Information security offense and defense drill competition system for power industry
An information security and power industry technology, applied in transmission systems, electrical components, etc., can solve problems such as weak information security protection, stealing sensitive information, tampering with website content, etc., to improve the company's independent and controllable information security capabilities, and strengthen team building. , Improve the effect of vulnerability mining ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
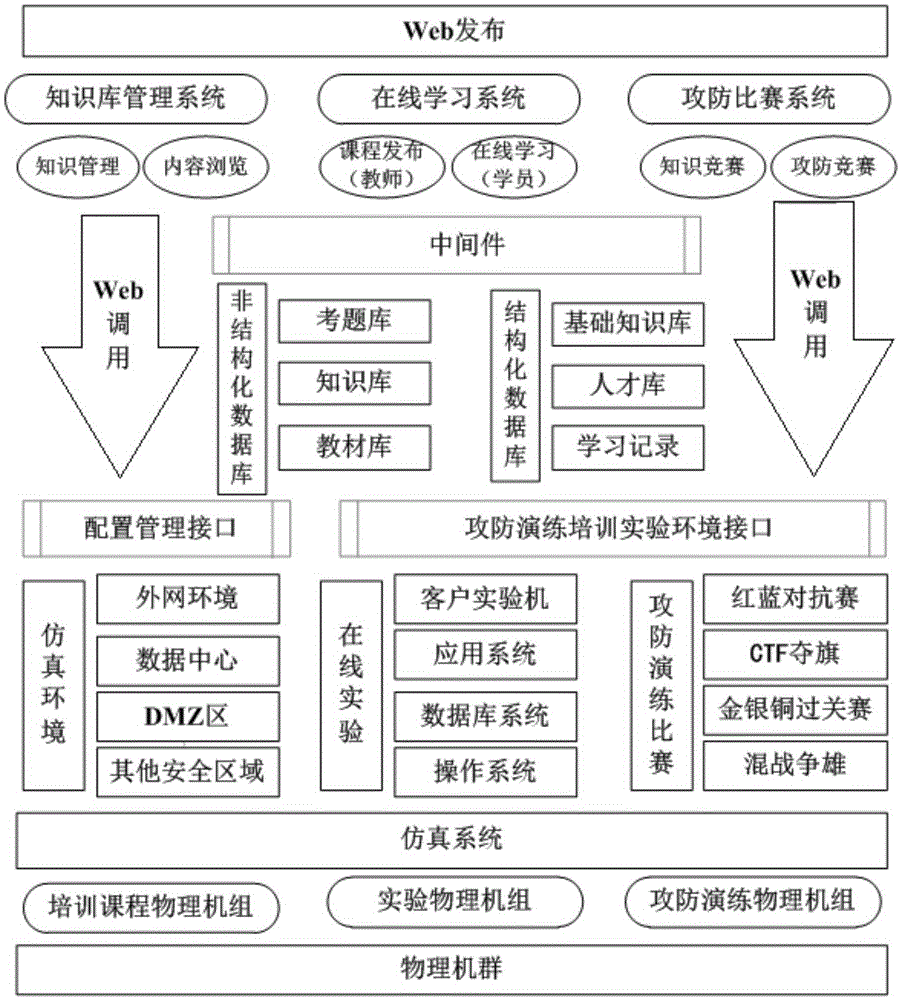
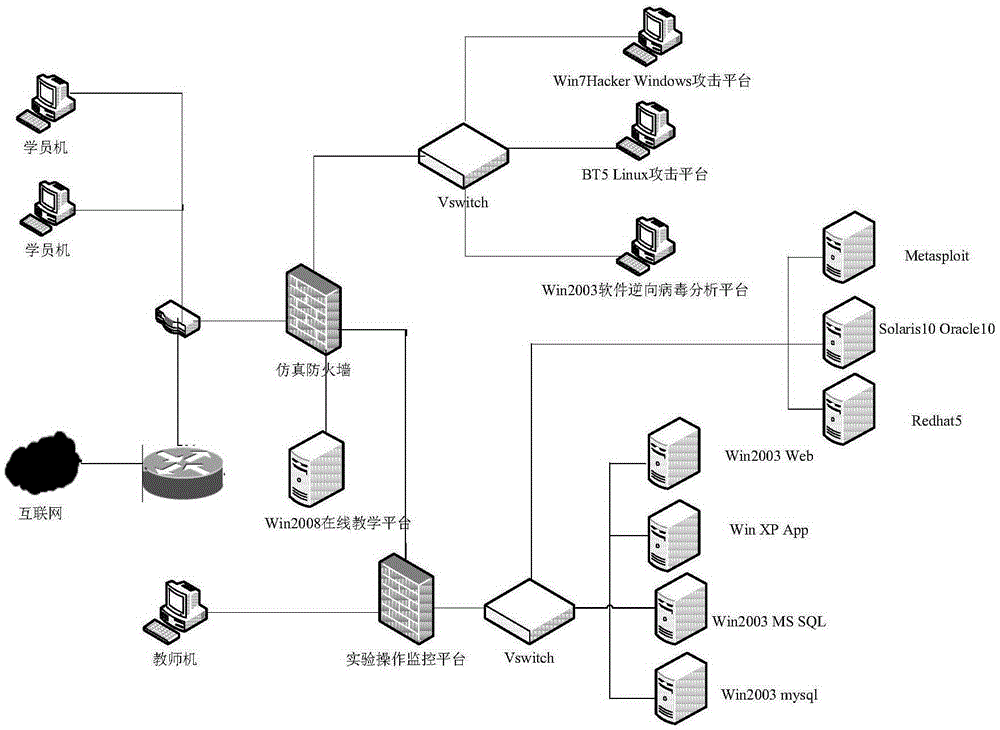
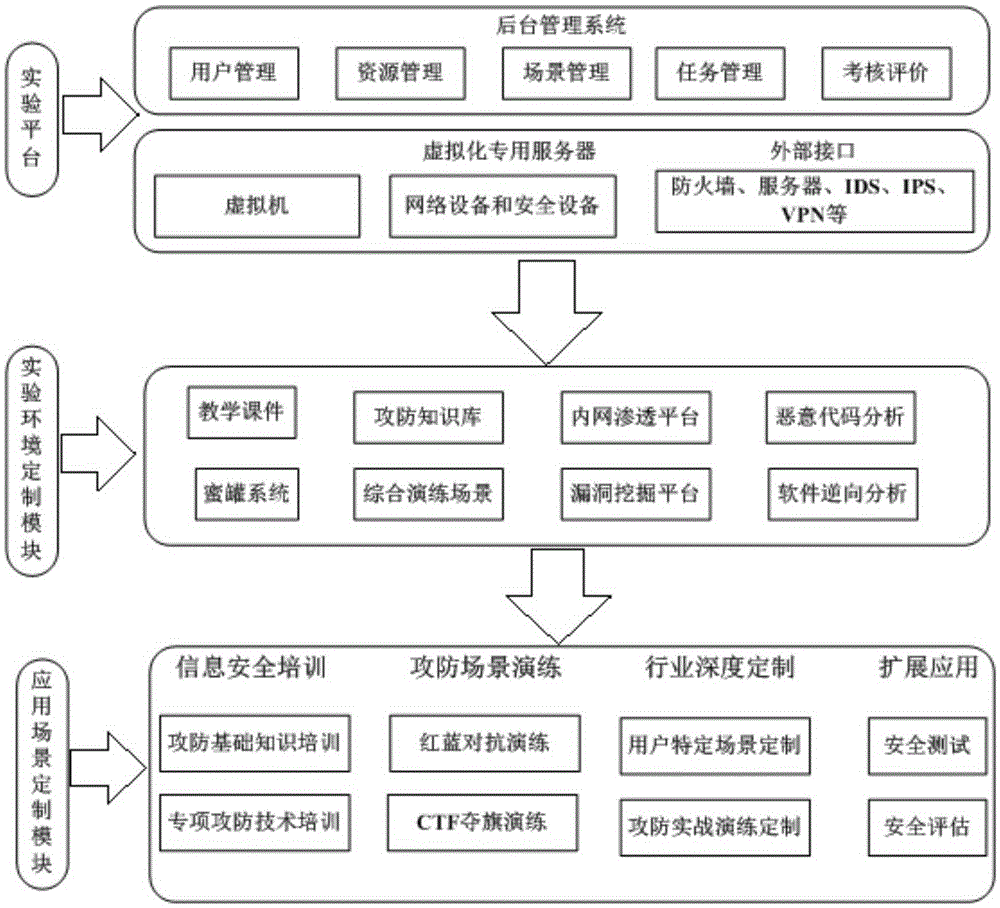
[0035] like figure 1 As shown, the power system will organize information security professionals from various units to participate in competitions from time to time, which will be used to select outstanding personnel to set up information security red and blue teams, and to carry out work such as power information system vulnerability mining and hidden danger investigation. The knowledge contest is mainly a stand-alone operation, and the offensive and defensive competition includes two aspects: attack and defense. The attacker mainly targets the company's information security red team, exploits the loopholes on the target target machine, obtains administrator privileges through some privilege escalation methods, and then obtains the information on the target target machine. Sensitive information; the defender is mainly aimed at the company's information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com