A mobile terminal of a stolen anti-swiping machine and a stolen anti-swiping machine method
A mobile terminal and anti-swipe technology, applied in data processing applications, instruments, computing, etc., can solve problems such as loss or theft of mobile terminals, reduce value, increase initiative, and avoid resale of users' mobile terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
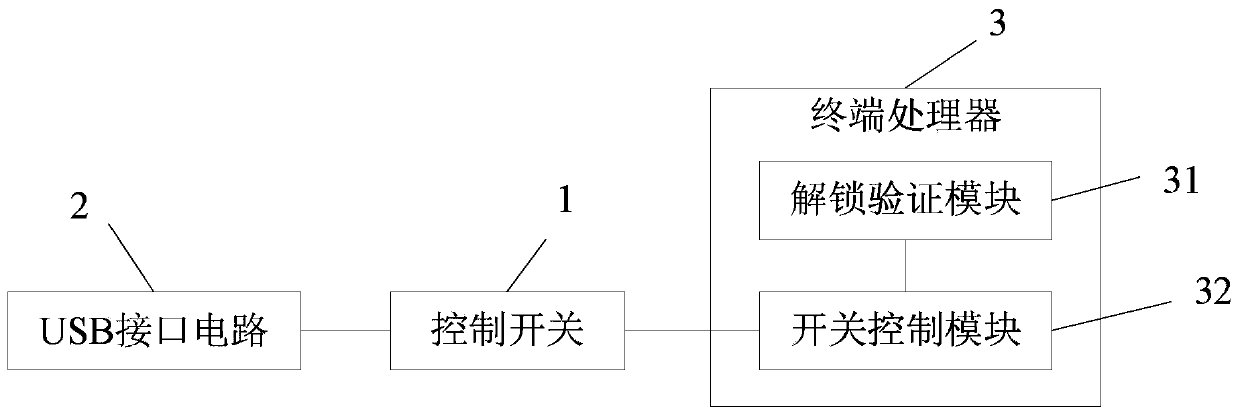
[0033] The first embodiment of the present invention provides a mobile terminal of a stolen anti-brush machine, please refer to figure 1 The mobile terminal of the embodiment of the present invention includes a control switch 1, a USB interface circuit 2 and a terminal processor 3. This embodiment will be described in detail below with reference to the accompanying drawings.
[0034] The control switch 1, which is connected in series to the data transmission port or power port of the USB interface circuit 2 of the mobile terminal, and is located between the USB interface circuit 2 and the terminal processor 3, and is used to turn on / off the signal of the USB interface circuit 2 Circulate, or turn on / off the power of the USB interface circuit 2. The control switch 1 is in an off state when the mobile terminal locks the screen.
[0035] In specific implementation, the data transmission port of the USB interface circuit 2 includes the D+ port and the D- port of the USB interface circu...
Embodiment 2
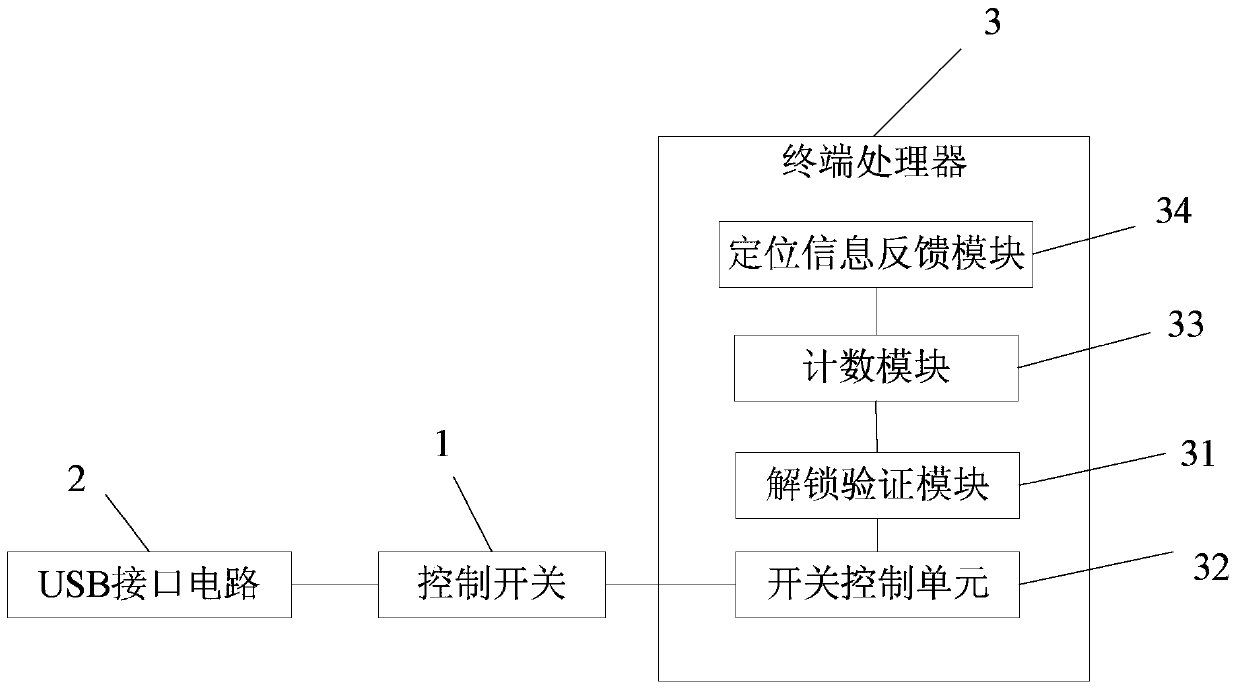
[0043] The second embodiment of the present invention provides a mobile terminal of a stolen anti-brush machine, please refer to figure 2 The difference between the mobile terminal in the second embodiment of the present invention and the mobile terminal in the first embodiment is that the terminal processor 3 of the mobile terminal in the second embodiment of the present invention further includes a counting module 33 and a positioning information feedback module 34. The modules are described, the same modules are not repeated here.
