A Method for Quickly and Automatically Identifying Encrypted Network Behavior
An automatic identification and network technology, applied in the field of network security, can solve problems such as high computational overhead, inability to meet online real-time identification, and difficulty in matching encryption application patterns, and achieve the effect of increasing the workload of research and development.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
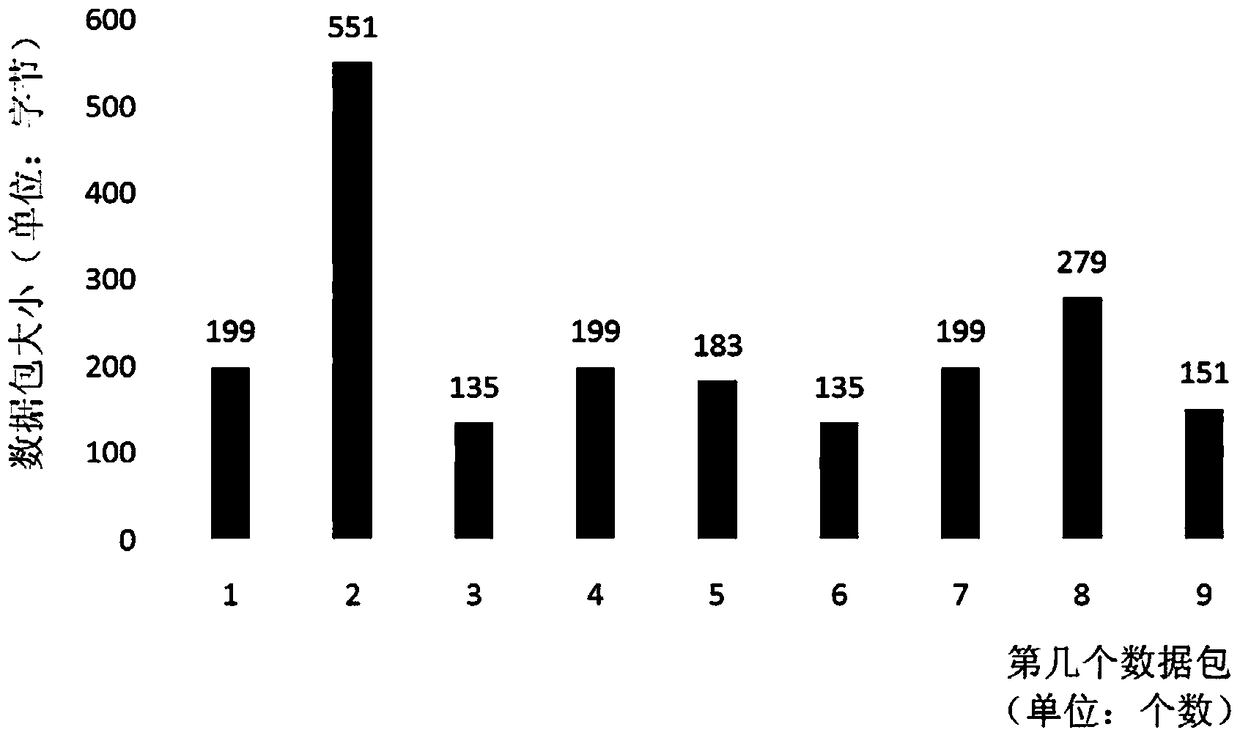
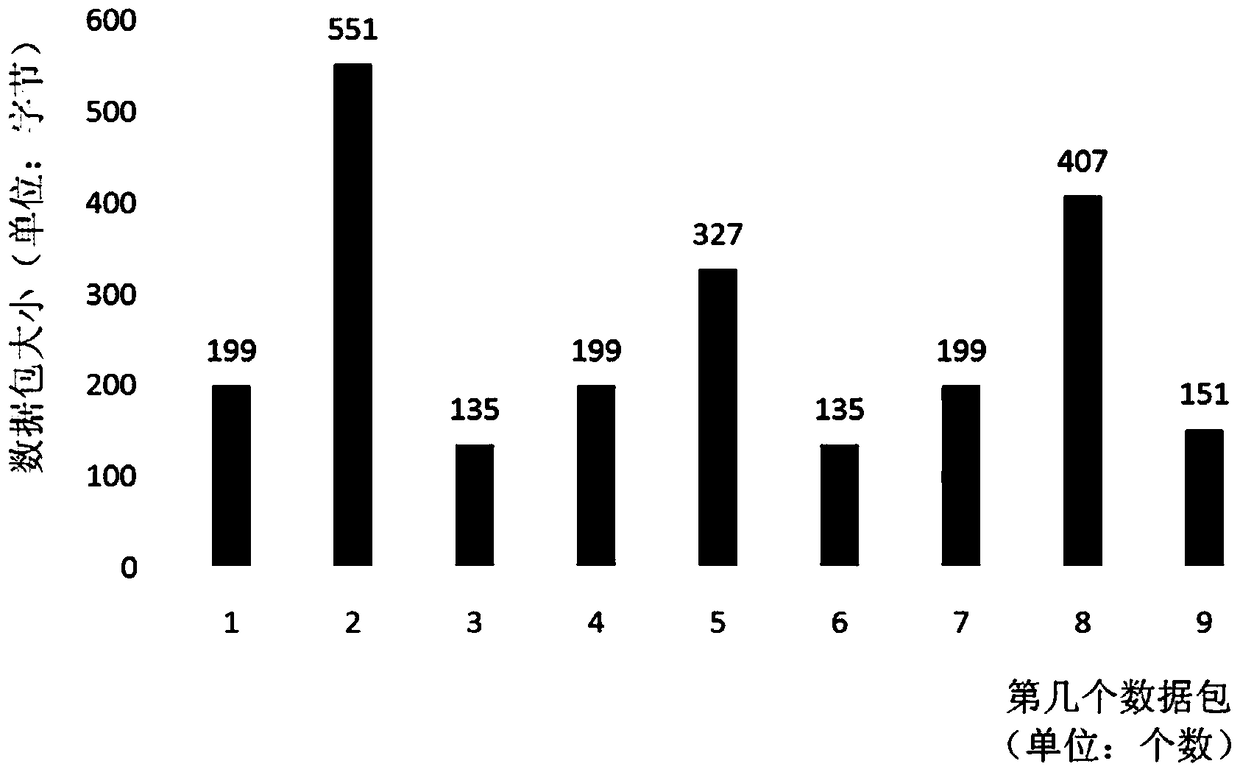
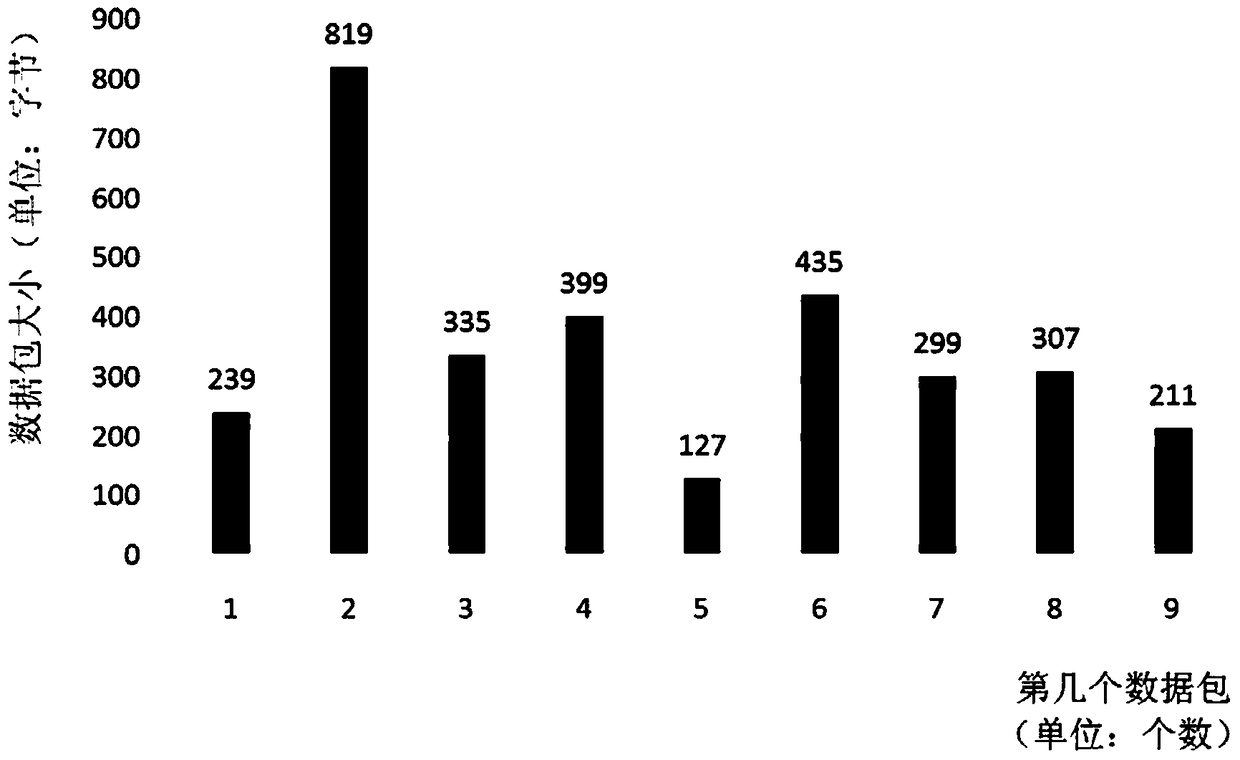
[0027] Aiming at the problem that it is difficult to identify massive encrypted network behaviors, the present invention proposes a method for quickly and automatically identifying encrypted network behaviors. This method first builds a specific encrypted network behavior model library, then collects network interaction data in real time, and calculates the correlation coefficient between the real-time collected network interaction data and the model library, and performs automatic classification and identification based on the calculated correlation coefficient combined with the preset threshold.
[0028] The present invention will be specifically introduced below in conjunction with the accompanying drawings and specific embodiments.
[0029] In this embodiment, the Android version of Twitter is used as the research object.
[0030] Twitter posting involves text messages and uploading pictures. When sending text messages, the domain name can be obtained from the interaction ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com