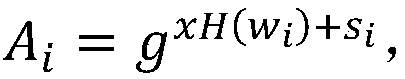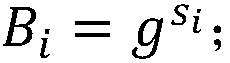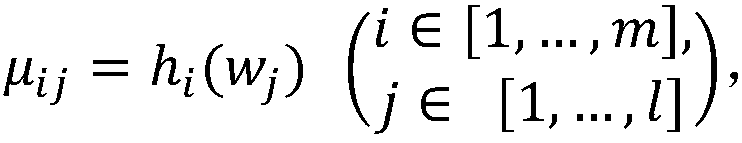Keyword Searchable Encryption Method Based on Bloom Filter with Storage Structure
A storage structure and encryption method technology, applied in the field of information security, can solve the problem of low efficiency of ciphertext retrieval
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0115] Assume that the user wants to store a document D containing 4 keywords: Xi’an, Hangzhou, Beijing, and Shanghai in the database, and then the user will retrieve documents containing 2 keywords: Xi’an and Hangzhou, and set the Bloom filter The size of the array M is n=12, the number of hash functions is m=3,
[0116] First, through step 1 system parameter initialization and step 2 user key generation,
[0117] (1) User upload document stage:
[0118] Use 3 different hash functions to calculate the hash values of the keyword group {Beijing, Shanghai, Hangzhou, Xi'an} as follows:
[0119] Table 1 keyword hash table
[0120]
[0121] Then the ciphertext C corresponding to these 4 keywords 1 , C 2 , C 3 , C 4 added to index M
[0122]
[0123] Generate its corresponding compressed index M according to the index M (size n) * (of size n) is 111110101001,
[0124] Then store the index M of document D in the index table of the database,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com