File processing method and processing system
A processing method and processing system technology, applied in the field of file processing methods and processing systems, can solve problems such as easy cracking, negligence or omission risk, etc., and achieve the effect of not easy to crack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
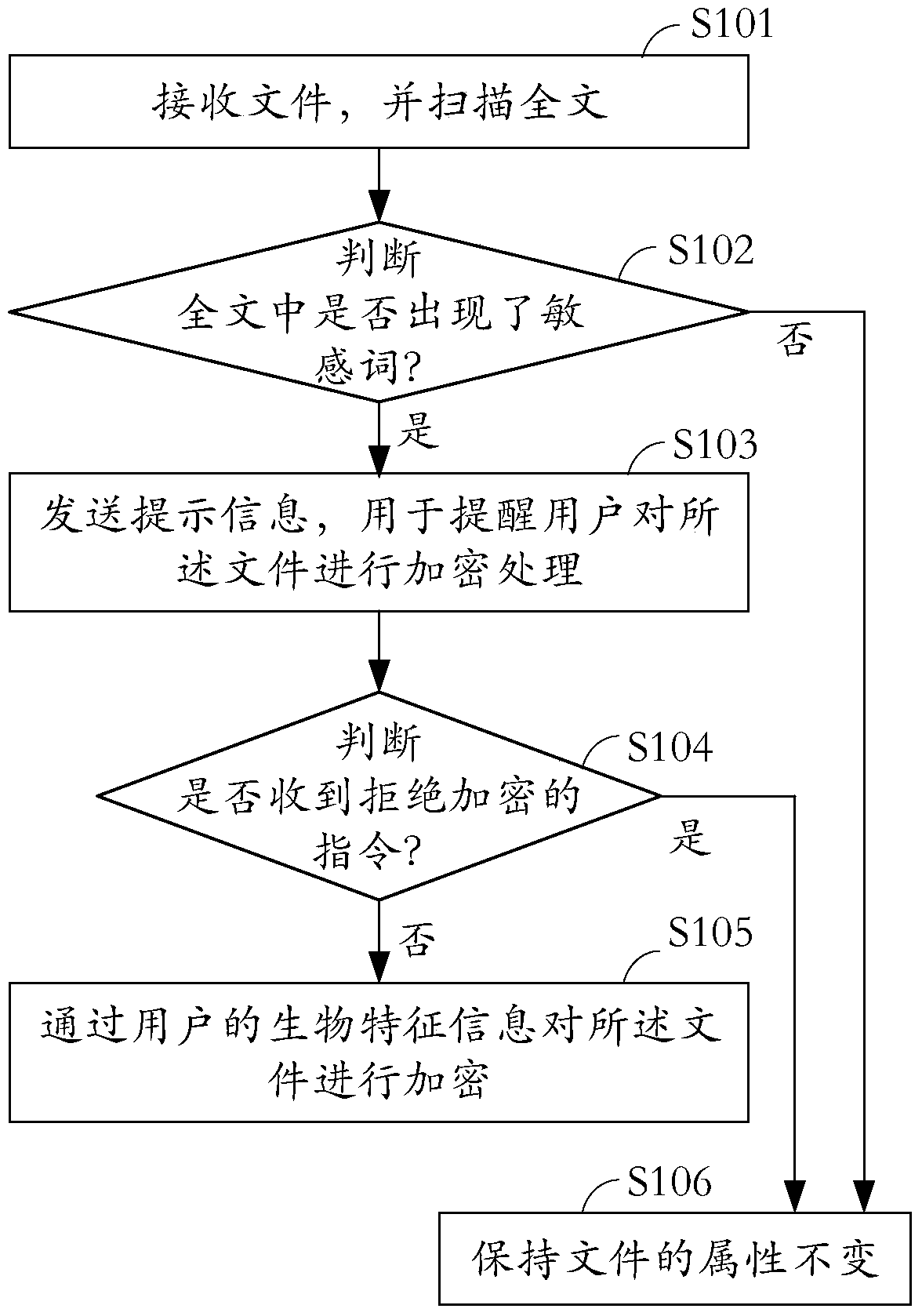
[0030] see figure 1 , which is a schematic flowchart of the file processing method provided by the embodiment of the present invention.
[0031] The processing method of the file is applied to a terminal device, such as a mobile phone, and the processing method includes:
[0032] In step S101, the document is received and the full text is scanned.
[0033] The files include, but are not limited to: office software (such as WORD, EXCEL, WPS, or Notepad), web pages (such as Evernote), applications (such as memos, or reminders), or photos, etc.
[0034] In step S102, it is judged whether sensitive words appear in the full text.
[0035] Wherein, if the sensitive word appears, execute step S103; if the sensitive word does not appear, execute step S106.
