Webpage loophole detecting method and device
A vulnerability detection and web page technology, applied in the computer field, can solve problems such as incomplete detection, and achieve the effect of solving incomplete detection, ensuring flexibility, and avoiding individual omissions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
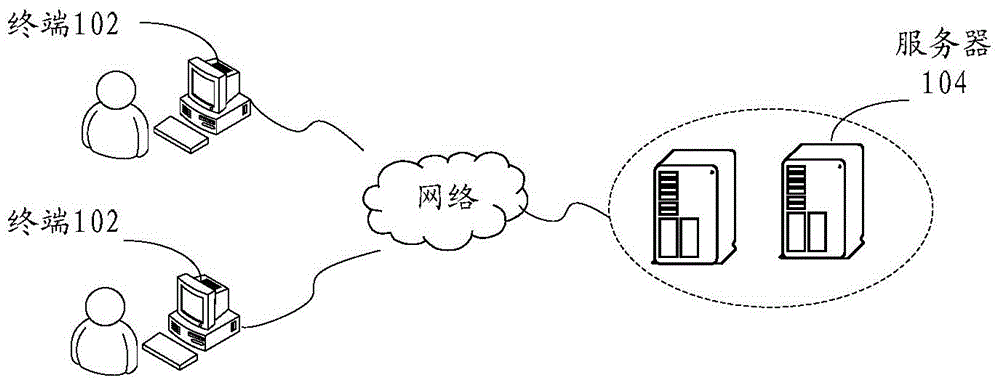
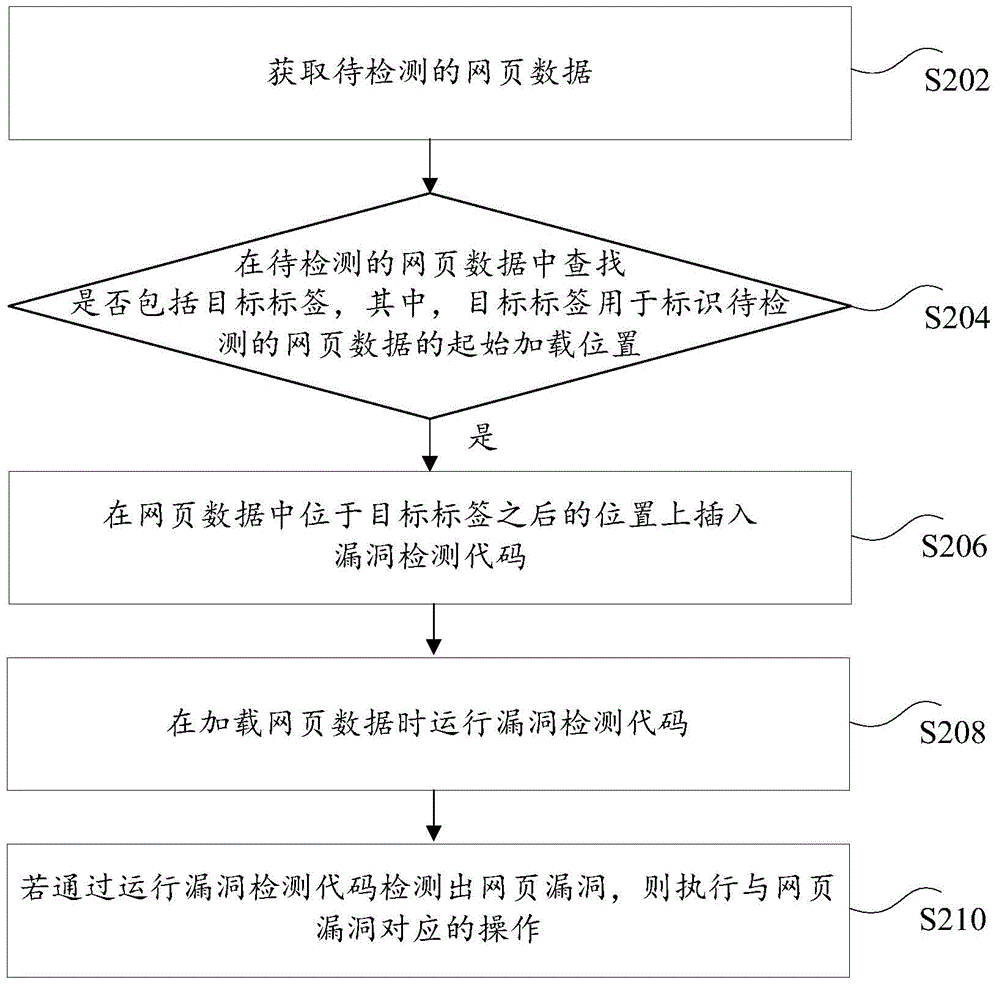
[0023] According to an embodiment of the present invention, an embodiment of a method for detecting a webpage vulnerability is provided, wherein the above method for detecting a webpage vulnerability can be applied to, but not limited to, such as figure 1 In the network environment shown, the above network environment includes a terminal 102 and a server 104 . Optionally, in this embodiment, the terminal 102 may include but not limited to at least one of the following: a mobile phone, a tablet computer, a notebook computer, and a PC. Optionally, in this embodiment, the foregoing network may include but not limited to at least one of the following: a wide area network, a metropolitan area network, and a local area network. For example, a predetermined Uniform Resource Locator URL (Uniform Resource Locator) address is input into the browser on the terminal 102, corresponding webpage data is obtained from the corresponding server 104 through the network, and vulnerability detecti...
Embodiment 2
[0073] According to an embodiment of the present invention, an embodiment of a webpage vulnerability detection device is provided, wherein the above-mentioned webpage vulnerability detection device can be applied, but not limited to, such asfigure 1 In the network environment shown, the above network environment includes a terminal 102 and a server 104 . Optionally, in this embodiment, the terminal 102 may include but not limited to at least one of the following: a mobile phone, a tablet computer, a notebook computer, and a PC. Optionally, in this embodiment, the foregoing network may include but not limited to at least one of the following: a wide area network, a metropolitan area network, and a local area network. For example, a predetermined Uniform Resource Locator URL (Uniform Resource Locator) address is input into the browser on the terminal 102, corresponding webpage data is obtained from the corresponding server 104 through the network, and vulnerability detection is p...
Embodiment 3
[0119] According to an embodiment of the present invention, an embodiment of a terminal for implementing the above webpage vulnerability detection method is provided, wherein the above terminal can be applied to, but not limited to, such as figure 1 In the network environment shown, the above network environment includes a terminal 102 and a server 104 . Optionally, in this embodiment, the terminal 102 may include but not limited to at least one of the following: a mobile phone, a tablet computer, a notebook computer, and a PC. Optionally, in this embodiment, the foregoing network may include but not limited to at least one of the following: a wide area network, a metropolitan area network, and a local area network. For example, a predetermined Uniform Resource Locator URL (Uniform Resource Locator) address is input into the browser on the terminal 102, corresponding webpage data is obtained from the corresponding server 104 through the network, and vulnerability detection is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com