A method and device for detecting sql injection vulnerabilities
A vulnerability and vector technology, applied in the field of detecting SQL injection vulnerabilities, can solve problems such as increased resource consumption, false negatives, and inability to obtain a large amount of data network conditions, and achieve the effect of reducing operating load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
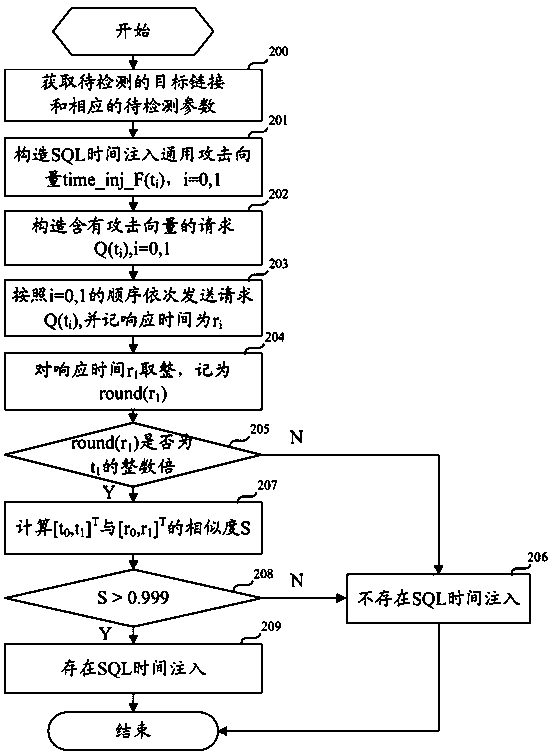
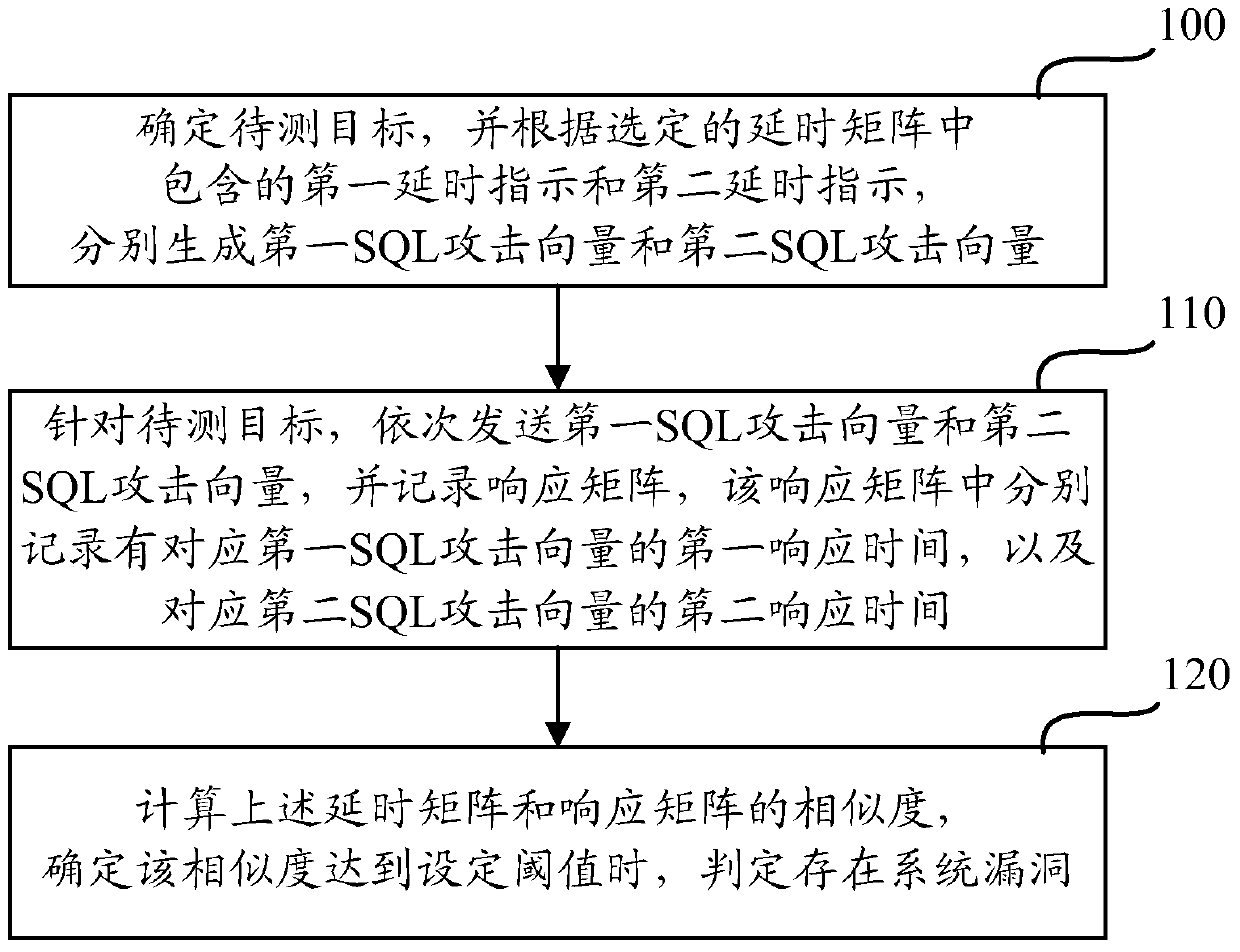
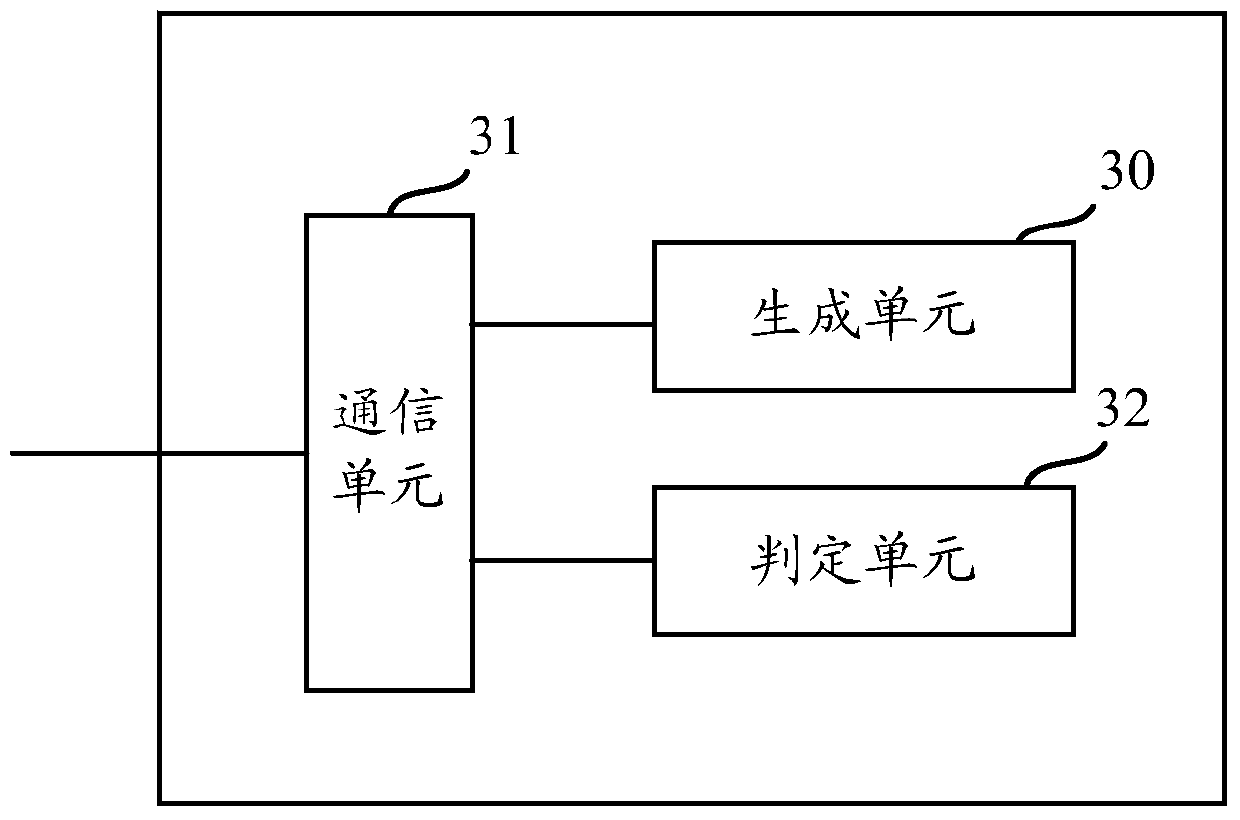
[0052] In order to solve the above problems, the present invention can automatically, quickly and accurately detect time-based SQL injection through a program, and proposes an environment-adaptive SQL time injection detection method. The method is as follows: send two SQL attack vectors carrying delay indications successively, and then record the corresponding response times respectively, and then calculate the difference between the delay matrix composed of two SQL attack vectors and the response matrix composed of two response times. After the similarity is determined to reach the threshold, it is determined that there is a time-type SQL injection vulnerability.
[0053] Preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0054] In the embodiment of the present invention, in order to adapt to different network conditions and different target environments, an environment-adaptive SQL time injection ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap