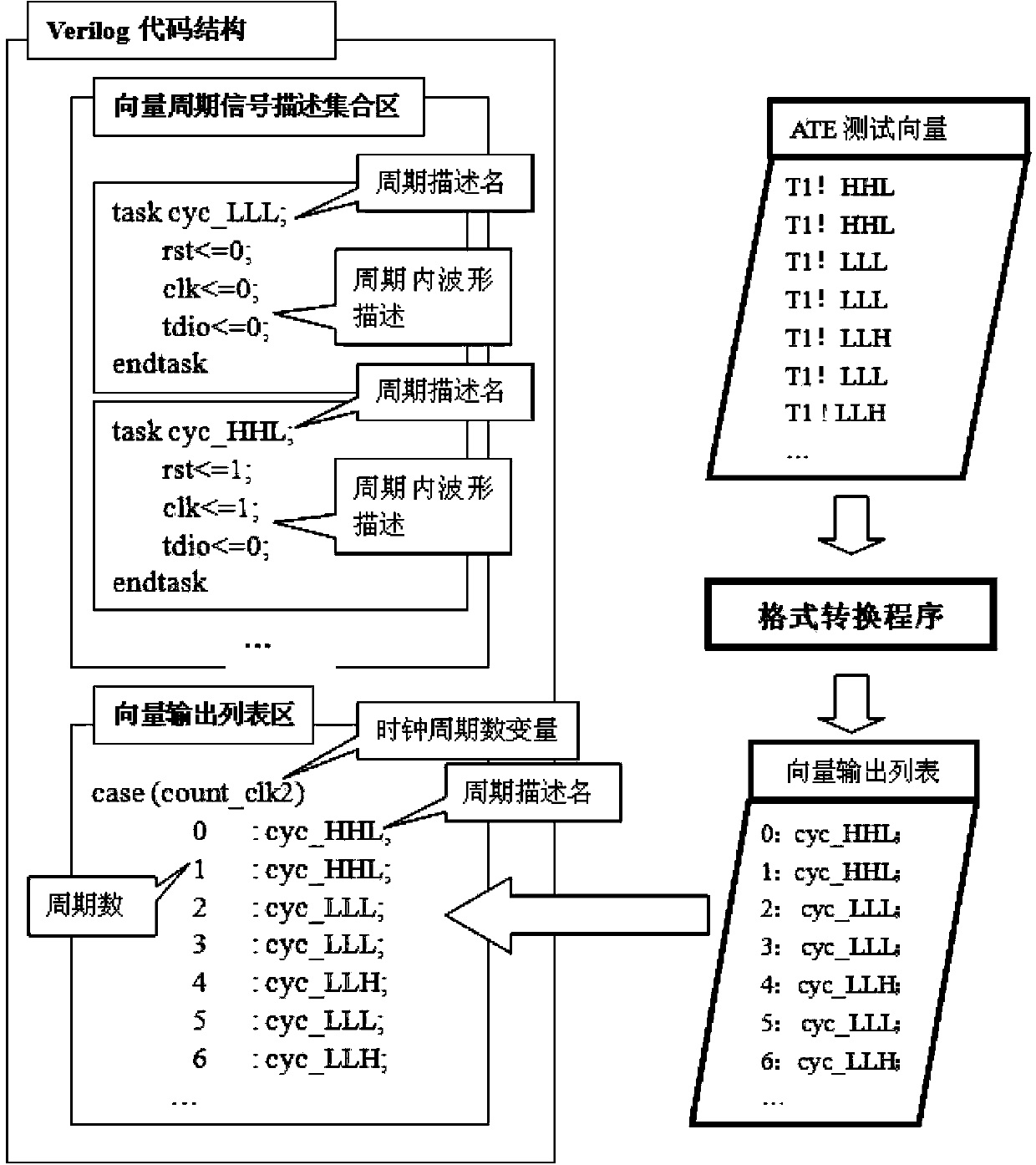
Verilog coding method achieving ATE test waveform by adoption of FPGA
InactiveCN103969574AEnsure reliabilityImprove development efficiencyElectrical testingVerilog codeFpga design
The invention discloses a Verilog coding method achieving ATE test waveform by the adoption of FPGA. Description of a vector period signal set is constructed through task statements, an ATE test period vector is analyzed, and a periodic type set is classified; specific description is conducted on signal behaviors corresponding to all types of periods in the period type set in a vector period signal description set area of Verilog codes, a vector period signal description set is constructed, and period signal waveform is adopted for all period signals in the vector period signal description set to serve as characteristic keywords to be used as an identification naming period description name; Case conditional statements are applied, the number of vector periods serves as the triggering condition of the Case statements, the cycle description name serves as a condition selection object, and the period description name is in linkage with a designated clock period number, so that a vector output list corresponding to ATE test vector description is constructed. By means of the Verilog coding method achieving ATE test waveform by the adoption of the FPGA, efficiency and flexibility of development of converting from the ATE test vector to an FPGA design, development difficulty can be reduced, and design efficiency can be improved.