[0036] The sensitive words can be set by the owner of the terminal device. Unlike the sensitive words in the public opinion monitoring system, they do not refer to political tendencies, violent tendencies, unhealthy, or uncivil...
Embodiment 2
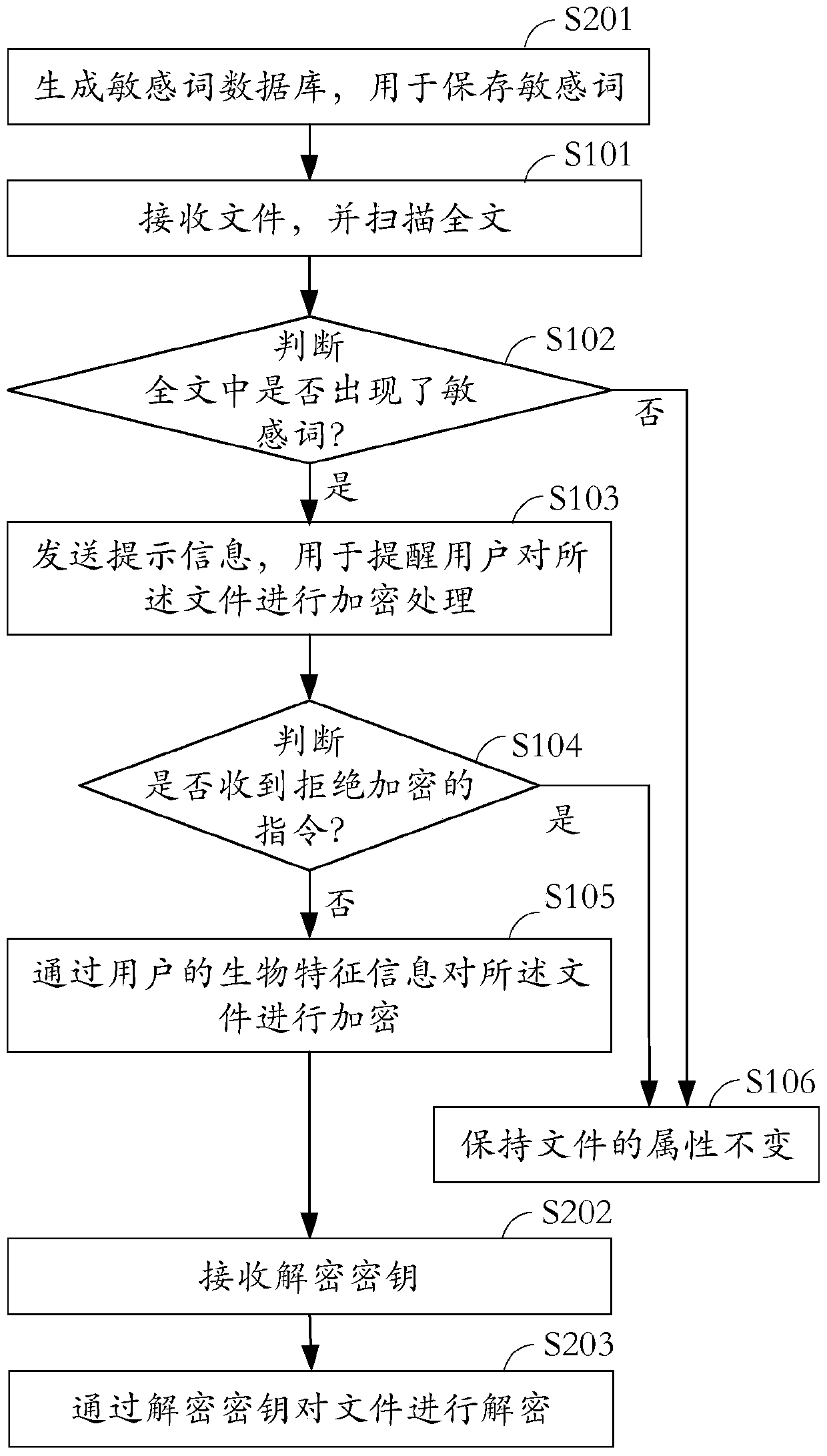
[0054] see figure 2 , which is a schematic flowchart of the file processing method provided by the embodiment of the present invention. in, figure 2 and figure 1 The same steps in still use the label beginning with S1, which is the same as figure 1 The different steps are labeled with S2 at the beginning to distinguish them.
[0055] The file processing method is applied to a terminal device, and the processing method includes:
[0056] In step S201, a database of sensitive words is generated for the sensitive words.
[0057] Specifically, the step of generating the sensitive word database includes:
[0058] (1) Receive sensitive words input by the user one by one, that is, set by the owner of the terminal device. The sensitive words include: divorce, agreement, adoption, medical records, contract, or confidentiality, etc.; or / and
[0059] (2) Receive the sensitive words selected by the user, and download the sensitive words corresponding to the sensitive words, such a...
