QR code generation and verification method
A two-dimensional code and data verification technology, applied to record carriers, instruments, computer parts, etc. used in machines, can solve the problems of easy copying and dissemination of two-dimensional code images, poor security, etc. The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
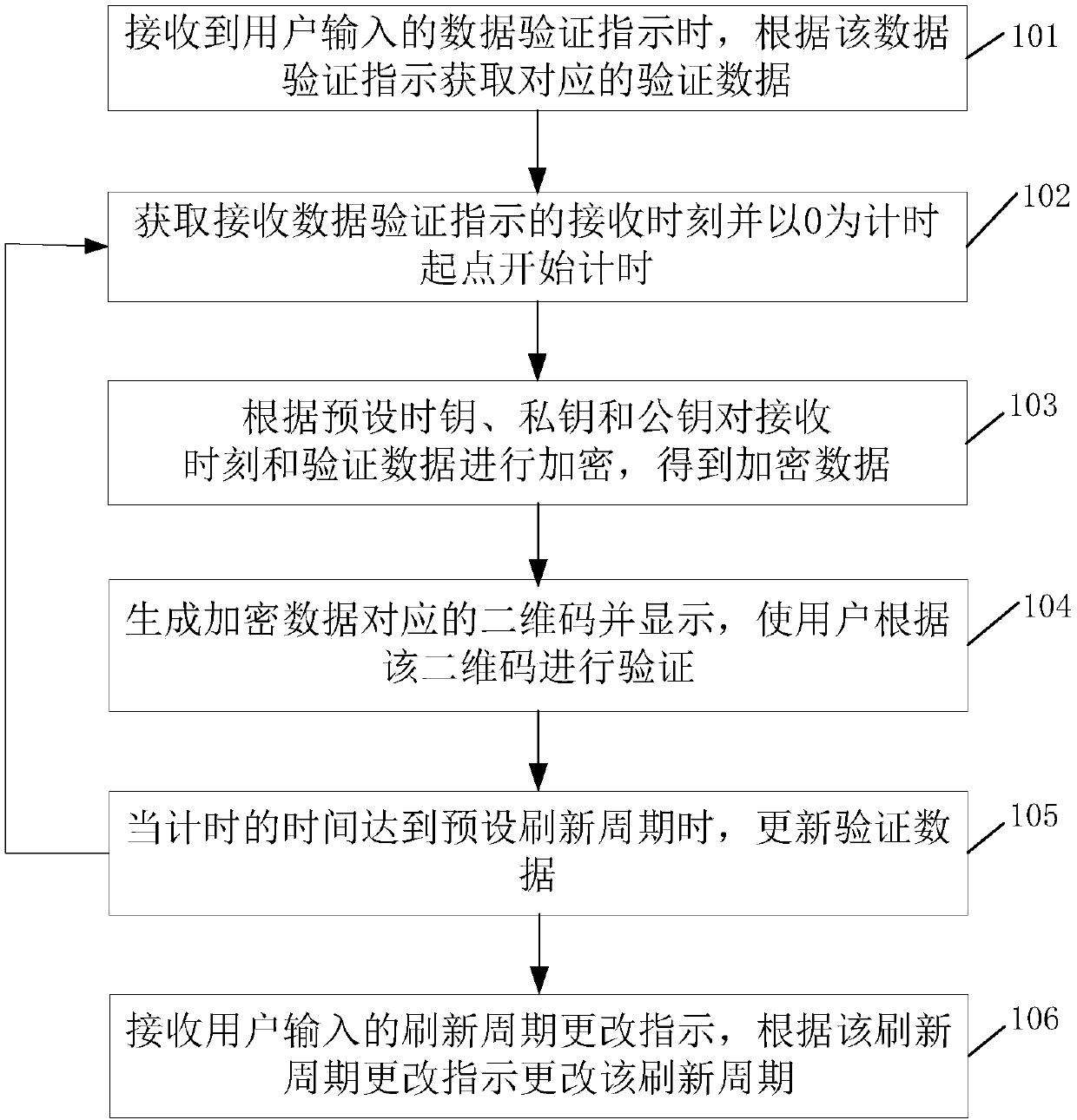
[0018] Such as figure 1 As shown, this embodiment provides a method for generating a two-dimensional code, including:
[0019] Step 101, when a data verification instruction input by a user is received, corresponding verification data is acquired according to the data verification instruction.
[0020] In this embodiment, the data verification instruction input by the user needs to indicate the specific type of data verification, such as indicating payment verification, electronic ticket verification, door lock verification, etc.; taking the electronic ticket verification of the scenic spot as an example, the data verification The instruction may also indicate the specific content of the data verification, such as the name of the scenic spot, the type of ticket for the scenic spot, etc., and the content mark corresponding to the specific content.