Owner:SHANGHAI HUAHONG GRACE SEMICON MFG CORP
A fractional frequency divider
InactiveCN104184461BAvoid Quantization NoiseQuantization Noise ImprovementCounting chain pulse countersControl signalReusability
The invention provides a fractional frequency divider which comprises a controller, a phase interpolater, a buffer and an integer frequency divider. The controller generates control signals. The phase interpolater is controlled by the controller to achieve frequency division of a fractional part. The buffer is used for shaping signals output by the phase interrpolater, and the integer frequency divider is connected to the buffer and achieves frequency division of an integer part. The fractional frequency divider can be used in a digital phase-locked loop system and also can be used in a simulation phase-locked loop system, a digital phase-locked loop system difficult to deign based on a TDC is avoided, and the design of a full digital phase-locked loop system is greatly simplified. Quantizing noise generated by a delta-sigma modulator is avoided, the quantizing noise of the system is greatly improved, and the system performance is optimized. Meanwhile, extra circuit compensation is of no need in the design process of the phase interpolater, and therefore the design is simple. The logic of the controller is simple and can be achieved through a Verilog code, and the reusability is good.
Owner:SHANGHAI JIAOTONG UNIV
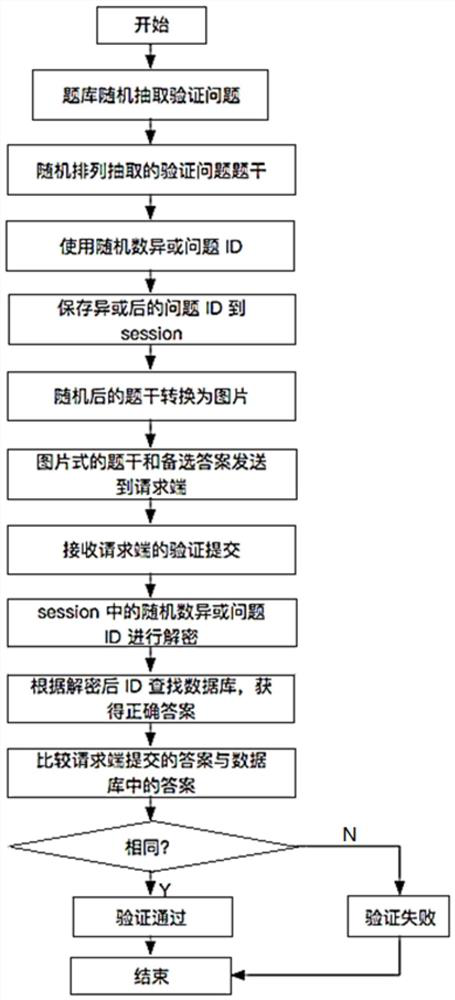
An anti-cracking verification code generation method
ActiveCN109981268BIncrease the difficulty of crackingTo achieve the purpose of anti-crackingKey distribution for secure communicationDigital data authenticationAlgorithmTheoretical computer science
The invention discloses an anti-cracking verification code generation method, which randomly rearranges the characters of the question stems of the verification code to generate a picture sequence P; and performs an XOR operation with a random number R and a serial number ID to obtain an encrypted question number EID; send the candidate answer group A, question number EID, and picture sequence P to the requesting end; then perform an XOR operation with the random number R and the question number EID returned by the requesting end to obtain the real question number ID, Find the exact answer a corresponding to the question number ID, compare the found exact answer a with the selected answer a1 returned by the requester, and obtain the verification result. The present invention greatly increases the difficulty of automatic identification of the computer, greatly increases the difficulty of cracking the verification code, effectively achieves the purpose of preventing cracking of the verification code, and increases the security of the web system.