Embodiment 3
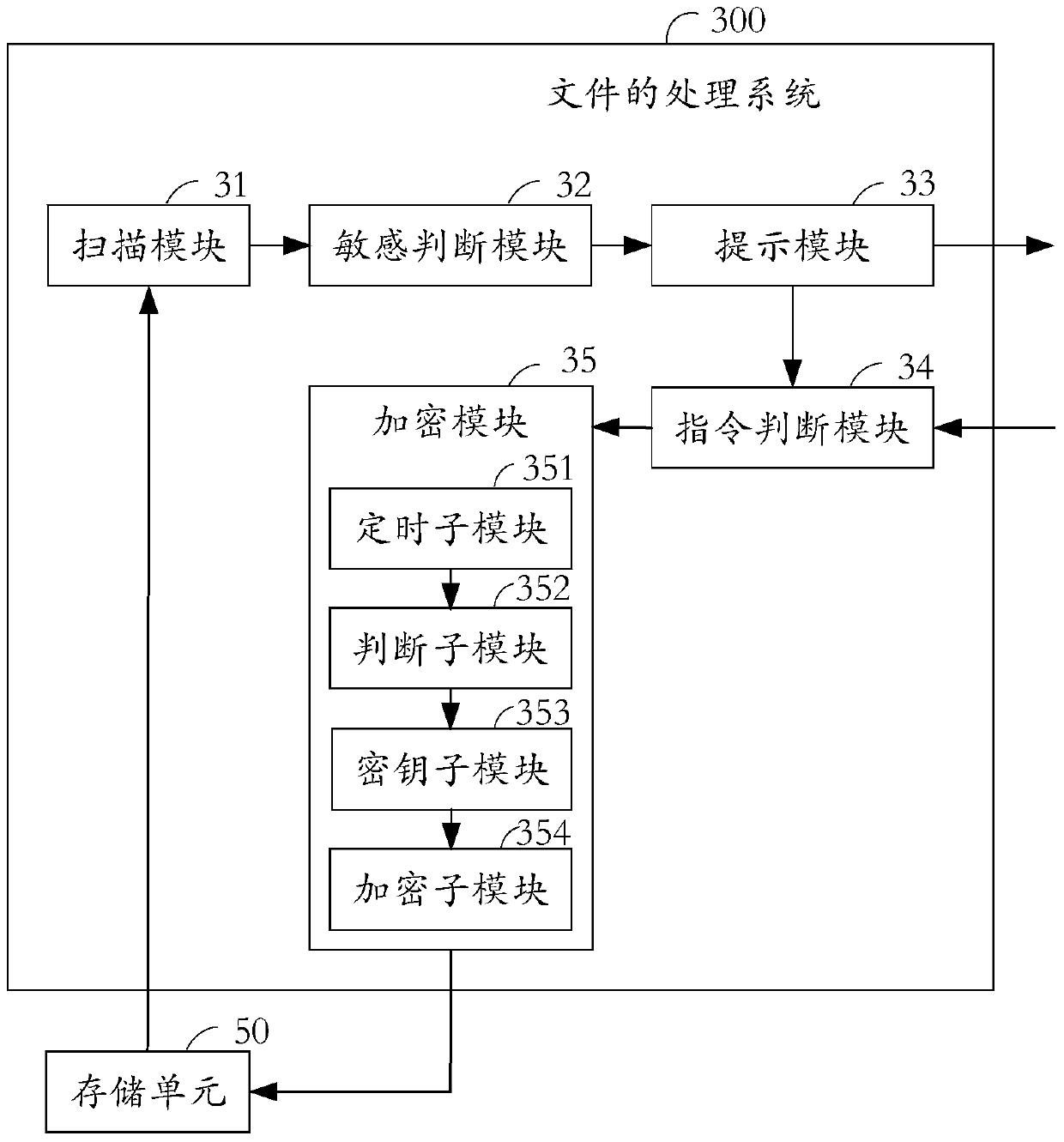
[0097] see image 3 , which is a schematic flowchart of the file processing system provided by the embodiment of the present invention.
[0098] The file processing system 300 is applied to a terminal device, and the processing system 300 includes: a scanning module 31 , a sensitivity judgment module 32 , a prompt module 33 , an instruction judgment module 34 , and an encryption module 35 .
[0099] The scanning module 31 is connected to the storage unit 50 and used for receiving or reading the files in the storage unit 50 and scanning the full text.
[0100] Among them, the files include but are not limited to: office software (such as WORD, EXCEL, WPS, or Notepad), web pages (such as Evernote), applications (such as memos, or reminders), or pictures (such as photos), etc. .
[0101] Sensitive judging module 32, connected to the scanning module 31, is used to judge whether sensitive words appear in the full text.
[0102] Wherein, the sensitive words can be set by the owne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com