[0021] In this embodiment, the process of obtaining corresponding verification data through step 101 includes: obtaining specific...
Embodiment 2
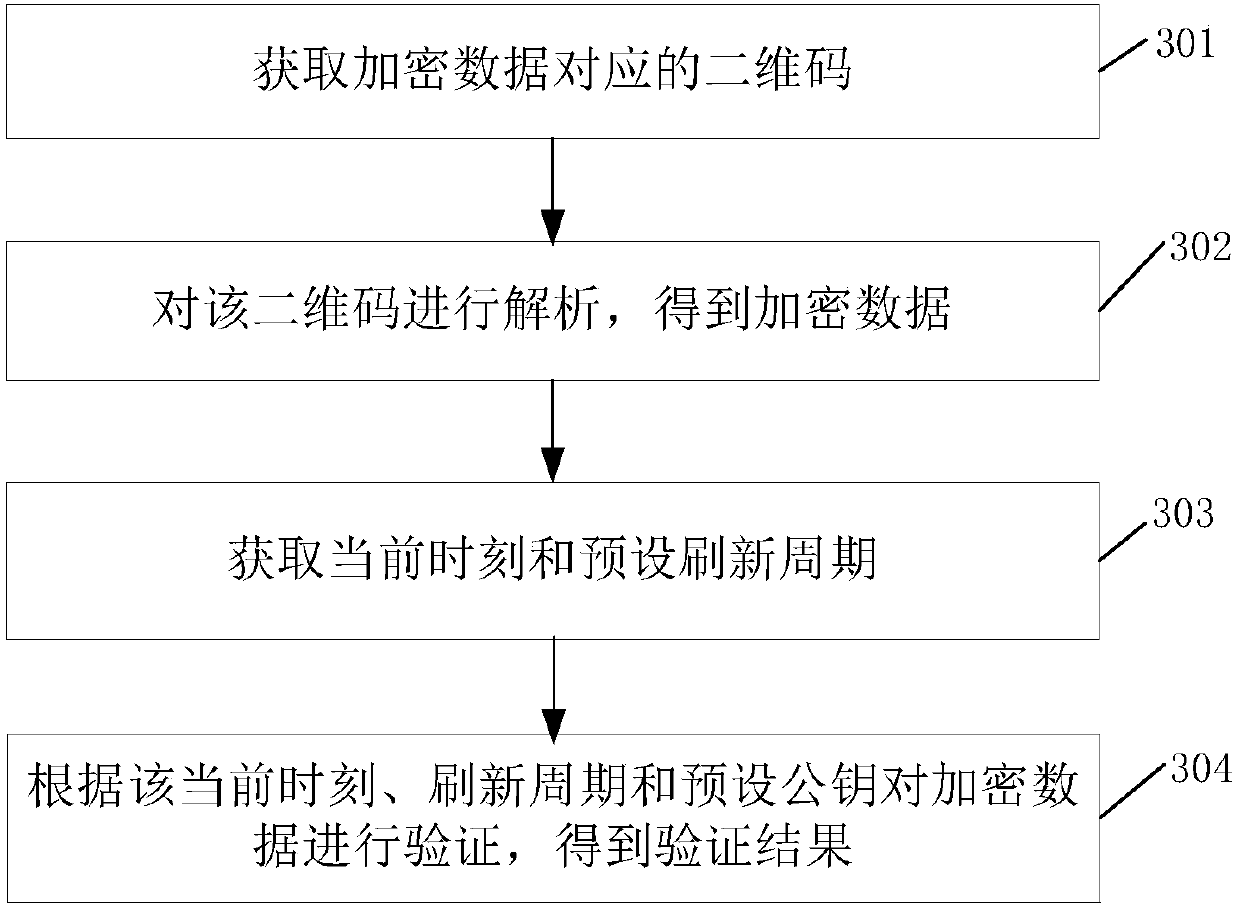
[0035] Such as image 3 As shown, this embodiment provides a two-dimensional code verification method, including:
[0036] Step 301, acquiring a two-dimensional code corresponding to encrypted data.
[0037] In this embodiment, the encrypted data in step 301 is obtained by encrypting the data to be verified with the preset time key and private key; the specific process of generating the two-dimensional code is similar to the process provided in Embodiment 1 of the present invention, and will not be repeated here Let me repeat them one by one. After the QR code is generated, the QR code can be obtained by scanning or taking a photo, which is not limited here.
[0038] Step 302, analyzing the two-dimensional code to obtain encrypted data.
[0039] Step 303, obtaining the current time and a preset refresh period.
[0040]Step 304: Verify the encrypted data according to the current time, the refresh period and the preset public key, and obtain a verification result.
[0041] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com