Owner:成都知道创宇信息技术有限公司
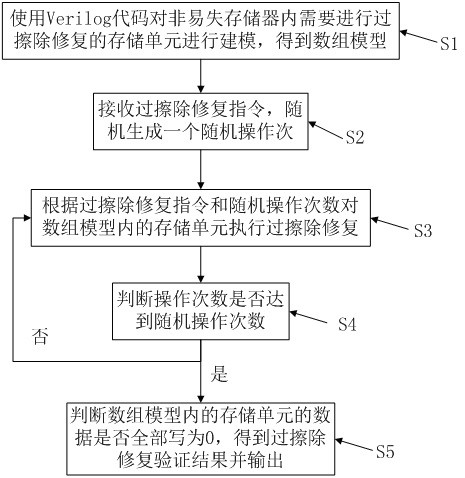
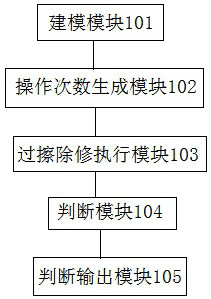
Method, device, storage medium and terminal for over-erasing verification based on real modeling
The invention discloses an over-erasure verification method, device, storage medium and terminal based on real modeling. By using Verilog codes to model the storage units that need to be over-erased and repaired in the non-volatile memory, after receiving When erasing the repair command, a random number is generated, and the memory unit in the array model is erased and repaired according to the random number. When it is detected that the number of operations reaches the random number, it is judged whether all the data in the memory unit in the array model is written as 0 and output the verification result of over-erasing modification; in the verification stage of the non-volatile memory control terminal, a highly close to the actual array model is established through Verilog code, and the non-volatile memory control terminal is simulated for over-erasing repair by verifying the array model The authenticity of the feature can more accurately verify the accuracy of the control terminal operation, and the automatic inspection of the erase repair operation results enhances the automation of the verification.
Owner:XTX TECH INC
A Gaussian Error Function Circuit Applied to Neural Network
ActiveCN106682732BPrecision advantageHigh precisionDigital data processing detailsPhysical realisationBinary multiplierEngineering
The invention discloses a Gaussian error function circuit applied to neural networks. The Gaussian error function circuit comprises three squarers, two multipliers, two multiplier-adders, two dot product digital signal processors, an adder, a derivation DSP, and an exponent DSP. The DSPs are Design Ware floating-point DSPs from Synopsys. The circuit has a simple structure, uses DSPs easy to obtain, and is easy to implement. Compared with the traditional Taylor expansion method implementation scheme, the circuit has very obvious advantages in terms of precision, area and speed, and especially, the precision is at least two orders of magnitude higher. Meanwhile, the circuit can be implemented using a Verilog code, and has nothing to do with any specific process, so that the circuit can be applied to different processes very easily and is of very strong portability. The Gaussian error function circuit can be applied to the design of various hardware circuits related to neural networks as a soft-core IP.
Owner:ZHEJIANG UNIV
A method for generating a two-dimensional code and its application
ActiveCN104331728BUniqueness guaranteedGuaranteed randomnessCo-operative working arrangementsCommerceCode generationAlgorithm
Owner:ANHUI GUOKE TESTING TECH CO LTD
Hollow verification code quick identification method
ActiveCN108038484BQuick identificationAccurate identificationNeural architecturesNeural learning methodsAlgorithmTheoretical computer science
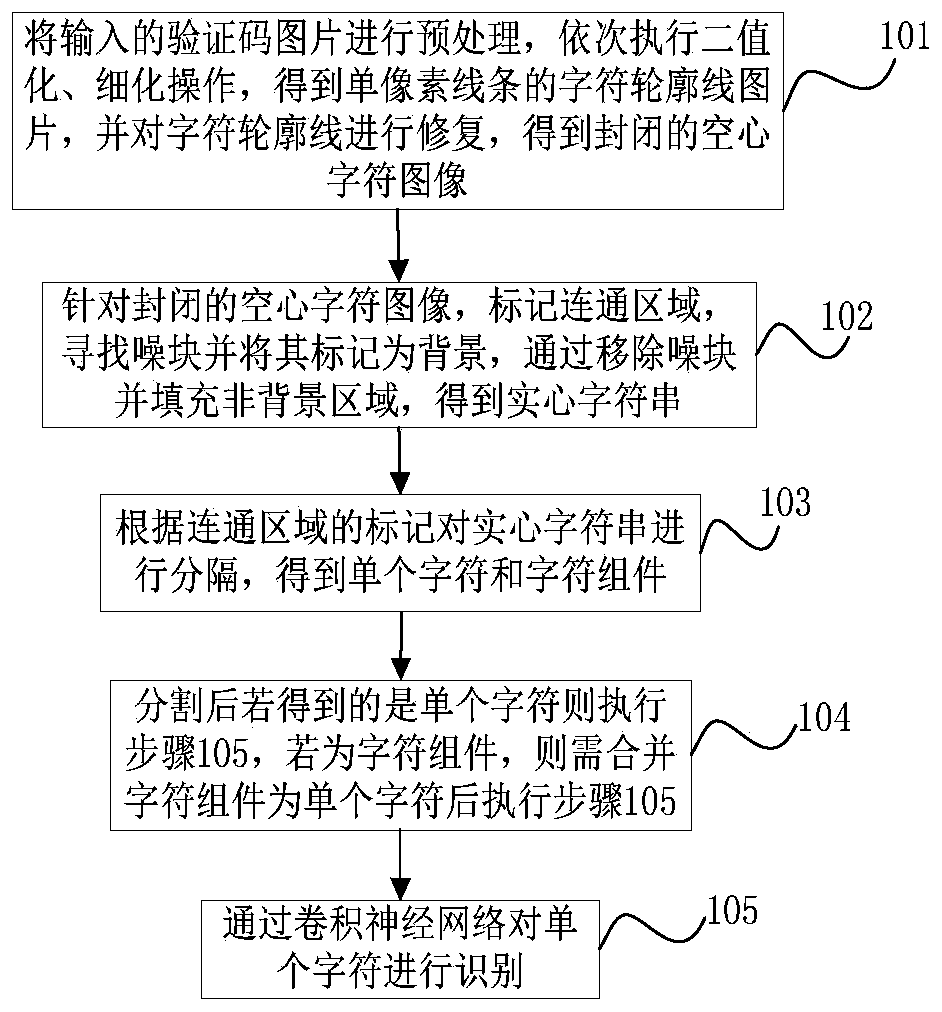
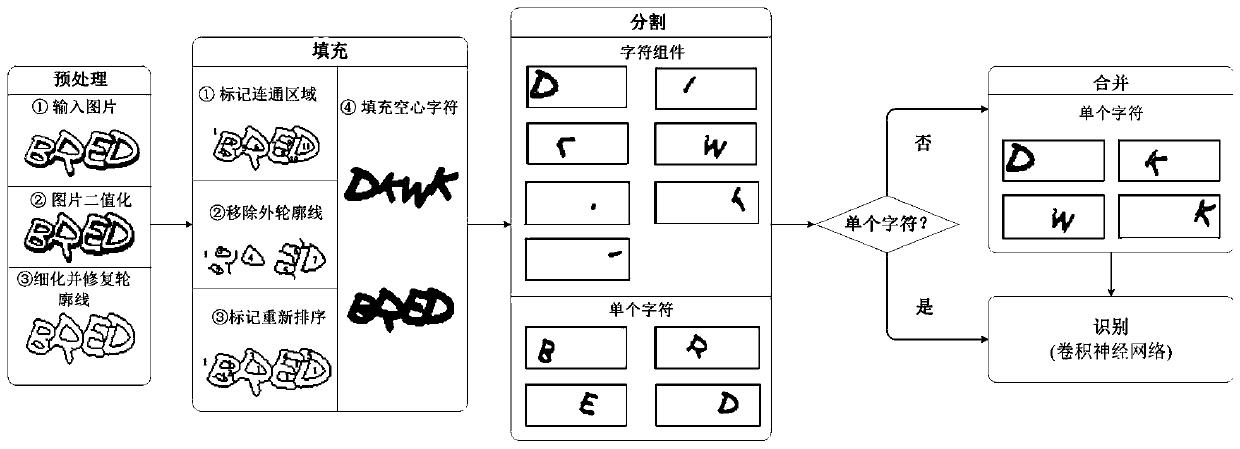
The present invention belongs to the technical field of verification code identification, and in particular relates to a method for quickly identifying a hollow verification code. Fill the character blocks to obtain solid characters; then, split to obtain individual characters and character components; then, analyze the structural characteristics and order associations of character components, and use the minimum neighbor algorithm to merge to obtain a single character without redundancy; finally, use volume The product neural network recognizes the individual characters obtained after segmentation and merging, and obtains the final cracking result. Compared with the existing recognition methods, the present invention not only keeps the original structure from being damaged, but also guarantees accurate repair of broken parts of character outlines, can reduce filling time, improve filling accuracy, and realize accurate acquisition and rapid identification of hollow verification codes , the recognition success rate is greatly improved, the applicability is strong, and it has good application value.