[0044] The counting module 33 is configured to calculate the number of times that the unlock verification information input by the user fails to be verified.
[0045] The positioning information feedback module 34 is configured to send the current location information of the mobile terminal to the preset mobile phone number of the anti-theft notification contact when the number of verification failures reaches a preset threshold.
[0046] The mobile t...
Embodiment 3
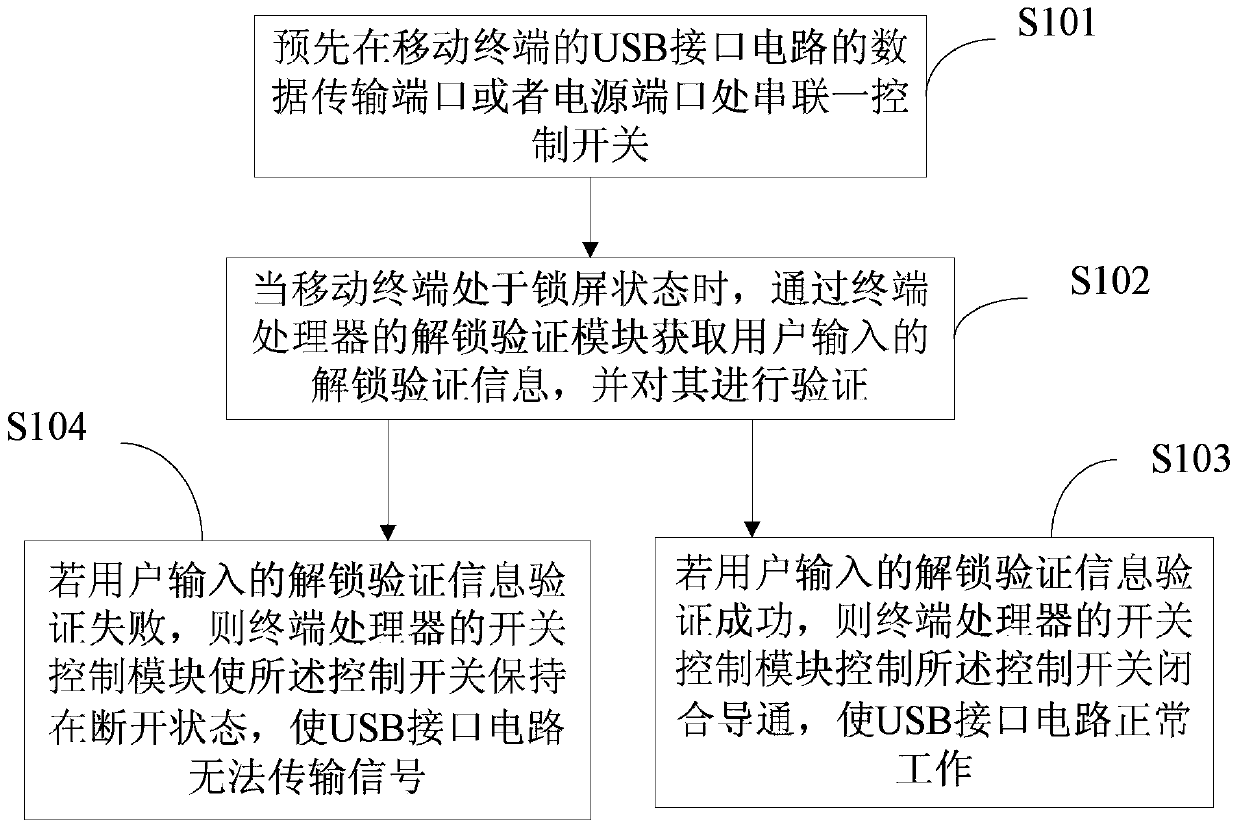
[0048] The third embodiment of the present invention provides a stolen anti-brushing method implemented by using the mobile terminal described in the above technical solution. image 3 It is the method flowchart of the third embodiment of the present invention, please refer to image 3 , The method of the embodiment of the present invention includes the following steps:
[0049] Step S101: A control switch 1 is connected in series with the data transmission port or the power port of the USB interface circuit 2 of the mobile terminal in advance;
[0050] In specific implementation, the data transmission port of the USB interface circuit 2 includes the D+ port or the D- port of the USB interface circuit 2; the power port of the USB interface circuit 2 includes the VBUS port of the USB interface circuit 2. Wherein, the control switch 1 is in an off state when the mobile terminal locks the screen.
[0051] Step S102: When the mobile terminal is in the locked screen state, obtain the un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com