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Information processing method and device for reducing error rate of digital circuit
ActiveCN112511273AReduce error rateAvoid influenceCorrect operation testingTransmitted data organisation to avoid errorsInformation processingVerilog code
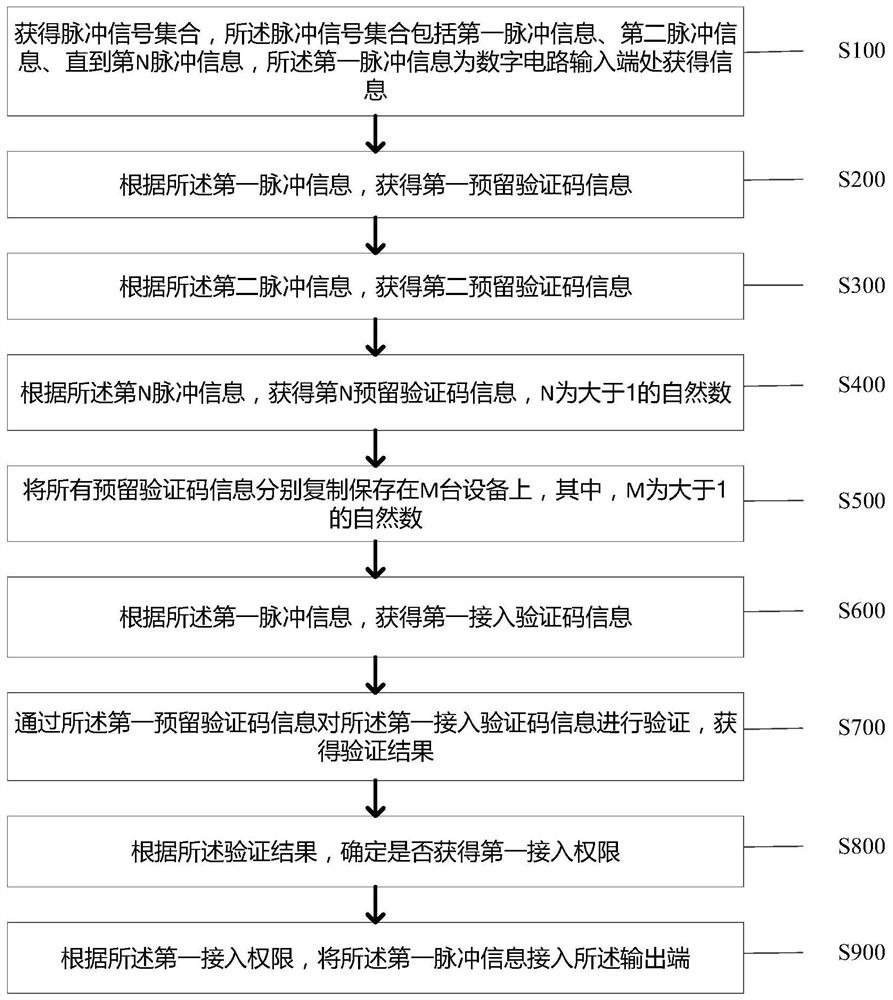
The invention discloses an information processing method and device for reducing the error rate of a digital circuit, and the method comprises the steps: obtaining a pulse signal set which comprises first, second pulse information to the Nth pulse information, and obtaining the corresponding reserved verification code information according to all pulse information; copying and storing all the reserved verification code information on M pieces of equipment respectively, and obtaining first access verification code information according to the first pulse information; verifying the first accessverification code information through the first reserved verification code to obtain a verification result; and according to the verification result, determining whether the first access permission isobtained, and accessing the first pulse information to the output end. The technical problems that in the prior art, a filter is used for filtering processing, but interference factors are diversified, the filtering effect is limited, the reliability of signal transmission cannot still be guaranteed, and errors exist are solved. The technical effects of encrypting the signal in the digital circuit by using the blockchain technology, ensuring the stability of the signal transmission process and reducing the circuit error rate are achieved.
Owner:江苏博沃汽车电子系统有限公司
Verification code generation method and device
ActiveCN111460422AFix security issuesDoes not affect legibilityDigital data authenticationEditing/combining figures or textCode generationSoftware engineering
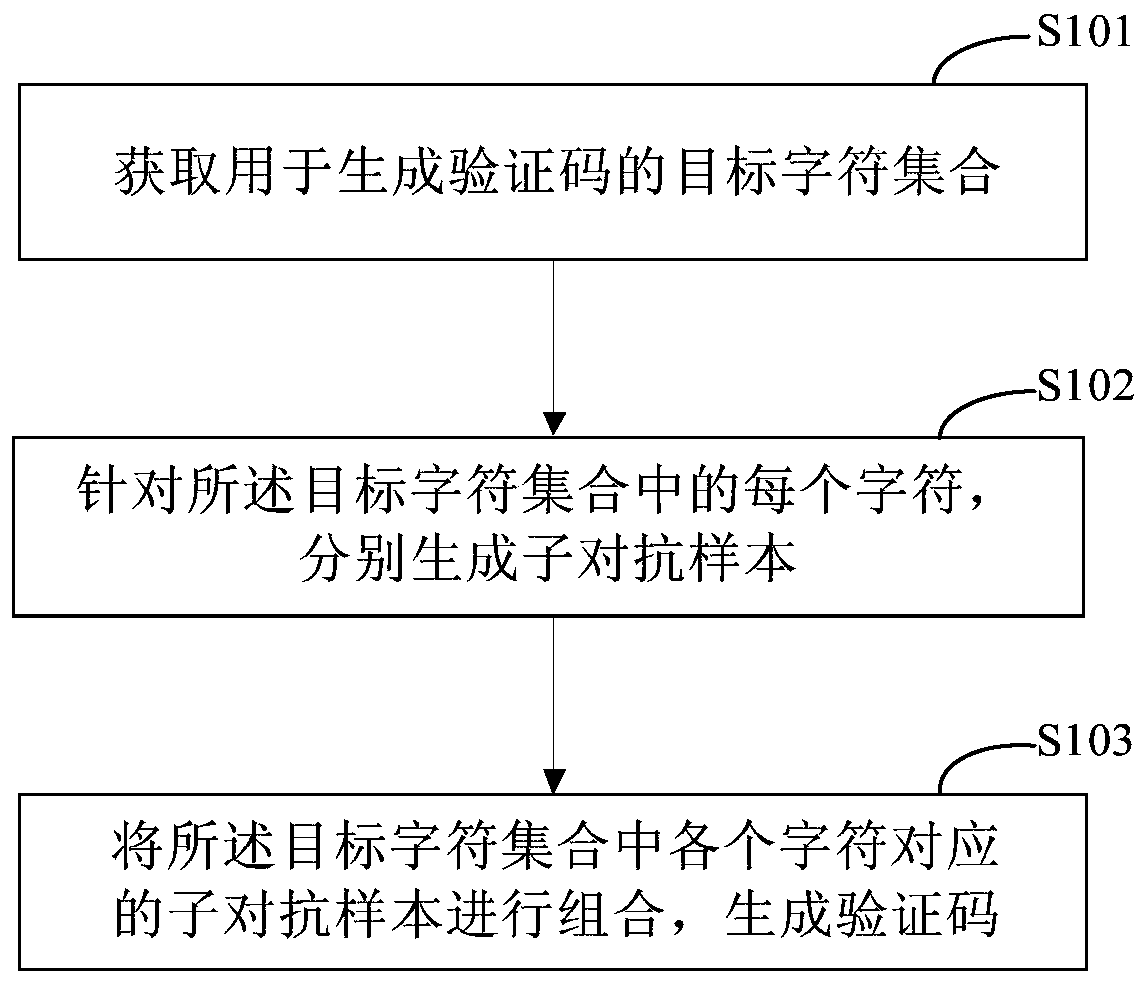
The invention discloses a verification code generation method and device, and relates to the technical field of computers. A specific embodiment of the method comprises: obtaining a target character set used for generating a verification code; for each character in the target character set, generating a sub-adversarial sample; and combining the sub-adversarial samples corresponding to the characters in the target character set to generate a verification code. According to the embodiment, the security problem existing in the prior art due to the adoption of universal adversarial samples is solved, so that the technical effects of not influencing the readability of the user and improving the security of the verification code can be achieved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
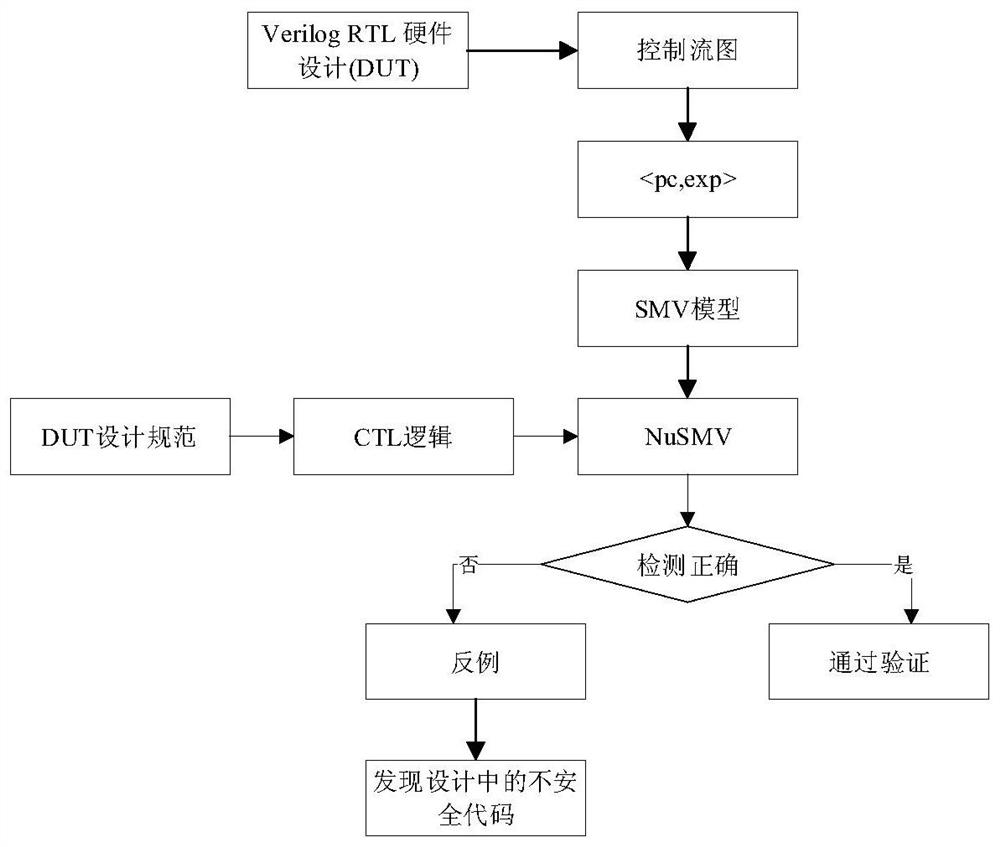
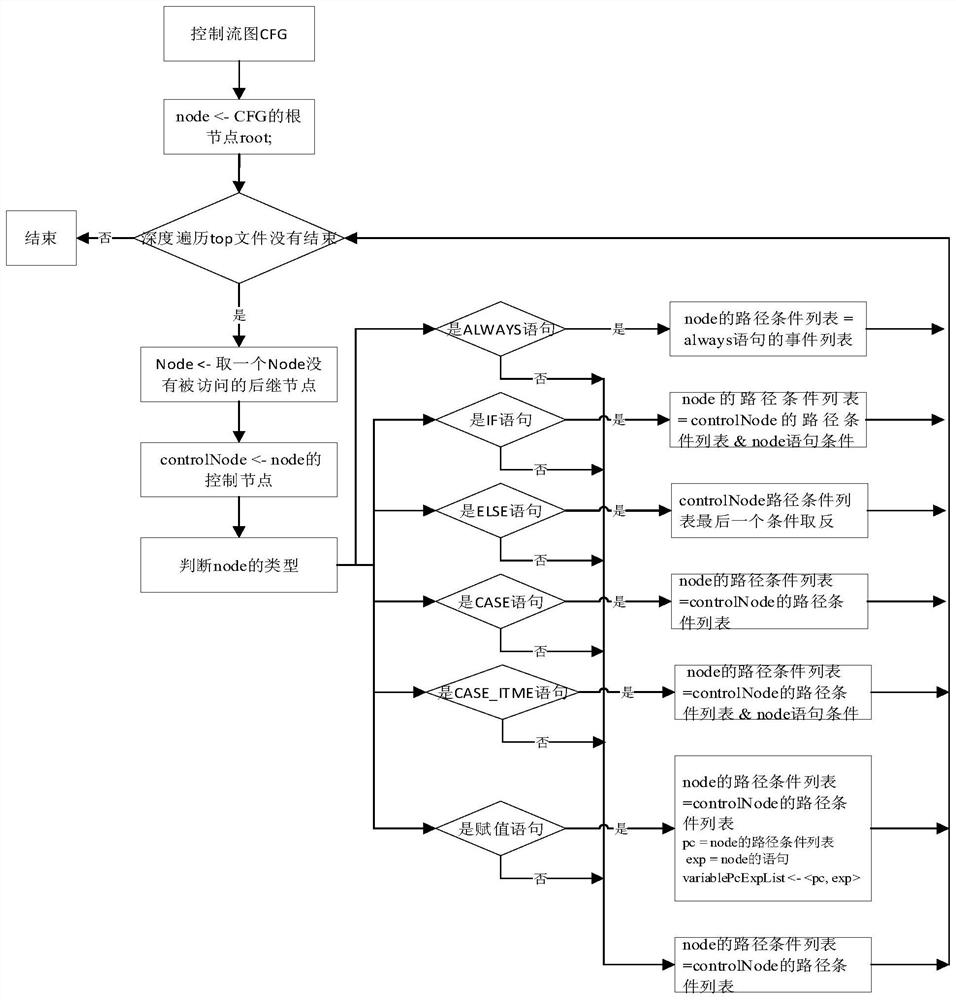
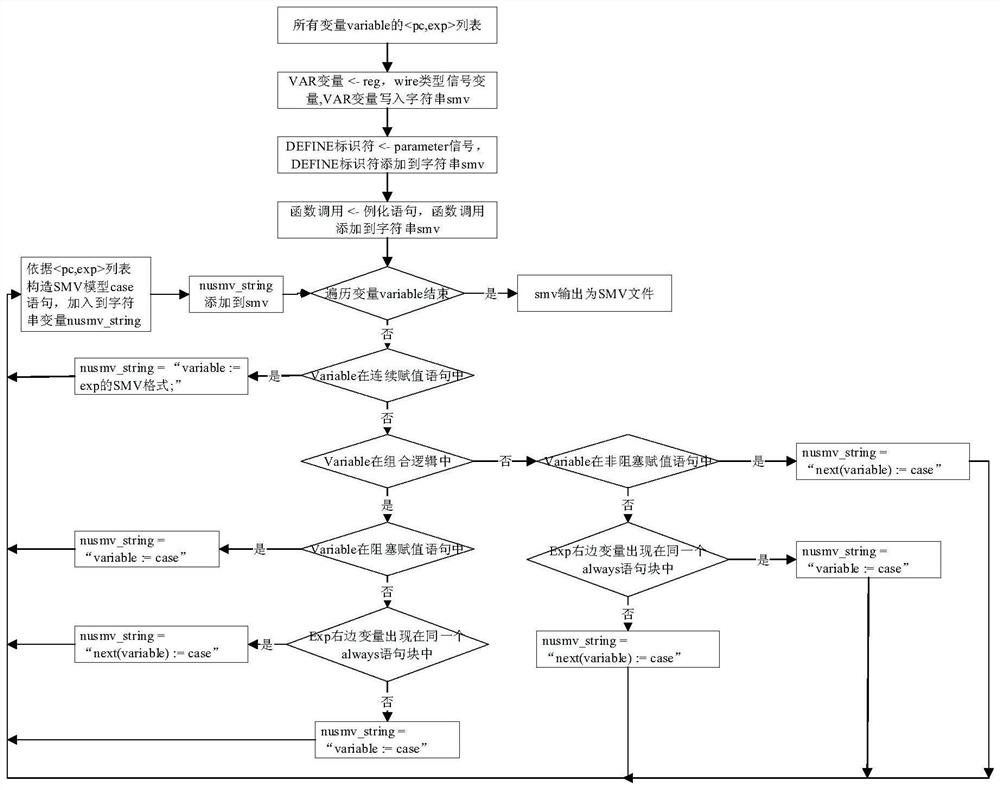
SMV model construction method for register transfer level verilog code
Owner:NORTHWESTERN POLYTECHNICAL UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com